2024年NSSCTF秋季招新赛(校外赛道) Crypto
Aftermath
题目
让我们把CRYPTO烧成灰
from Crypto.Util.number import getPrime, inverse, long_to_bytes, bytes_to_long
from sympy import gcd
key_size = 1024
p = getPrime(key_size // 2)
q = getPrime(key_size // 2)
N = p * q
phi = (p - 1) * (q - 1)
e1 = 3
e2 = 7
message = b"NSSCTF{...............................................}"
m = bytes_to_long(message)
assert gcd(m, N) == 1
c1 = pow(m, e1, N)
c2 = pow(m, e2, N)
print(f"N = {N}")
print(f"e1 = {e1}")
print(f"c1 = {c1}")
print(f"e2 = {e2}")
print(f"c2 = {c2}")
#N = 80722936701364382749961243326484006977187702986017980842794443374132452156776306032868217795522046975068822236770836452911408536092460646410756678157902792329645719935468879960944028782788489463895870961967670931567205550383999951787250211085264314795753745003815839218062934564501884684565508432346164094171
#e1 = 3
#c1 = 77027474990431732719325428265107176934045610651944725251406683442684093440239073195437770144166442593914418380343458827052860752131667771506129334676070396374008929588455988149871039697387983766750148969695215583137356681988572655848921827794639096404716760310059622671470680330144220097050812716421370445797
#e2 = 7
#c2 = 13491956530007991248882899018888359080930858500993821006822695375714947537976202424265808646466853291165511243721829370428583392329886743499827454177786585477285598196204906977043127274613692623229137936467994670727274820568522666762615055848367486507714640497446688083840123758417442971555904294548595887600
分析
gcd(e1,e2)=1,e1,e2互质
根据扩展欧几里德算法,对于不完全为 0 的整数 a,b,gcd(a,b)表示 a,b 的最大公约数。那么一定存在整数 x,y 使得 gcd(a,b)=ax+by
所以得到:
e1s1+e2s2 = 1
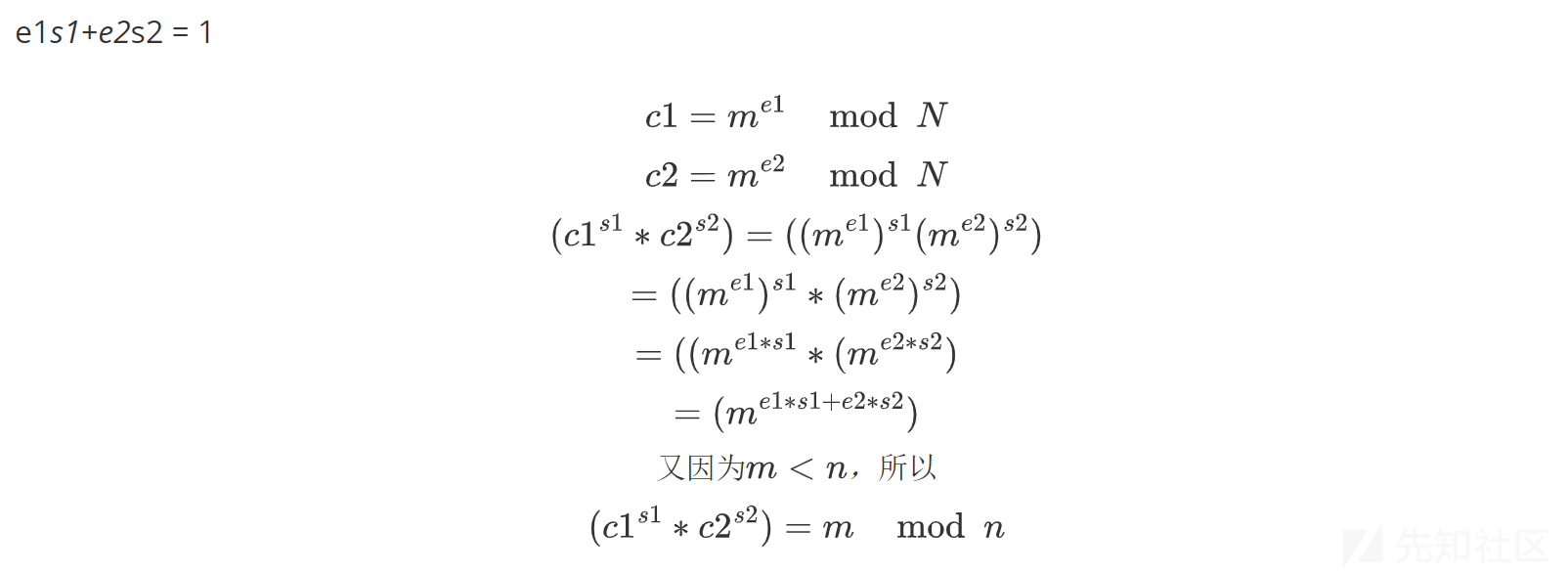
import gmpy2
import libnum
from Crypto.Util.number import long_to_bytes
N = 80722936701364382749961243326484006977187702986017980842794443374132452156776306032868217795522046975068822236770836452911408536092460646410756678157902792329645719935468879960944028782788489463895870961967670931567205550383999951787250211085264314795753745003815839218062934564501884684565508432346164094171
e1 = 3
c1 = 77027474990431732719325428265107176934045610651944725251406683442684093440239073195437770144166442593914418380343458827052860752131667771506129334676070396374008929588455988149871039697387983766750148969695215583137356681988572655848921827794639096404716760310059622671470680330144220097050812716421370445797
e2 = 7
c2 = 13491956530007991248882899018888359080930858500993821006822695375714947537976202424265808646466853291165511243721829370428583392329886743499827454177786585477285598196204906977043127274613692623229137936467994670727274820568522666762615055848367486507714640497446688083840123758417442971555904294548595887600
s,s1,s2=gmpy2.gcdext(e1,e2)
m=(pow(c1,s1,N)*pow(c2,s2,N))%N
print(long_to_bytes(m))
b'NSSCTF{It all played out with my life on pause}'
完全感觉Dreamer
题目
这就是签到题了
GyAGD1ETr1EbnKZtnKZtoKxto3qhVTc1MTqyoJIhqPRuVRqiqPOho3EbnJ5aVUEiVUAurK0=
分析
base64
NSSCTF{This is my own judgement!! Got nothing to say}
看懂了就来拿flag吧
题目
没梗玩了,呜呜呜
from Crypto.Cipher import AES
import base64
class Encrypt:
def __init__(self,key,iv):
self.key = key.encode('utf-8')
self.iv = iv.encode('utf-8')
def pkcs7padding(self, text):
bs = 16
length = len(text)
bytes_length = len(text.encode('utf-8'))
padding_size = length if (bytes_length == length) else bytes_length
padding = bs - padding_size % bs
padding_text = chr(padding) * padding
self.coding = chr(padding)
return text+padding_text
def aes_encrypt(self, content):
cipher = AES.new(self.key, AES.MODE_CBC, self.iv)
content_padding = self.pkcs7padding(content)
encrypt_bytes = cipher.encrypt(content_padding.encode('utf-8'))
result = str(base64.b64encode(encrypt_bytes),encoding='utf-8')
return result
def aes_decrypt(self, content):
cipher = AES.new(self.key, AES.MODE_CBC, self.iv)
content = base64.b64decode(content)
text = cipher.decrypt(content).decode('utf-8')
return text.rstrip(self.coding)
if __name__ == '__main__':
iv = '01pv928nv2i5ss68'
key = '53f09k56nv2b10cf'
a = Encrypt(key=key, iv=iv)
e = a.aes_encrypt('{12evw_utker_5ythgf}')
print(e)分析
本来应该是
flag=a.aes_decrypt(e)
key,iv都知道,仔细一看
e = a.aes_encrypt('{12evw_utker_5ythgf}')
已经给出了明文
加上NSSCTF就是flag
泰坦陨落2
题目
飞天克莱伯还阴啊
# LCG参数
a = 1664525
c = 1013904223
m = 2**32
# 妙蛙种子
seed = .........
# 生成伪随机数
def lcg(seed, n):
numbers = []
for _ in range(n):
seed = (a * seed + c) % m
numbers.append(seed)
return numbers
# 给你5个伪随机数
random_numbers = lcg(seed, 5)
print(random_numbers)
#[3771924608, 3319331295, 583630258, 2401321321, 611326900]def xor_encrypt_decrypt(data, key):
key_bytes = key.to_bytes((key.bit_length() + 7) // 8, 'big')
key_length = len(key_bytes)
result = bytearray()
for i in range(len(data)):
result.append(data[i] ^ key_bytes[i % key_length])
return bytes(result)
flag = "NSSCTF{........................................}"
flag_bytes = flag.encode('utf-8')
# 使用妙蛙种子进行加密,如果你没有妙蛙种子,请先去克莱伯那里拿妙蛙种子
key = seed
encrypted_bytes = xor_encrypt_decrypt(flag_bytes, key)
# 输出加密后的字节和字符串
print("Encrypted Bytes:", encrypted_bytes)
#Encrypted Bytes: b"n2!&t'\t\x06A\x14\x01\x00\x00\x16\x17EA\x13\x17ET\t\x17EC\x0e\x1e\nR\x12R\x0cNA\x06\rEA\x16\x04R\n\x0f"分析
lcg--求出seed
def lcg(seed, n):
numbers = []
for _ in range(n):
seed = (a * seed + c) % m
numbers.append(seed)
return numbers

from Crypto.Util.number import long_to_bytes
a = 1664525
c = 1013904223
m = 2**32
def lcg(seed, n):
numbers = []
for _ in range(n):
seed = (a * seed + c) % m
numbers.append(seed)
return numbers
output=[3771924608, 3319331295, 583630258, 2401321321, 611326900]
MMI = lambda A, n,s=1,t=0,N=0: (n < 2 and t%N or MMI(n, A%n, t, s-A//n*t, N or n),-1)[n<1] #逆元计算
ani=MMI(a,m)
seed=output[-1]
for i in range(5):
seed = (ani*(seed-c))%m
print(long_to_bytes(seed))
def xor_encrypt_decrypt(data, key):
key_bytes = key.to_bytes((key.bit_length() + 7) // 8, 'big')
key_length = len(key_bytes)
result = bytearray()
for i in range(len(data)):
result.append(data[i] ^ key_bytes[i % key_length])
return bytes(result)
encrypted_bytes=b"n2!&t'\t\x06A\x14\x01\x00\x00\x16\x17EA\x13\x17ET\t\x17EC\x0e\x1e\nR\x12R\x0cNA\x06\rEA\x16\x04R\n\x0f"
key = seed
flag = xor_encrypt_decrypt(encrypted_bytes, key)
print(flag)b' are'
b'NSSCTF{cause we are the colors in the dark}'
脚本跑不出来了吧
题目
俺寻思这个脚本跑不通
e1*e2= 59653
n= 16282992590526808657350657123769110323293742472515808696156540766049532922340638986423163288656942484229334024198335416611687418341772216996129634991032127943095069143600315325916614910606100091970611448259491799589221889445348698100959509165262891180065554743420149168801638644589921791426690475846945077068114953844817073866258377206796158690941199907230130273657375727245023893672164113928189304228859412794067127721813637080447782673535996272223836127807775157150041664783263093604946744032762535394974814371771505843653571711445892969781888188805943142126747365056482511805191315474848971218180999336497135314654469910566730389765499603897685968204361422568601724914800686608628299192714352963744010136960423806304763245890692476493455775025753944860040020178234660999290356849442926396627701588938894161779071628447041006556793933320976506046066961014953196791133933438500843139378274786265308568167479880984705152809744111382599071097574636570516674122980589207824718402382459624138317432883921371298272851693734695823787102433937406420318428888224246291987404818042038201886113203158444083427668636941
c1= 15508846802476602732219982269293312372397631462289816533805702700260237855119470146237752798828431803179124957728439730580289236458563016332461725094295883030444173189424666004498359269921250956676320570006883951982237098373954348825003467019876101438948387668628518937831820206221522881150831840296199498447304138839838135264071071817072965792514115711621435317078108239744829134467948386247696344881838815422262901903767893118533887779588425725845820071451782420200868341564360095012698956683395031351656817392008005928265838760875070634021907630535014959579709368637536268853337028760833769278841040734409299575870823873616769863828516877971432999417800417684146077045836940988096634144368727546539602310924702126212020003620219218637652874119299016382481718659448722433296761241365473608283436835986184098161365747699791248301452334044327014782249692551362625130537300221641910570569803981153117200694806974917501061411963827755822672178568783269357196133308719688843211664095412087717861154226475203597889635926903753481174280305996204091501578865951177135086807765873529089048911740160698421289371229606
c2= 7038544062804420883340530319534054090343999593726615071597649914714397773106261660516938820194721330117082799104642674913839235601210294807255855747823709326405317366422536981850436536877639492293904186333547681934006229055311359852552059601531864585759120757265084674695094298158389804437120173997679271166467086009884419942249925895393890707373985126949313101489352481737754459985522998334847972008827503987883850638250024631354158979424169551575287515128697843093987592614974905262077415255065744686115142126350167970451060399517705823298929164793769442986603707135790651560436497661713972277808036463771768932747376668116480068277125579165831615220097562066809632099809702980365194257899499384219864311379004681733844738981954144617140038448109869114888325128710654235506628539192955240723379334422880368605005772426413018696218105733457019400100498450734710865067764542737004071080719589912326985050985424145053072697267879019954400205613591419766583673115931337146967400159040252514654983240188915104134405655336152730443436887872604467679522955837013574944135975481174502094839012368918547420588186051分析
分解e1*e2 =11· 11· 17· 29
e1=11*17
e2=11*29
gcd(e1,e2)=11
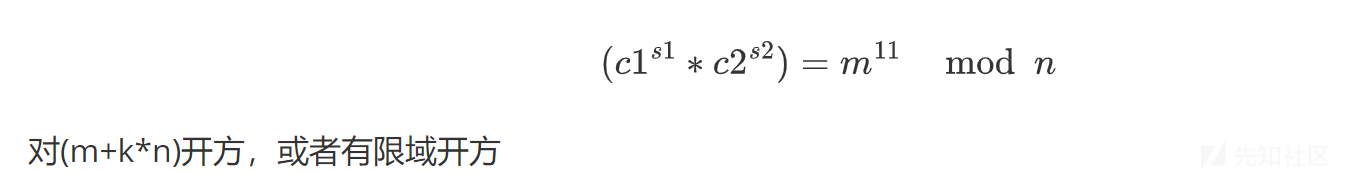
import gmpy2
import libnum
from Crypto.Util.number import long_to_bytes
from gmpy2 import gcd, iroot
from sympy import nthroot_mod
n= 16282992590526808657350657123769110323293742472515808696156540766049532922340638986423163288656942484229334024198335416611687418341772216996129634991032127943095069143600315325916614910606100091970611448259491799589221889445348698100959509165262891180065554743420149168801638644589921791426690475846945077068114953844817073866258377206796158690941199907230130273657375727245023893672164113928189304228859412794067127721813637080447782673535996272223836127807775157150041664783263093604946744032762535394974814371771505843653571711445892969781888188805943142126747365056482511805191315474848971218180999336497135314654469910566730389765499603897685968204361422568601724914800686608628299192714352963744010136960423806304763245890692476493455775025753944860040020178234660999290356849442926396627701588938894161779071628447041006556793933320976506046066961014953196791133933438500843139378274786265308568167479880984705152809744111382599071097574636570516674122980589207824718402382459624138317432883921371298272851693734695823787102433937406420318428888224246291987404818042038201886113203158444083427668636941
c1= 15508846802476602732219982269293312372397631462289816533805702700260237855119470146237752798828431803179124957728439730580289236458563016332461725094295883030444173189424666004498359269921250956676320570006883951982237098373954348825003467019876101438948387668628518937831820206221522881150831840296199498447304138839838135264071071817072965792514115711621435317078108239744829134467948386247696344881838815422262901903767893118533887779588425725845820071451782420200868341564360095012698956683395031351656817392008005928265838760875070634021907630535014959579709368637536268853337028760833769278841040734409299575870823873616769863828516877971432999417800417684146077045836940988096634144368727546539602310924702126212020003620219218637652874119299016382481718659448722433296761241365473608283436835986184098161365747699791248301452334044327014782249692551362625130537300221641910570569803981153117200694806974917501061411963827755822672178568783269357196133308719688843211664095412087717861154226475203597889635926903753481174280305996204091501578865951177135086807765873529089048911740160698421289371229606
c2= 7038544062804420883340530319534054090343999593726615071597649914714397773106261660516938820194721330117082799104642674913839235601210294807255855747823709326405317366422536981850436536877639492293904186333547681934006229055311359852552059601531864585759120757265084674695094298158389804437120173997679271166467086009884419942249925895393890707373985126949313101489352481737754459985522998334847972008827503987883850638250024631354158979424169551575287515128697843093987592614974905262077415255065744686115142126350167970451060399517705823298929164793769442986603707135790651560436497661713972277808036463771768932747376668116480068277125579165831615220097562066809632099809702980365194257899499384219864311379004681733844738981954144617140038448109869114888325128710654235506628539192955240723379334422880368605005772426413018696218105733457019400100498450734710865067764542737004071080719589912326985050985424145053072697267879019954400205613591419766583673115931337146967400159040252514654983240188915104134405655336152730443436887872604467679522955837013574944135975481174502094839012368918547420588186051
e1=319
e2=187
# assert e1*e2==59653
gc=(gcd(e1,e2))
s,s1,s2=gmpy2.gcdext(e1,e2)
m=(pow(c1,s1,n)*pow(c2,s2,n))%n
for j in range(1000):
if iroot(m+j*n,gc)[-1]:
print(long_to_bytes(int(iroot(m+j*n,gc)[0])))
b'flag{83003508-f7a0-4f11-bf47-1efd46bf4da6}'NSSCTF{83003508-f7a0-4f11-bf47-1efd46bf4da6}
Take what you want
题目
想要flag?给你
5gb 87yjnb
5tgbyujm 6yhnuik, jkiuhnm
fgtrdcv bgtyujm hgvbhu
ytfvbhn
ytfvb 6tfcyuhb ytfvbhn tgbyujm ytfvbjkiuhnm
rtygb tfvbhy
76thbv rtygb ytfvbhn 5tgby78 tyuhn
uygbnjm 76thujnbv resxcfv 7jm tgbyujm
得到的flag请用NSSCTF{}包裹,除NSSCTF外,flag内容里所有字母均为小写
hint:做这道题你需要一个键盘
分析
就是在键盘上描出来,能表示出一个字符

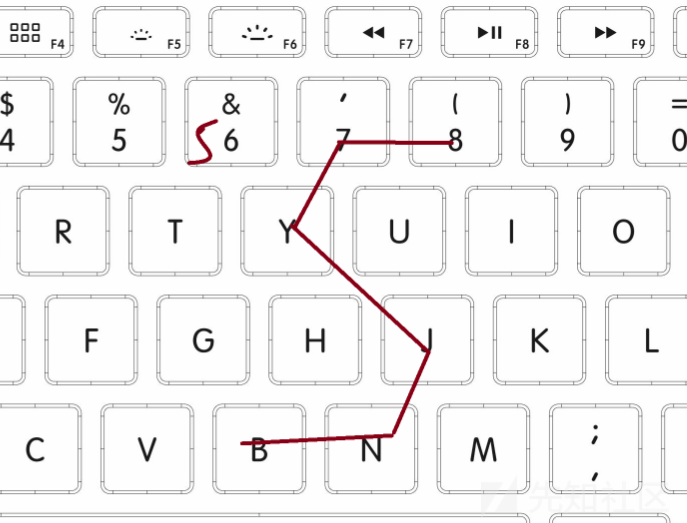
i s
the
end
a
chance
to
start
again
NSSCTF{is the end a chance to start again}
flag_where
题目
flag1=b'******'
p = getPrime(512)
q = getPrime(512)
n = p*q
e = 3
m1 = bytes_to_long(flag1)
a = getPrime(128)
b = getPrime(128)
m2 = a*m1 + b
hint1 = a**2 + a*b
hint2 = b**2 + b*a
c1 = pow(m1, e, n)
c2 = pow(m2, e, n)
print(f'n = {n}')
print(f'hint1 = {hint1}')
print(f'hint2 = {hint2}')
print(f'c1 = {c1}')
print(f'c2 = {c2}')
'''
n = 96294984374753089080583610747240203389088051930341615602841335596072081913930052484580770899610689065293206976889303327507604080242460321817406117877072425663471808350427893332726383611142246218026112051129578226014713958882307096859175042839198895428723757405196020266267824586199807170149650434306779718677
hint1 = 111128465335502483574544230236618721723785067258103368528600651970108082026274
hint2 = 149777690555091648253749138438840244052377948686936166203166372618778229891842
c1 = 19258639302759286032385037035129183959148363633353536085988651266927081471573889078520697158985164250184287591219408939982288951952002632371950165308028756191357634396067109728491154241759098403135297660541258808223827178690693818047525955978891748361038516201626720292976210372367169577574791733786601438737
c2 = 94728391095098686718854324913205273277837107275197779266203956111447917954217642996612375426900185362566372715775684730383657923112702380810451305560067414494793397392647318953106387697001580454130672044011060132072400728672015125332880303053556556640562753160804196189095016248121783366388642672259225712092
'''分析
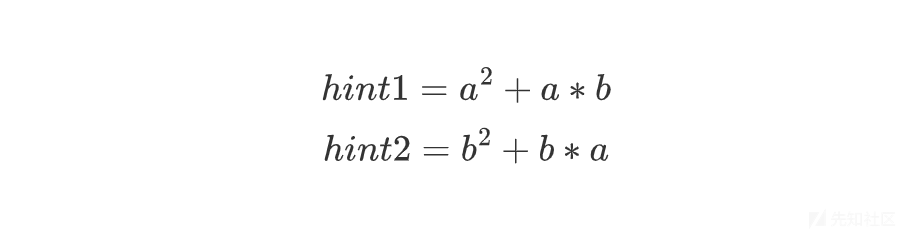
解二元一次方程
求出a,b,就得到m1,m2之间的关系m2 = a*m1 + b
RSA—相关消息攻击
from Crypto.Util.number import long_to_bytes
n =
hint1 = 111128465335502483574544230236618721723785067258103368528600651970108082026274
hint2 = 149777690555091648253749138438840244052377948686936166203166372618778229891842
c1 =
c2 =
# x, y = var('a, b')
# solve([a**2 + a*b ==hint1, b**2 + b*a==hint2], x, y)
# [a == 217562055747111316427029035559575901669, b == 293227681709108659093110186239101833877]]
a=217562055747111316427029035559575901669
b=293227681709108659093110186239101833877
def franklinReiter(n, e, c1, c2, a, b):
PR.<x> = PolynomialRing(Zmod(n))
g1 = (x) ^ e - c1
g2 = (a * x + b) ^ e - c2
def gcd(g1, g2):
while g2:
g1, g2 = g2, g1 % g2
return g1.monic() #
return -gcd(g1, g2)[0]
m = franklinReiter(n, 3, c1, c2, a, b)
print(long_to_bytes(int(m)))
# b'ZcxKh0OHA4nmSOnyeKsfh44P8FukJ6VMmQlXsAAAAASUVORK5CYII='ZcxKh0OHA4nmSOnyeKsfh44P8FukJ6VMmQlXsAAAAASUVORK5CYII=
压缩包密码打开得到图片
NSSCTF{flagls1neverywhereatanytimef}

发现这不是flag,图片有猫腻,把图片扔到010里,发现
n= 23613440611274671981103562117762261407657733032262530808365808460802265777404559689770212205664056651689849304576137012508441030782562719114824768464775304331357062635791932441797662757831660552844003759285119574349208127247279359306048367901670313942242293660325209254802053786362409960527461289549743183131793123086882884499956331652650601135698081029508500034843745858862415689306278980446458807168395881472172471730255424421648602988543988586027701543404817919626933524670439936405497236264107287151288962539180486176914120546870484668665264576021156708057529615192067896540955731053282702775053130195750940441499
e= 3
c= 6224502790241725121858151083881916470453047115244132459991459154927516119017085320641701845030115595623733051828266146127822033656314679638782226145682487721992169123432564248314029318691399607764252052430390312899182425006711775775635366515484611511550894355625585295587944764723959996392921955004444258683331994239527759128065125
直接开方,e=3
n= 23613440611274671981103562117762261407657733032262530808365808460802265777404559689770212205664056651689849304576137012508441030782562719114824768464775304331357062635791932441797662757831660552844003759285119574349208127247279359306048367901670313942242293660325209254802053786362409960527461289549743183131793123086882884499956331652650601135698081029508500034843745858862415689306278980446458807168395881472172471730255424421648602988543988586027701543404817919626933524670439936405497236264107287151288962539180486176914120546870484668665264576021156708057529615192067896540955731053282702775053130195750940441499
e= 3
c= 6224502790241725121858151083881916470453047115244132459991459154927516119017085320641701845030115595623733051828266146127822033656314679638782226145682487721992169123432564248314029318691399607764252052430390312899182425006711775775635366515484611511550894355625585295587944764723959996392921955004444258683331994239527759128065125
# print(isPrime(n))
m=int(gmpy2.iroot(c,3)[0])
print(long_to_bytes(m))
# NSSCTF{flagIs1neverywhereatanytimeforeveryone}Bury the Light
题目
出题人发烧好了,发一道签到题庆祝一下
from Crypto.Cipher import AES
from Crypto.Util.number import *
from Crypto.Util.Padding import pad
from secret import flag
mask1 = 131151158277430590850506190902325379931
mask2 = 234024231732616562506949148198103849397
mask3 = 175840838278158851471916948124781906887
mask4 = 270726596087586267913580004170375666103
def lfsr(R, mask):
R_bin = [int(b) for b in bin(R)[2:].zfill(128)]
mask_bin = [int(b) for b in bin(mask)[2:].zfill(128)]
s = sum([R_bin[i] * mask_bin[i] for i in range(128)]) & 1
R_bin = [s] + R_bin[:-1]
return (int("".join(map(str, R_bin)), 2), s)
def ff(x0, x1, x2, x3):
return (x0 ^ x1 ^ x2 ^ x3) & 1
def round(R, R1_mask, R2_mask, R3_mask, R4_mask):
out = 0
R1_NEW, _ = lfsr(R, R1_mask)
R2_NEW, _ = lfsr(R, R2_mask)
R3_NEW, _ = lfsr(R, R3_mask)
R4_NEW, _ = lfsr(R, R4_mask)
for _ in range(300):
R1_NEW, x1 = lfsr(R1_NEW, R1_mask)
R2_NEW, x2 = lfsr(R2_NEW, R2_mask)
R3_NEW, x3 = lfsr(R3_NEW, R3_mask)
R4_NEW, x4 = lfsr(R4_NEW, R4_mask)
out = (out << 1) + ff(x1, x2, x3, x4)
return out
key = getRandomNBitInteger(128)
out = round(key, mask1, mask2, mask3, mask4)
cipher = AES.new(long_to_bytes(key), mode=AES.MODE_ECB)
print(f"out = {out}")
print(f"enc = {cipher.encrypt(pad(flag.encode(), 16))}")
#out = 1758689793017181583485607518128257451365441445520643573250819171196665713945177624962575711
#enc = b'g\xf6\xc8\x1d\x1ap\xb9\xefd\xcc\xf0t\xe8/O\x7f\x89\xa3l \x8bR[\x91\xddd\x11\x98tA\x12\xcc\xa5Jl\x08\xd7\x87\xa2M\x1c\xe46rm\x16\x9b('
分析

hint给了key,秒了,aes解
NSSCTF{Born in flames, I have been blessed}


 转载
转载
 分享
分享
