赣育杯2024逆向方向部分wp
level3
一个apk文件,直接丢进jeb反编译,发现反编译的内容很乱,看到左侧
加了SecShell壳
下载脱壳工具BlackDex
https://github.com/CodingGay/BlackDex
在模拟器中脱壳后,得到了一个dex文件,丢进jeb反编译
package com.example.myapplication;
import android.os.Bundle;
import android.view.View.OnClickListener;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.Toast;
import androidx.appcompat.app.AppCompatActivity;
import java.io.ByteArrayOutputStream;
import java.io.IOException;
import java.io.InputStream;
import java.util.zip.Inflater;
public class MainActivity extends AppCompatActivity implements View.OnClickListener {
byte[] map;
EditText password;
public MainActivity() {
this.map = null;
this.password = null;
}
public boolean checkPassword(byte[] map, String password) {
int x = 1;
int y = 1;
char[] arr_c = password.toCharArray();
int v2 = 0;
label_4:
while(v2 < arr_c.length) {
switch(arr_c[v2]) {
case 97: {
--y;
break;
}
case 100: {
++y;
break;
}
case 0x73: {
++x;
break;
}
case 0x77: {
--x;
break;
}
default: {
return false;
}
}
switch(map[x * 11 + y]) {
case 35: {
return false;
}
case 36: {
return true;
}
default: {
++v2;
continue label_4;
}
}
return true;
}
return false;
}
public static byte[] decompress(byte[] compressedData) throws IOException {
Inflater inflater = new Inflater();
inflater.setInput(compressedData);
ByteArrayOutputStream outputStream = new ByteArrayOutputStream(compressedData.length);
byte[] buffer = new byte[0x400];
while(!inflater.finished()) {
try {
outputStream.write(buffer, 0, inflater.inflate(buffer));
}
catch(Exception e) {
break;
}
}
outputStream.close();
return outputStream.toByteArray();
}
@Override // android.view.View$OnClickListener
public void onClick(View v) {
try {
InputStream inputStream0 = this.getResources().getAssets().open("map");
byte[] arr_b = new byte[inputStream0.available()];
this.map = arr_b;
inputStream0.read(arr_b);
if(inputStream0.read(this.map) != 0) {
this.map = MainActivity.decompress(this.map);
goto label_10;
}
throw new Exception();
}
catch(Exception e) {
Toast.makeText(this, "something wrong", 0).show();
}
label_10:
if(this.checkPassword(this.map, this.password.getText().toString())) {
Toast.makeText(this, "you are right flag is md5(your input)(lower case~)", 0).show();
return;
}
Toast.makeText(this, "wrong input!", 0).show();
}
@Override // androidx.fragment.app.FragmentActivity
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
this.setContentView(layout.activity_main);
Button mazescheck = (Button)this.findViewById(id.button);
this.password = (EditText)this.findViewById(id.editTextText);
mazescheck.setOnClickListener(this);
}
}
显然是一个迷宫,1111,wasd控制上下左右,`为路径,#为墙壁,$`为终点
map只经过了decompress方法加密,即zlib压缩
先找map,解压apk文件,在assets目录下找到了map文件,用010打开,把十六进制部分复制下来
先用cyberchef改一下形式
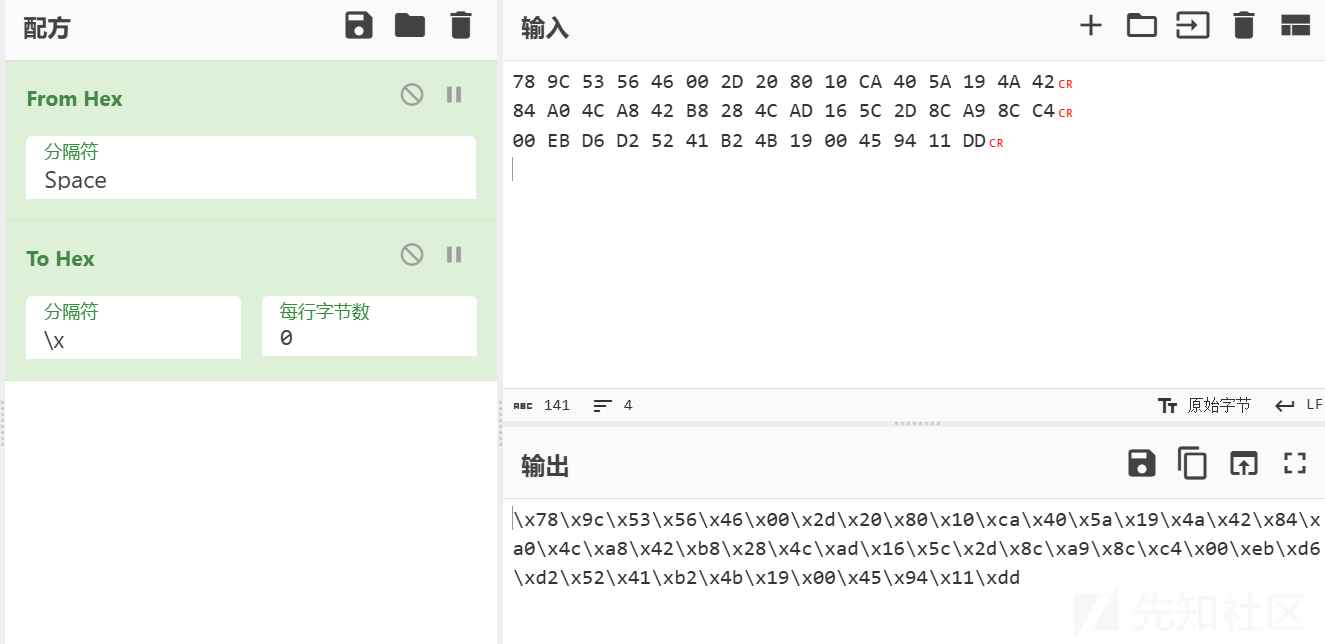
然后写解压代码
import zlib
data = b'\x78\x9c\x53\x56\x46\x00\x2d\x20\x80\x10\xca\x40\x5a\x19\x4a\x42\x84\xa0\x4c\xa8\x42\xb8\x28\x4c\xad\x16\x5c\x2d\x8c\xa9\x8c\xc4\x00\xeb\xd6\xd2\x52\x41\xb2\x4b\x19\x00\x45\x94\x11\xdd'
data1 = zlib.decompress(data)
print(data1)
a = '############****#****##*#*###*#*##*#*****#*##*#######*##*#*******##*#*#*#*#*##*#*#*#*#*####*#*#*####***#*#**$############'
for i in range(len(a)):
if i % 11==0:
print()
print(a[i],end='')
###########
#****#****#
#*#*###*#*#
#*#*****#*#
#*#######*#
#*#*******#
#*#*#*#*#*#
#*#*#*#*#*#
###*#*#*###
#***#*#**$#
###########
手动走一下迷宫
ddssddddwwddssssaassssdd
md5加密得到flaga7bfaf2c2d38fea97b8ecc0919cdff04
勒索病毒
解压看到4个文件
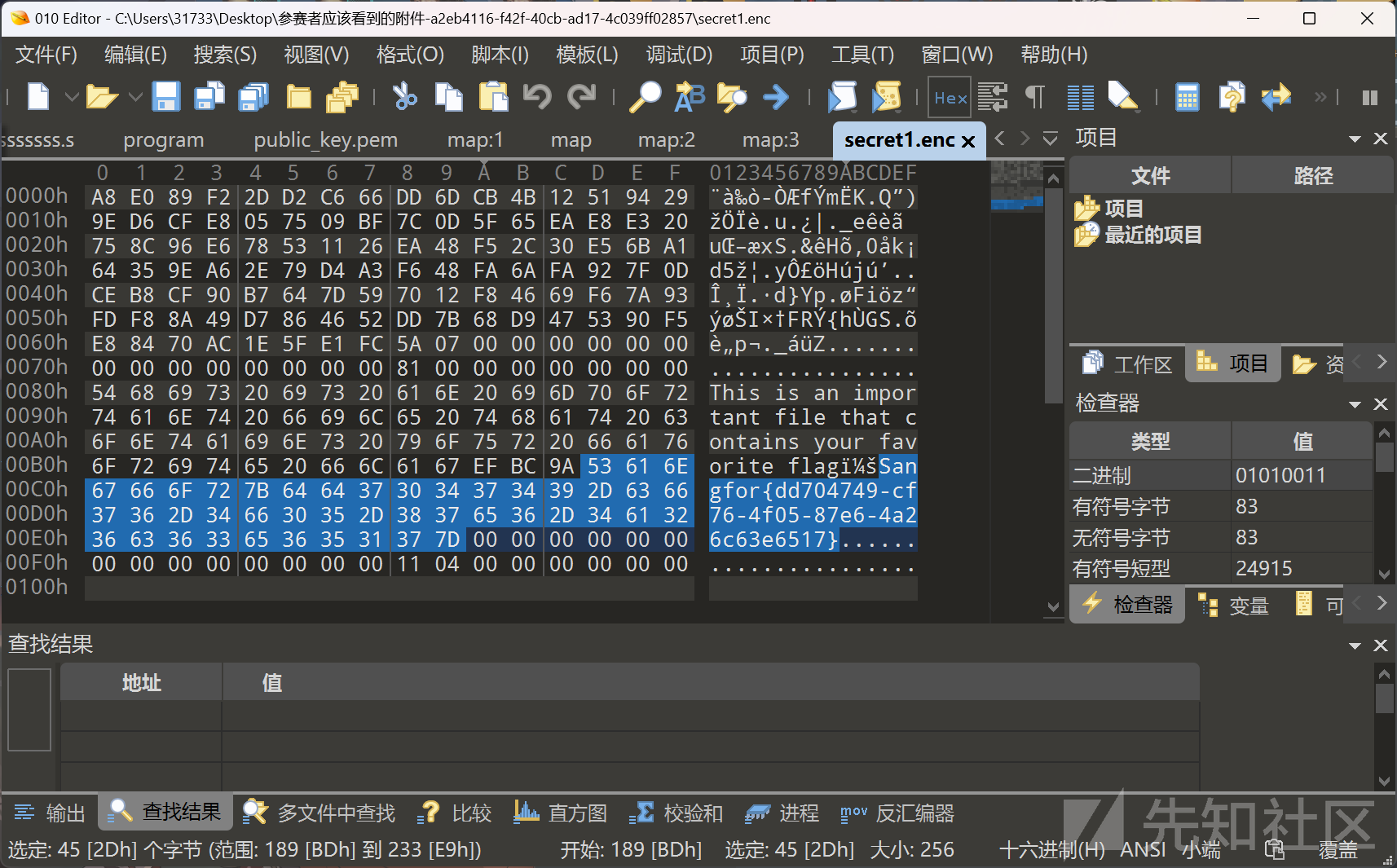
用010editor打开secret1,就这么水灵灵地看到flag了。。。
0 条评论
可输入 255 字


 转载
转载
 分享
分享
