2024江西省赛 misc&crypto&reverse
2024江西省赛 misc&crypto&reverse
misc
TheCutestPeople
开题一张图片010打开
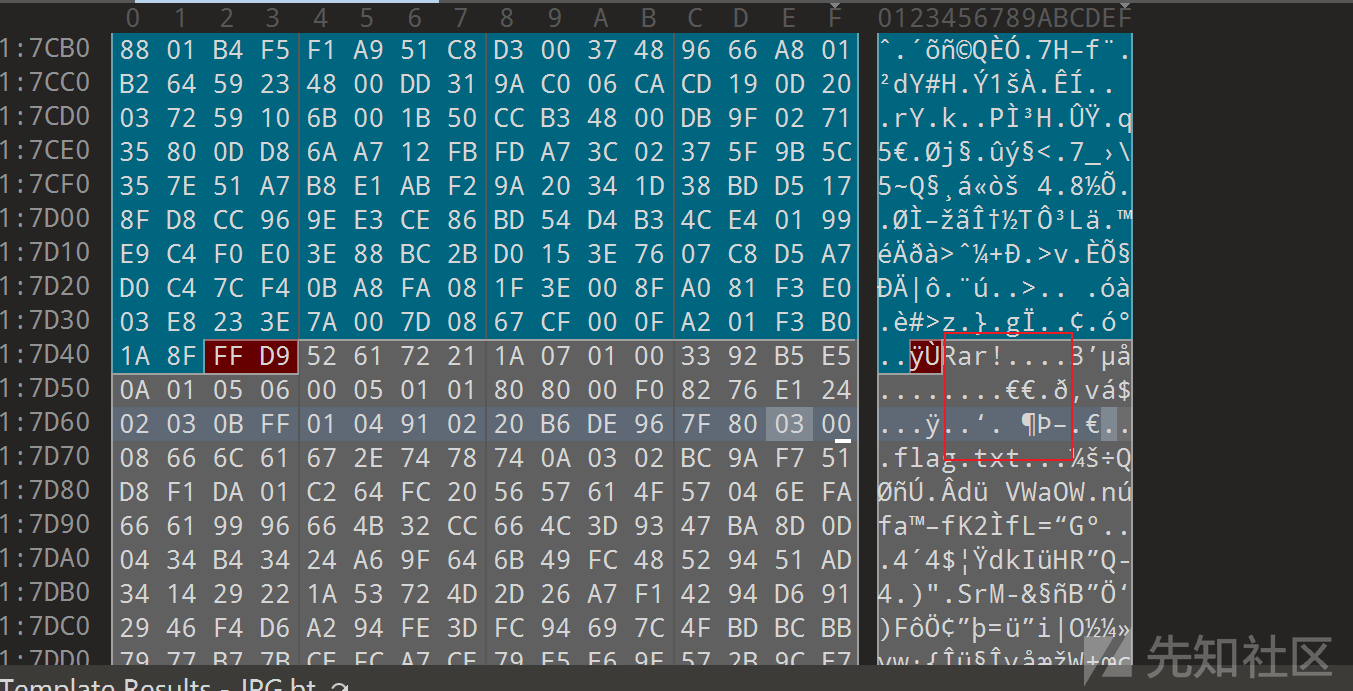
尾部发现rar
然后手动分离
解压发现一个txt

非常明显的zip的倒叙
写个脚本然后调整过来
flag = '00000000009600000065000100010000000006054b50000803454100010007990101daf1d6831f9a3a01daf1d697c3027101daf1d697c3027100180001000000000020000a7478742e67616c660000000000000020000000000000002f000800000037000000557bef941c59134b1a006300090014001f02014b5000000037000000557bef941c08074b5049e0781d171c8f55713bc21ee4a059ff8918b068d8240f5ac2cc631ec811b528fccf28ac671619772e92579bf8c133a26e20857cc78a28fbcf8a8e6d0eda11a2db6ad6bbc83cc938c4bae4ae8d220d55e37cdd4d4100080345410001000799017478742e67616c66000b000800000037000000557bef941c59134b1a00630009001404034b50'
def sp(s):
if len(s) < 2:
return s
return ' '.join([s[i:i+2] for i in range(0, len(s), 2)])
out = sp(flag)
flag = out
flag = flag.split(' ')[::-1]
for i in flag:
print(i, end='')
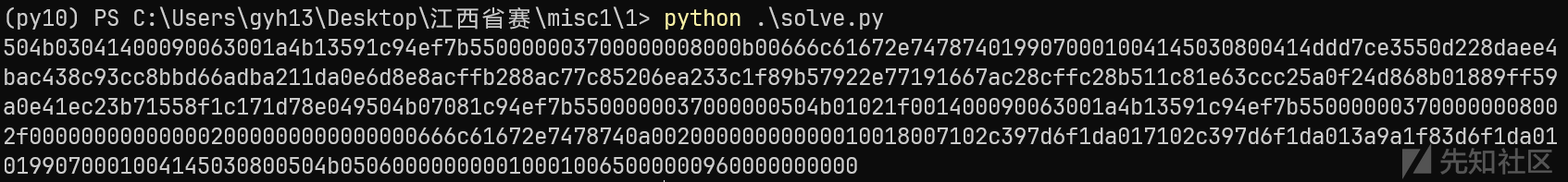
然后放进010 保存成zip
发现是真加密
尝试爆破未果
在属性中发现16进制
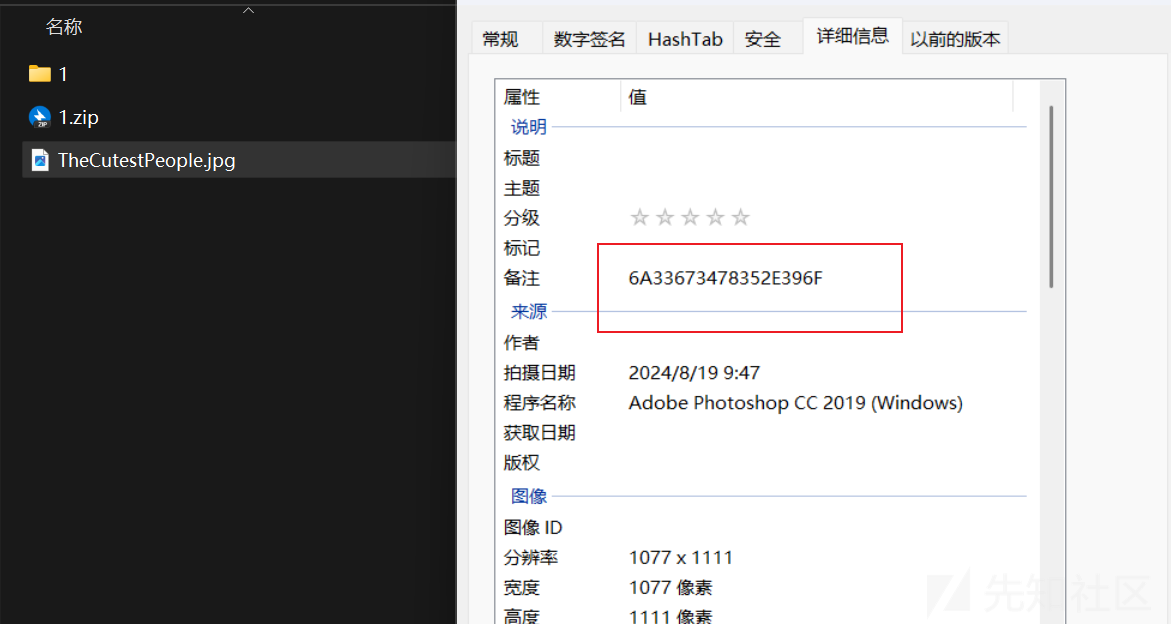
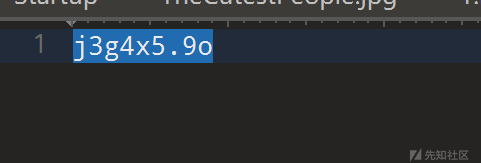
这个就是密码,解压的内容如下
4rHP3nL8XpKjkQNHfbrqg3AbCc3SodmMjdFK9TXkAXVYhCzjxRJasAp
进行解密
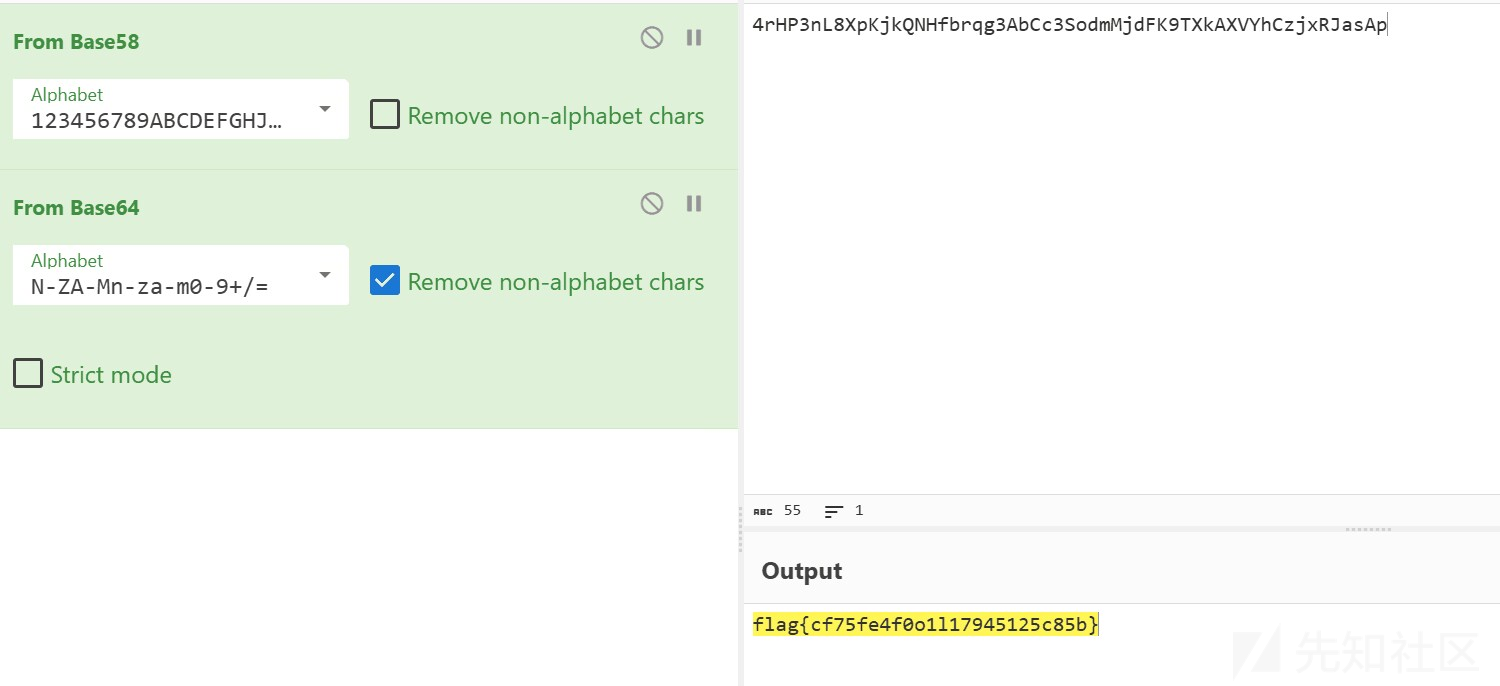
拿到flag
crypto
random
发现了网上原题找到个现成的脚本
import os,sys
os.chdir(sys.path[0])
from random import Random
# right shift inverse
def inverse_right(res, shift, bits=32):
tmp = res
for i in range(bits // shift):
tmp = res ^ tmp >> shift
return tmp
# right shift with mask inverse
def inverse_right_mask(res, shift, mask, bits=32):
tmp = res
for i in range(bits // shift):
tmp = res ^ tmp >> shift & mask
return tmp
# left shift inverse
def inverse_left(res, shift, bits=32):
tmp = res
for i in range(bits // shift):
tmp = res ^ tmp << shift
return tmp
# left shift with mask inverse
def inverse_left_mask(res, shift, mask, bits=32):
tmp = res
for i in range(bits // shift):
tmp = res ^ tmp << shift & mask
return tmp
def extract_number(y):
y = y ^ y >> 11
y = y ^ y << 7 & 2636928640
y = y ^ y << 15 & 4022730752
y = y ^ y >> 18
return y&0xffffffff
def recover_state(out):
state = []
for y in out:
y = inverse_right(y,18)
y = inverse_left_mask(y,15,4022730752)
y = inverse_left_mask(y,7,2636928640)
y = inverse_right(y,11)
state.append(y)
return state
def backtrace(cur):
high = 0x80000000
low = 0x7fffffff
mask = 0x9908b0df
state = cur
for i in range(3,-1,-1):
tmp = state[i+624]^state[(i+397)]
# recover Y,tmp = Y
if tmp & high == high:
tmp ^= mask
tmp <<= 1
tmp |= 1
else:
tmp <<=1
# recover highest bit
res = tmp&high
# recover other 31 bits,when i =0,it just use the method again it so beautiful!!!!
tmp = state[i-1+624]^state[(i+396)]
# recover Y,tmp = Y
if tmp & high == high:
tmp ^= mask
tmp <<= 1
tmp |= 1
else:
tmp <<=1
res |= (tmp)&low
state[i] = res
return state
f = open('output','r').readlines()
c = []
for i in range(1000):
c.append(int(f[i].strip()))
part = recover_state(c)
state = backtrace([0]*4 + part)[:624]
# print(state)
prng = Random()
prng.setstate((3,tuple(state+[0]),None))
flag = "flag{" + ''.join(str(prng.getrandbits(32)) for _ in range(4)) + "}"
print(flag)
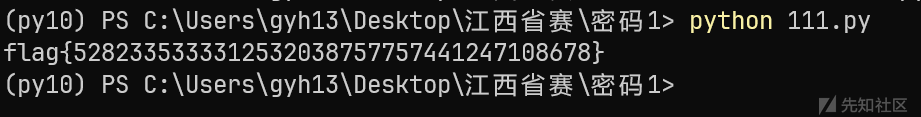
拿到flag
reverse
xor
def reverse_xor_decryption():
# 原始的加密数据(作为字符列表)
encrypted_data = list("t~suiFz{aM{aMsMwsakM`wdw`awo")
# 已知的XOR密钥
xor_key = 0x12
# 通过XOR逆向计算出原始的明文
# 将每个字符与密钥进行XOR操作,然后将其转换回字符
decrypted_data = ''.join([chr(ord(char) ^ xor_key) for char in encrypted_data])
# 打印解密后的明文
print(f"The decrypted input is: {decrypted_data}")
# 调用函数以执行解密
reverse_xor_decryption()
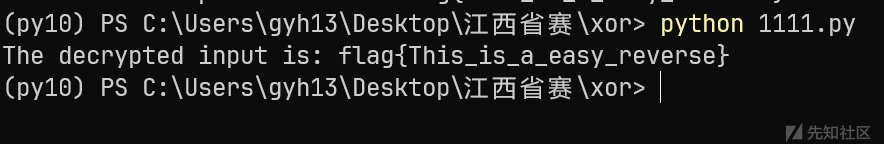
flag{This_is_a_easy_reverse}
find
查看文件信息发现有ASpack壳:
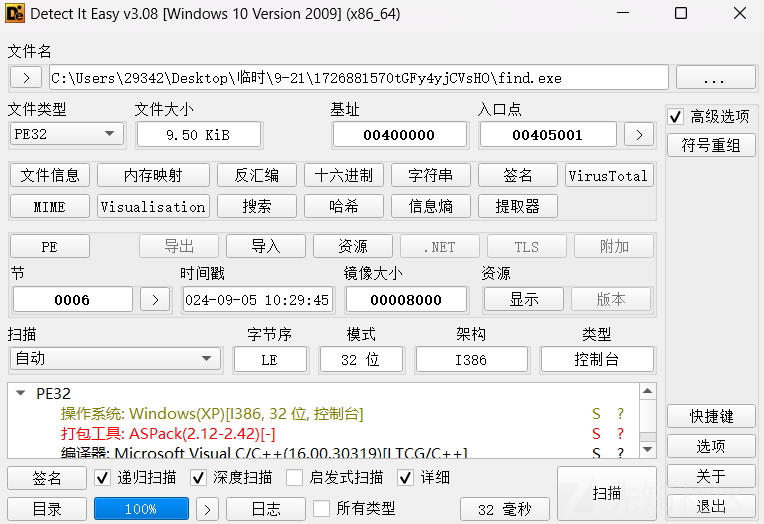
手动脱壳后丢入ida分析:
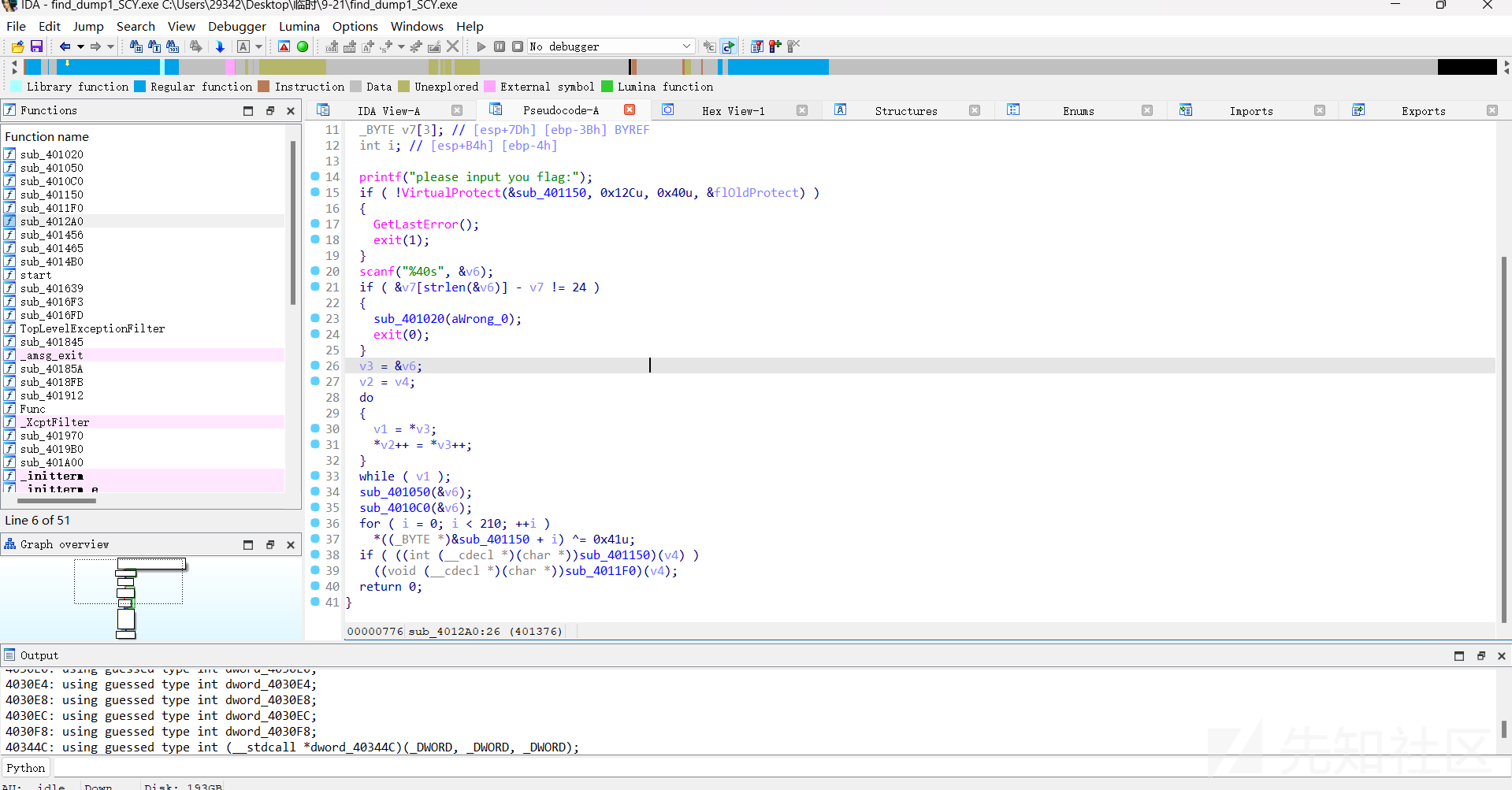
发现是一个SMC,前面两个函数是一个混淆,直接动态运行查看真实的加密函数:
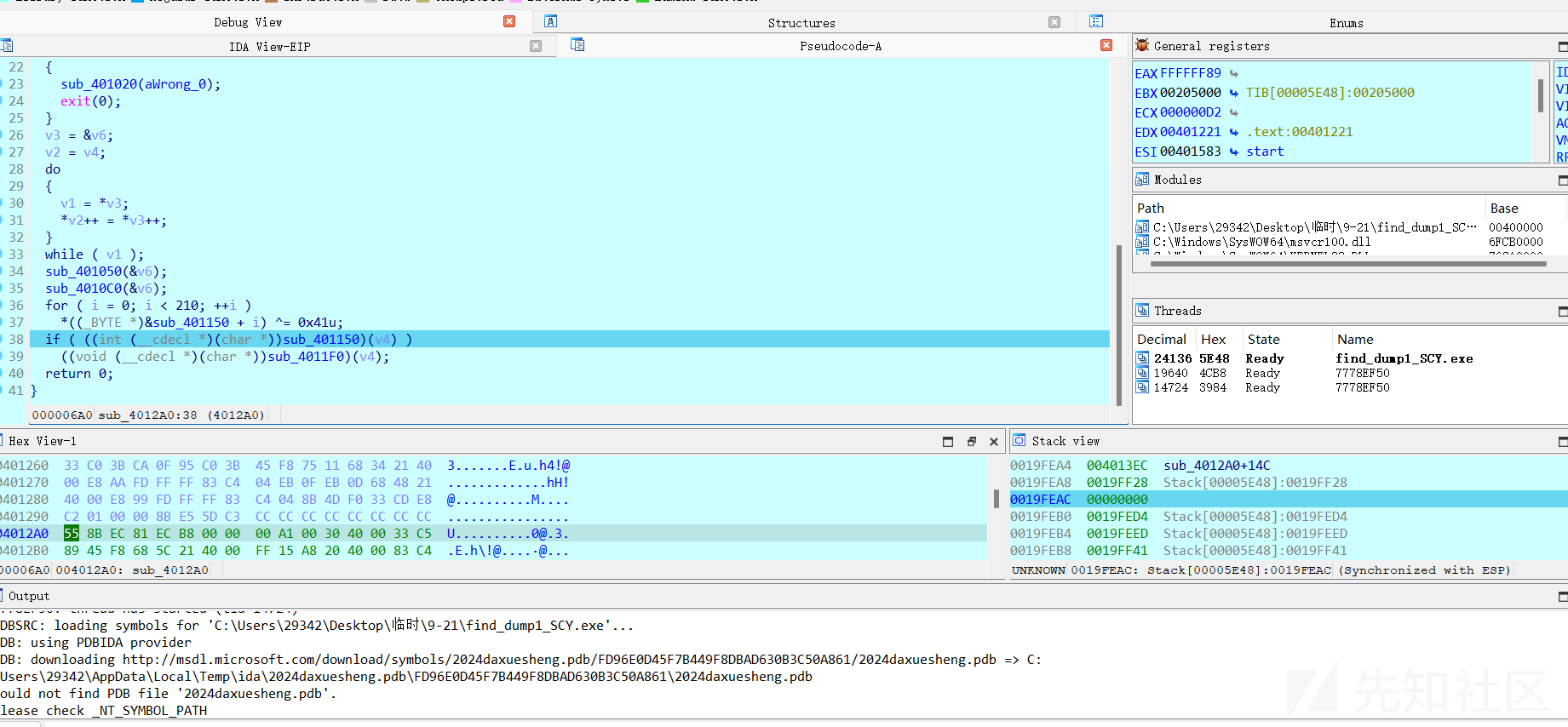
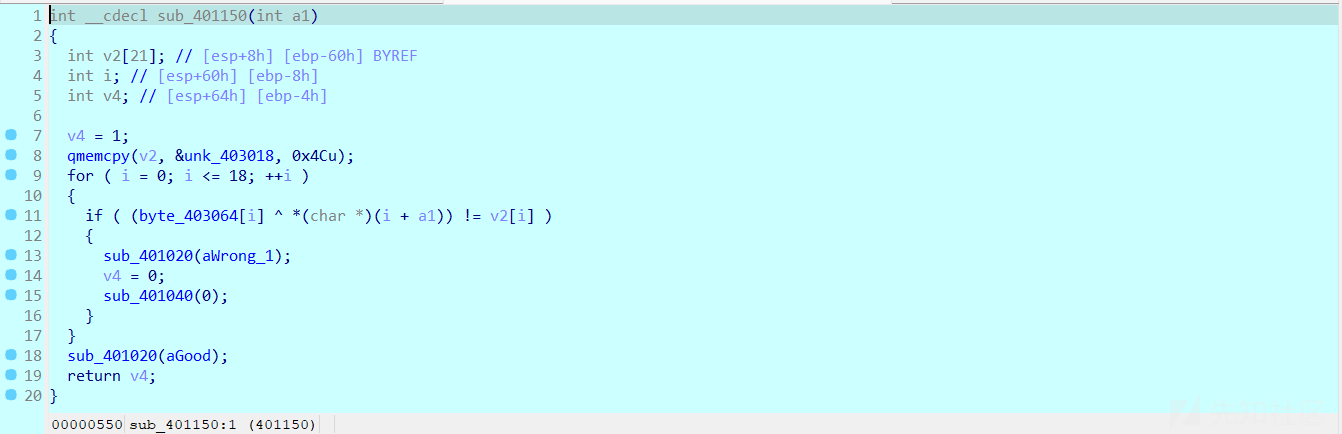
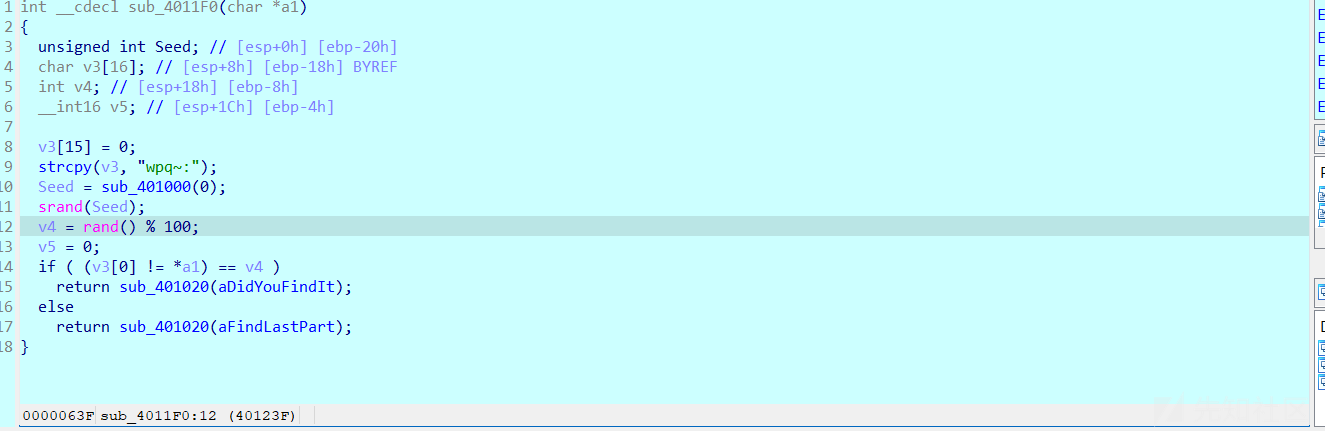
发现还是一个简单的异或,解密代码如下:
key = [0x68, 0x65, 0x6C, 0x6C, 0x6F, 0x68, 0x6F, 0x77, 0x61, 0x72,
0x65, 0x79, 0x6F, 0x75, 0x69, 0x61, 0x6D, 0x66, 0x69, 0x6E,
0x65, 0x74, 0x68, 0x69]
y= [0x0E, 0x00, 0x00, 0x00, 0x09, 0x00, 0x00, 0x00, 0x0D, 0x00,
0x00, 0x00, 0x0B, 0x00, 0x00, 0x00, 0x14, 0x00, 0x00, 0x00,
0x2E, 0x00, 0x00, 0x00, 0x57, 0x00, 0x00, 0x00, 0x31, 0x00,
0x00, 0x00, 0x25, 0x00, 0x00, 0x00, 0x45, 0x00, 0x00, 0x00,
0x55, 0x00, 0x00, 0x00, 0x41, 0x00, 0x00, 0x00, 0x2C, 0x00,
0x00, 0x00, 0x4C, 0x00, 0x00, 0x00, 0x5B, 0x00, 0x00, 0x00,
0x52, 0x00, 0x00, 0x00, 0x55, 0x00, 0x00, 0x00, 0x57, 0x00,
0x00, 0x00, 0x5E, 0x00, 0x00, 0x00]
x = []
for i in y:
if i != 0:
x.append(i)
print(x)
print(len(x))
for i in range(19):
k = x[i] ^ key[i]
print(chr(k),end='')
z = 'wpq~:'
for i in z:
print(chr(ord(i)^(ord(':')^ord('}'))),end='')
#flag{F8FD708C9238170769}
0 条评论
可输入 255 字

 转载
转载
 分享
分享
